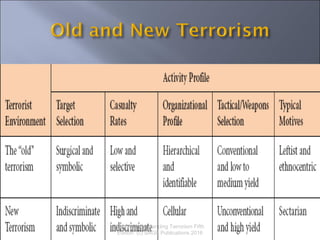
The document discusses the future of terrorism based on four theoretical waves of terrorist violence: anarchist, anti-colonial, new left, and religious. It examines terrorist environments in the 21st century which may include state-sponsored, dissident, religious, ideological, or criminal dissident terrorism. The document also explores potential future sources of terrorism in regions like the Middle East, Palestine/Israel, Latin America, Europe, Africa, and Asia as well as the threats posed by high-tech terrorism using weapons of mass destruction or cyberterrorism.