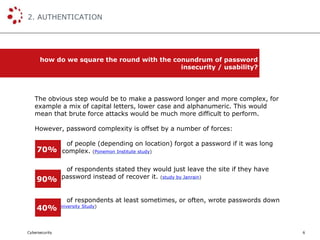
The document discusses the balance between usability and security, particularly in the context of the USP Secure Entry Server (SES). It highlights that good usability can enhance security, emphasizing the need for thoughtful design and better tools to achieve an optimal user experience while maintaining security measures. The document also details the SES's features, such as single sign-on and web application firewalls, which facilitate this balance and address common cybersecurity challenges.