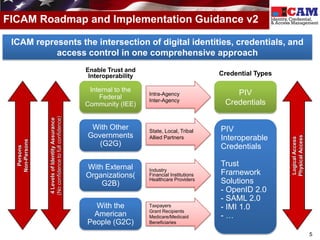
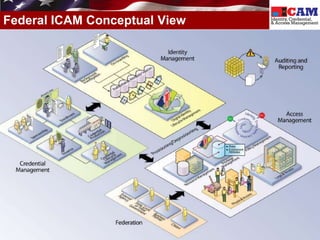
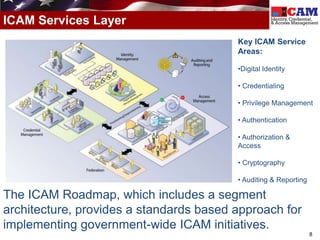
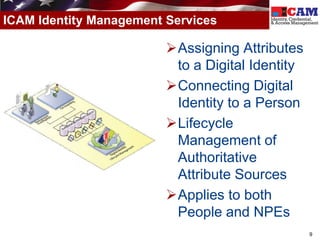
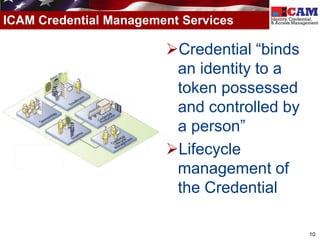
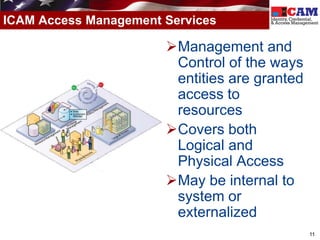
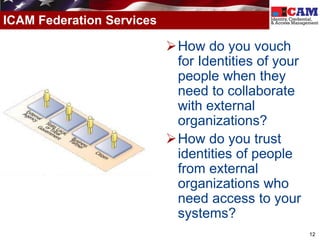
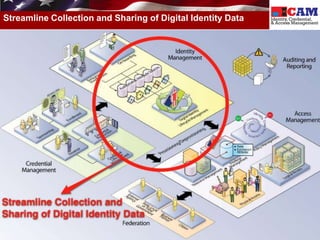
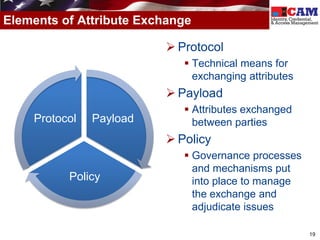
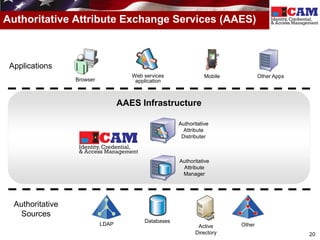
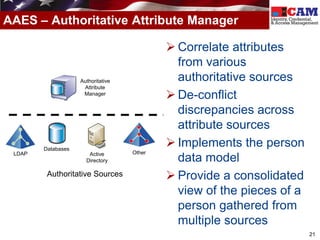
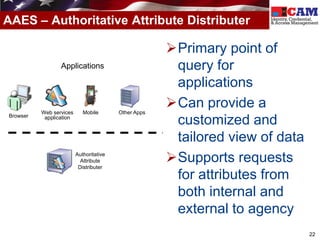
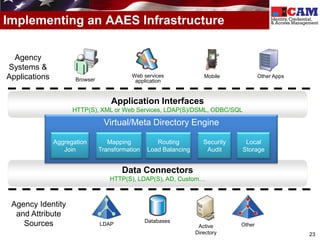
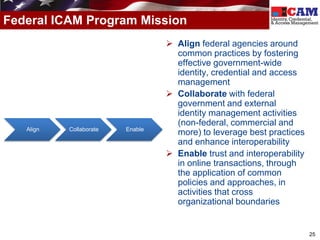
The document discusses the Federal Identity, Credential, and Access Management (FICAM) program. It provides an overview of FICAM, including its goals of complying with laws, facilitating e-government access, improving security, enabling trust and interoperability, and reducing costs. It outlines several FICAM initiatives, such as streamlining the collection and sharing of digital identity data and fully leveraging Personal Identity Verification credentials. The document emphasizes FICAM's mission to align agencies, collaborate with external partners, and enable trust and interoperability across organizational boundaries through common identity management policies and practices.