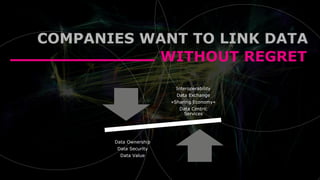
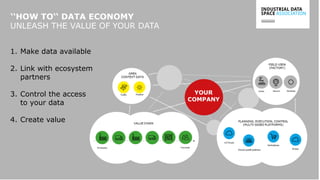
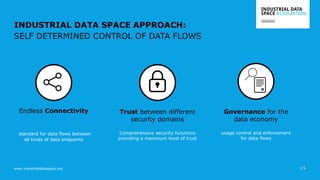
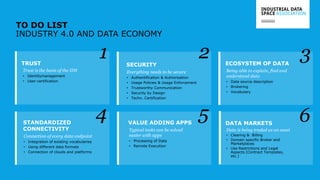
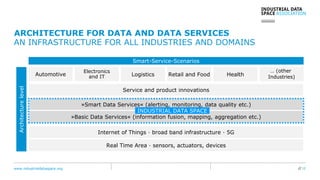
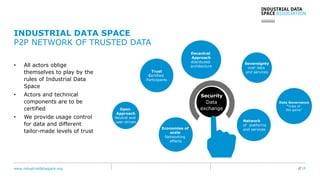
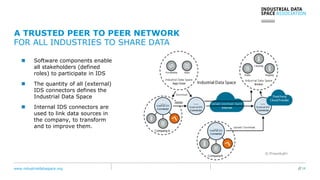
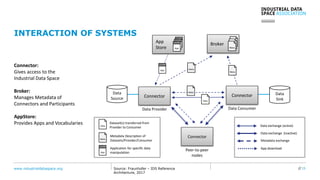
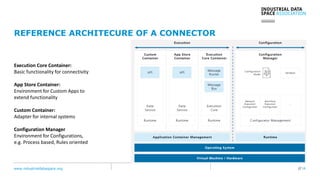
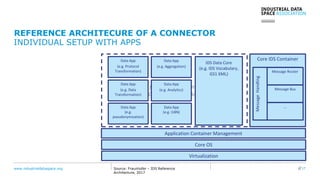
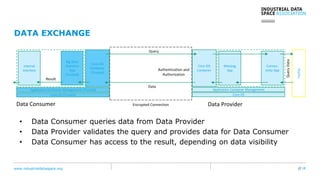
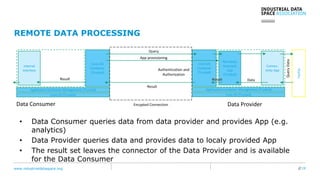
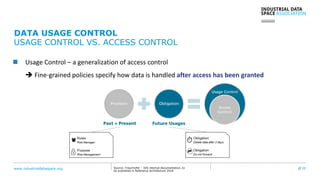
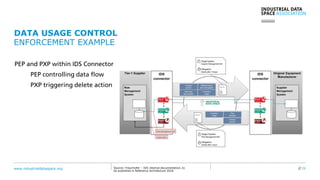
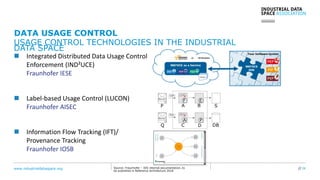
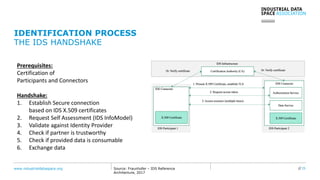
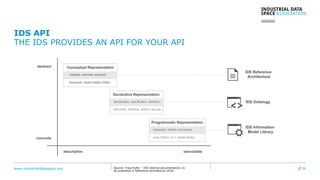
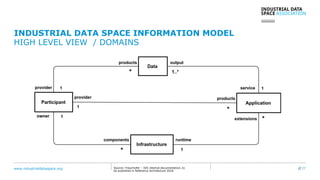
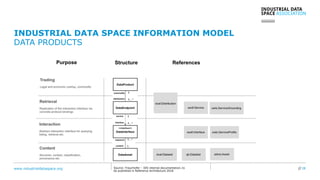
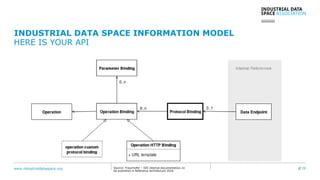
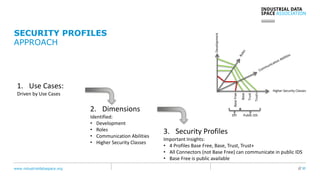
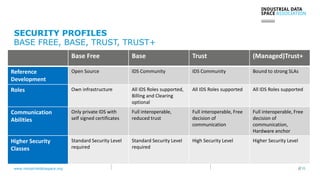
The document presents the Industrial Data Space (IDS) initiative aimed at establishing a secure, shared data ecosystem that supports data linkage and exchange among various industries. It outlines the strategies for data availability, partner integration, access control, and value creation while emphasizing data security and governance. The IDS architecture promotes a decentralized and trusted peer-to-peer network, facilitating efficient data commerce and enhancing innovation across various sectors.