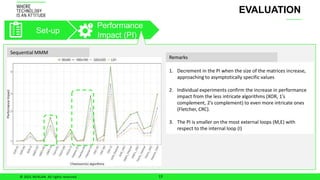
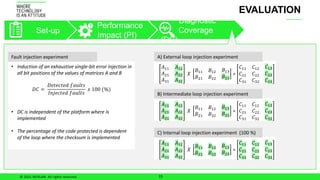
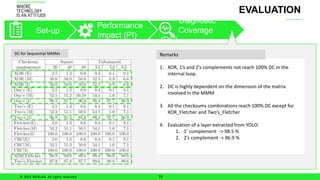
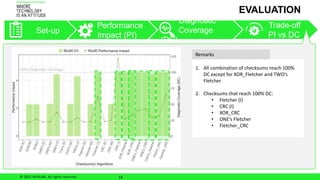
The document discusses ensuring functional safety for machine learning-based autonomous systems. It proposes using checksum algorithms to detect errors in matrix-matrix multiplication, a key computation. The solution was evaluated on sequential and AVX-based multiplication, finding that checksums can achieve 100% diagnostic coverage with minimal performance impact depending on matrix size. Future work includes evaluating multiple bit errors and accelerators.


![© 2021 IKERLAN. All rights reserved
Introduction
CONTEXT
IEC 61508 IEC 61513 EN 5012X ISO 26262
Current Standards
“Process where a machine/computer/system learns things that can be
used to make it perform better in the future 2 ”
ML is based on probabilistic models built from training
data set instead from specifications for making
predictions and for making decisions
ML has made enormous progress reaching near-human
accuracy in several safety-related tasks.
ML algorithms process large data volumes and they
need higher performance than that provided by
traditional dependable embedded systems
Machine learning (ML)
[1] IEC 61508 (1-7): Functional safety of
E/E/PE safety related systems
[2] Data Mining: Practical Machine Learning Tools and Techniques
• ISO/PAS 21448:2019 (SOTIF)
• ANSI/ UL 4600
• VDE-AR-E 2842-61
New standards
3](https://image.slidesharecdn.com/javierfdeztowardsfunctionalsafetycomplianceofmmmlivepresentation-210610053508/85/Towards-Functional-Safety-compliance-of-Matrix-Matrix-Multiplication-3-320.jpg)
![© 2021 IKERLAN. All rights reserved
Introduction
Object
Detection
CONTEXT
1. General Matrix-Matrix Multiplication (GEMM)
2. CUBLAS
3. Processor-specific variants such as AVX
MMM offered by YOLO
YOLO (You Only Look Once):
• Multiscale Object detector
• Based on darknet
Library
Matrix-Matrix Multiplication (MMM):
• 67 % execution time [1]
• Backbone of the
Convolutional Neural
Networks (CNNs)
Code subset
[1] Evaluation and mitigation of soft-errors in neural network
based object detection in three GPU architectures
4](https://image.slidesharecdn.com/javierfdeztowardsfunctionalsafetycomplianceofmmmlivepresentation-210610053508/85/Towards-Functional-Safety-compliance-of-Matrix-Matrix-Multiplication-4-320.jpg)
![© 2021 IKERLAN. All rights reserved
Failures &
Diagnostic
Coverage
CONTEXT
Introduction
Object
Detection
“DC denotes the effectiveness of
diagnostic techniques to detect
dangerous errors” [1]
Diagnostic Coverage (DC)
a) Permanent Faults
b) Intermittent Faults
c) Transient Faults
Classification of faults (frequency)
0 1 0
0 0 1
1 0 1
1 1 0
0 0 1
1 0 0
Activation weights
to be mapped
Activation weights
mapped Systematic: associated with the
development process
Random: Associated to hardware
errors. For example:
• Electromagnetic interference
• Component wear-out
• Voltage drops
Classification of faults (source)
5 [2] Understanding Error Propagation in Deep Learning
Neural Network (DNN) Accelerators and Applications
[2] [2]
[1] Evaluation Multi-core devices for safety-critical systems:
a survey](https://image.slidesharecdn.com/javierfdeztowardsfunctionalsafetycomplianceofmmmlivepresentation-210610053508/85/Towards-Functional-Safety-compliance-of-Matrix-Matrix-Multiplication-5-320.jpg)

![© 2021 IKERLAN. All rights reserved
Error avoidance
PROPOSED SOLUTION
MMM: VIOLATIONS BY RULE OF MISRA C:2012
DARKNET: VIOLATIONS BY RULE OF MISRA C:2012
• Usage of defensive programming
• Compliance with codification guidelines (MISRA C [1])
Strategy
• Not explicitly defining types with the size and signedness for
basic numerical types.
• Not checking the correctness of input parameters
• Not explicitly defining the desired precedence of operators
within expressions
• Not explicitly defining input parameter pointers as
const-qualified type
Violations Sequential MMM
7
[1] MISRA C:2012 – Guidelines for the use of the C language
in critical systems
• Polyspace
Analysis Tool](https://image.slidesharecdn.com/javierfdeztowardsfunctionalsafetycomplianceofmmmlivepresentation-210610053508/85/Towards-Functional-Safety-compliance-of-Matrix-Matrix-Multiplication-7-320.jpg)
![© 2021 IKERLAN. All rights reserved
Error Detection
Error avoidance
To guarantee a safe execution during the software
deployment of the Matrix-matrix multiplication (MMM)
through the use of diagnostic techniques.
Objective
a) To employ checksums algorithms as diagnostic
techniques to compute an Execution Signature (ES)
of all the values of the input and output matrices.
b) To provide a catalogue of checksums and to evaluate
a trade-off between DC and performance impact.
Proposal
• XOR
• Twos’ complement
• Ones’ complement
Checksums algorithms[1]
• Fletcher
• CRC
𝐴11 𝐴12
𝐴21 𝐴22
𝐴31 𝐴32
𝑋
𝐵11 𝐵12 𝐵13
𝐵21 𝐵22 𝐵23
=
𝐶11 𝐶12 𝐶13
𝐶21 𝐶22 𝐶23
𝐶31 𝐶32 𝐶33
PROPOSED SOLUTION
[1] The Effectiveness of Checksums for 8](https://image.slidesharecdn.com/javierfdeztowardsfunctionalsafetycomplianceofmmmlivepresentation-210610053508/85/Towards-Functional-Safety-compliance-of-Matrix-Matrix-Multiplication-8-320.jpg)