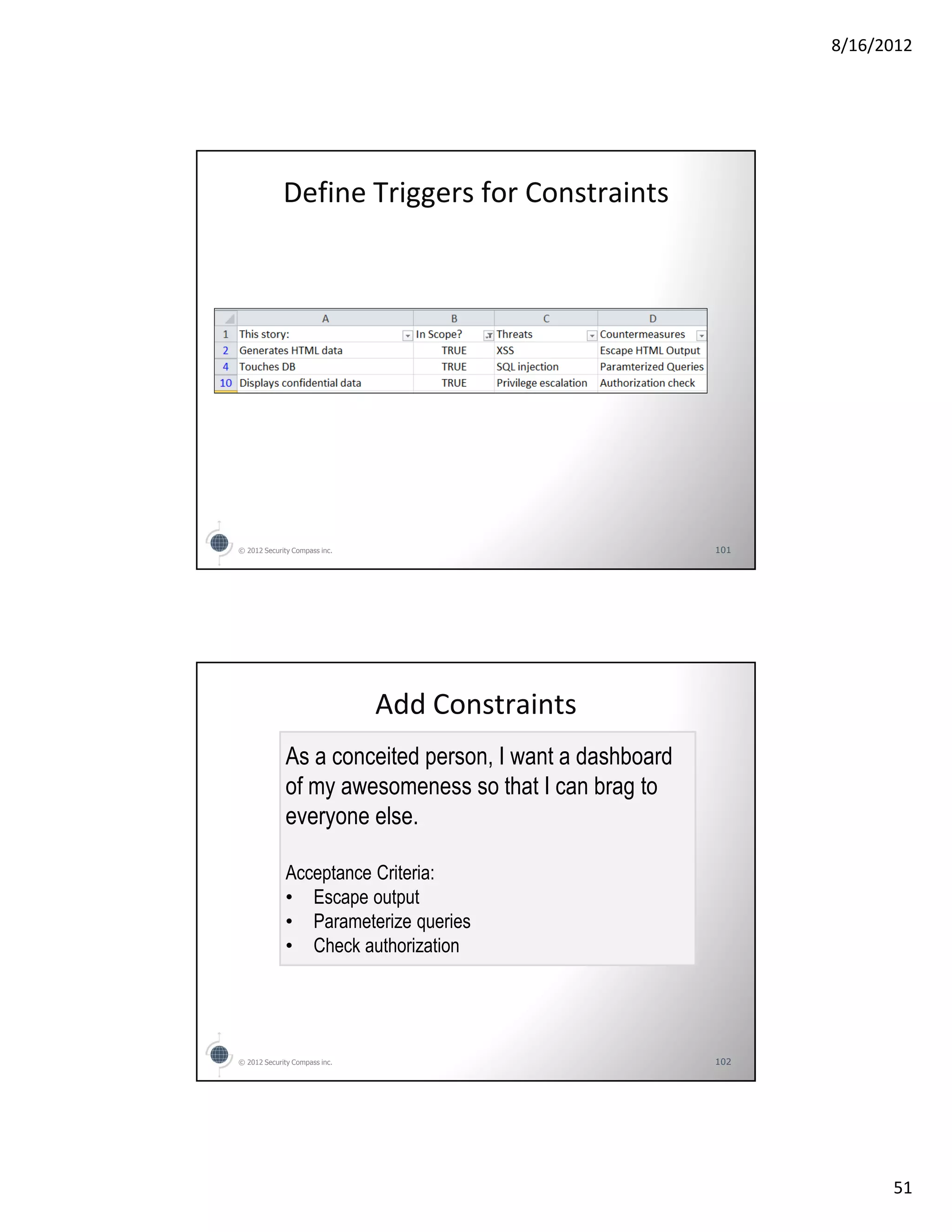
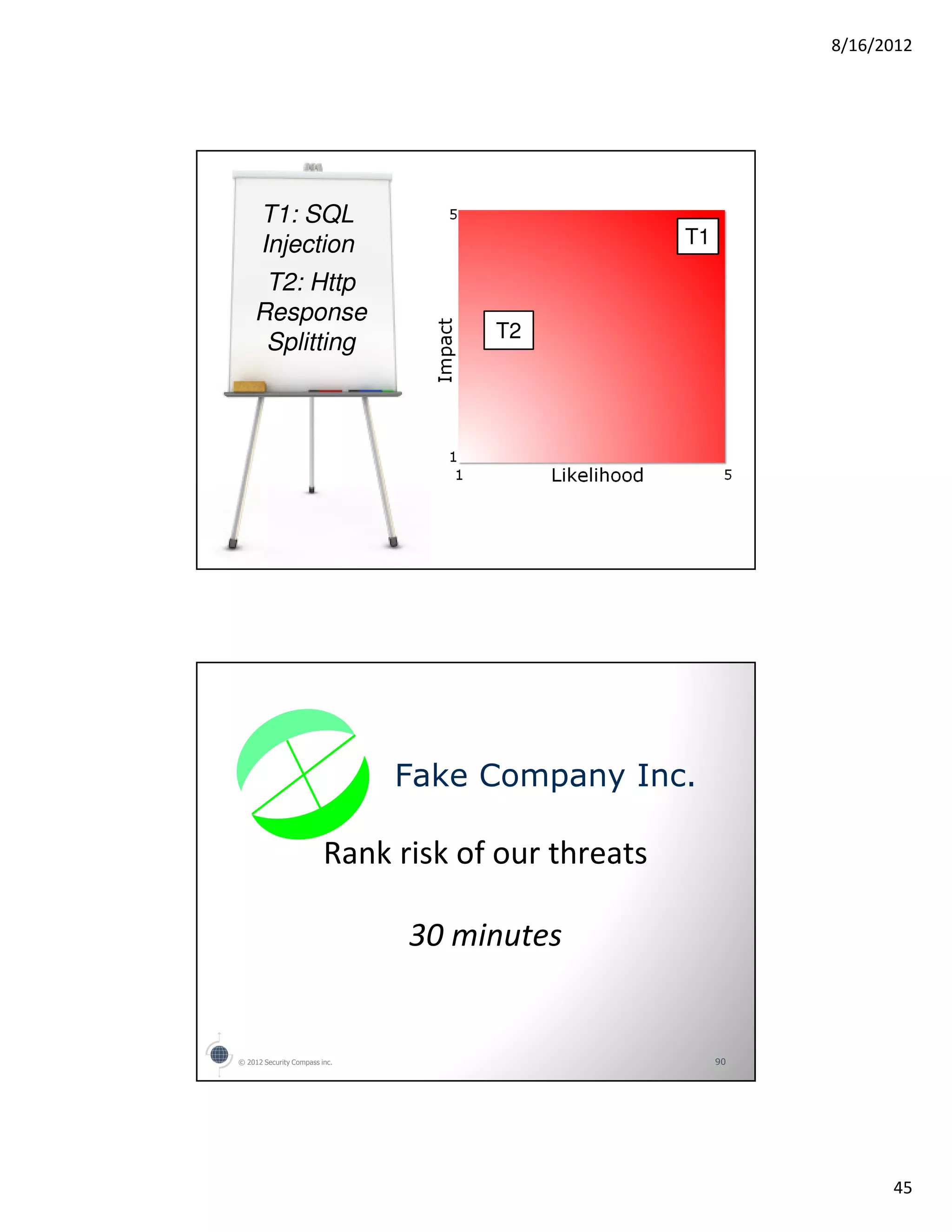
The document outlines an agenda for a class on threat modeling express. It introduces the topic and process of threat modeling express, which involves determining goals and scope, gathering information, enumerating threats, determining risk, and determining countermeasures. It provides examples of how to facilitate a threat modeling express session for a fake company application, including discussing motivations, use cases, threats, and risks. Finally, it discusses how to fit the results of a threat modeling express session into an agile development process.

























![8/16/2012
Not So Fast ….
Sometimes It’s Easy
As a security guru, I want [control] so that
my app is not vulnerable to [threat]
© 2012 Security Compass inc. 98
49](https://image.slidesharecdn.com/threatmodelexpressagile2012-121010200050-phpapp01/75/Threat-model-express-agile-2012-49-2048.jpg)