Embed presentation
Download to read offline


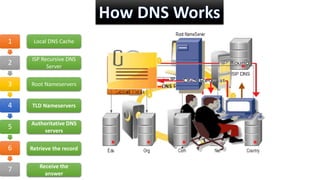
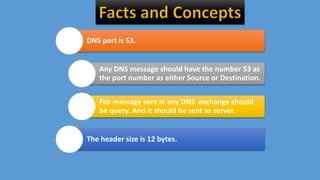

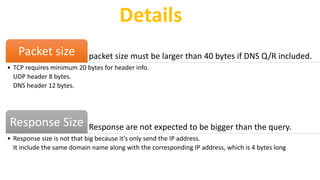
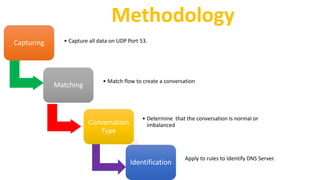


The document explains the Domain Name System (DNS), which translates web names like www.yahoo.com into IP addresses using a distributed database. It outlines the roles of various DNS servers, the structure of DNS messages, and key characteristics of DNS traffic exchange. Additionally, it describes methodologies for capturing and analyzing DNS traffic, emphasizing the importance of balanced queries and responses.







