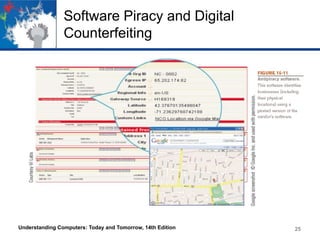
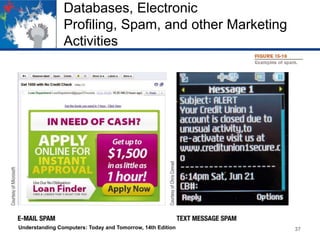
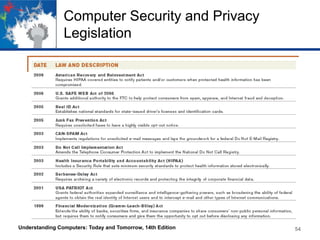
This chapter discusses computer security and privacy. It covers risks from hardware loss, damage, and failure, and ways to safeguard hardware through encryption, tracking software, and backups. It also addresses software piracy, digital counterfeiting, and their prevention. The chapter discusses privacy concerns regarding databases, electronic profiling, spam, and surveillance. It provides tips for protecting personal information and privacy online and offline. [/SUMMARY]