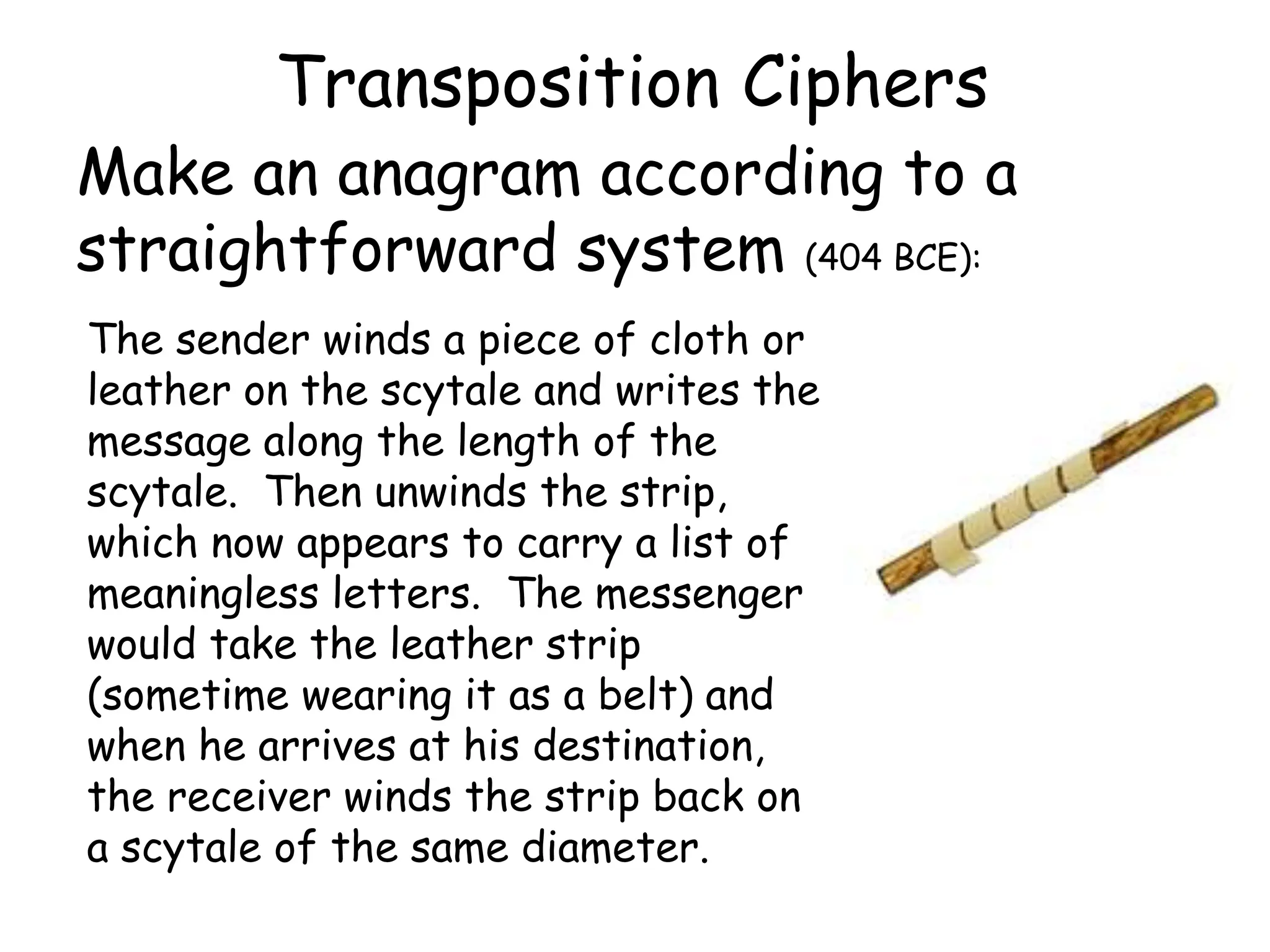
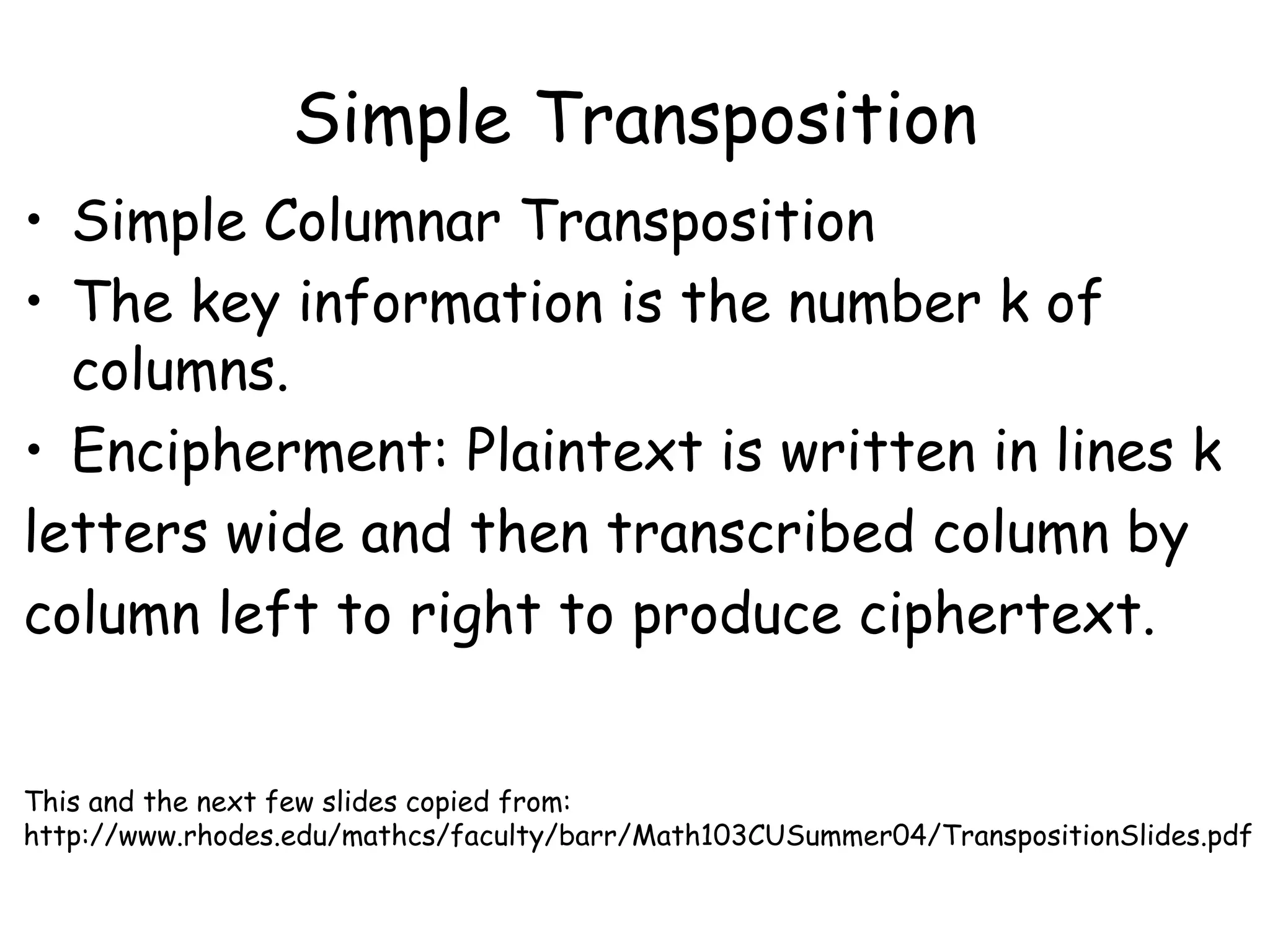
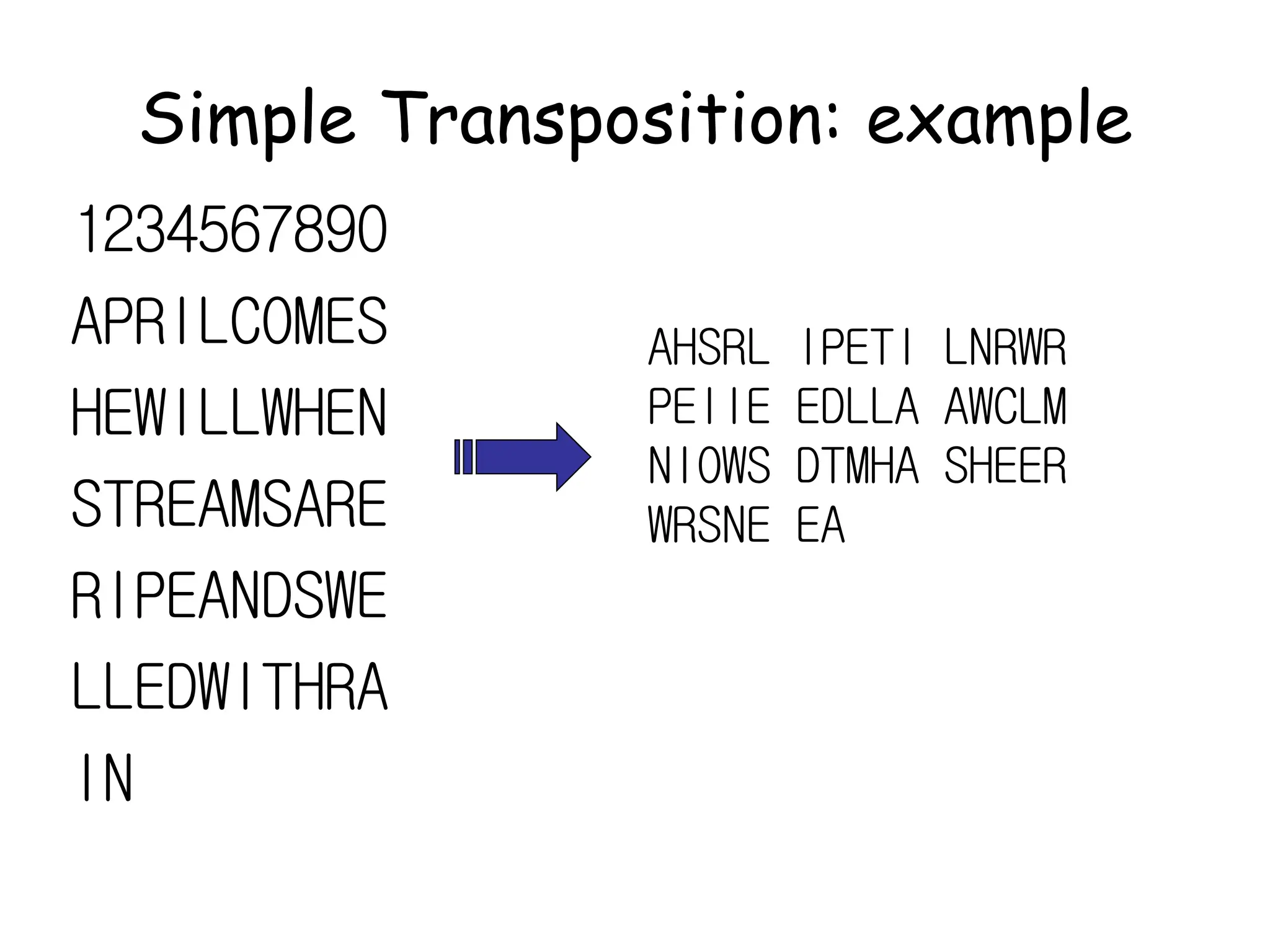
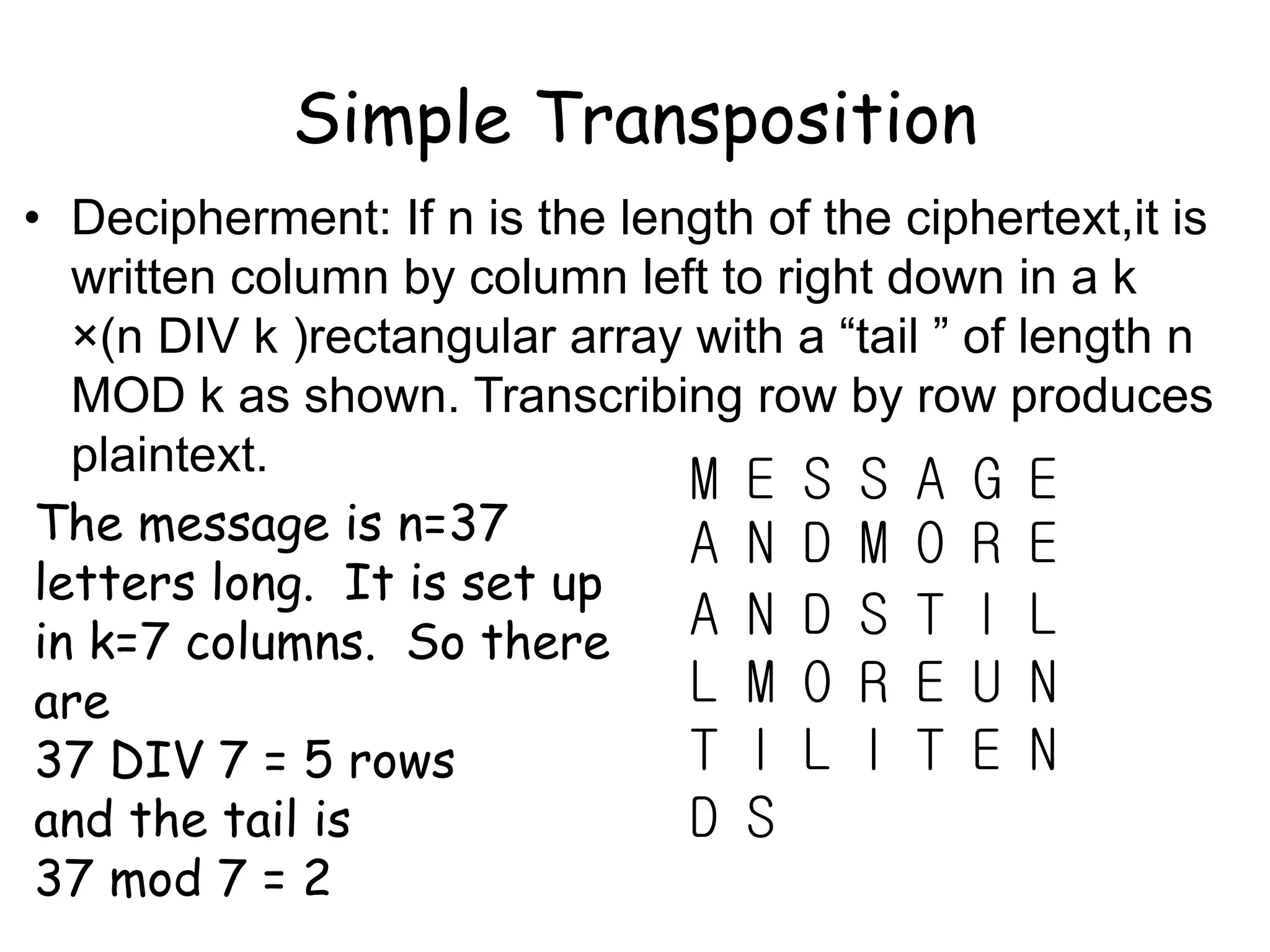
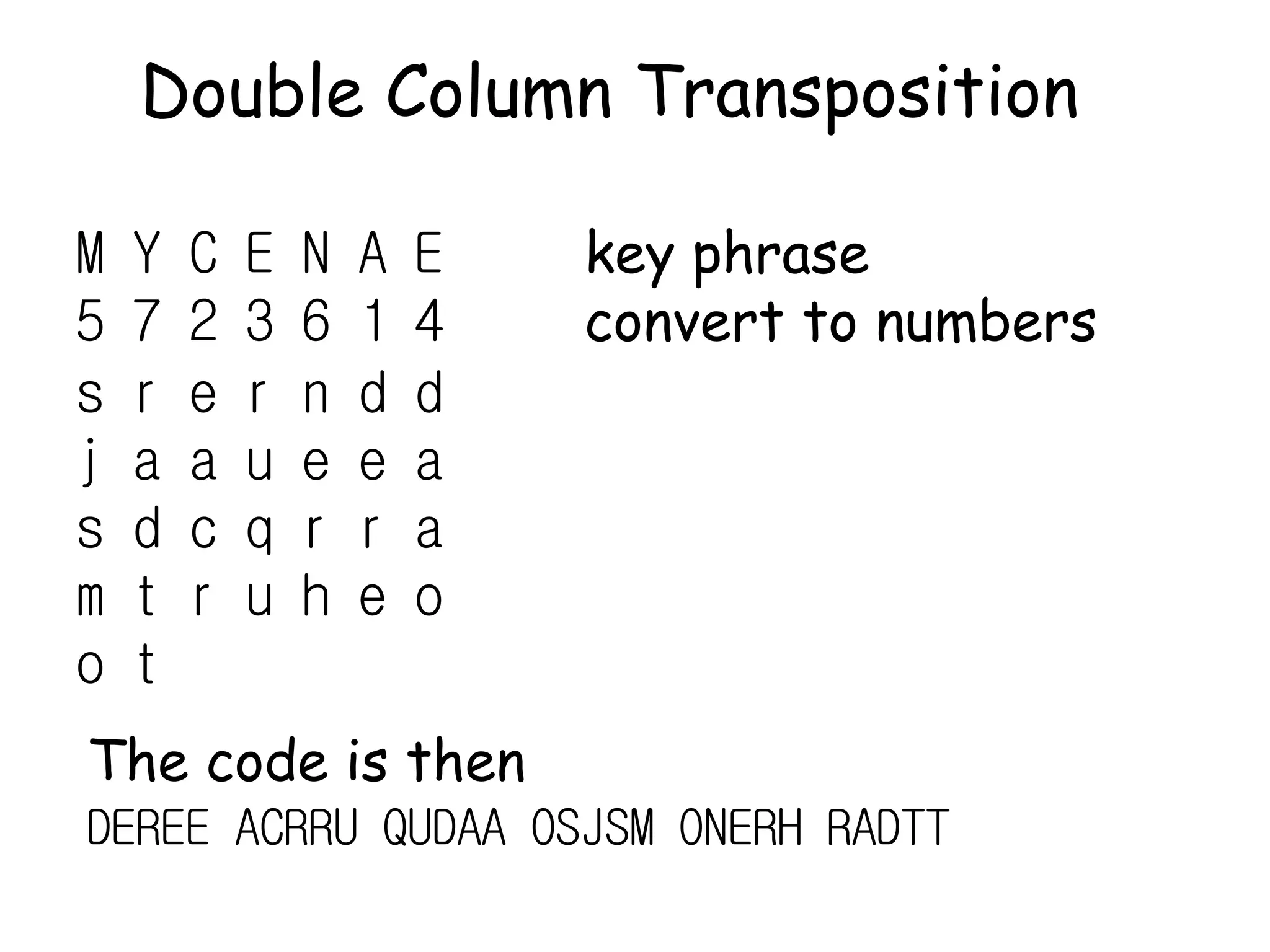
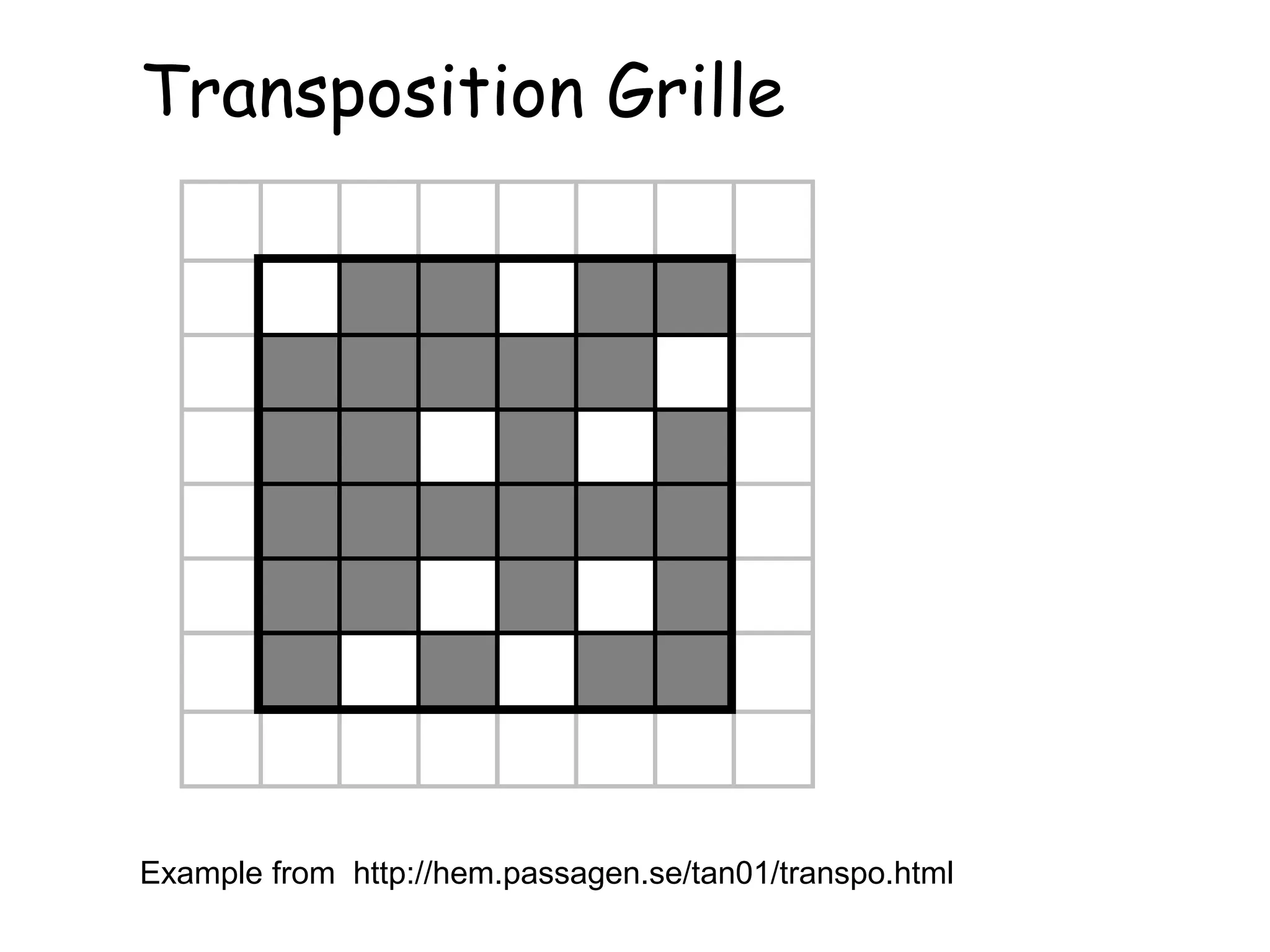
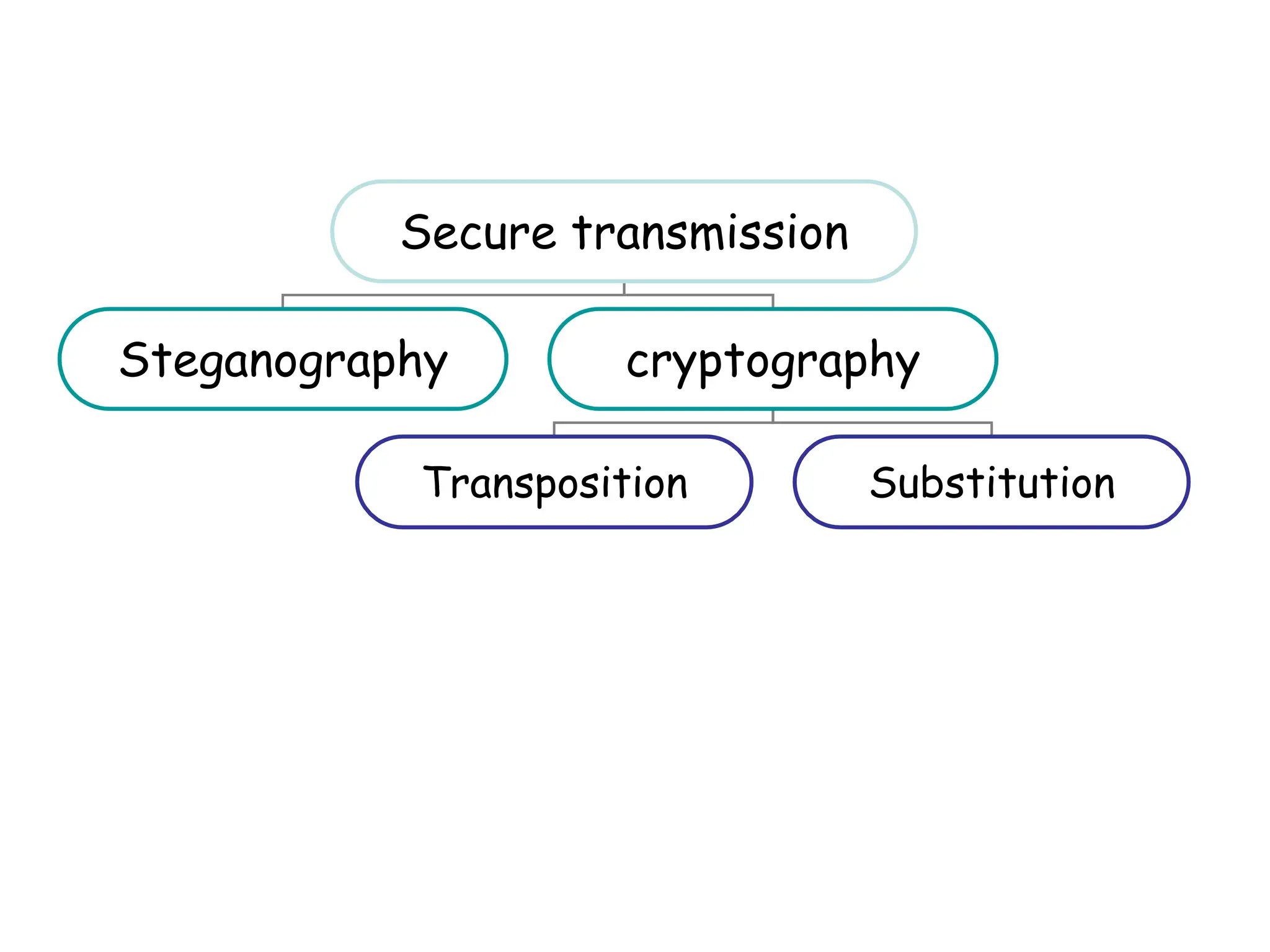
This document outlines the structure and expectations for a cryptography course. The course will include both lectures and group activities. Students will complete daily homework assignments, an essay, and a final project. Most work should be typed. Attendance is mandatory and respectful behavior is expected. When decrypting or deciphering information, students can use any legal methods and must disclose the techniques used. The document then provides examples of simple transposition ciphers like columnar transposition and rail fence ciphers. Students are assigned homework problems to encrypt and decrypt messages using various transposition cipher techniques.