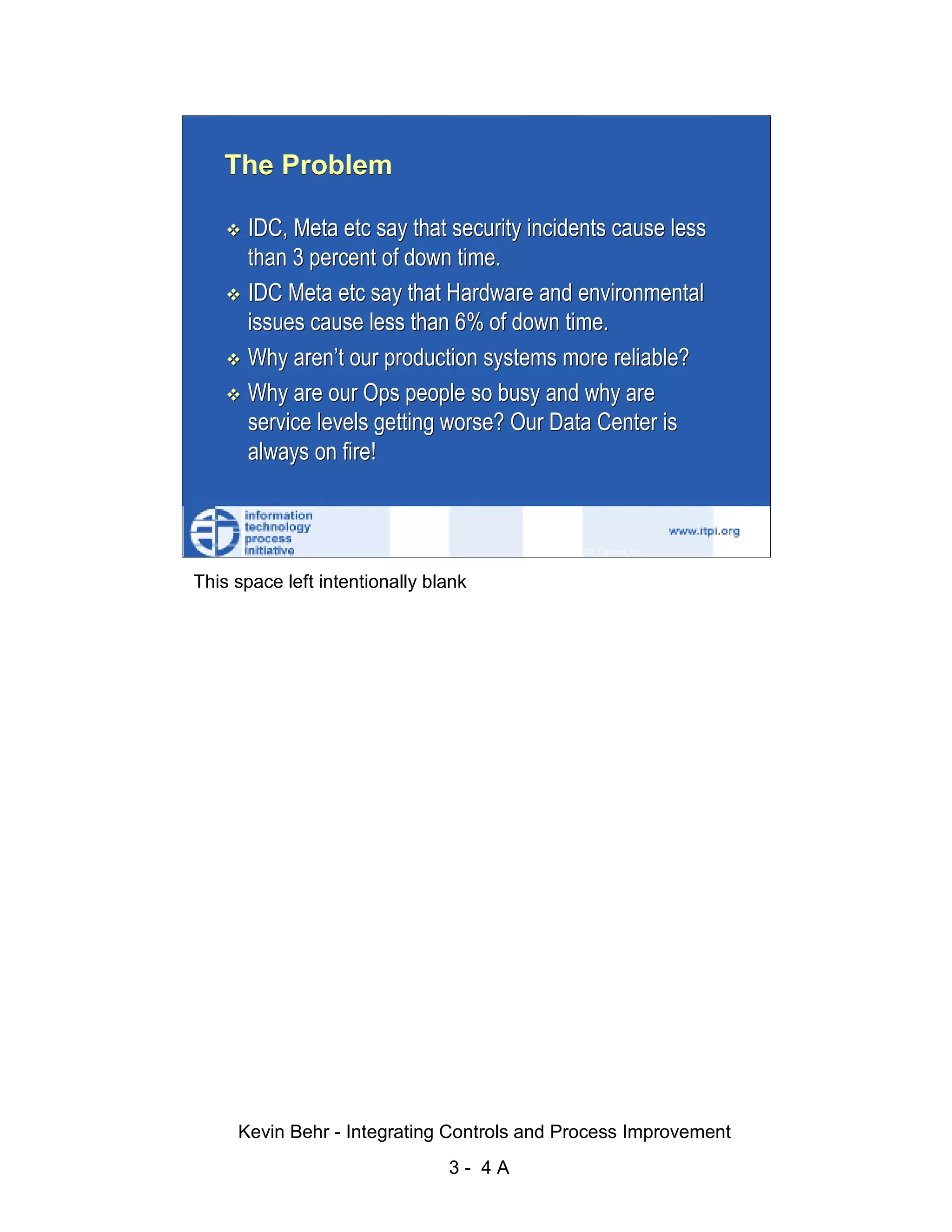
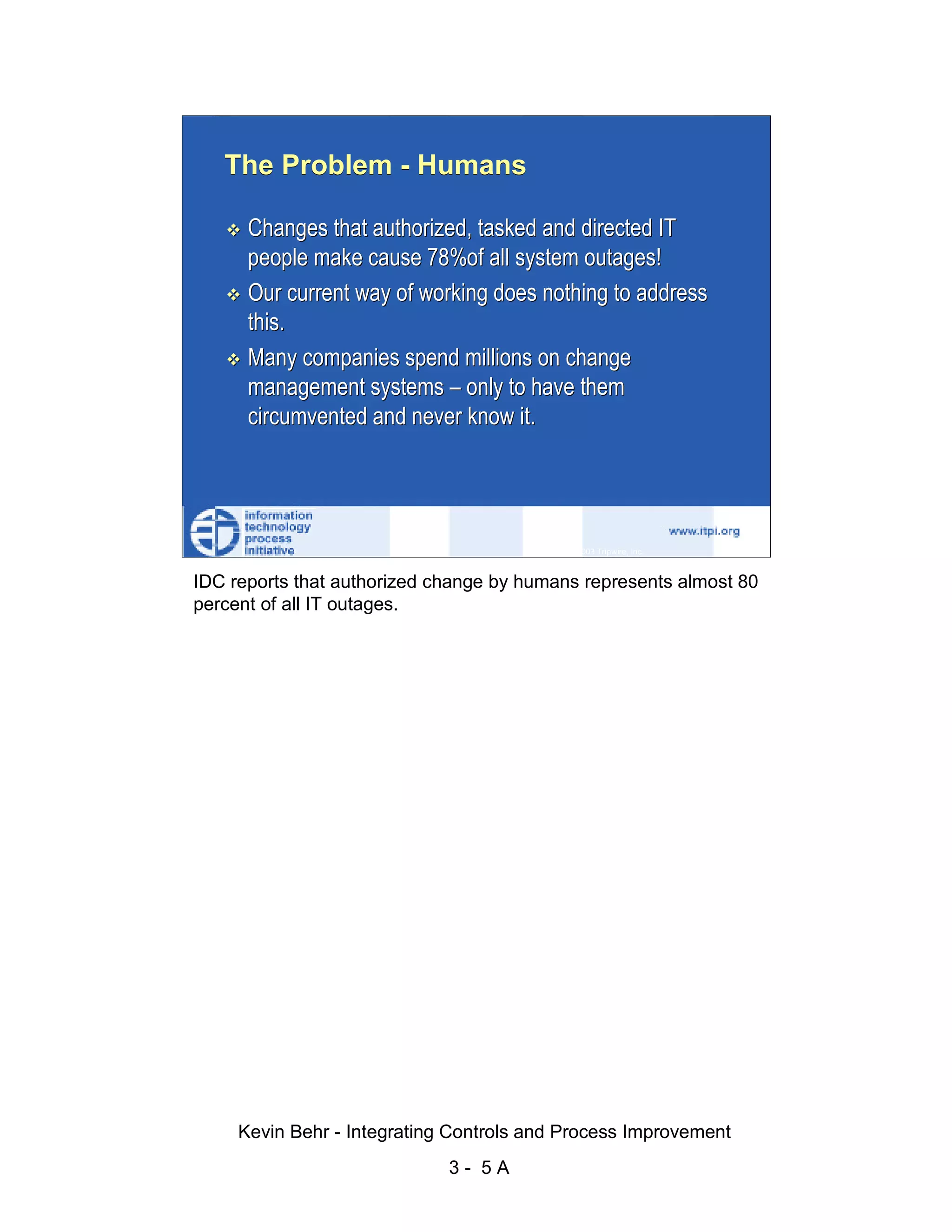
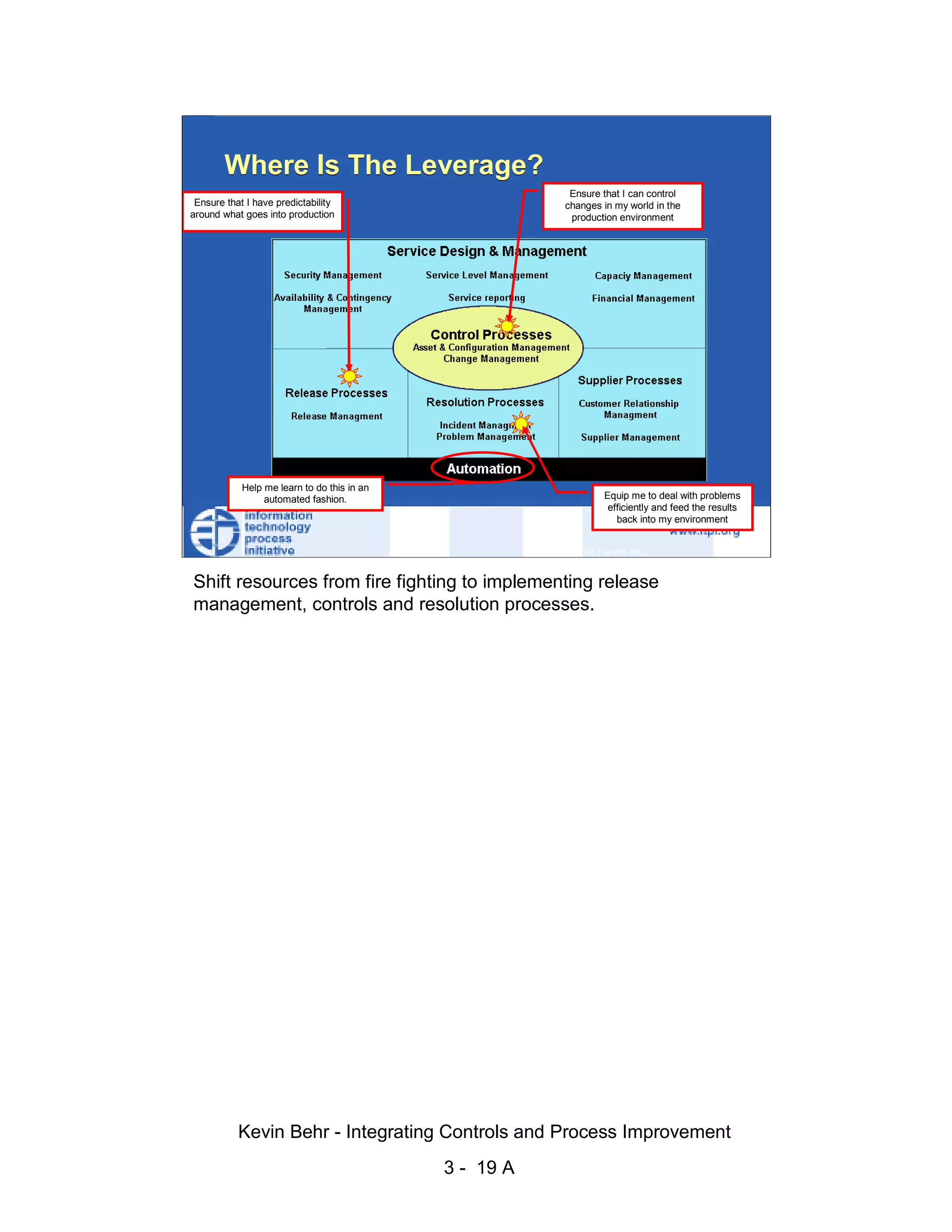
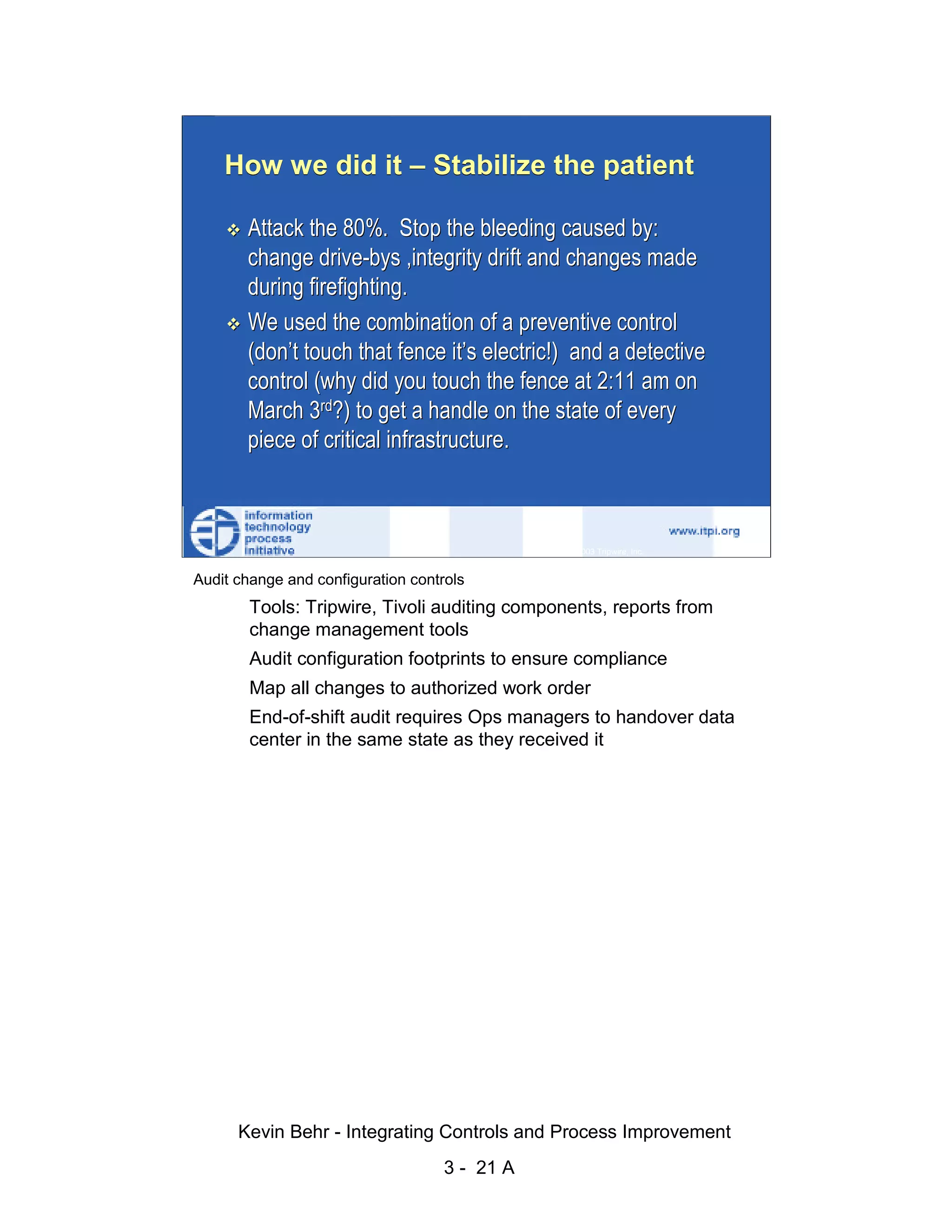
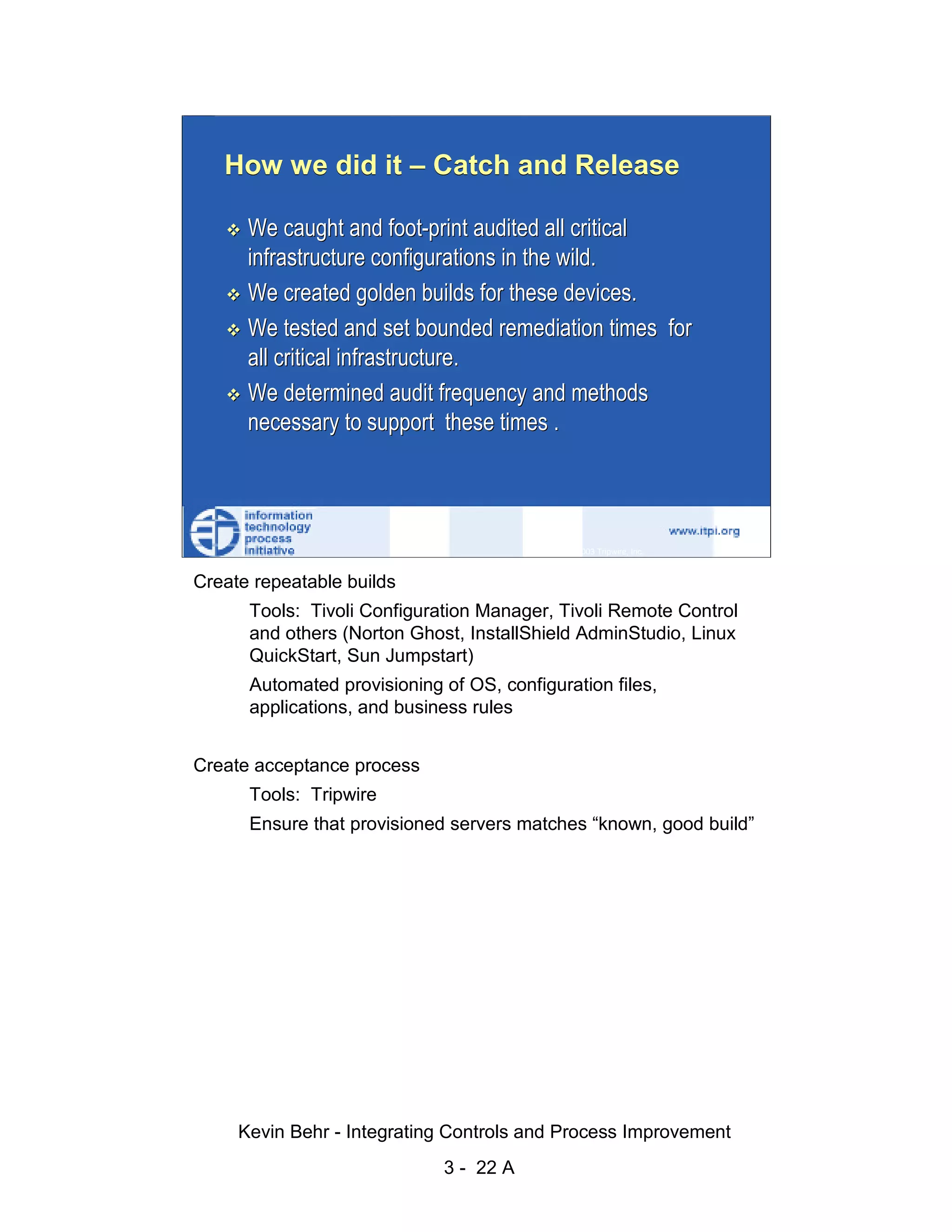
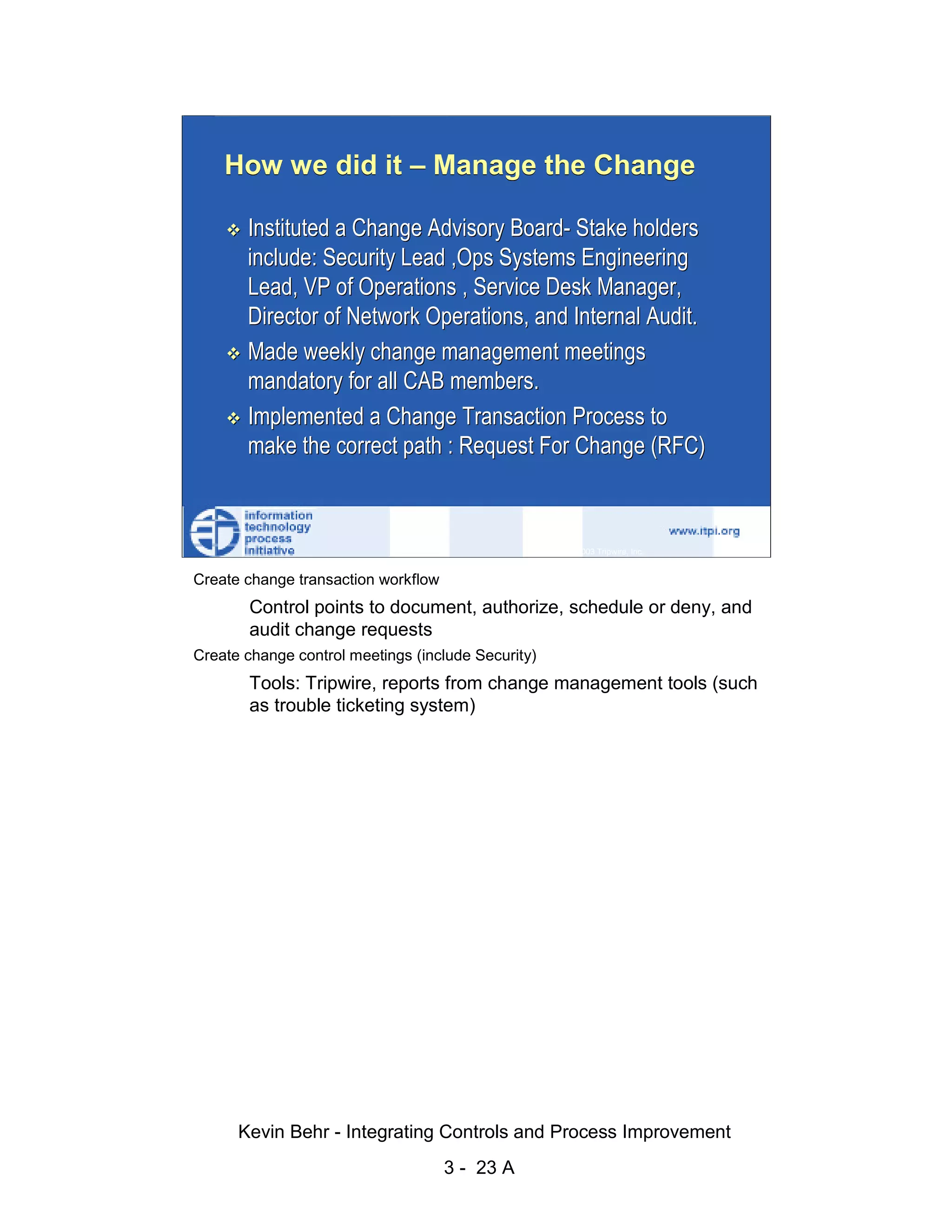
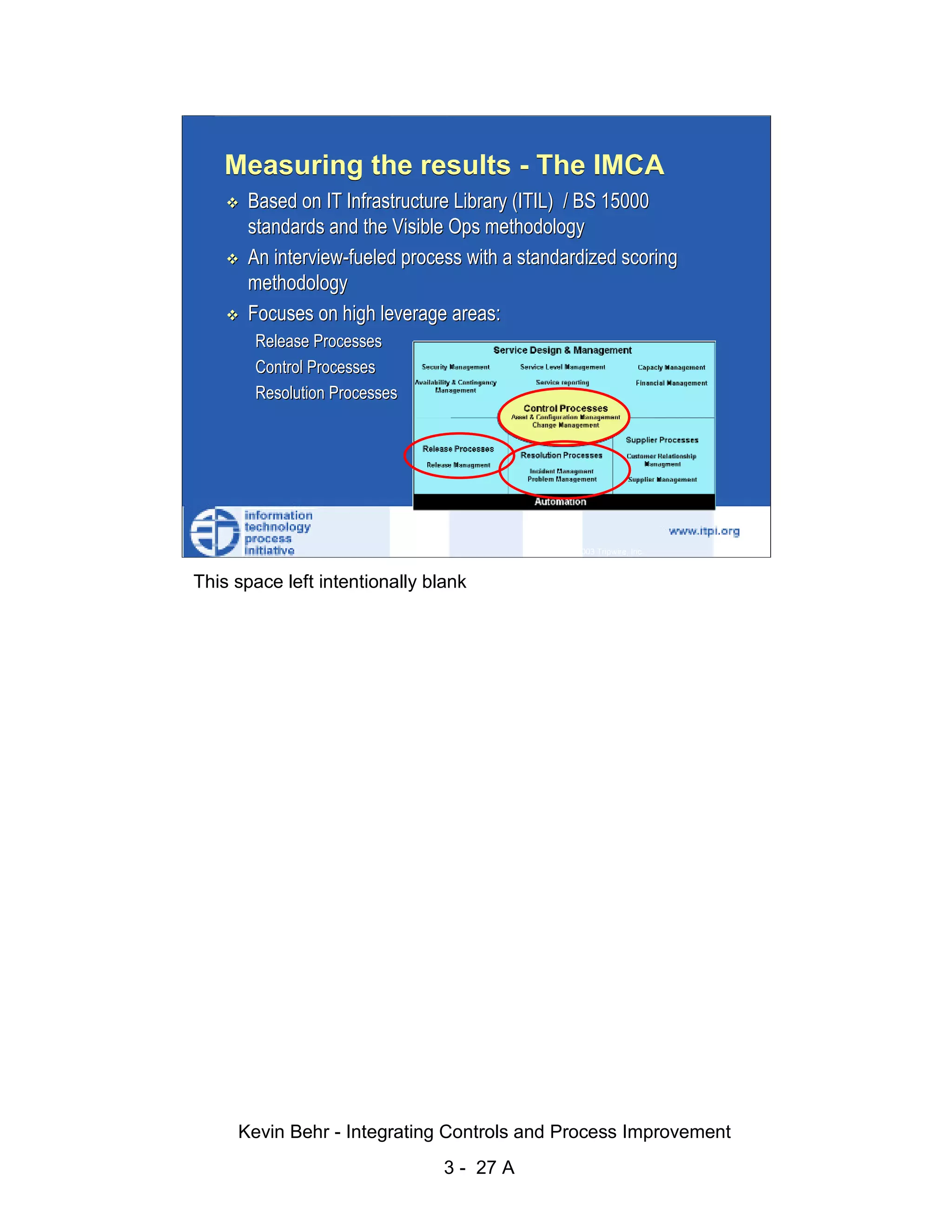
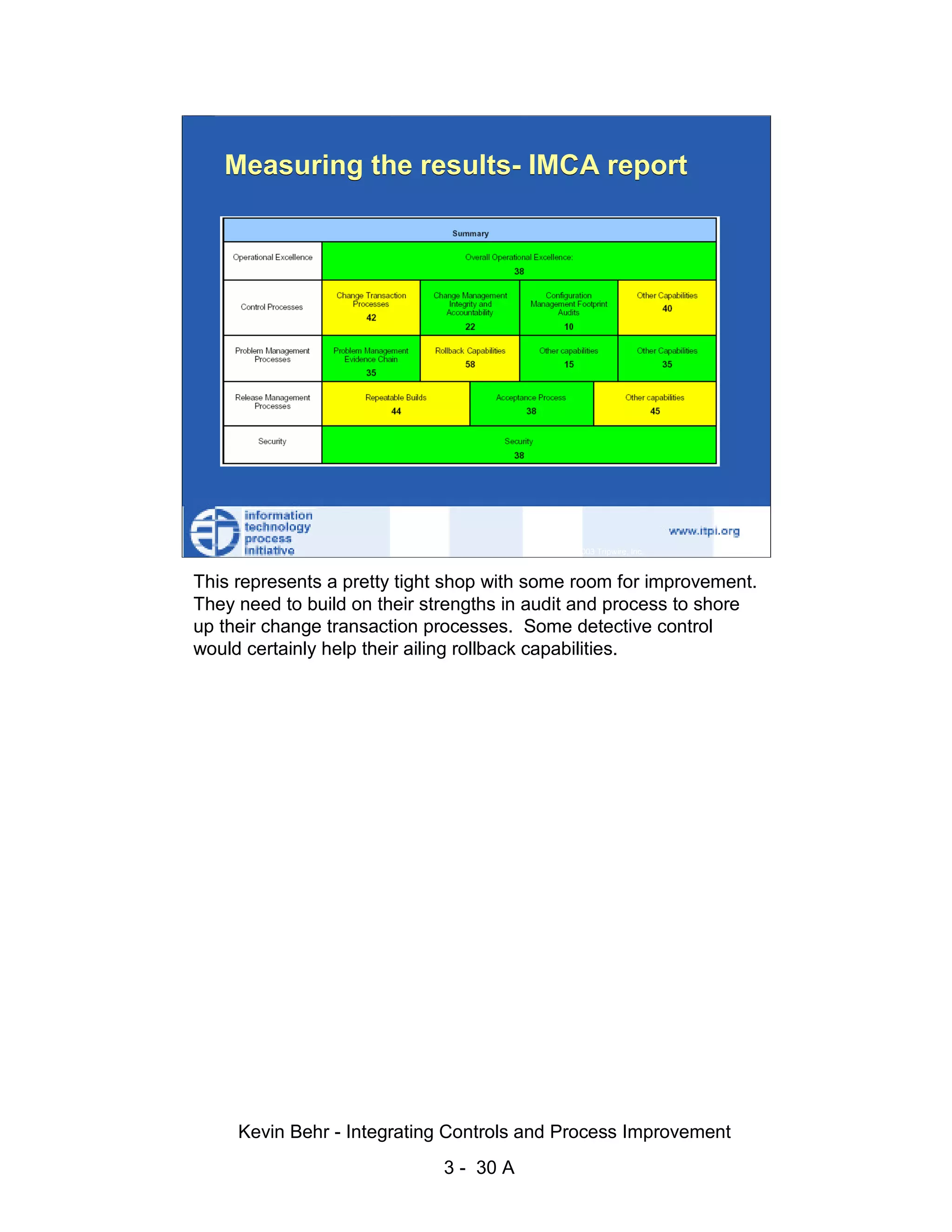
The document discusses integrating controls and process improvement. It notes that human-caused changes are responsible for 78% of system outages. The current approach does little to address this problem. The organization implemented a framework called ITIL and methodology called Visible Ops to better integrate controls and improve processes. This aims to increase operational efficiencies, service levels, and reduce problem resolution times through preventative and detective controls.