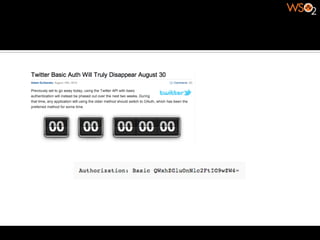
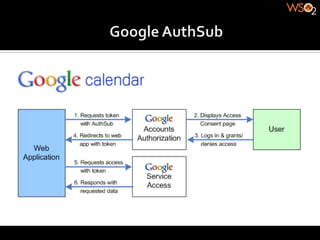
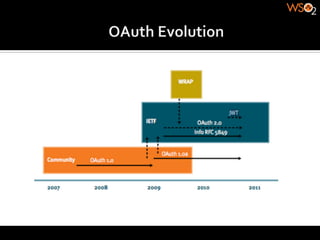
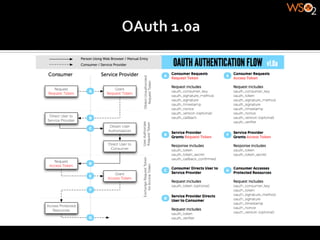
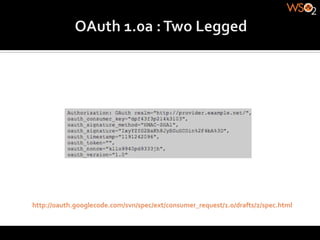
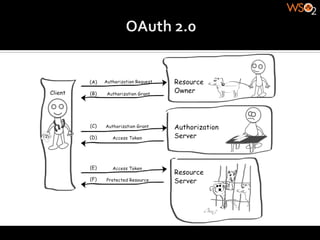
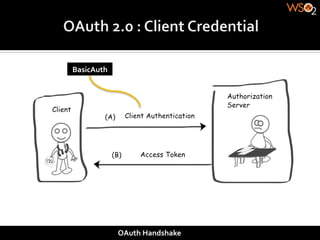
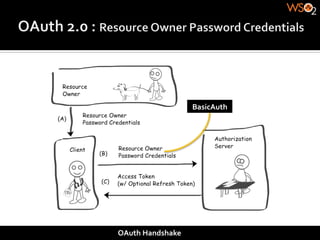
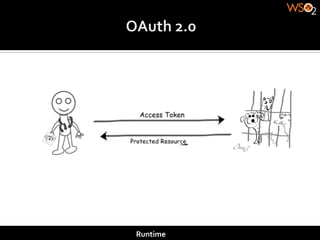
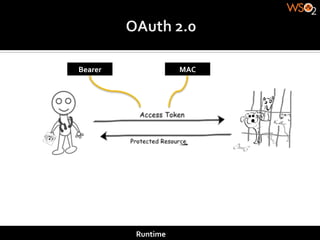
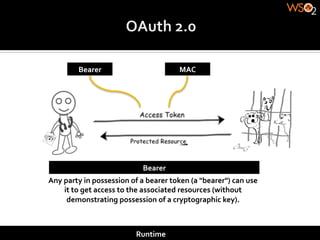
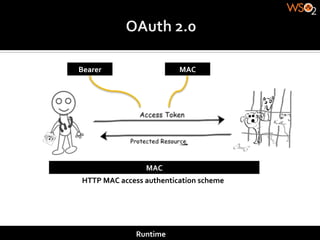
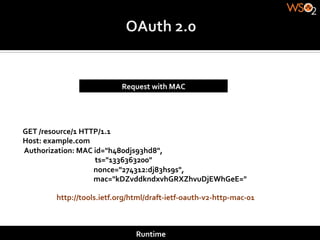
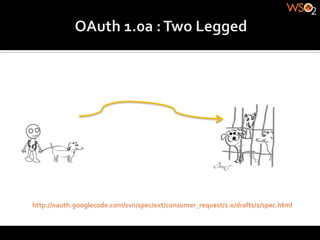The document discusses authentication methods for APIs, including basic authentication, OAuth, and different OAuth token and signature types like bearer tokens and MAC signatures. It notes some limitations of basic authentication and outlines the OAuth handshake process. It then compares bearer tokens, which allow access by any party possessing the token, to MAC signatures, which require demonstrating possession of a cryptographic key.