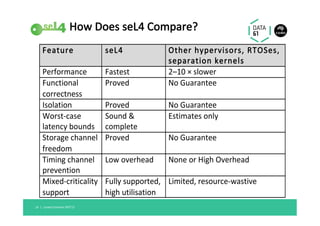
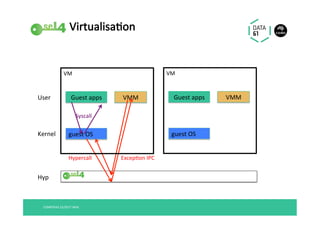
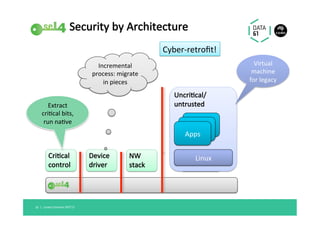
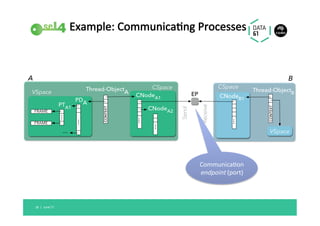
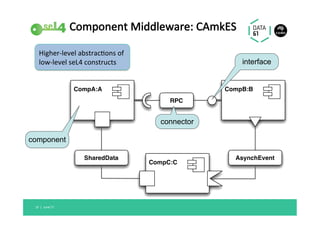
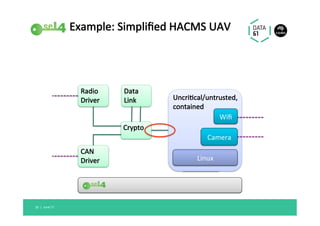
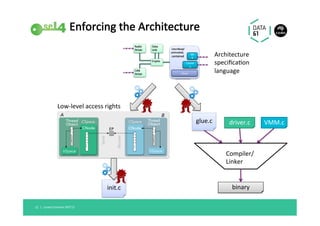
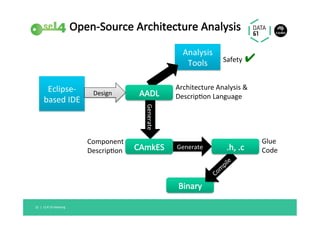
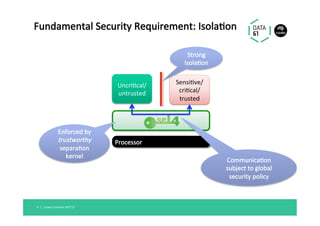
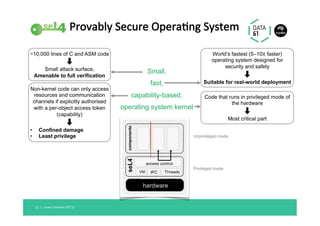
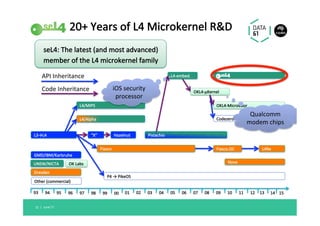
The document discusses the importance of a trustworthy operating system kernel, specifically the seL4 microkernel, which is designed for military-grade security and provable correctness. It highlights the challenges of software vulnerabilities in automotive systems and emphasizes the need for isolation and strong access control to ensure system trustworthiness. The document also compares seL4 with other operating systems and explores its integration with existing systems for enhanced security.

![Claim:
A system must be considered untrustworthy unless
proved otherwise!
Corollary [with apologies to Dijkstra]:
Tes@ng, code inspec@on, etc. can only show
lack of trustworthiness!
Linaro Connect SFO'17 10 |
Trustworthiness: Can We Rely on Isola@on?
A system is trustworthy if and only if:
• it behaves exactly as it is specified,
• in a timely manner,
• while ensuring secure execution](https://image.slidesharecdn.com/sfo17-417-sel4-170929180225/85/The-Open-Source-seL4-Kernel-Military-Grade-Security-Through-Mathematics-SFO17-417-10-320.jpg)
![Integrity
Abstract
Model
C Imple-
menta@on
Confiden-
@ality
Availability
Binary code
Proof Proof Proof
Func@onal
correctness
[SOSP’09]
Isola@on proper@es
[ITP’11, S&P’13]
Transla@on
correctness
[PLDI’13]
Exclusions (at present):
§ Ini@alisa@on
§ Low-level MMU model
§ caches
§ Mul@core
§ Covert >ming channels
Worst-case
execu@on @me
[RTSS’11, RTAS’16]
Provably impossible:
§ buffer overflow
§ null-pointer dereference
§ code injec@on
§ memory leaks
§ kernel crash
§ undefined behaviour
§ privilege escala@on
Proving Trustworthiness of seL4
Linaro Connect SFO'17 13 |](https://image.slidesharecdn.com/sfo17-417-sel4-170929180225/85/The-Open-Source-seL4-Kernel-Military-Grade-Security-Through-Mathematics-SFO17-417-13-320.jpg)