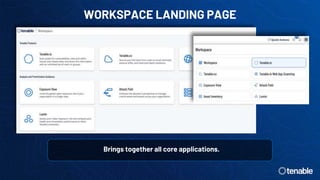
The document discusses the need for exposure management over vulnerability management due to the growing, dynamic, and interconnected modern attack surface. It introduces the Tenable One Exposure Management Platform which provides comprehensive visibility across identities, web applications, cloud infrastructure, and vulnerabilities. It aggregates data to provide risk prioritization, attack path analysis, and asset inventory with the goal of reducing risk through context and prioritization.