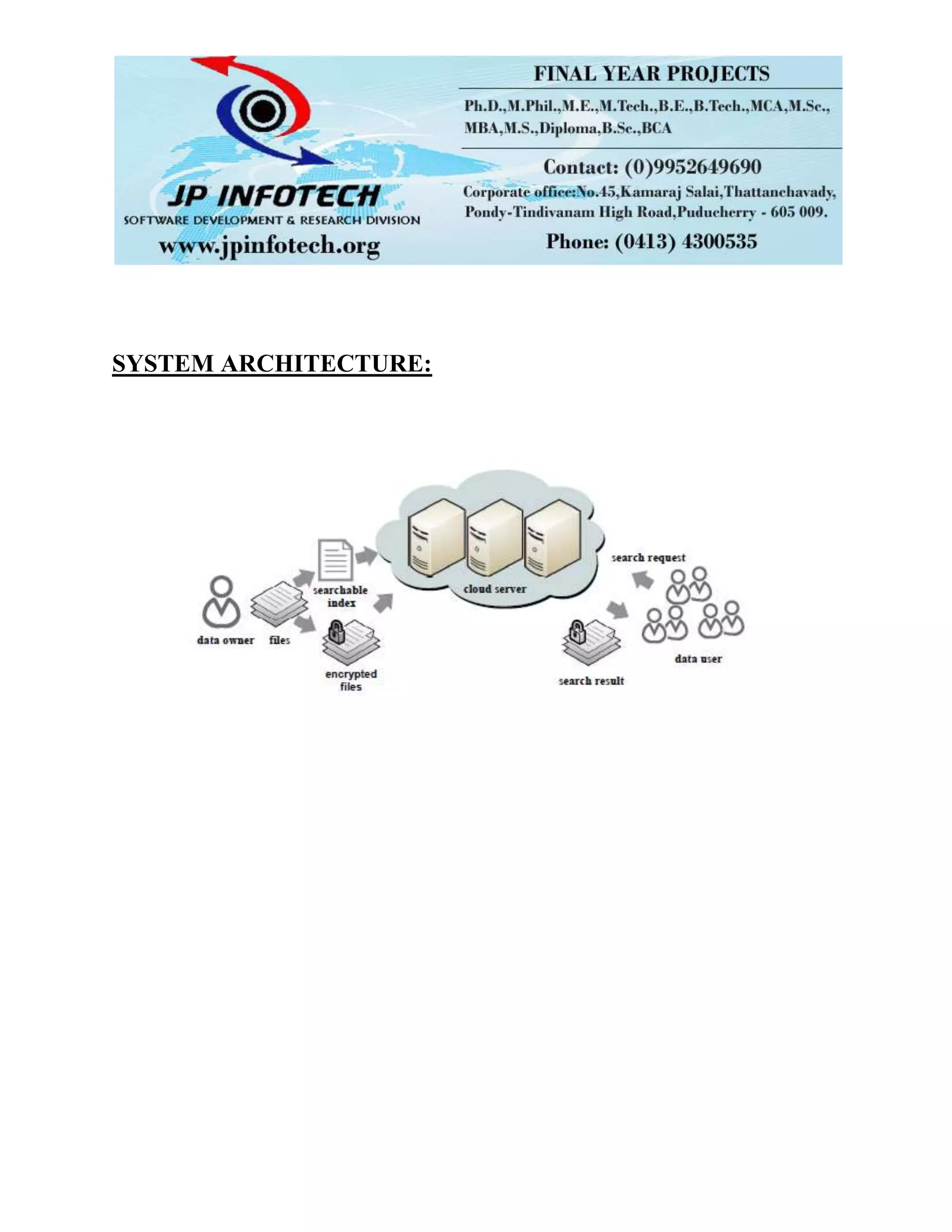
The document proposes a two-round searchable encryption scheme to enable secure multi-keyword top-k retrieval over encrypted cloud data. Existing searchable encryption schemes only support boolean keyword search and do not consider relevance. The proposed Two-Round Searchable Encryption scheme uses homomorphic encryption and a vector space model to enable users to participate in ranking while most computation is done on the server side ciphertext only. This guarantees security without sacrificing efficiency.