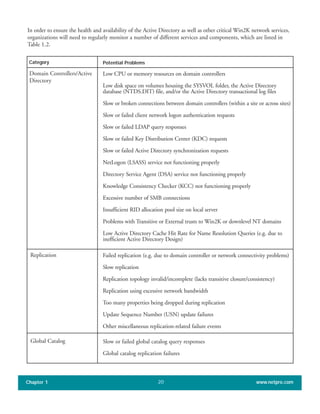
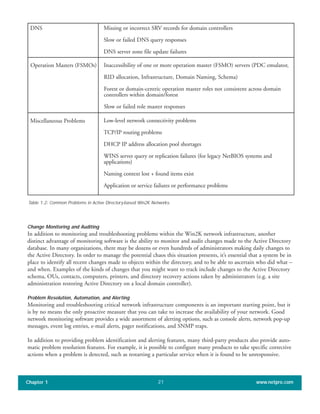
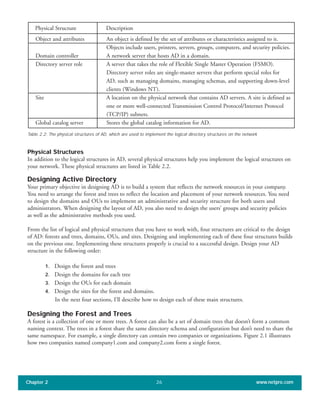
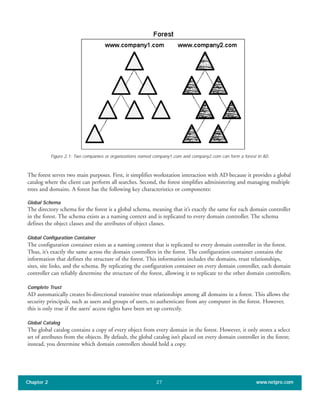
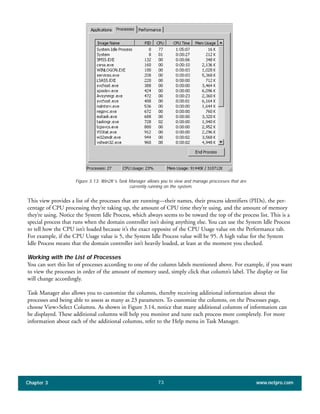
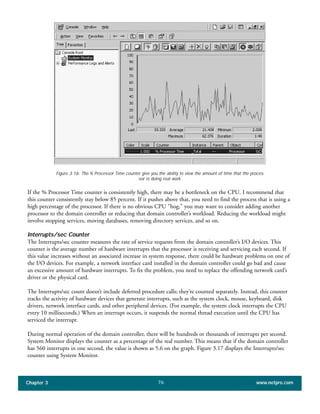
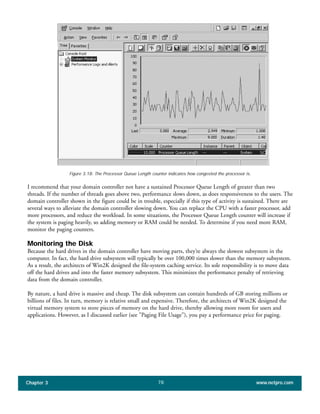
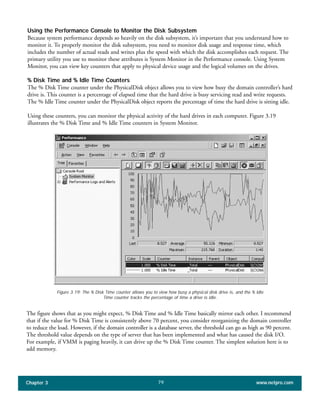
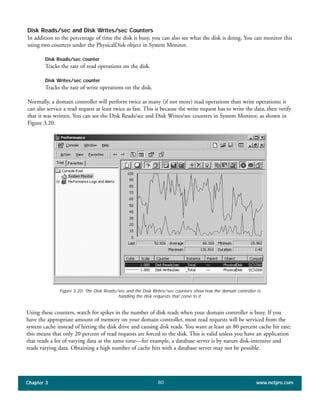
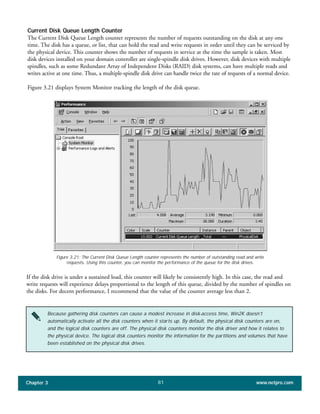
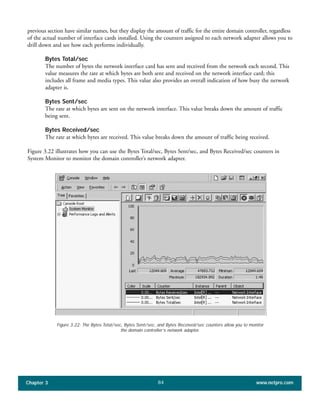
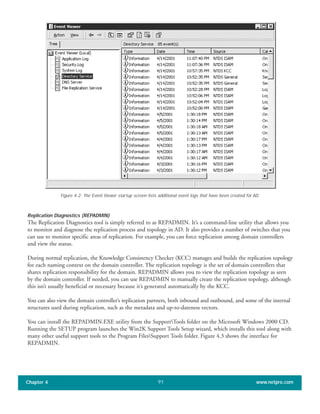
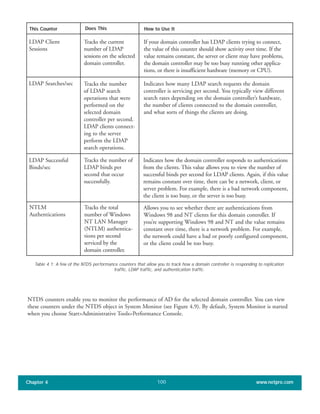
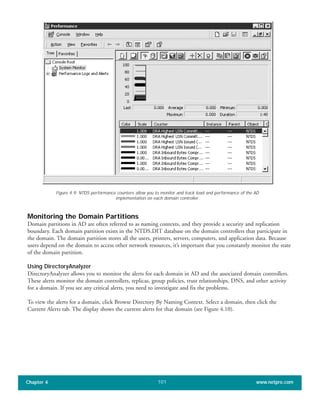
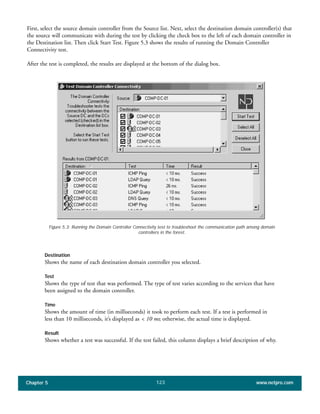
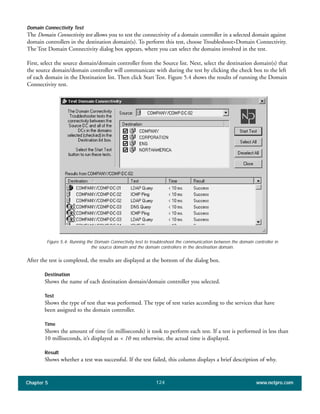
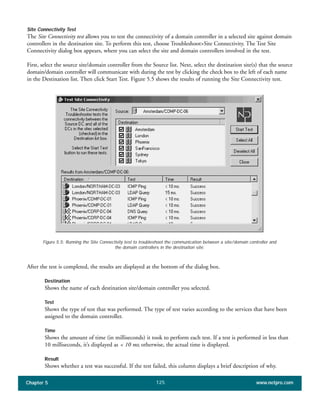
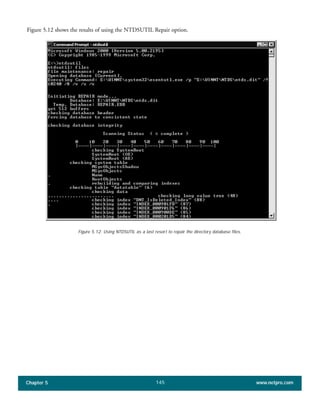
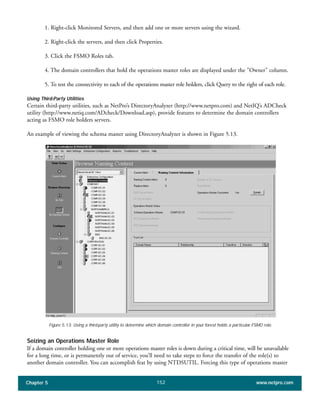
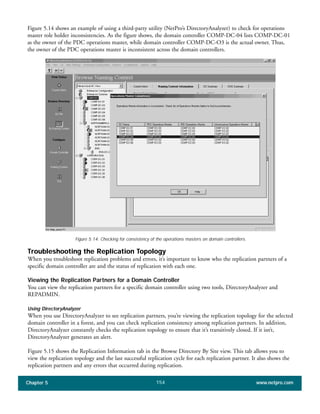
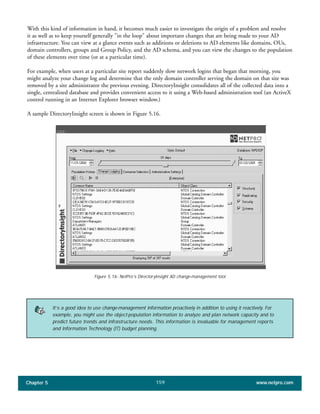
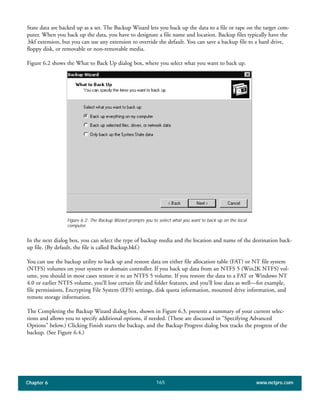
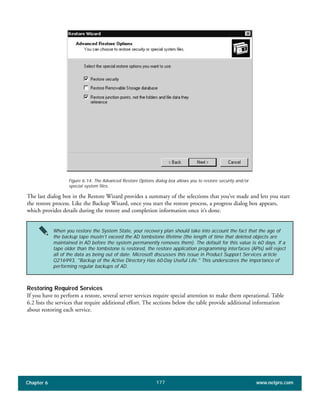
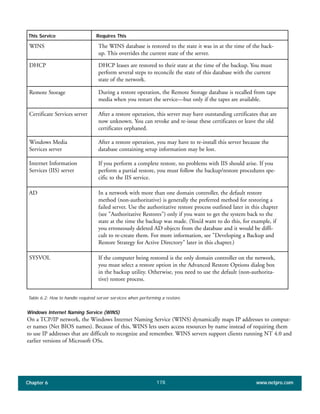
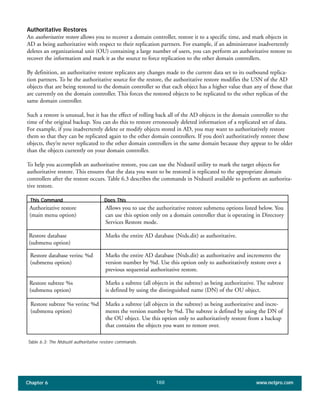
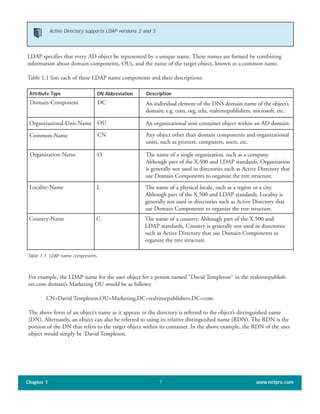
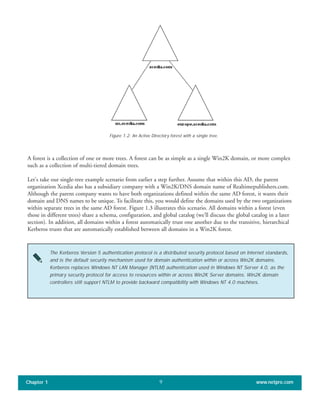
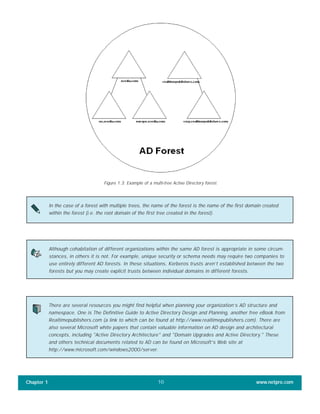
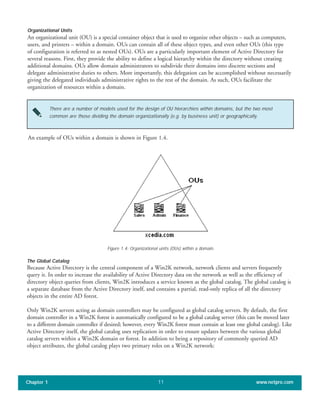
The document discusses the key features of Active Directory (AD) in Windows 2000. It explains that AD represents a significant change from previous directory services by supporting unprecedented scale through features like multi-master replication, sites, and global catalogs. It also notes that while AD's various components generally work well together, occasional issues will arise due to its complexity, requiring administrators to understand how all the parts fit together to quickly troubleshoot problems.


















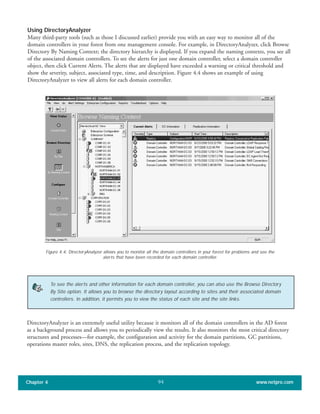
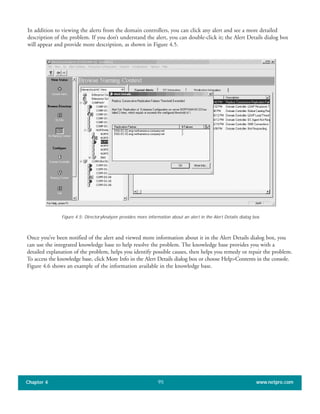
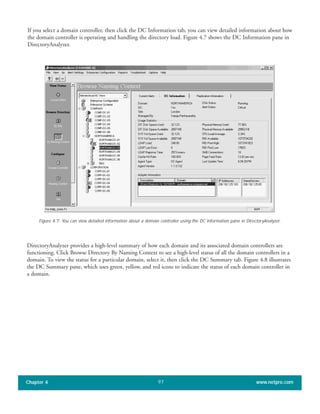
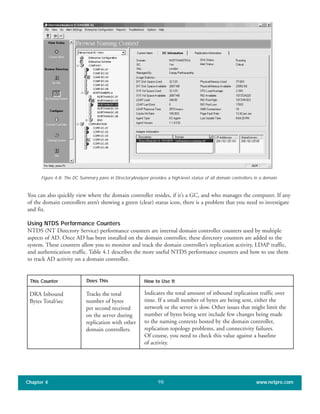
![When you use the Active Directory Installation Wizard to create the first domain in a new forest, all five of the
]single master operations roles are automatically assigned to the first domain controller in that domain. In a small
Active Directory forest with only one domain and one domain controller, that domain controller continues to own
all the operations master roles. In a larger network, whether with one or multiple domains, you can re-assign these
roles to one or more of the other domain controllers.
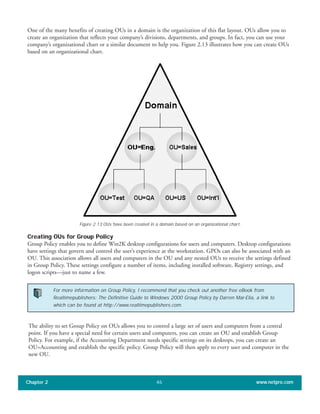
The two forest-specific operations master roles are listed below:
Schema master
The domain controller that serves the schema master role is responsible for all updates and modifications to
the forest-wide Active Directory schema. The schema defines every type of object and object attribute that
can be stored within the directory. Modifications to a forest’s schema can only be done by members of the
Schema Administrators group, and can be done only on the domain controller that holds the schema master role.
Domain naming master
The domain controller elected to the domain naming master role is responsible for making changes to the
forest-wide domain name space of the Active Directory. This domain controller is the only one that can add
or remove a domain from the directory, or add/remove references to domains in external directories.
The three domain-specific operations master roles are as follows:
PDC emulator
If a Win2K domain contains non-AD-enabled clients or is a mixed-mode domain containing Windows NT
backup domain controllers (BDCs), the PDC emulator acts as a Windows NT primary domain controller
(PDC) for these systems. In addition to replicating the Windows NT-compatible portion of directory
updates to all BDCs, the PDC emulator is also responsible for time synchronization on the network (which
is important for Win2K’s Kerberos security mechanism), and processing account lockouts and client pass
word changes.
RID master
The RID (relative ID) master allocates sequences of RIDs to each domain controller in its domain.
Whenever a Win2K domain controller creates an object such as a user, group, or computer, that object must
be assigned a unique security identifier (SID). A SID consists of a domain security ID (this is identical for all
SIDs within a domain), and a RID. When a domain controller has exhausted its internal pool of RIDs, it
requests another pool from the RID Master domain controller.
Infrastructure master
When an object in one domain is referenced by an object in another domain, it represents the reference by
the Globally Unique IDentifier (GUID), the Security IDentifier (SID – for objects that reference security
principals), and the Distinguished Name (DN) of the object being referenced. The infrastructure master is
the domain controller responsible for updating an object's SID and distinguished name in a cross-domain
object reference. The infrastructure master is also responsible for updating all inter-domain references any
time an object referenced by another object moves (for example, whenever the members of groups are
renamed or changed, the infrastructure master updates the group-to-user references). The infrastructure master
distributes updates using multi-master replication. Note: except where there is only one domain controller in
a domain, never assign the infrastructure master role to the domain controller that is also acting as a global
catalog server. If you use a global catalog server, the infrastructure master will not function properly.
Specifically, the effect will be that cross-domain object references in the domain will not be updated. In a
Chapter 1 www.netpro.com14](https://image.slidesharecdn.com/completeadtroubleshooting-181017140120/85/Complete-ad-troubleshooting-24-320.jpg)