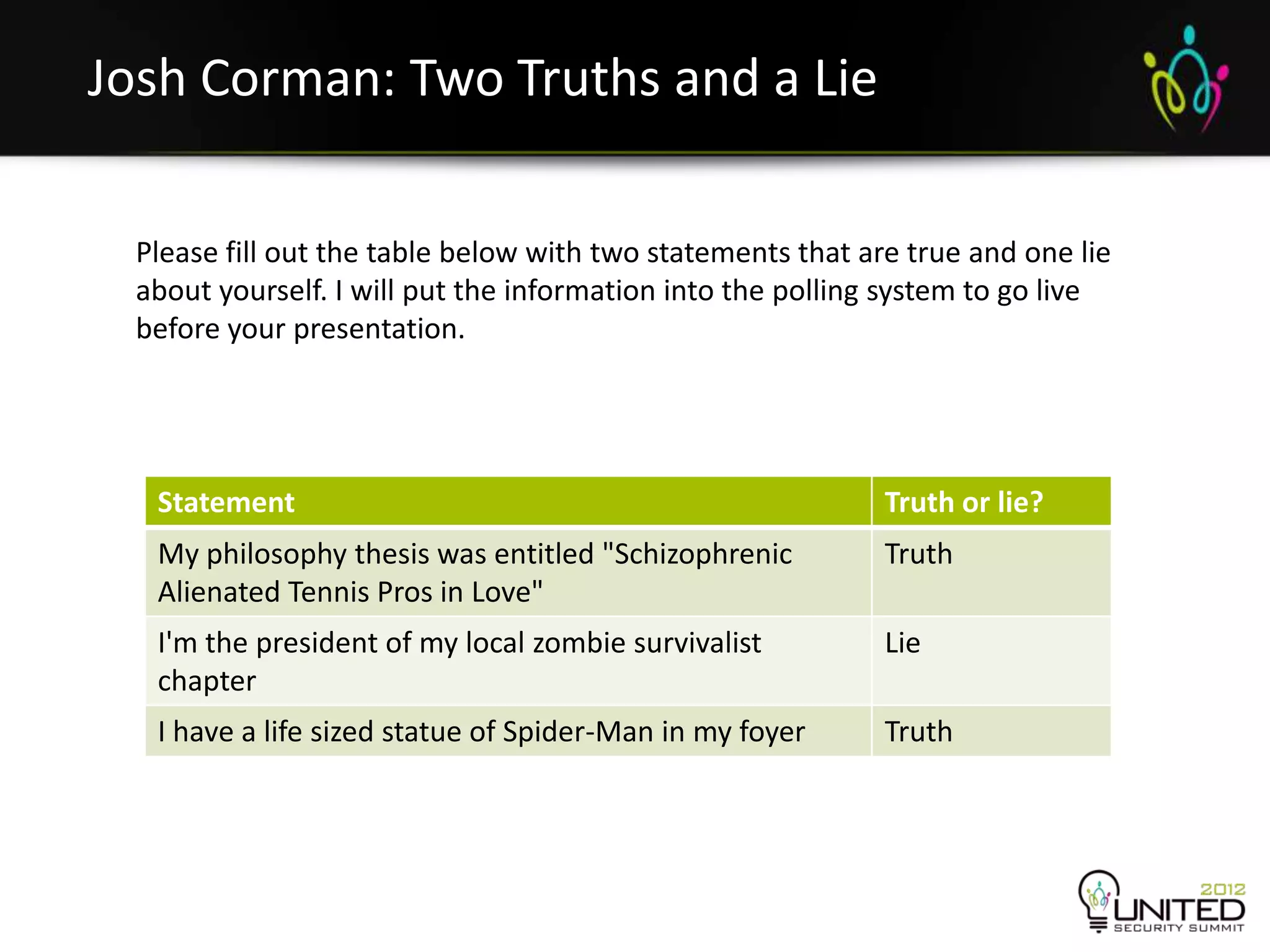
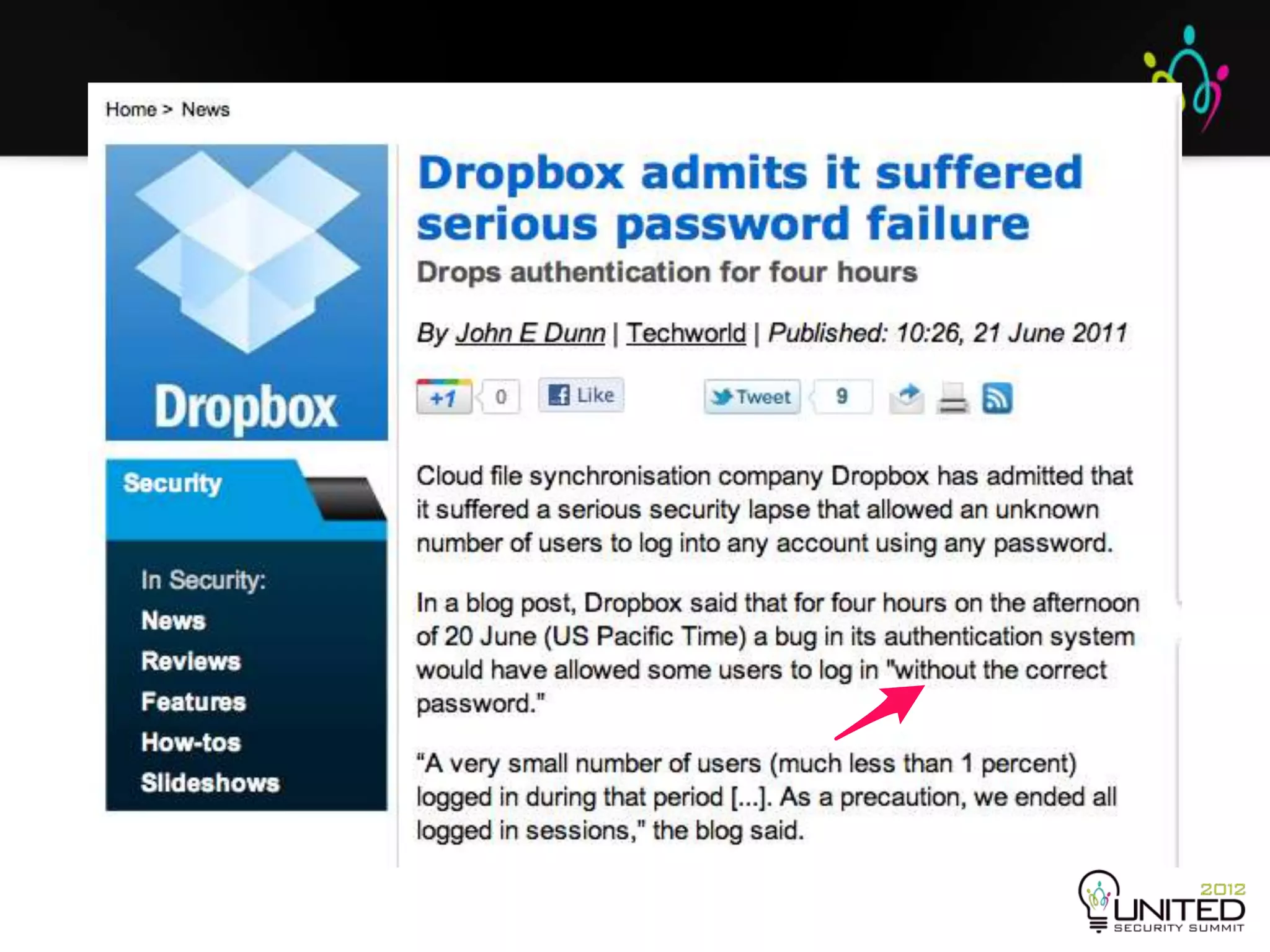
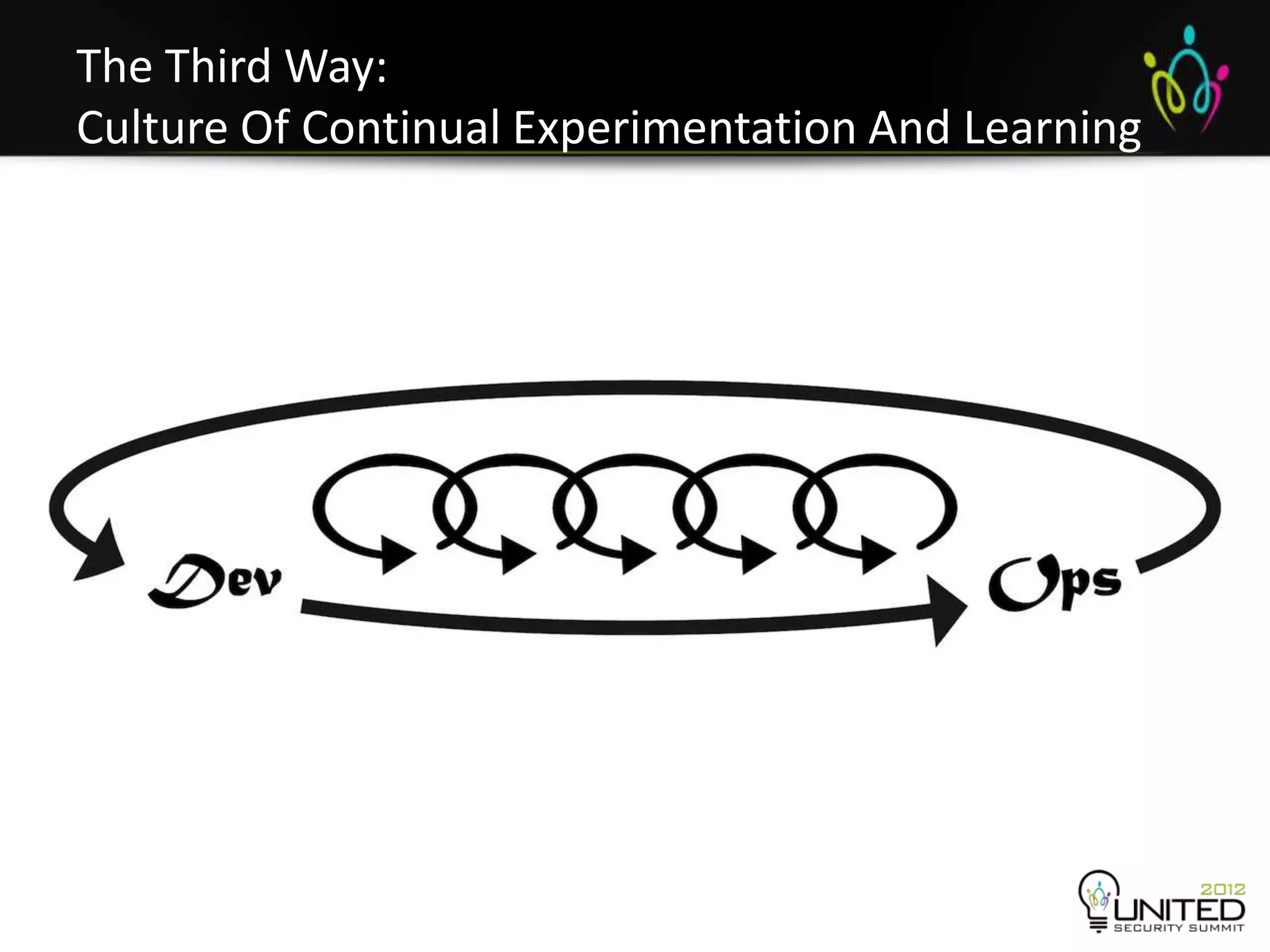
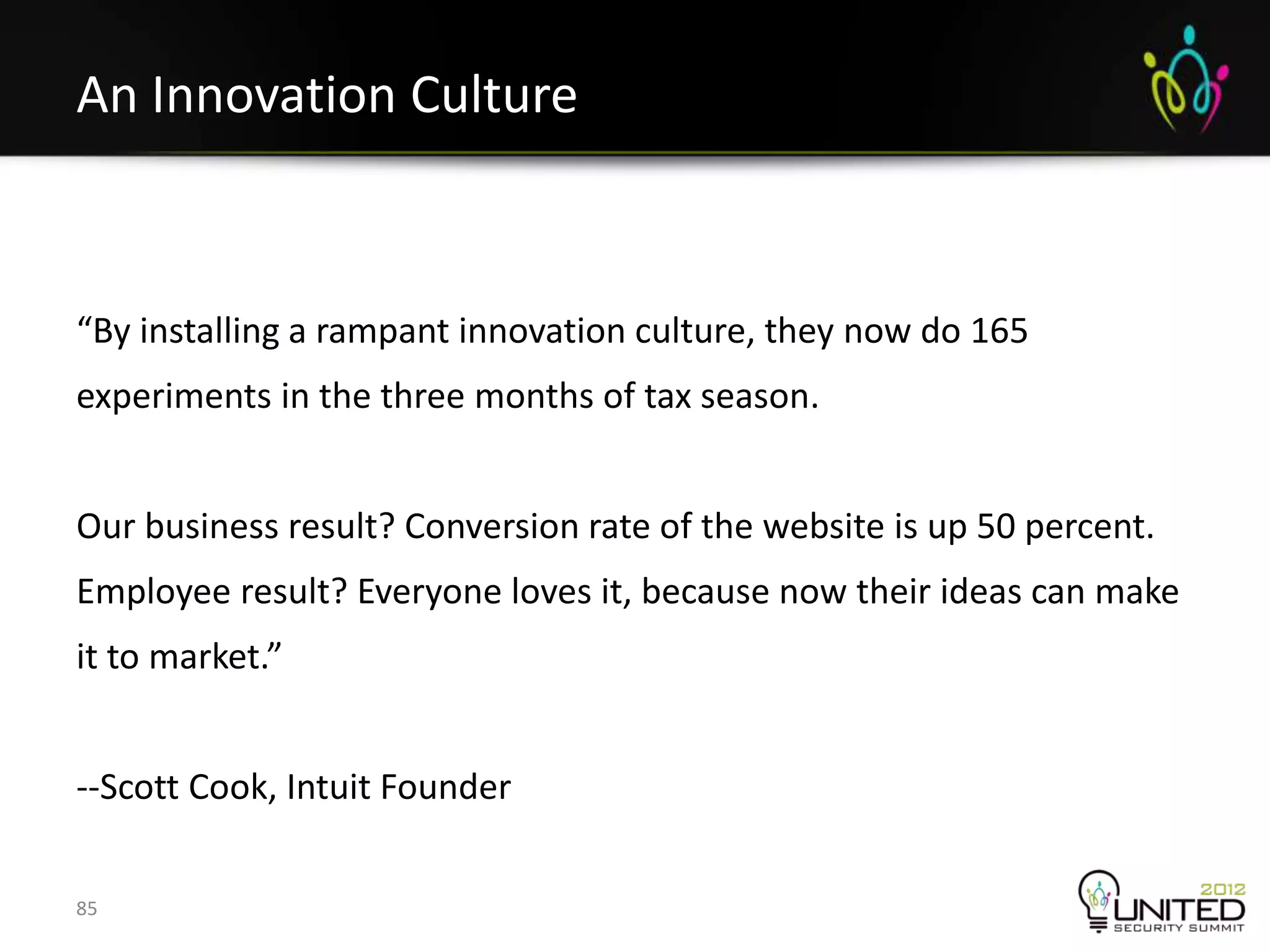
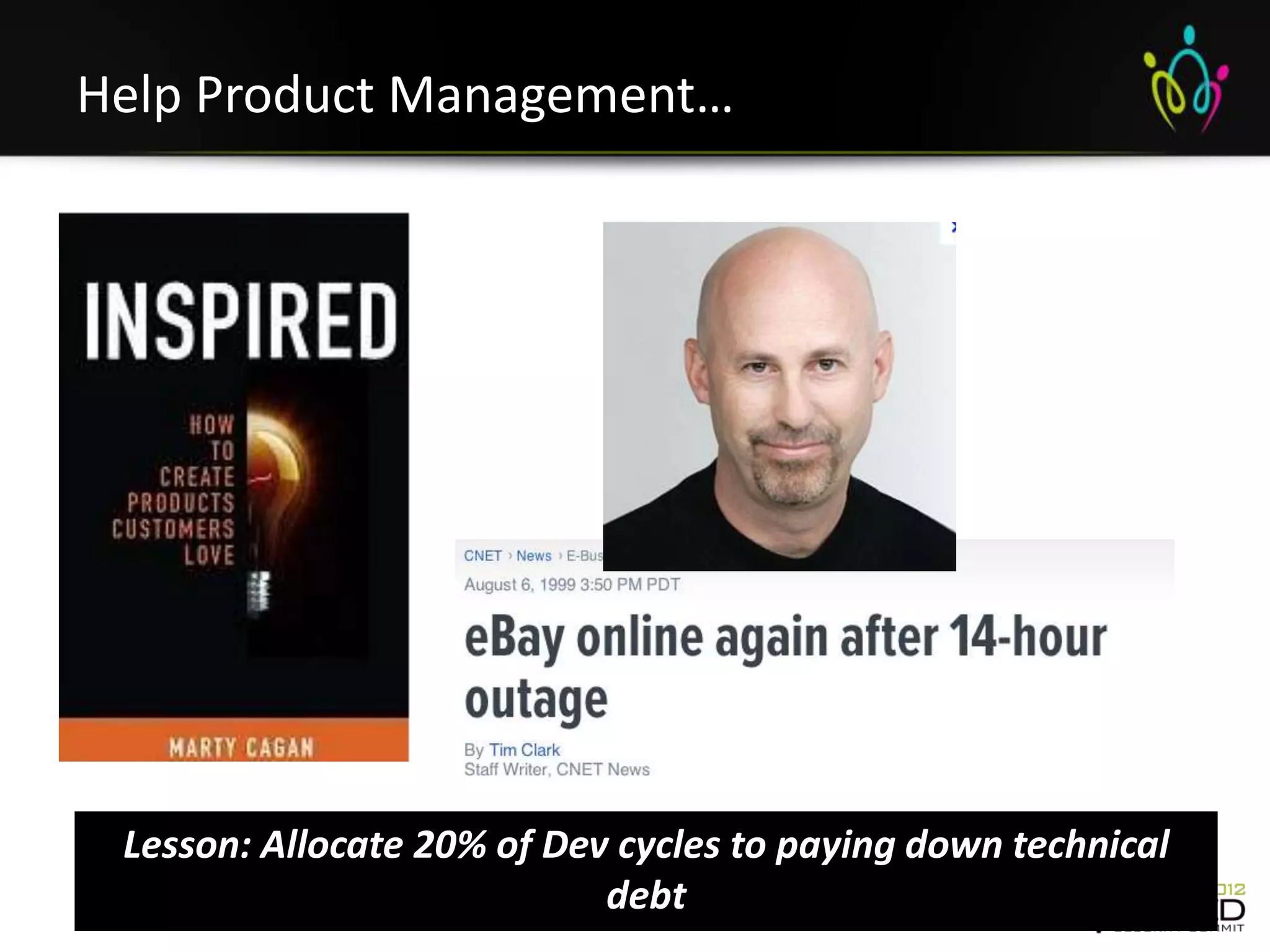
The document is a transcript from a presentation given by Joshua Corman and Gene Kim at a security conference in San Francisco in September 2012. The presentation discusses the problems with current security practices, introduces the concepts of DevOps and Rugged DevOps, and provides three ways ("systems thinking", "amplifying feedback loops", and "culture of continual experimentation") to implement Rugged DevOps practices to improve security. The overall message is that cultural and process changes are needed, not just technical fixes, to build more secure software.

![About Joshua Corman
• Director of Security Intelligence for Akamai Technologies
- Former Research Director, Enterprise Security [The 451 Group]
- Former Principal Security Strategist [IBM ISS]
• Industry:
- Expert Faculty: The Institute for Applied Network Security (IANS)
- 2009 NetworkWorld Top 10 Tech People to Know
- Co-Founder of “Rugged Software” www.ruggedsoftware.org
- BLOG: www.cognitivedissidents.com
• Things I’ve been researching:
- Compliance vs Security
- Disruptive Security for Disruptive Innovations
- Chaotic Actors
- Espionage
- Security Metrics
3](https://image.slidesharecdn.com/united2012ruggeddevopscormankimfinal-120914114407-phpapp01/75/United2012-Rugged-DevOps-Rocks-3-2048.jpg)