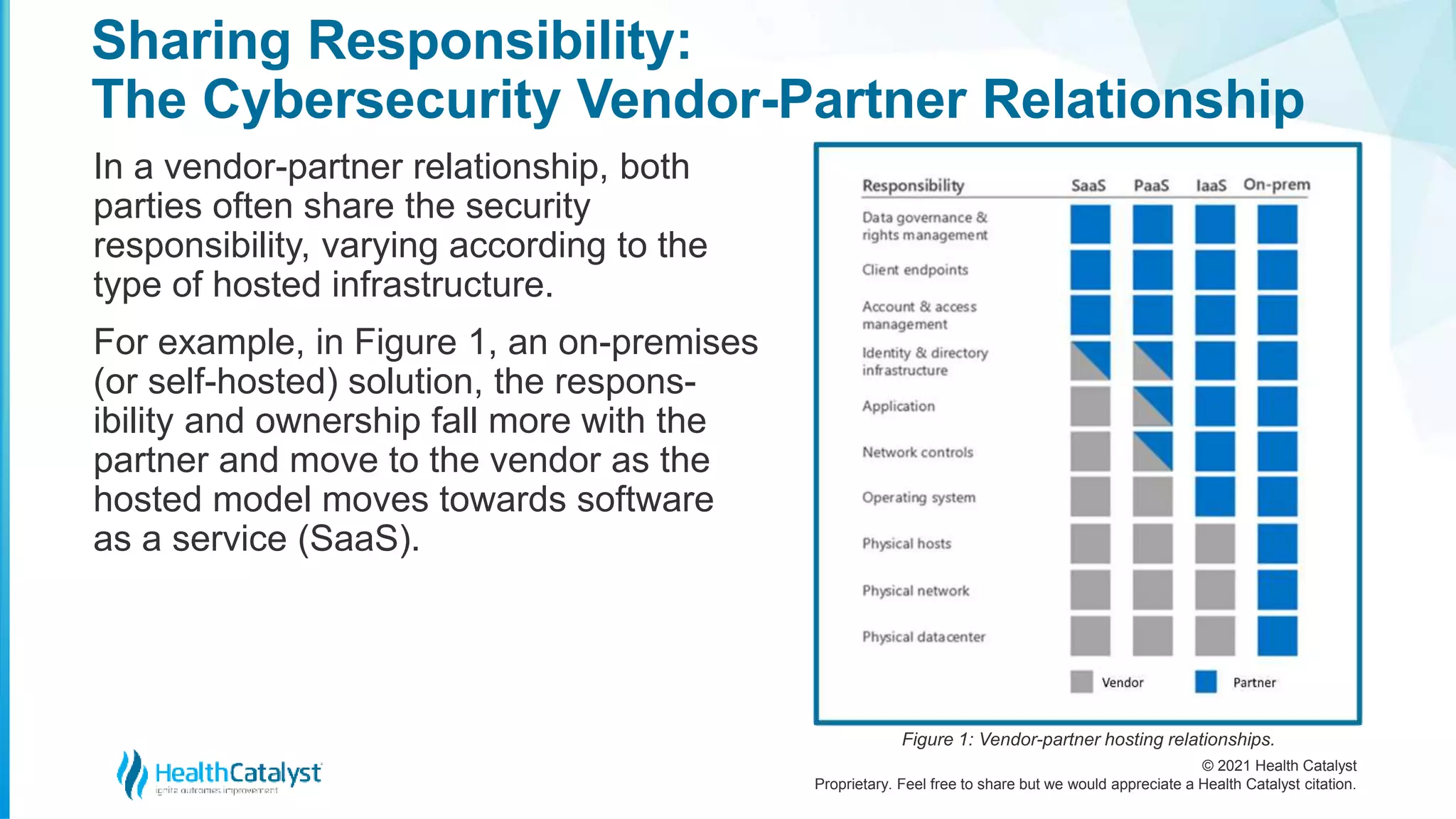
The document discusses the escalating cybersecurity challenges in the healthcare sector, noting that over 93% of healthcare organizations faced data breaches between 2017 and 2020. It emphasizes the importance of a robust cybersecurity framework, highlighting the shared responsibilities between healthcare IT vendors and organizations, and outlines necessary third-party audits and compliance measures to safeguard patient data. Additionally, it underscores the role of C-suite leadership in ensuring effective cybersecurity strategies amidst increasing cyber threats.