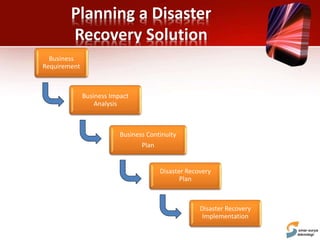
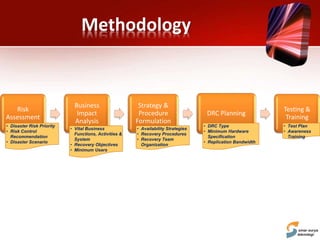
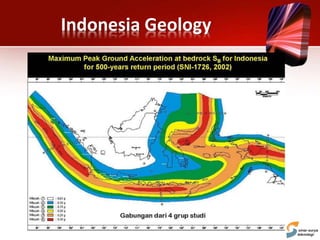
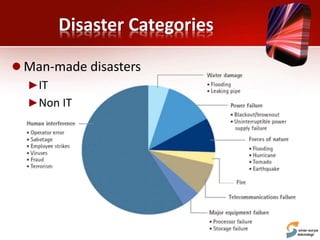
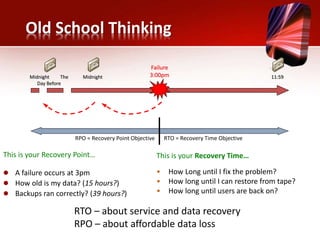
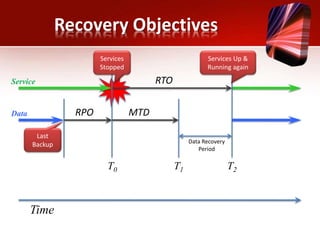
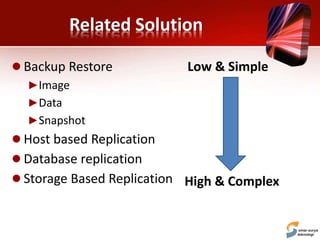
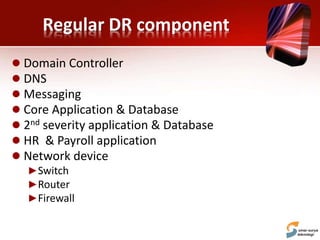
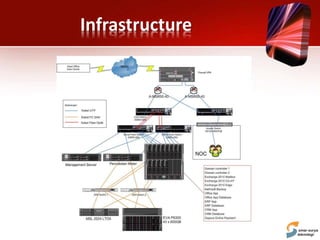
This document discusses planning for a disaster recovery infrastructure. It outlines objectives to minimize business loss during an IT disaster and protect business processes. Key aspects of planning covered include performing a business impact analysis, developing recovery time and point objectives, considering budget, location, system types, and security. The document also discusses various disaster recovery models and prerequisites, such as redundant components and backups.