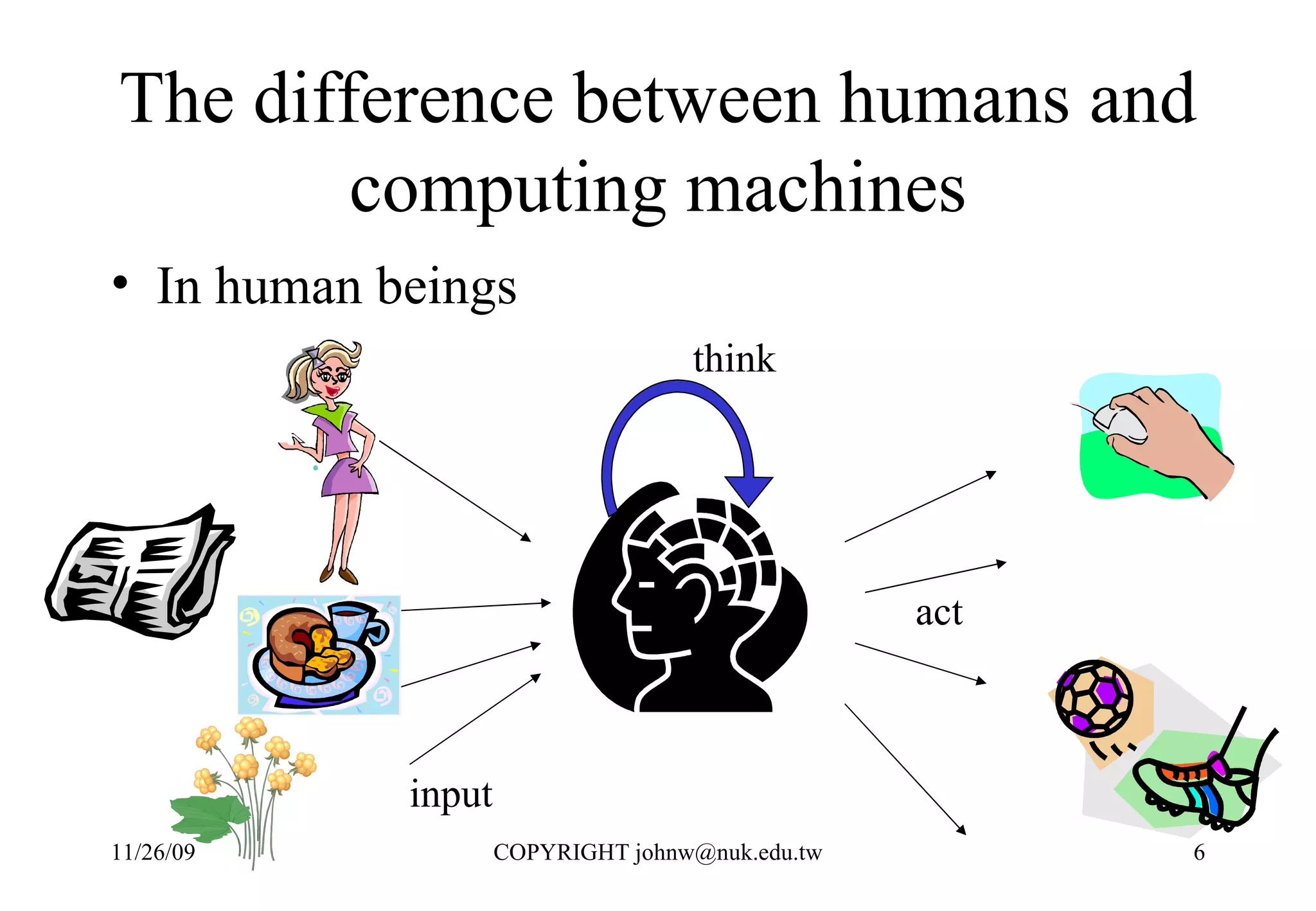
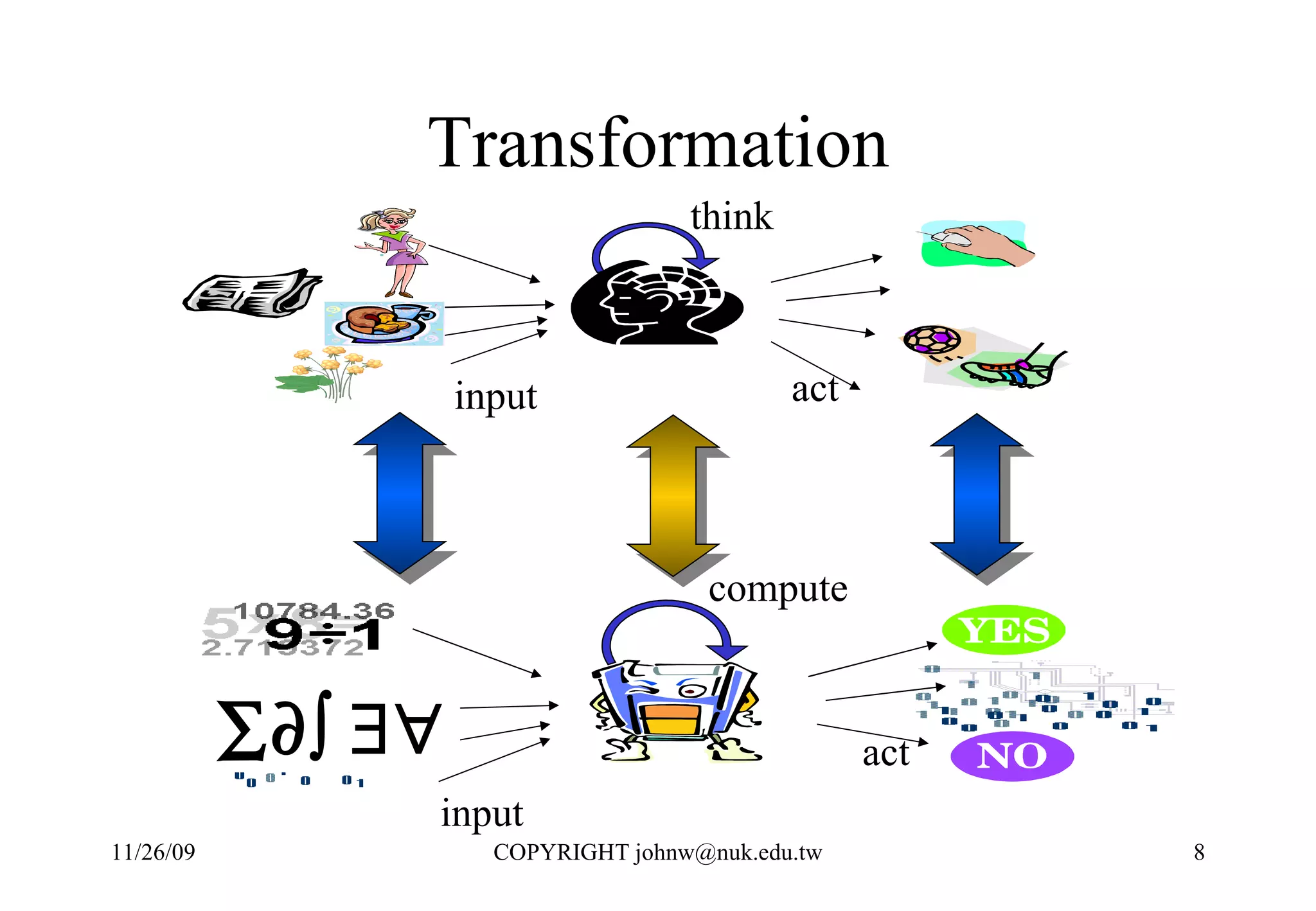
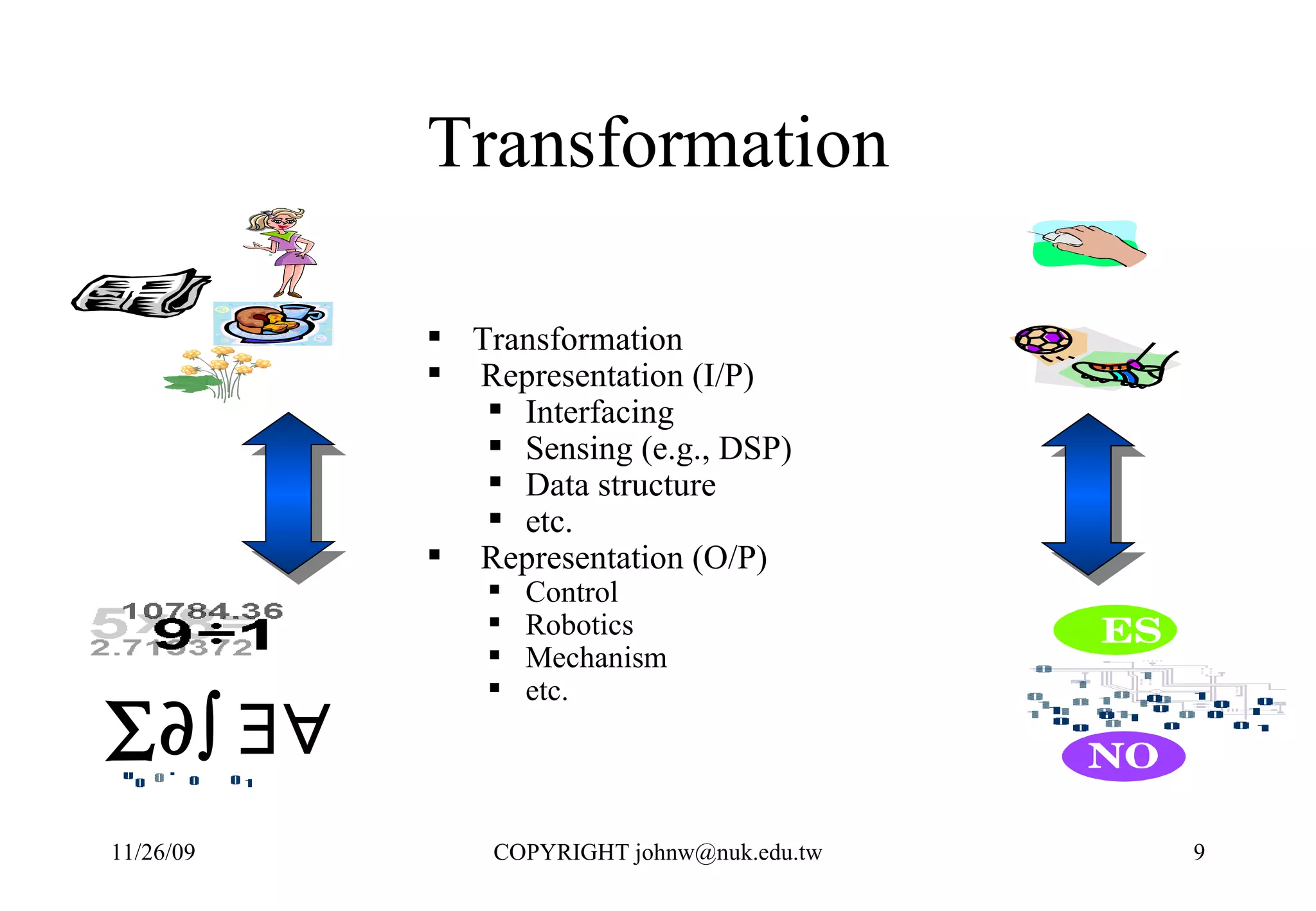
1) Humans use problem solving techniques to address challenges in everyday life like moving faster or making more food.
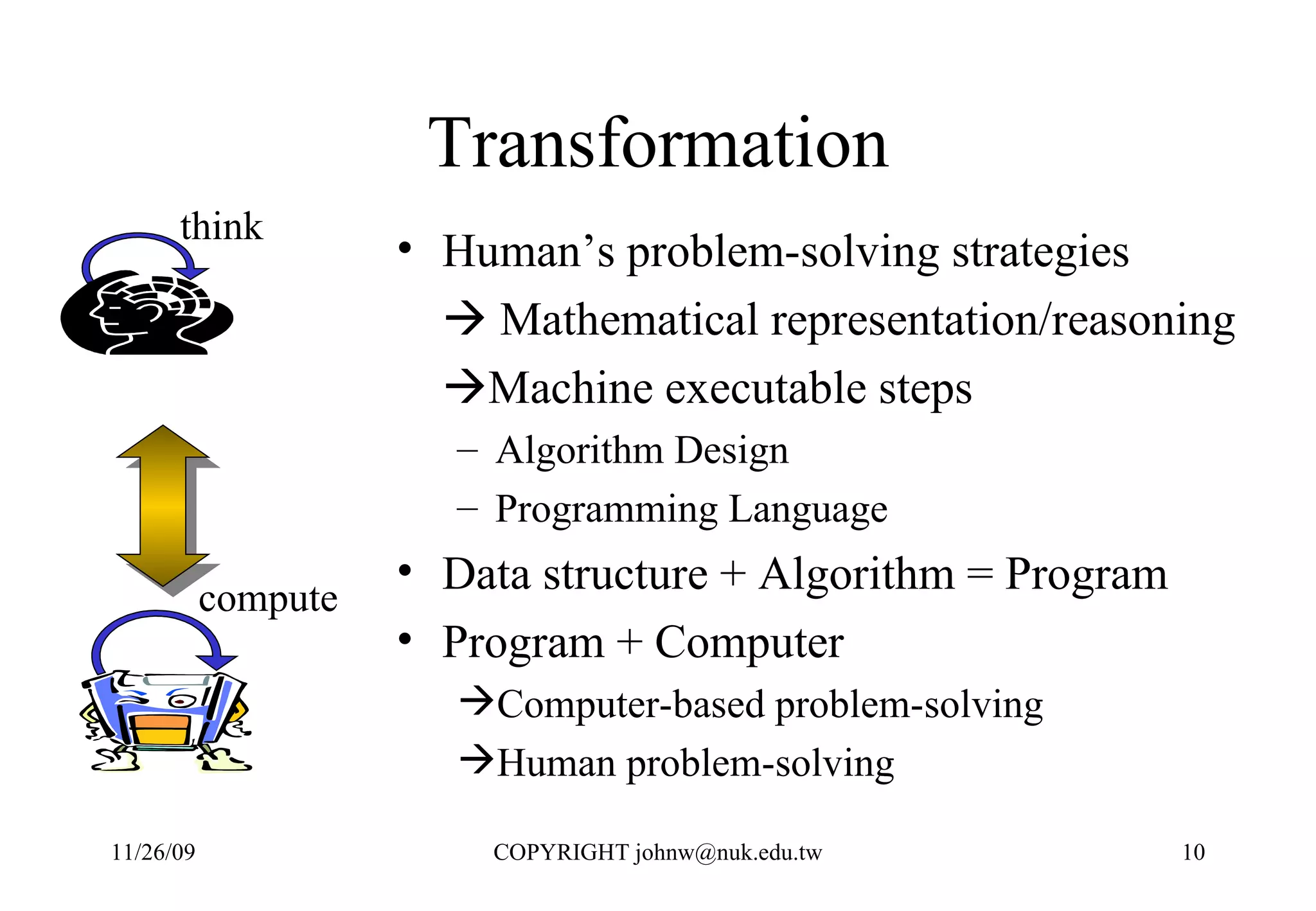
2) Mathematics provides a way to represent problem solving steps that can be executed by machines, allowing humans to leverage computation.
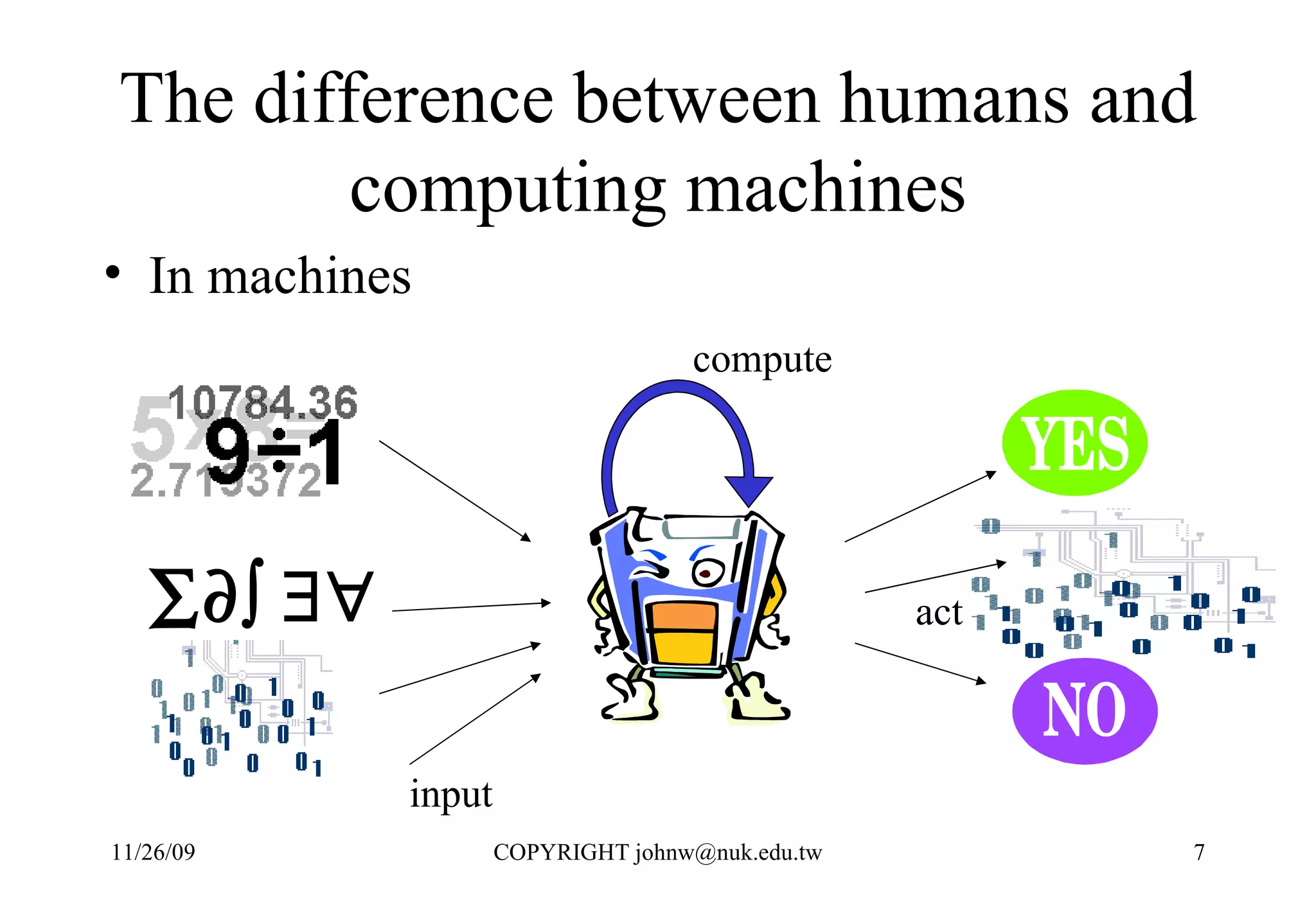
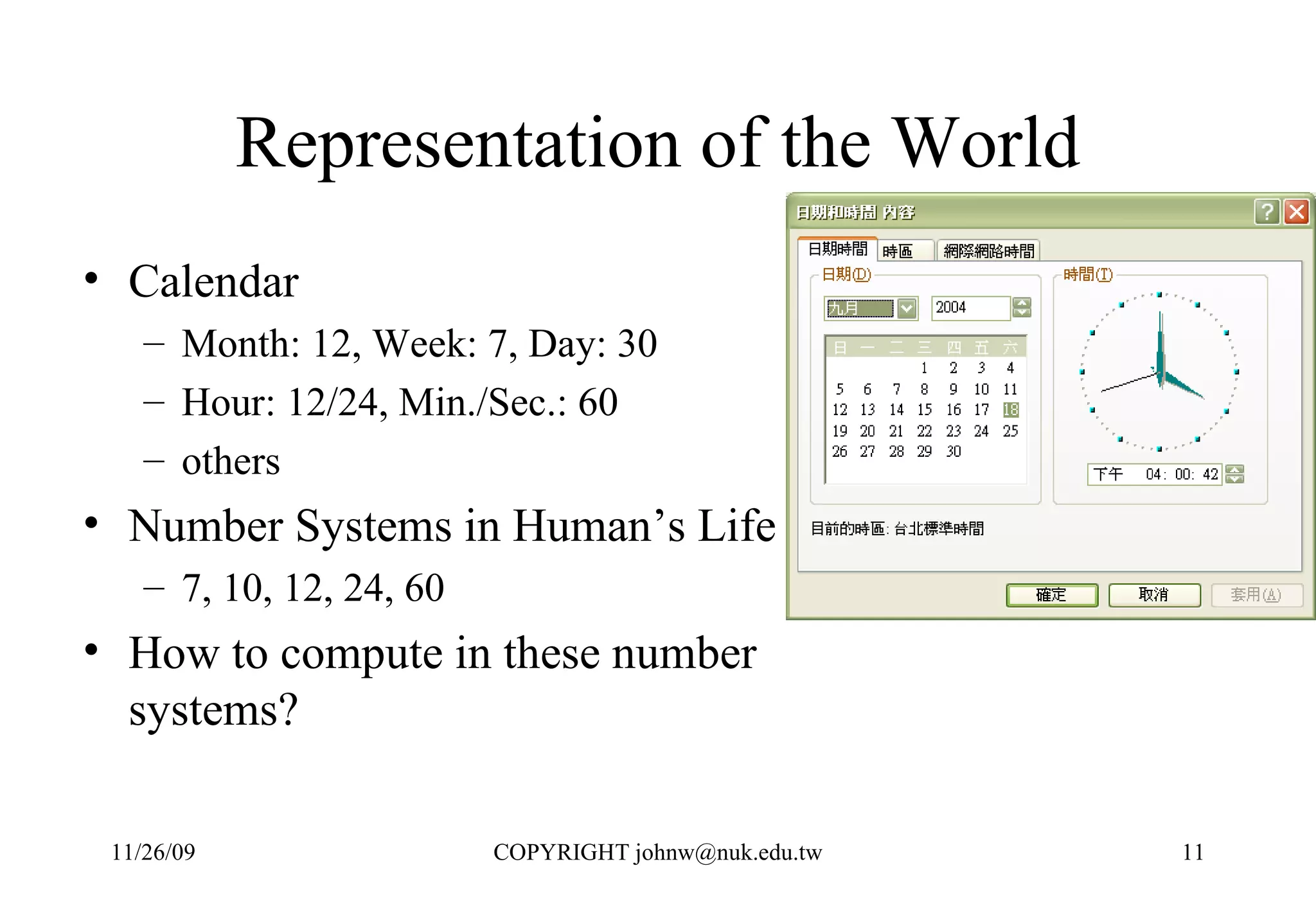
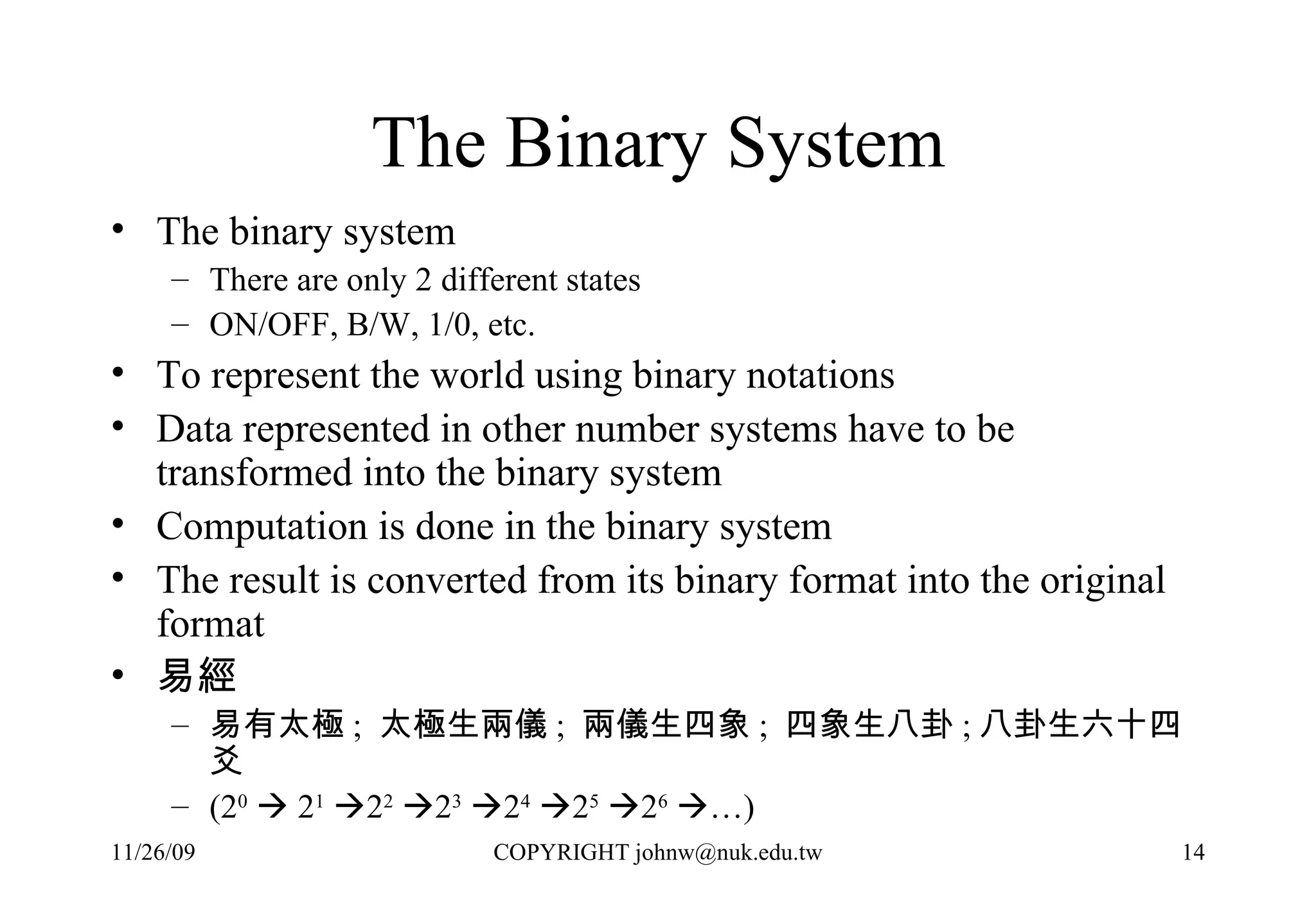
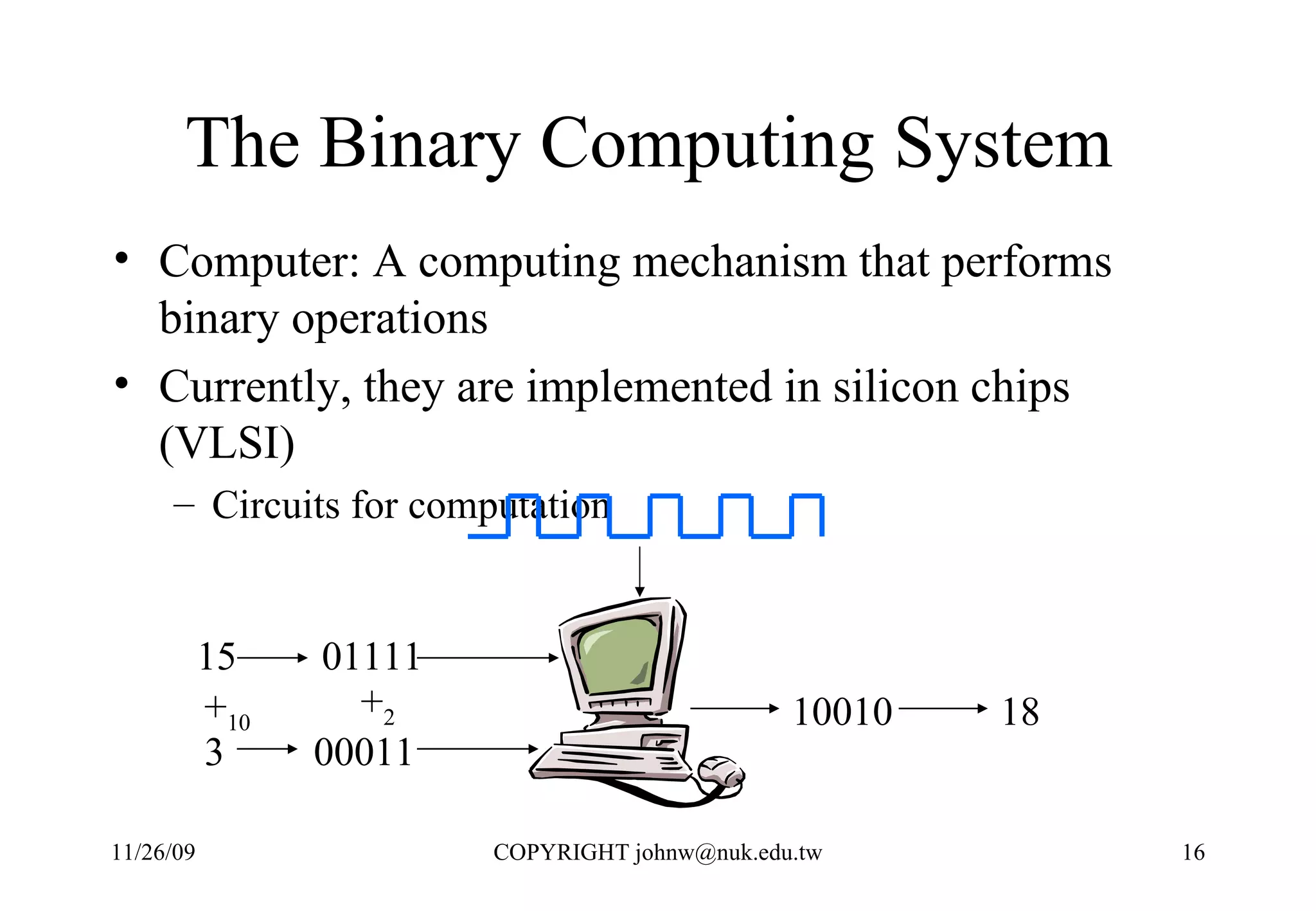
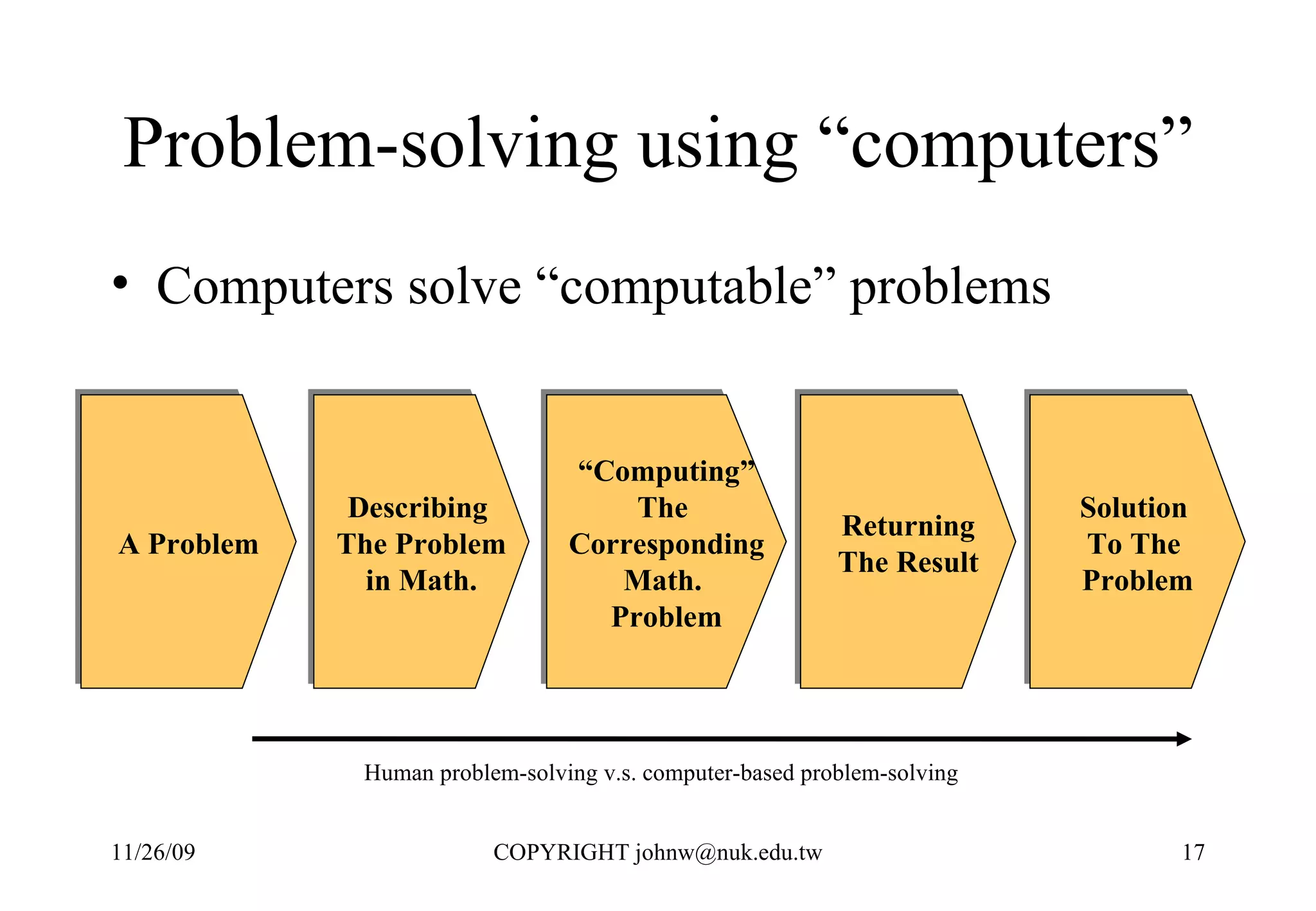
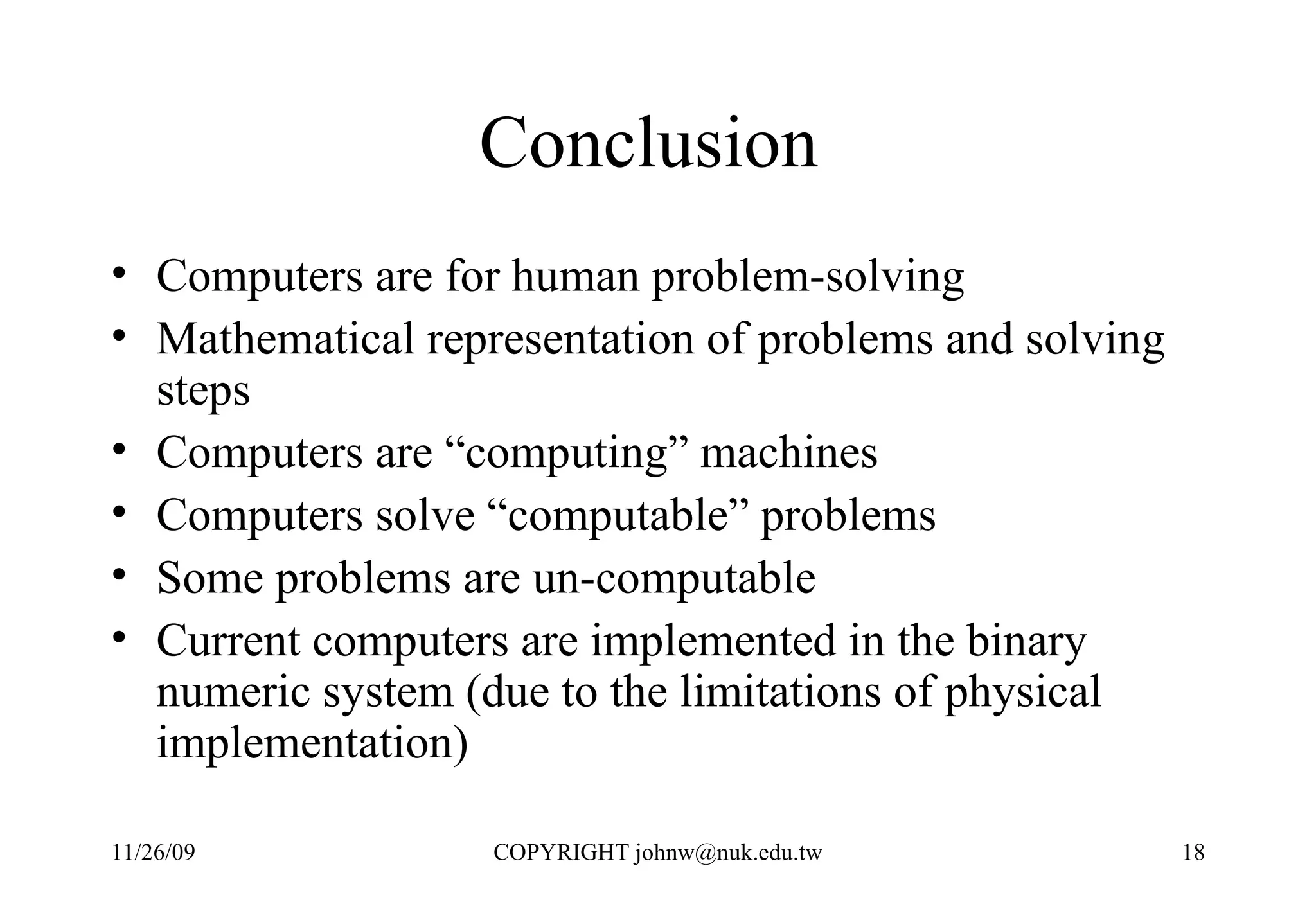
3) Computers were developed to automate computation, representing problems mathematically and executing the steps numerically in a binary system for performance and reliability.