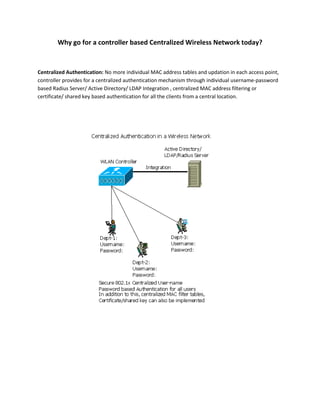
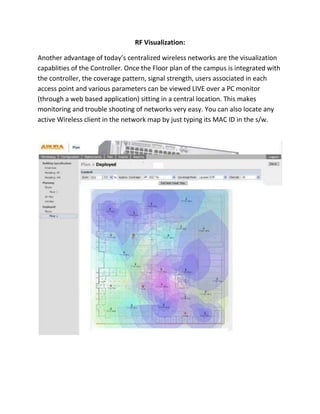
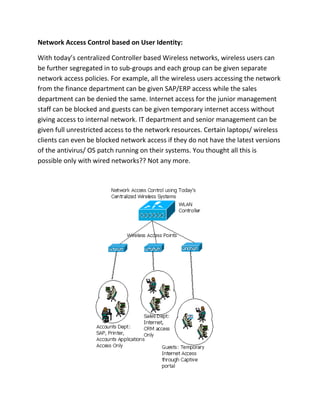
A centralized wireless network consists of wireless access points, wireless controllers, and wireless clients. Wireless access points connect clients to the wired network and are managed by wireless controllers located in data centers. Wireless controllers provide centralized authentication, load balancing, and failure recovery across access points. Controller-based networks allow for visualization of wireless coverage, security features like intrusion detection, and network access control based on user identity.