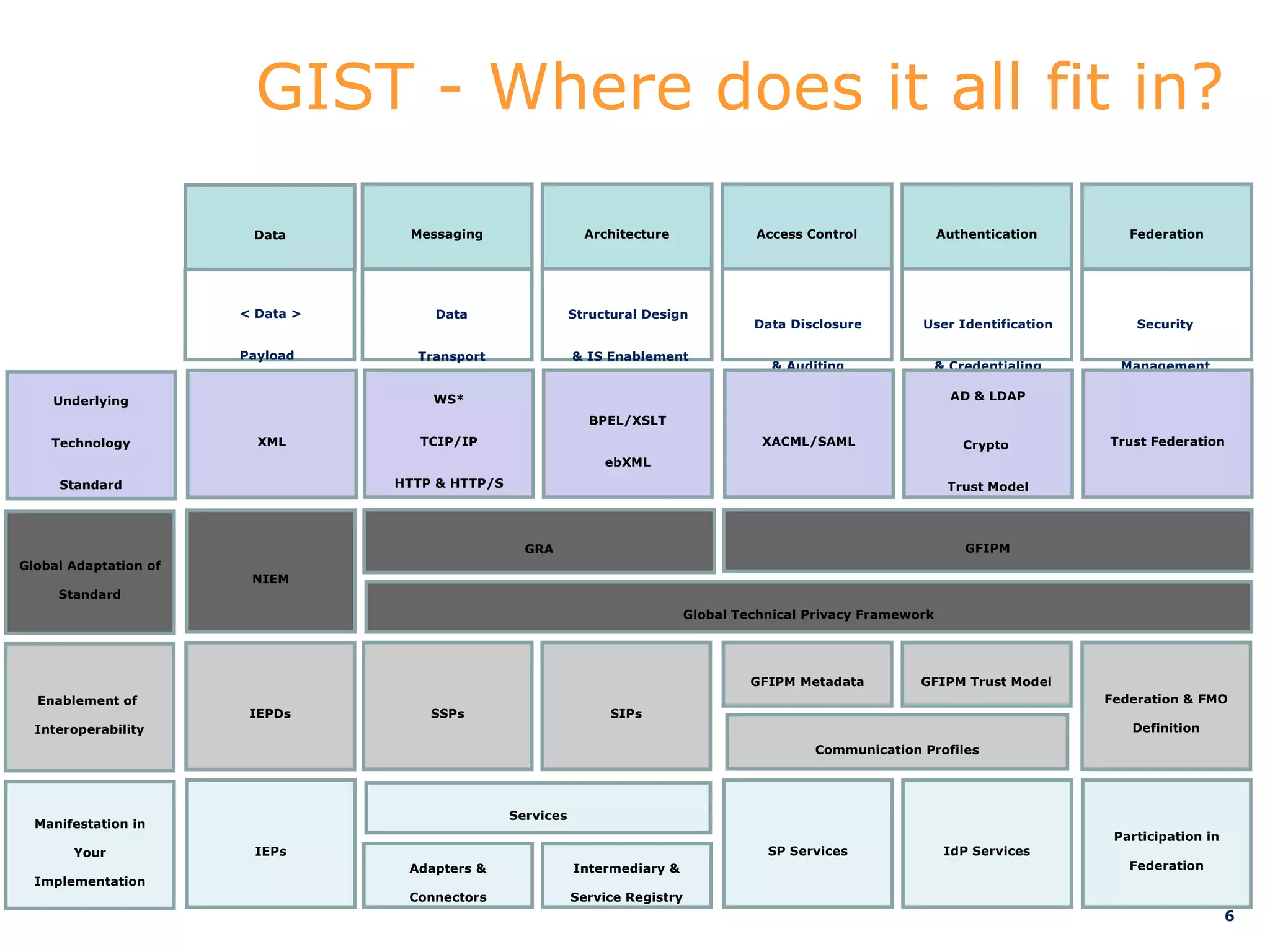
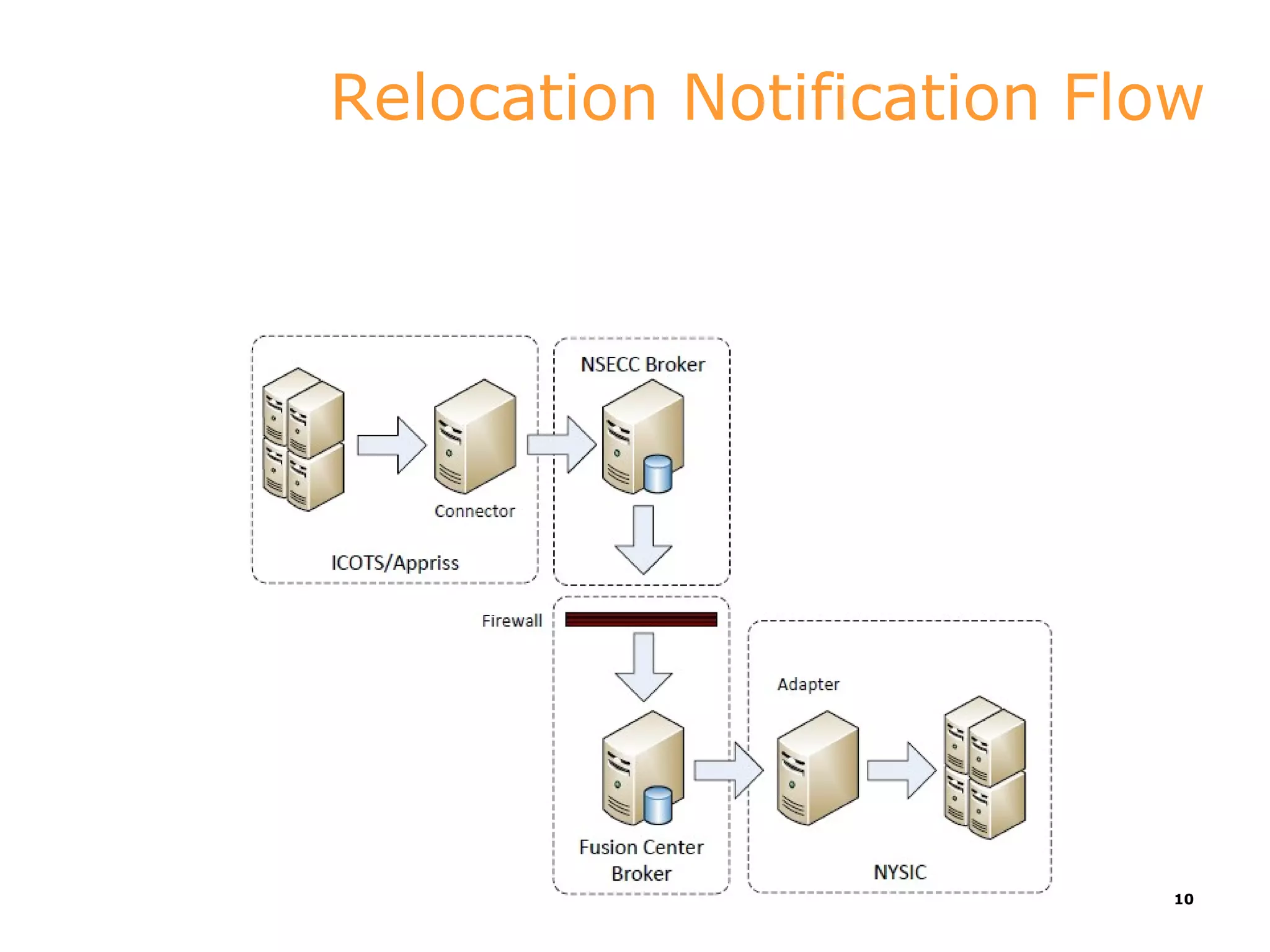
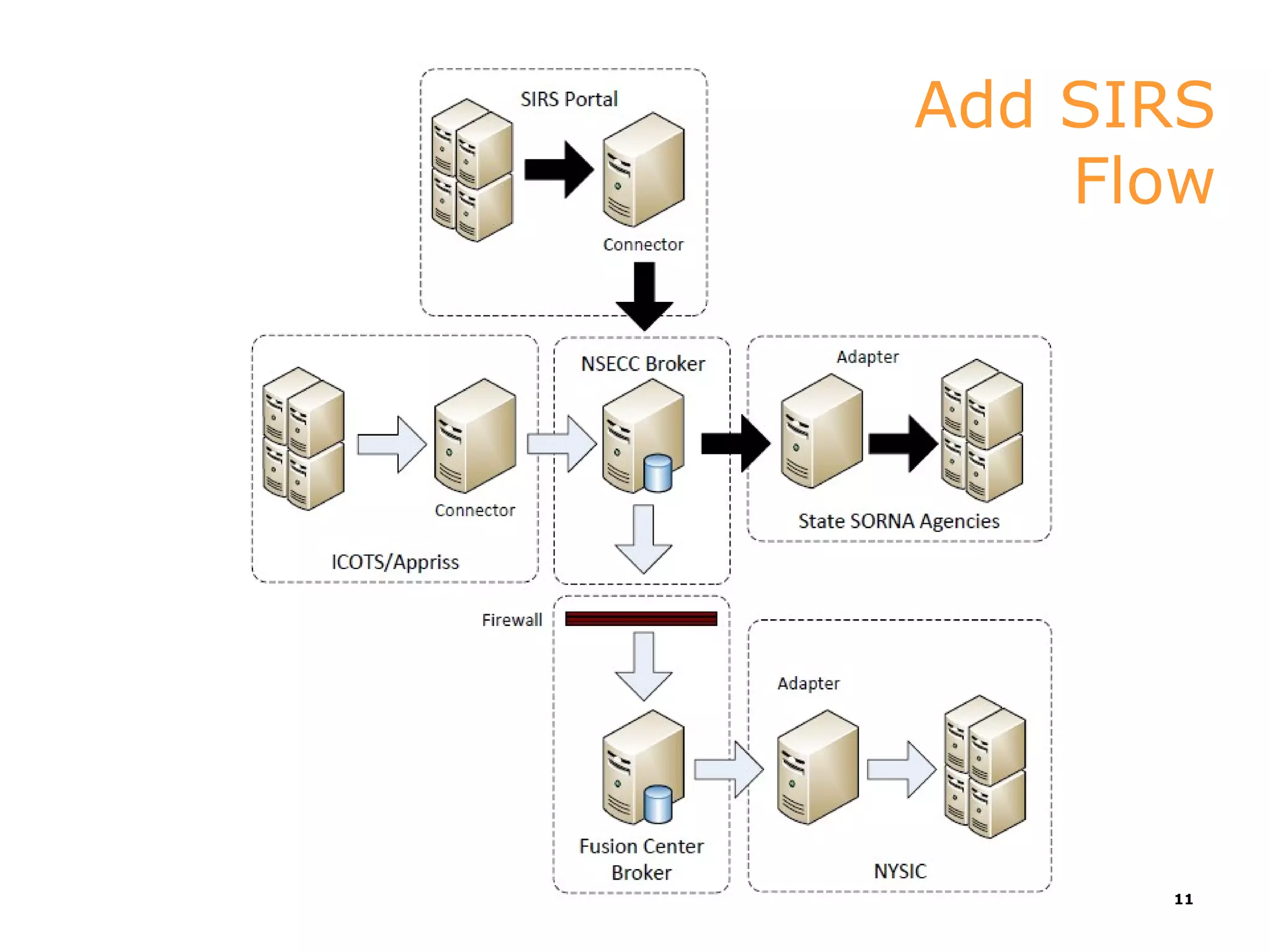
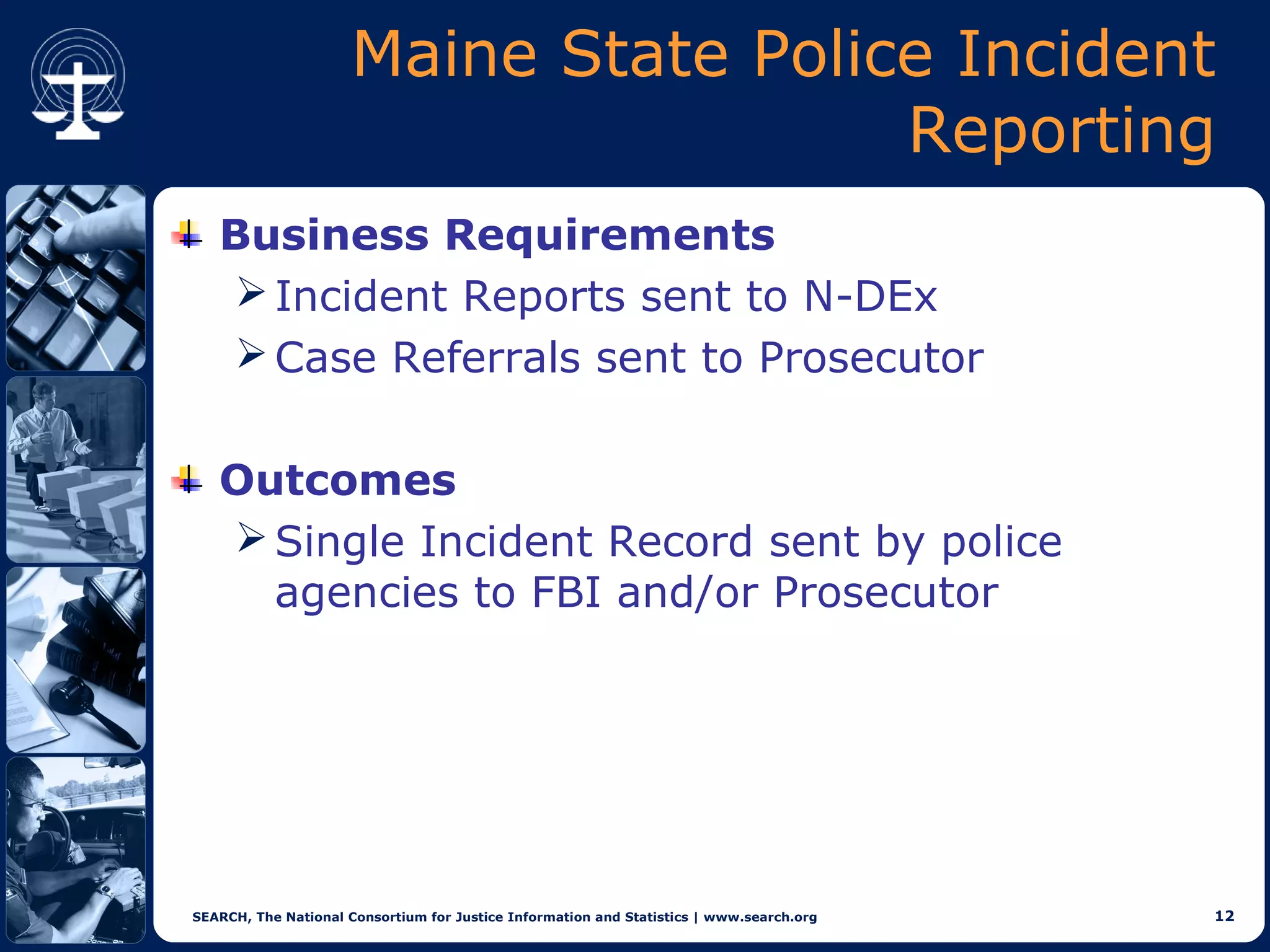
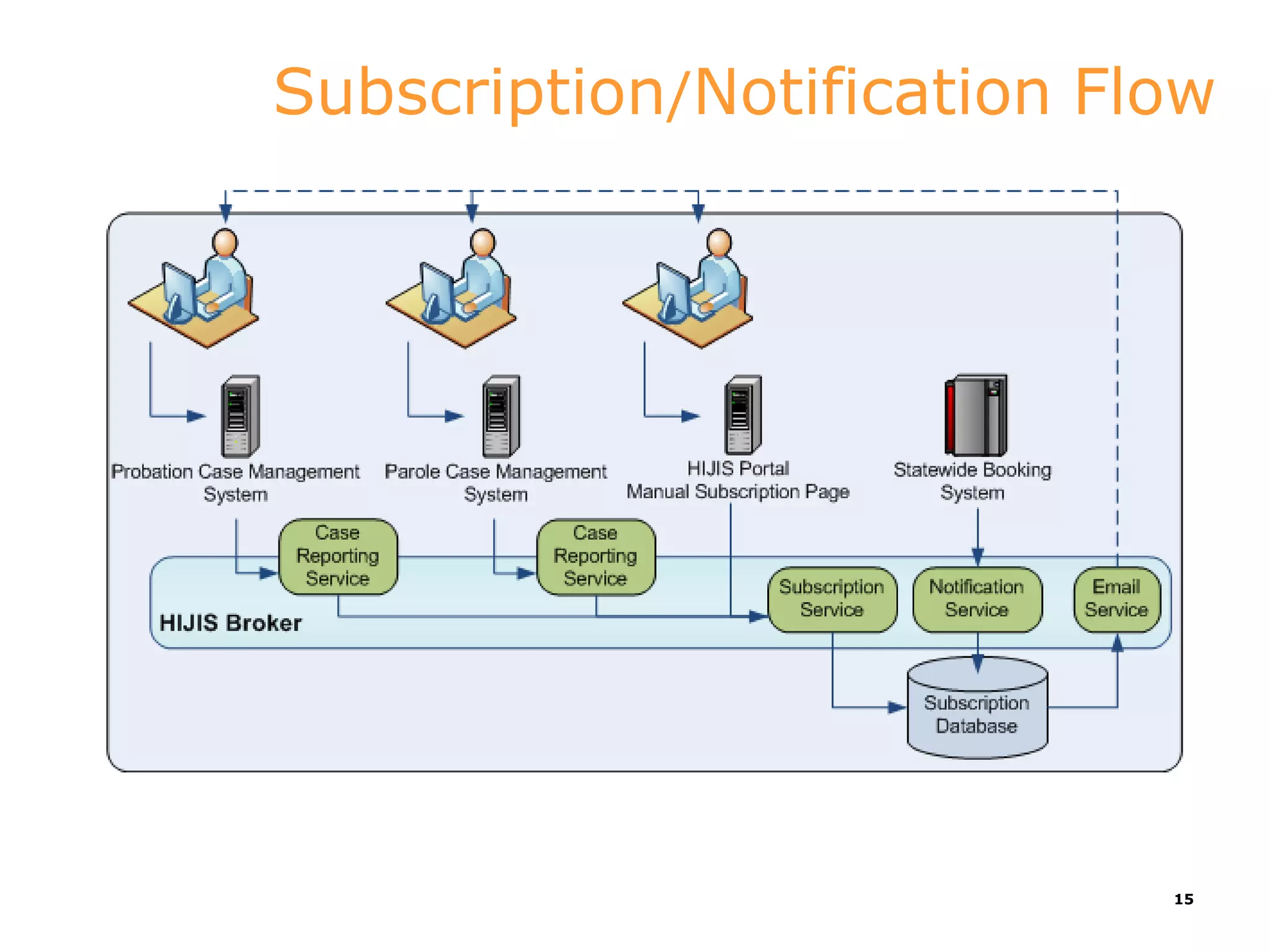
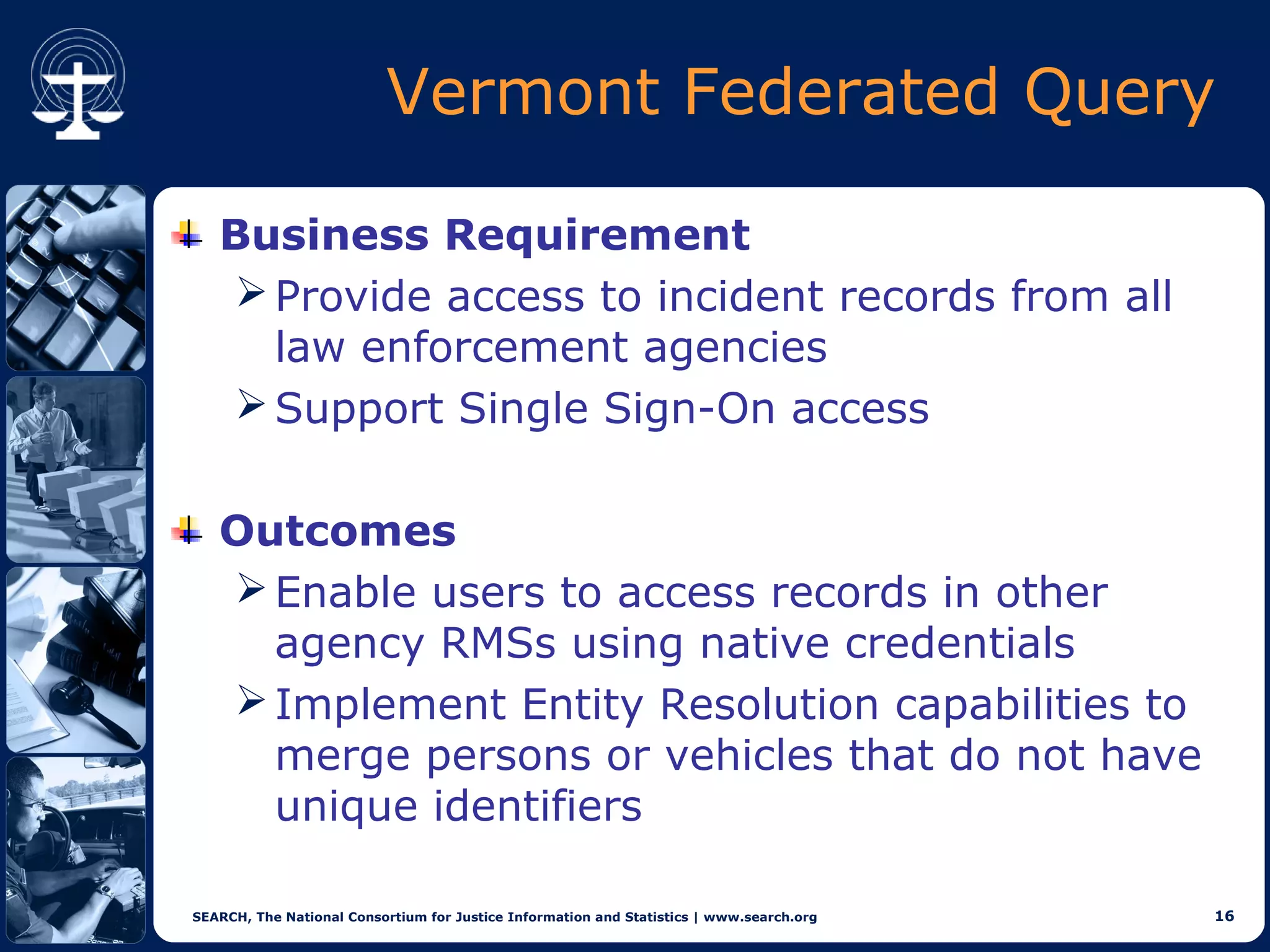
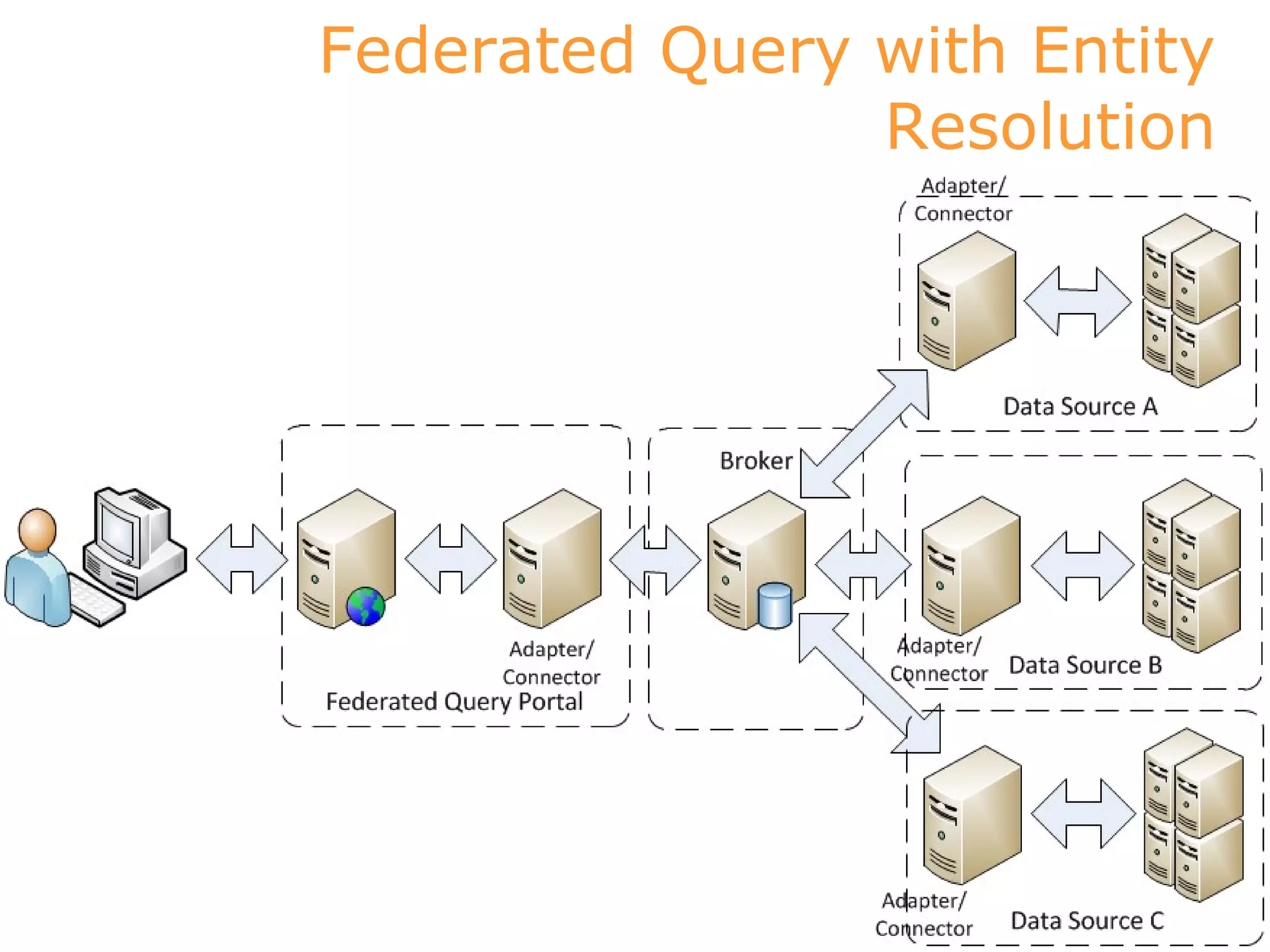
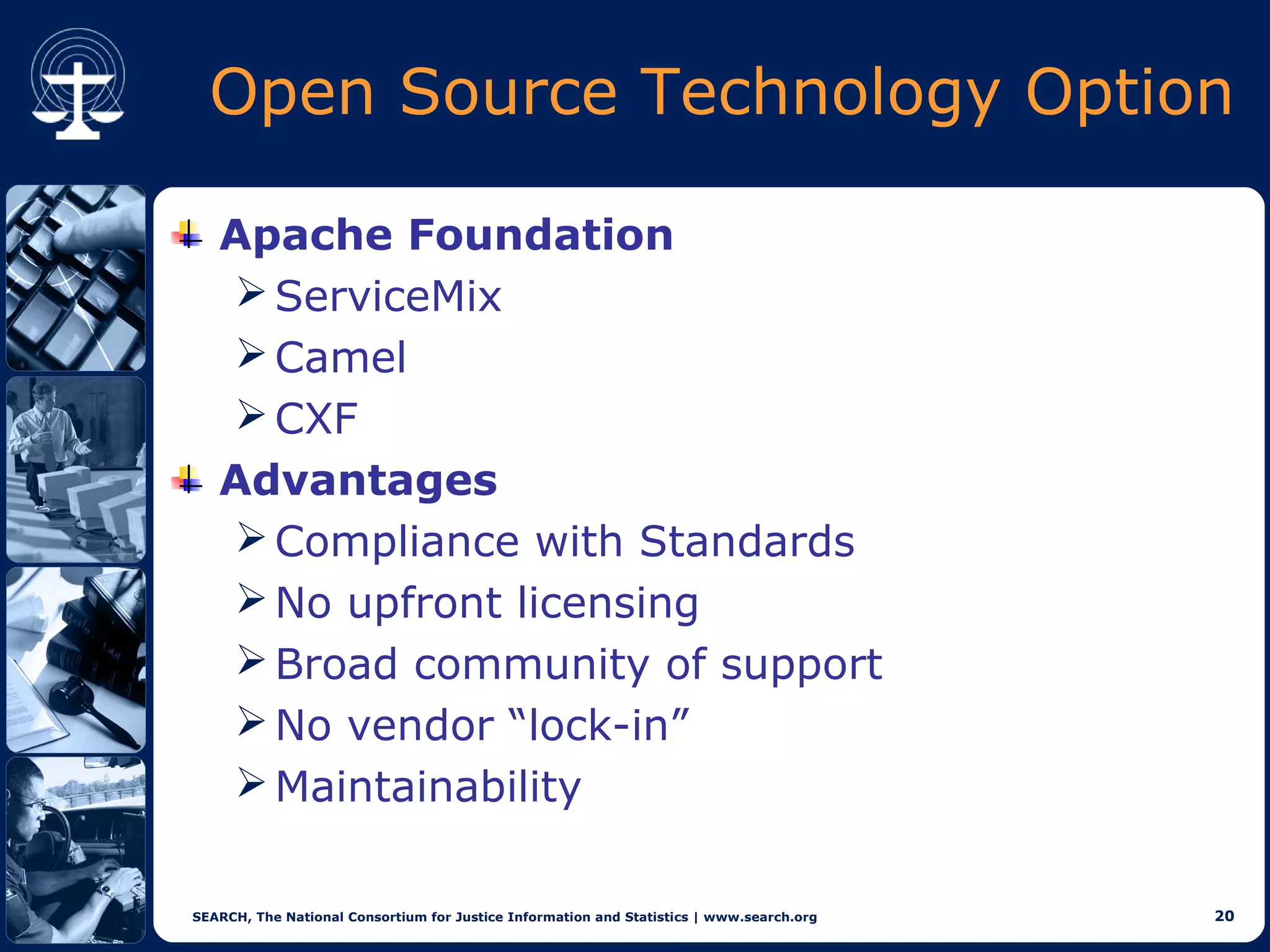
This document discusses implementations of global standards for information sharing using open source technologies. It describes projects in Maine, Hawaii, and Vermont that have adopted the Global Reference Architecture (GRA) and Global Federated Identity and Privilege Management (GFIPM) standards to build systems for notification services, incident reporting, and federated queries across agencies. These projects use open source technologies like Apache ServiceMix and Camel to build interoperable systems in a cost-effective and standards-compliant way. The document also introduces the Open Justice Brokerage Consortium (OJBC), a non-profit collaboration between states to support shared development and operations of these open systems.