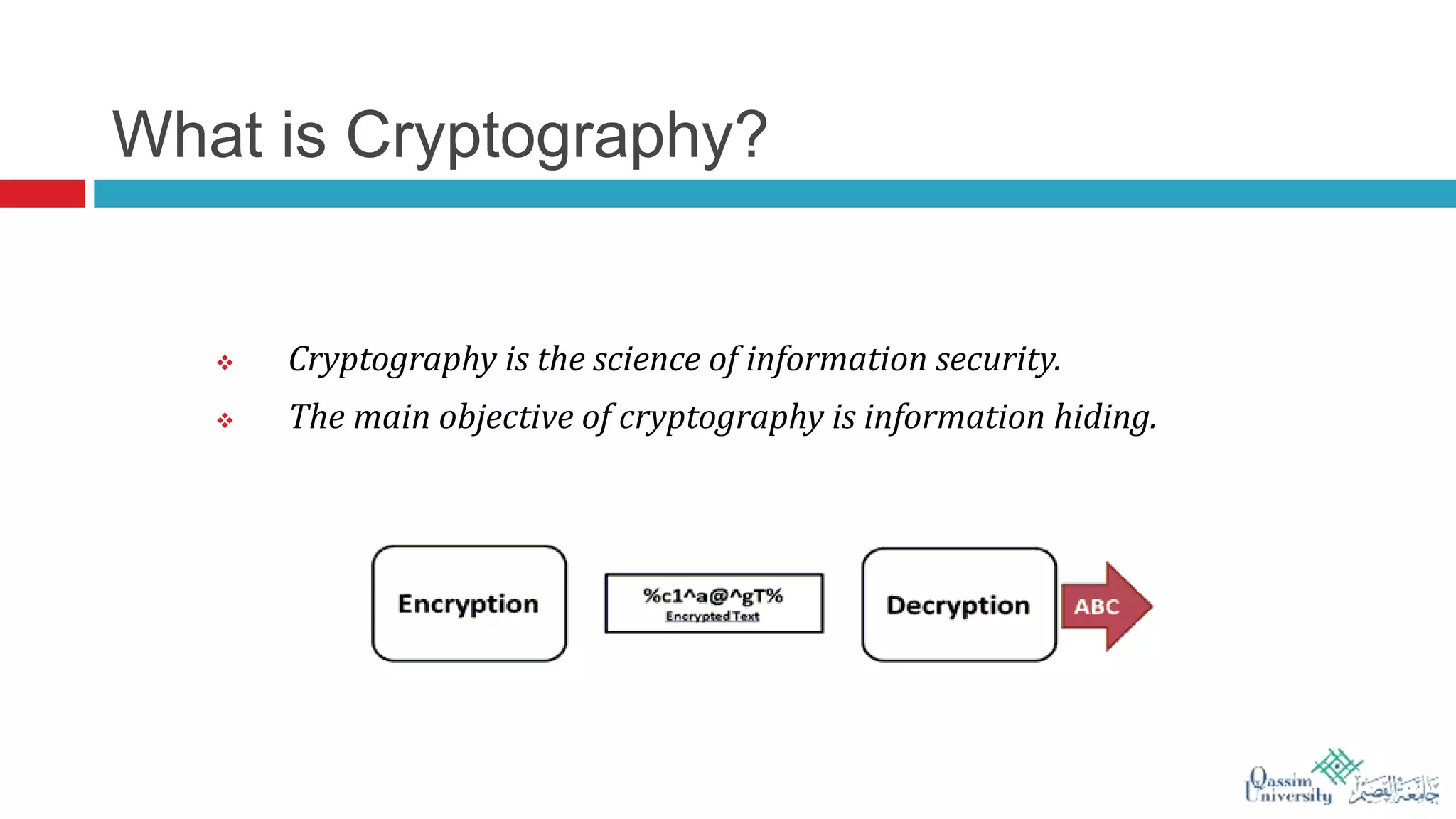
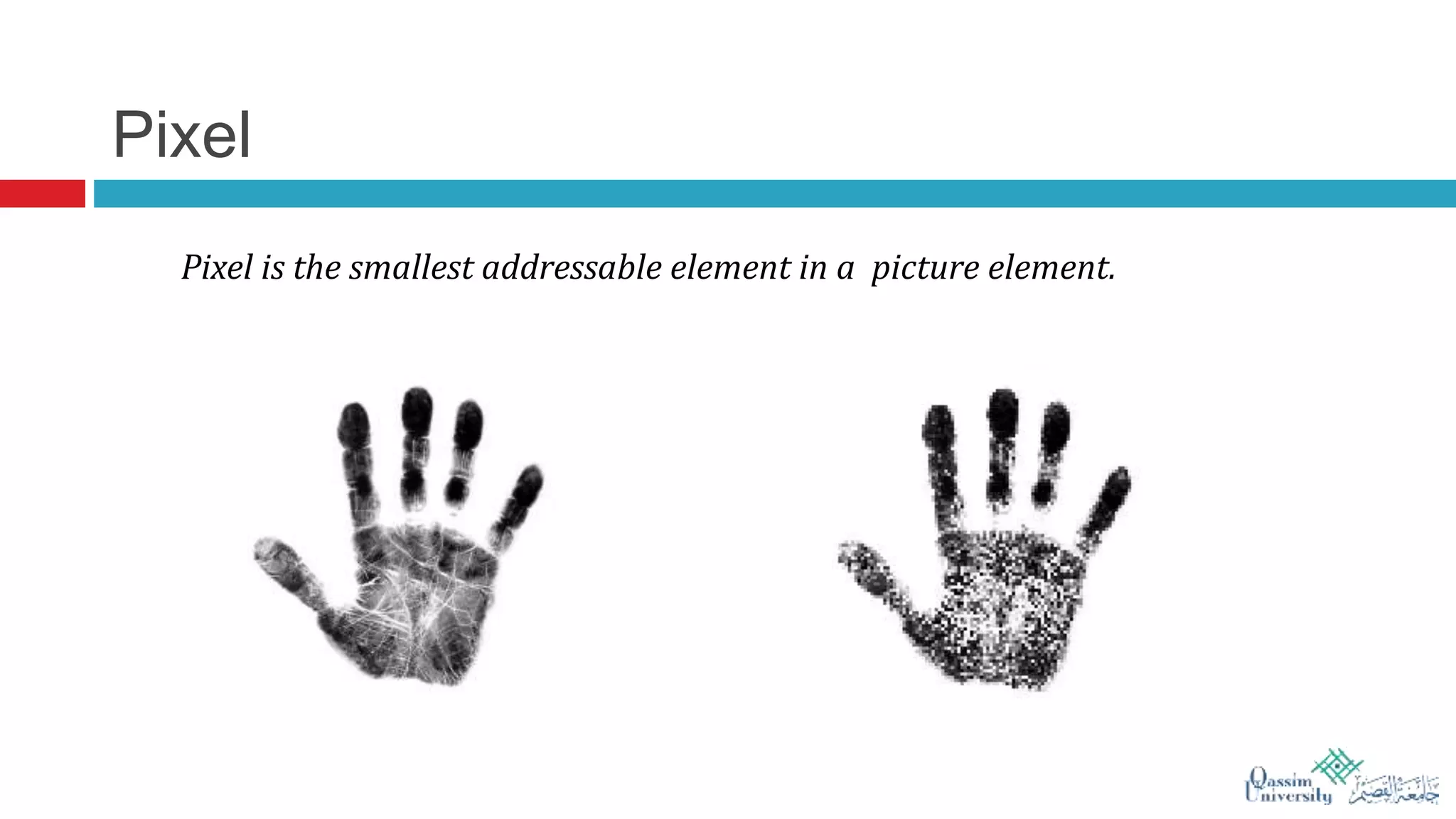
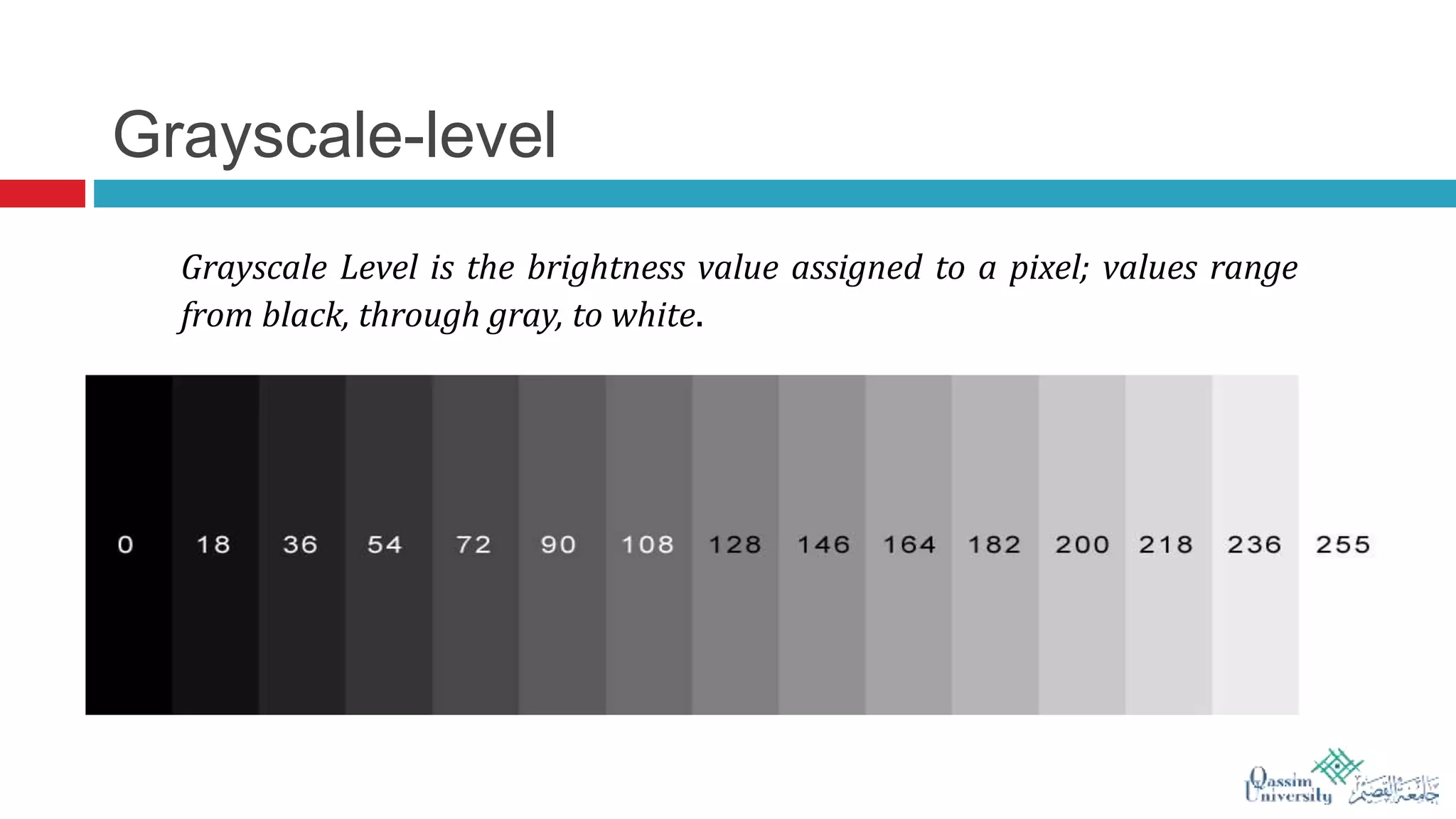
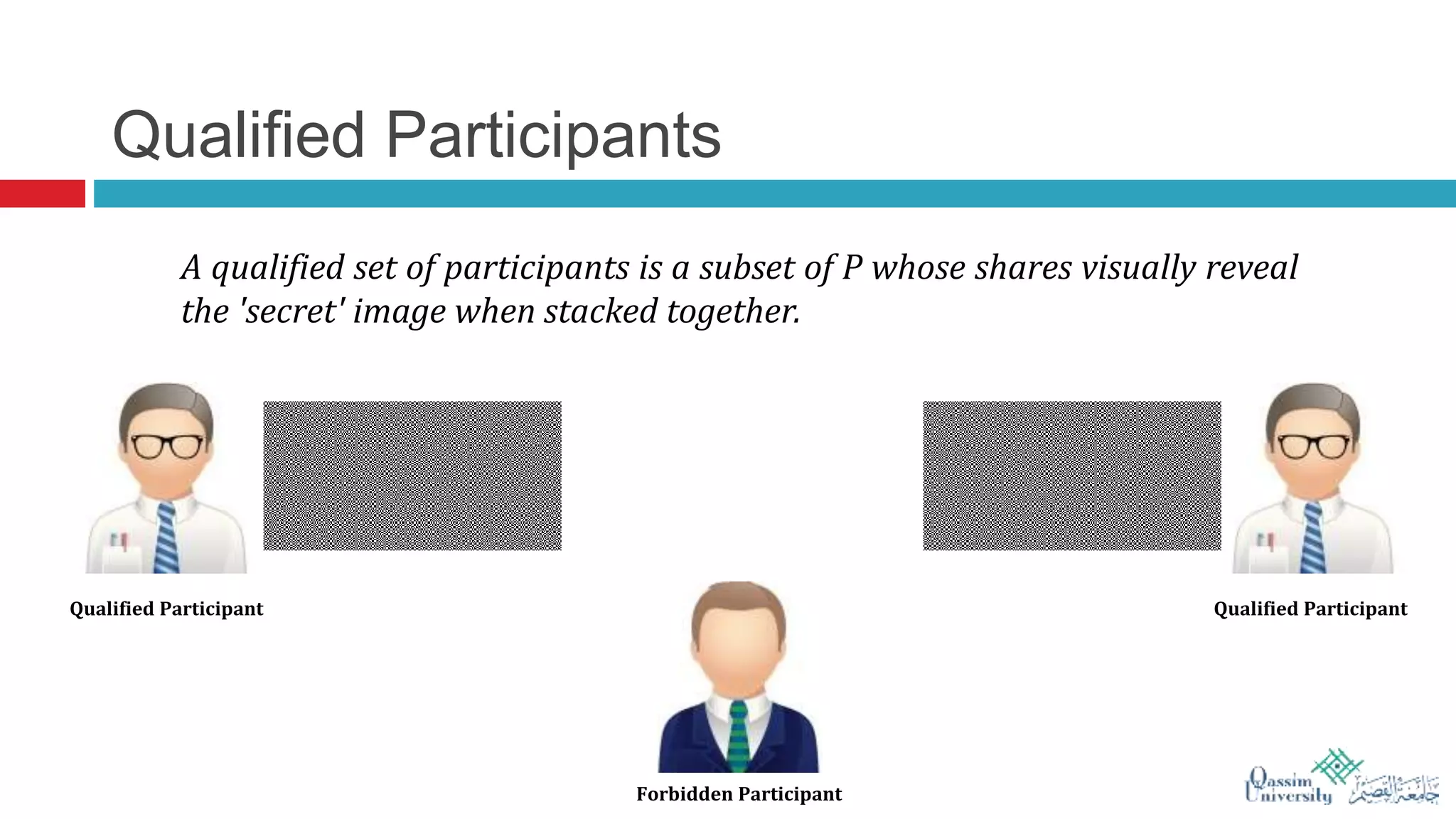
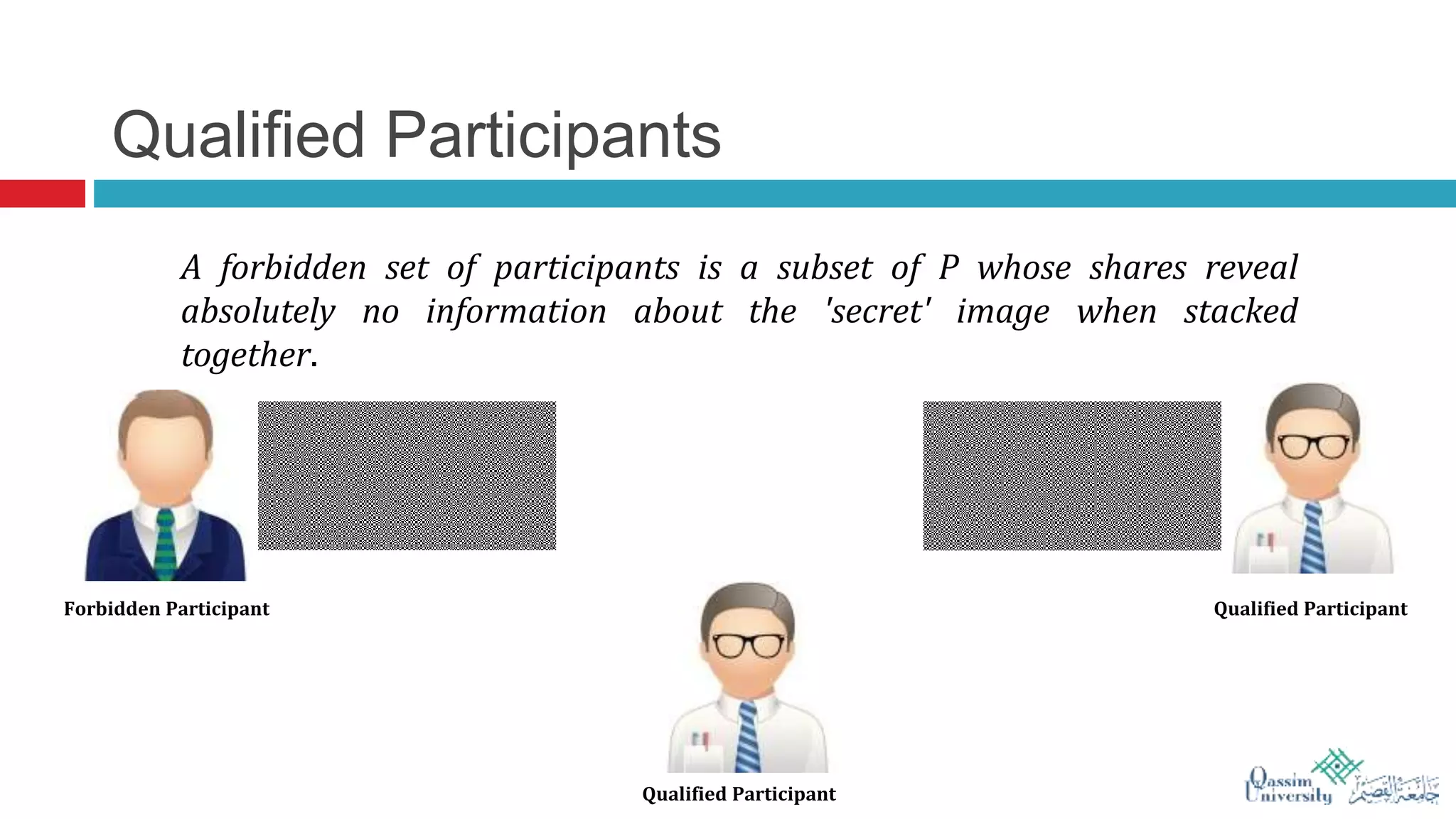
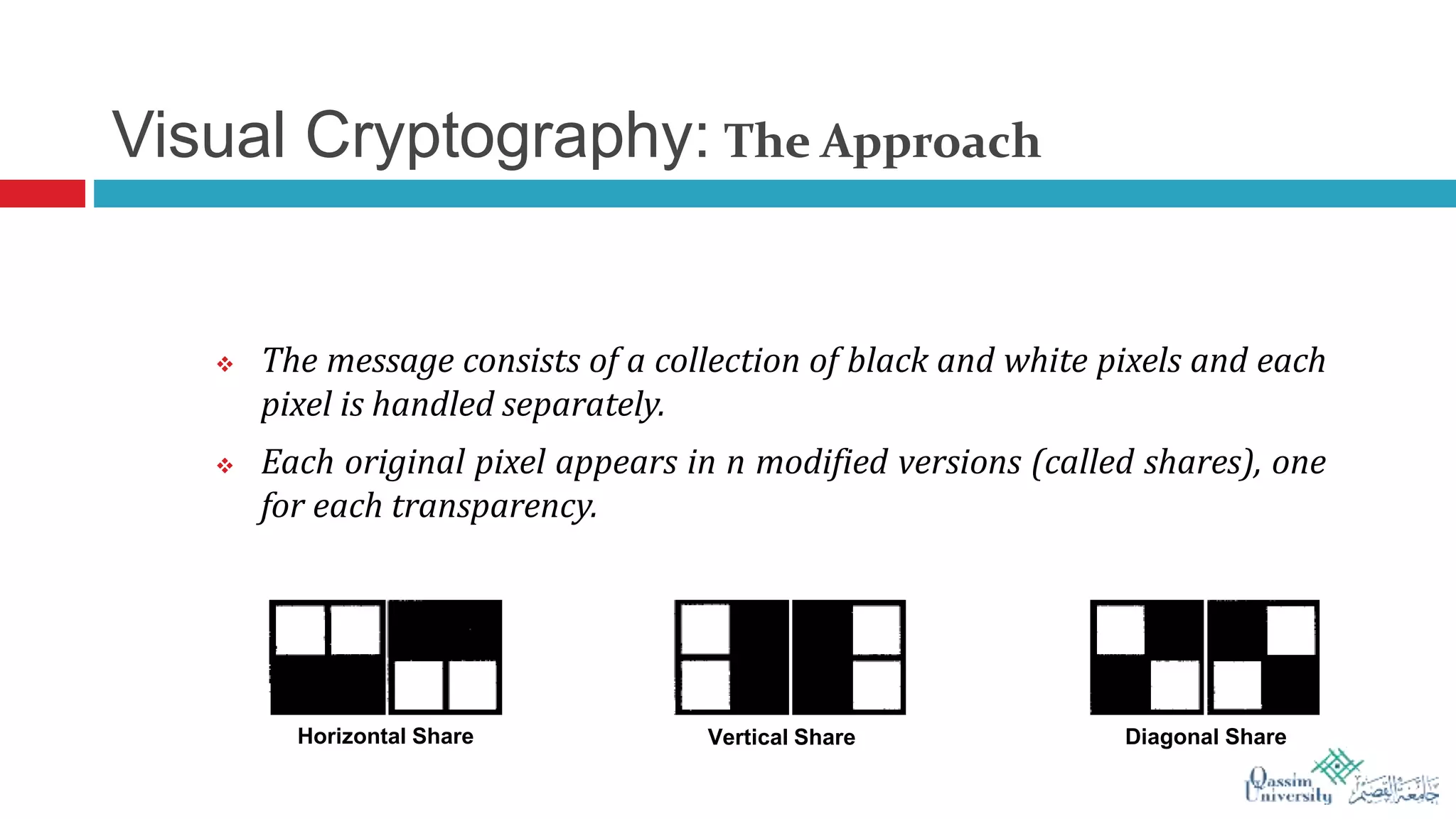
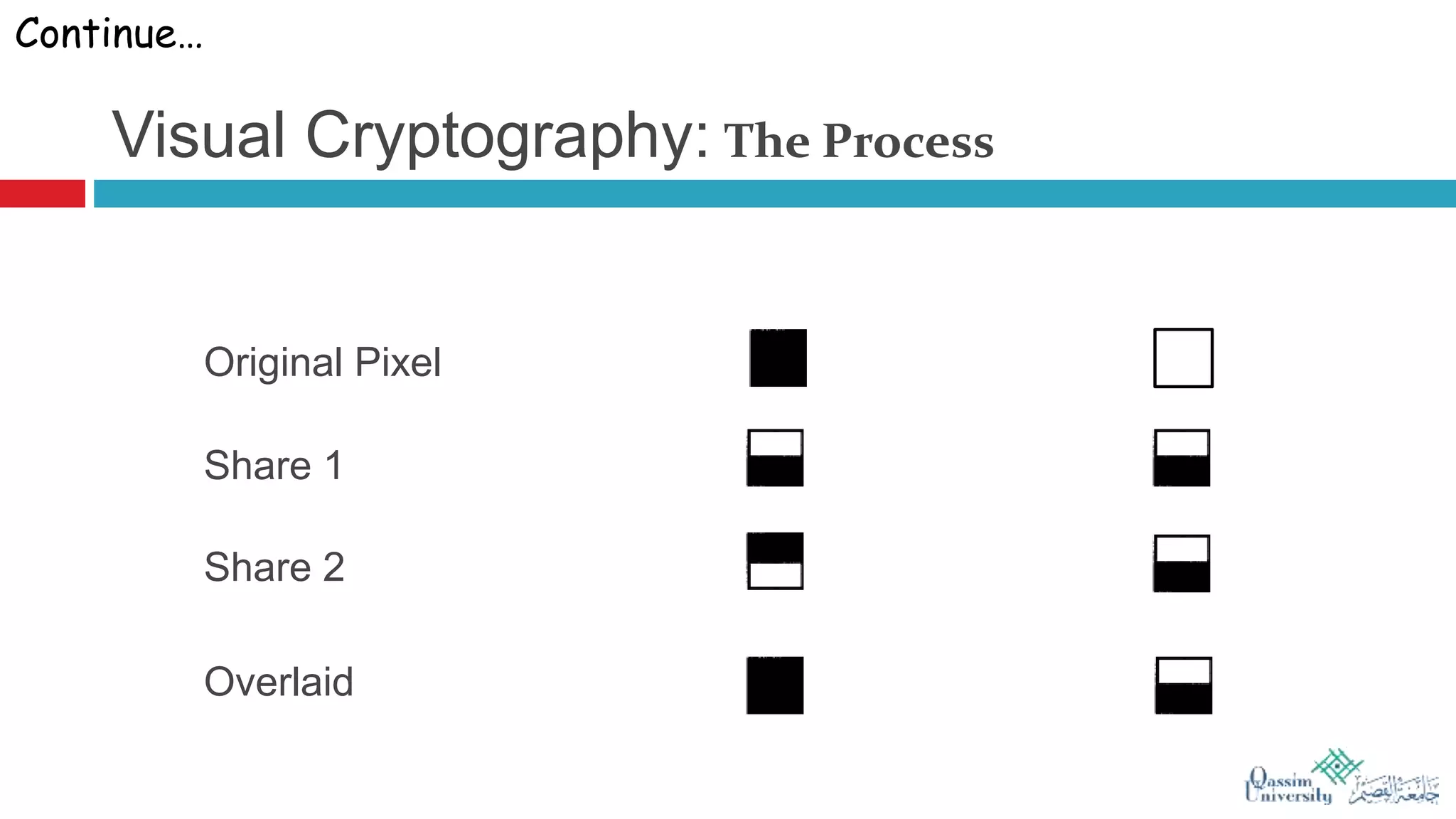
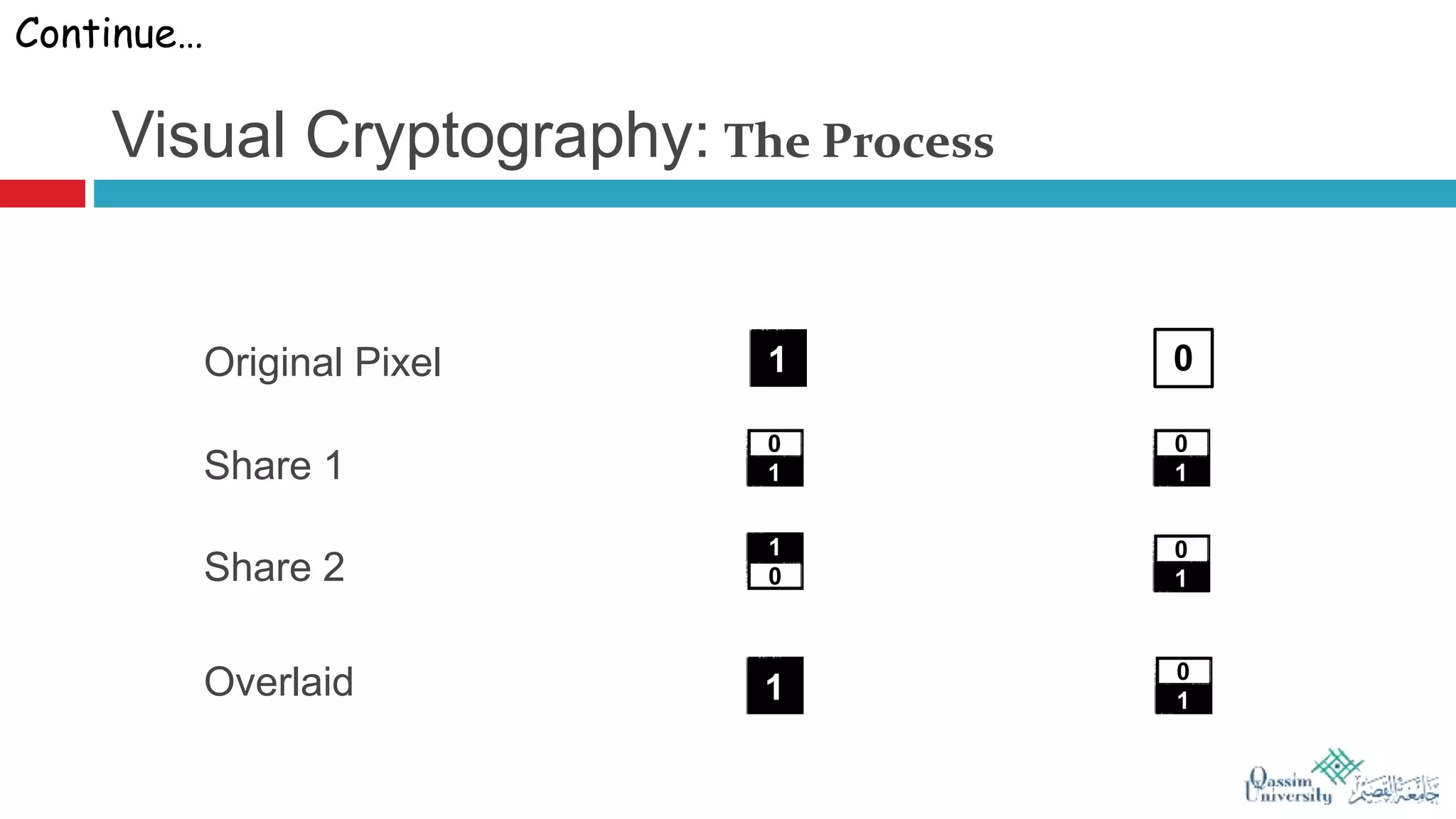
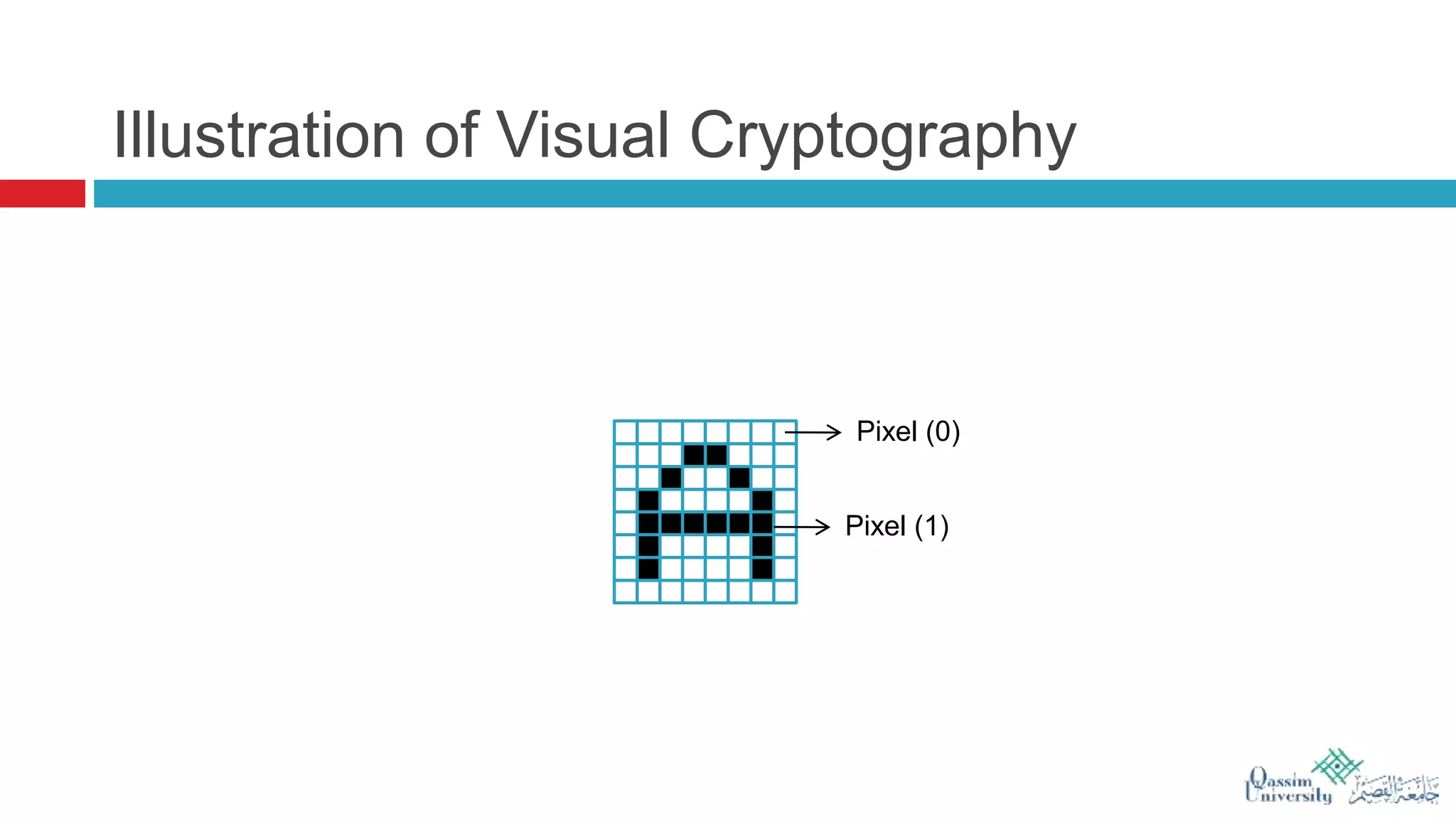
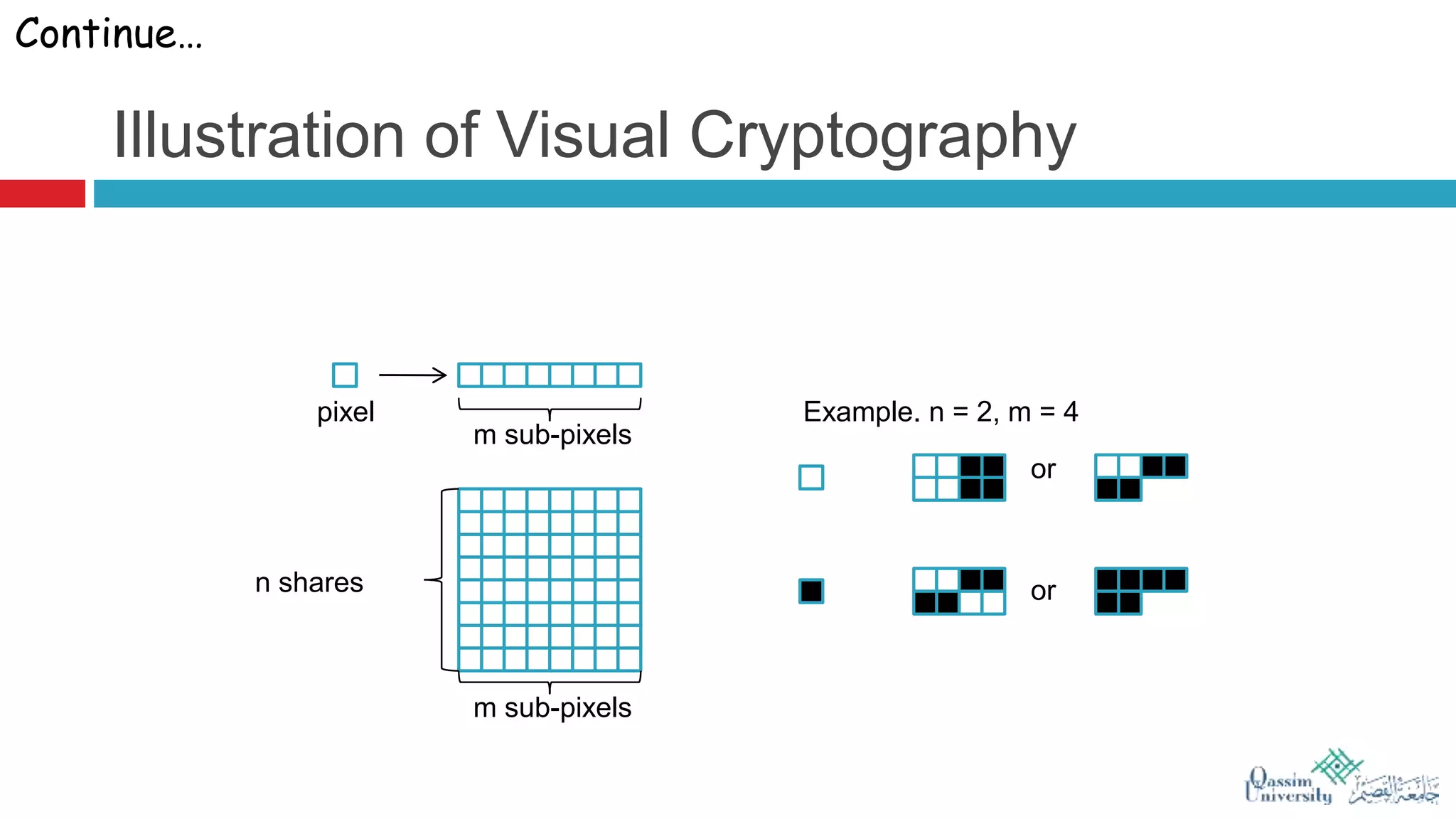
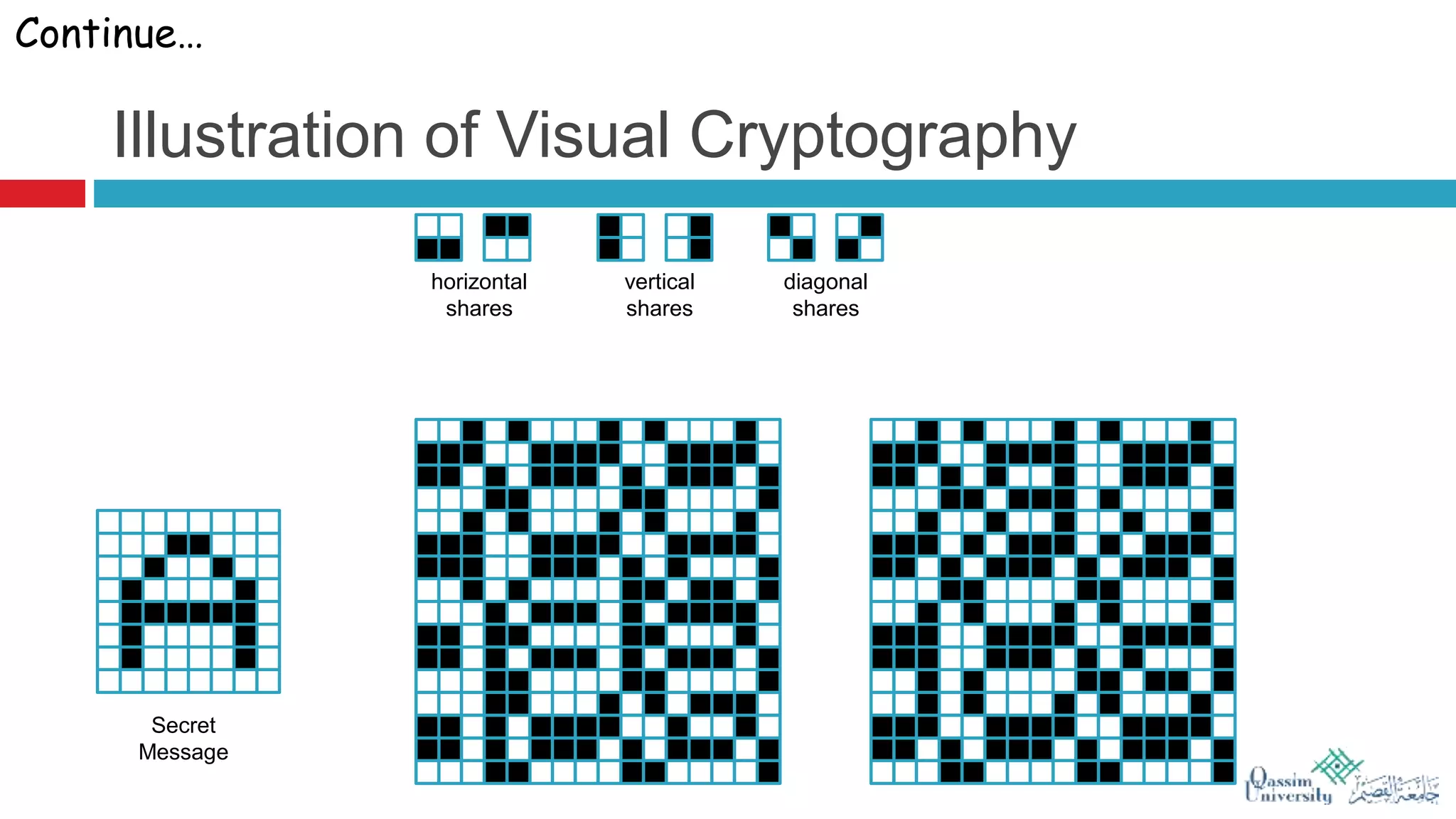
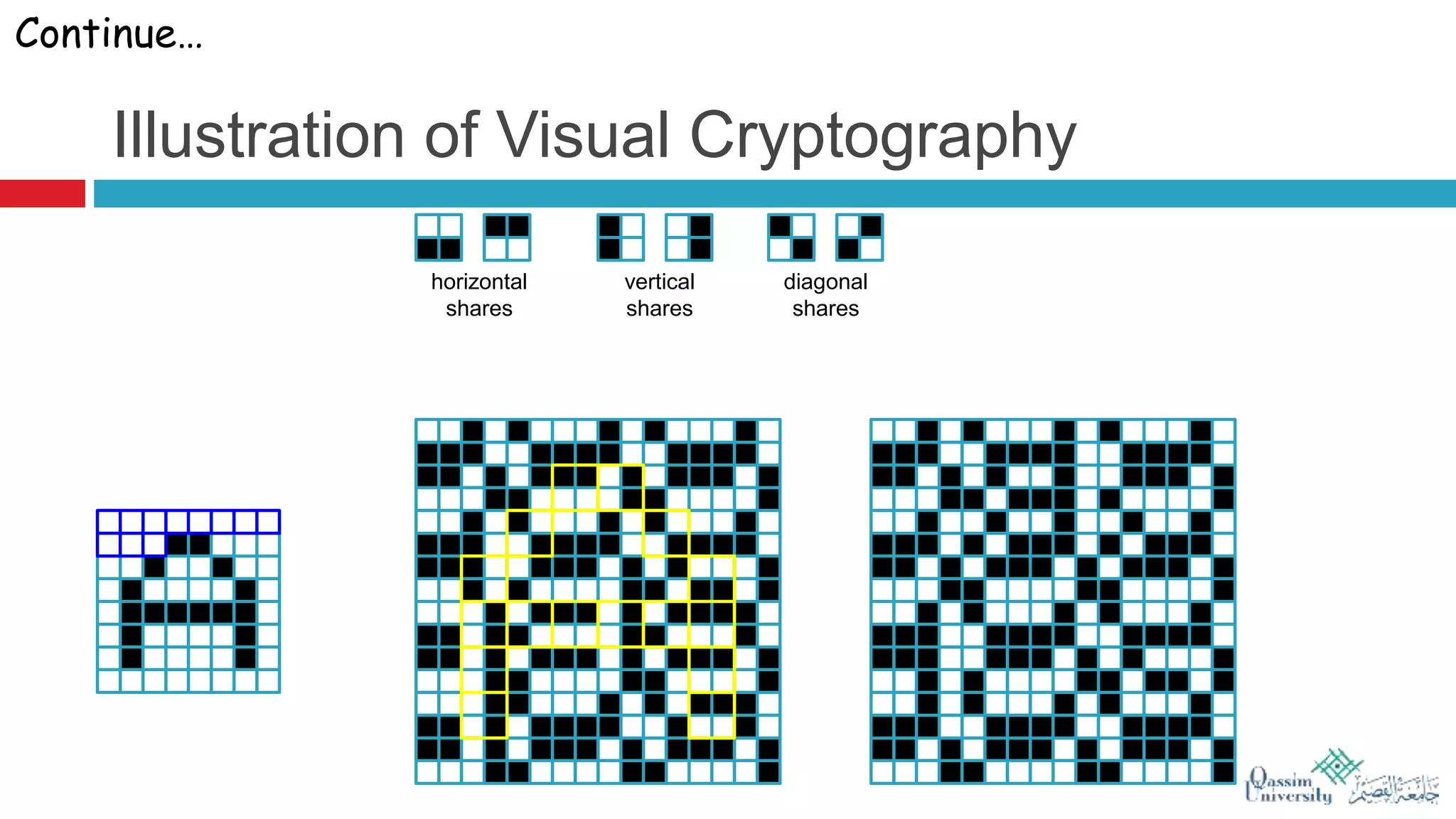
The document discusses visual cryptography, which is a cryptographic scheme that enables the secure encoding and decoding of images without complex computations. It highlights the historical evolution of cryptography, including early methods like hieroglyphics and the Caesar cipher, and details the process of visual cryptography involving shares of pixels. Future developments in the field aim to enhance applications by improving image quality and allowing for implementation with color images.