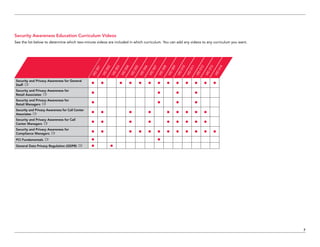
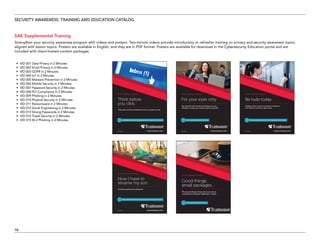
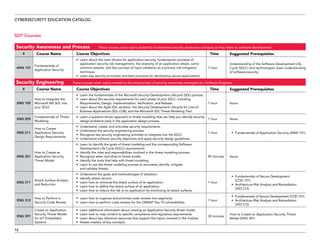
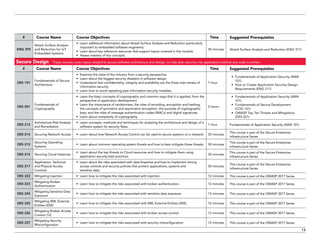
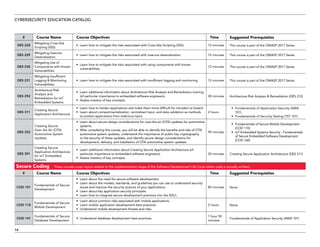
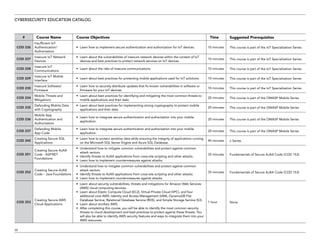
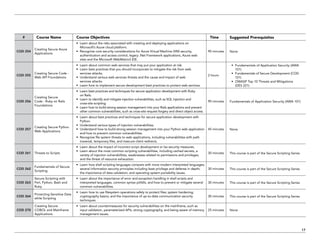
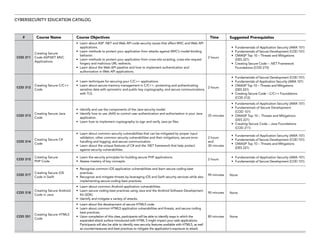
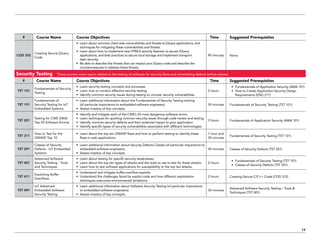
The document serves as a catalog for cybersecurity education offerings by Trustwave, emphasizing the importance of security training for employees to protect sensitive data. It provides details on various security awareness education programs, custom curricula, and specific courses targeting different job roles within organizations. Additionally, it outlines available supplemental materials and resources to reinforce ongoing security training year-round.