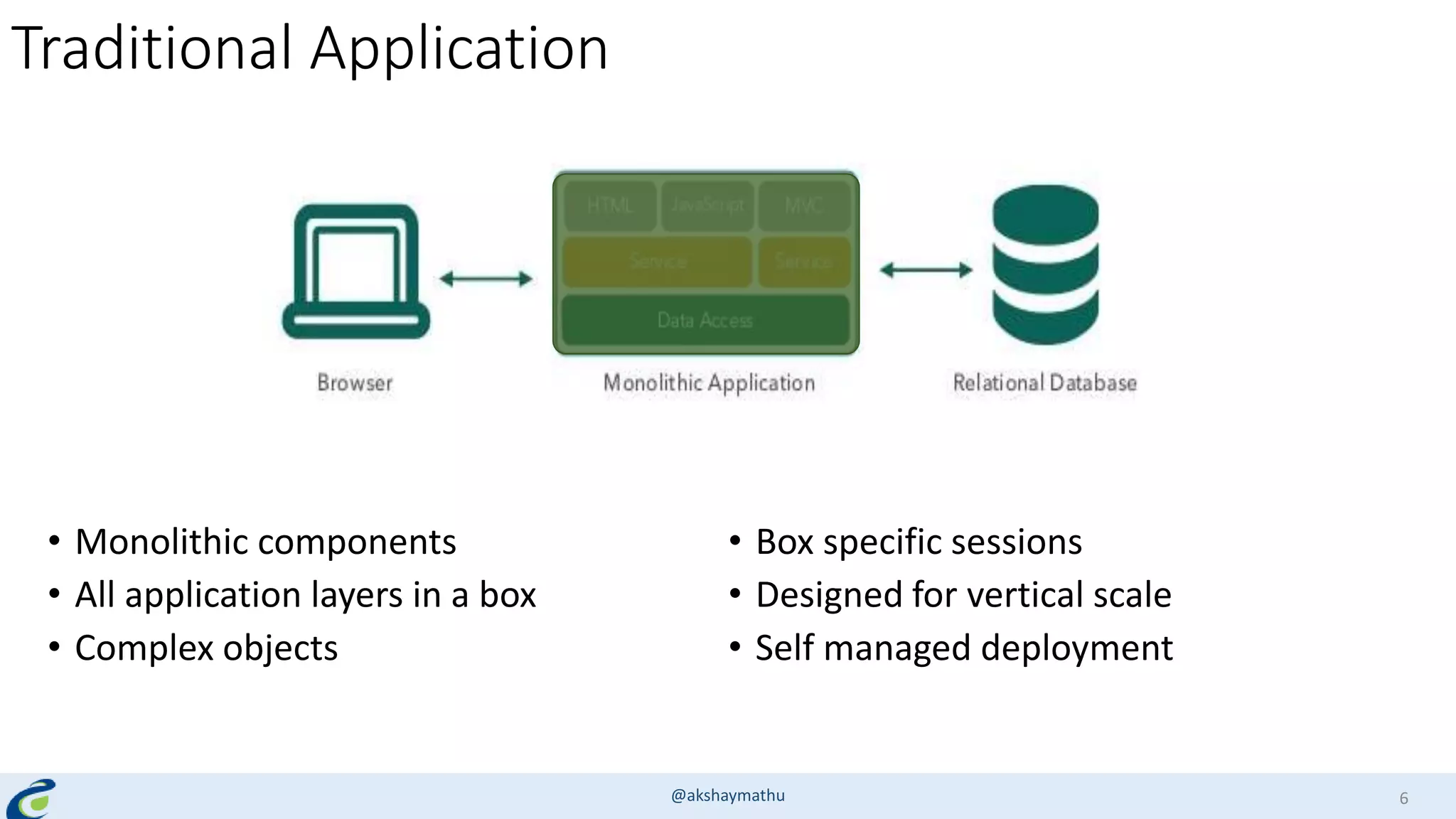
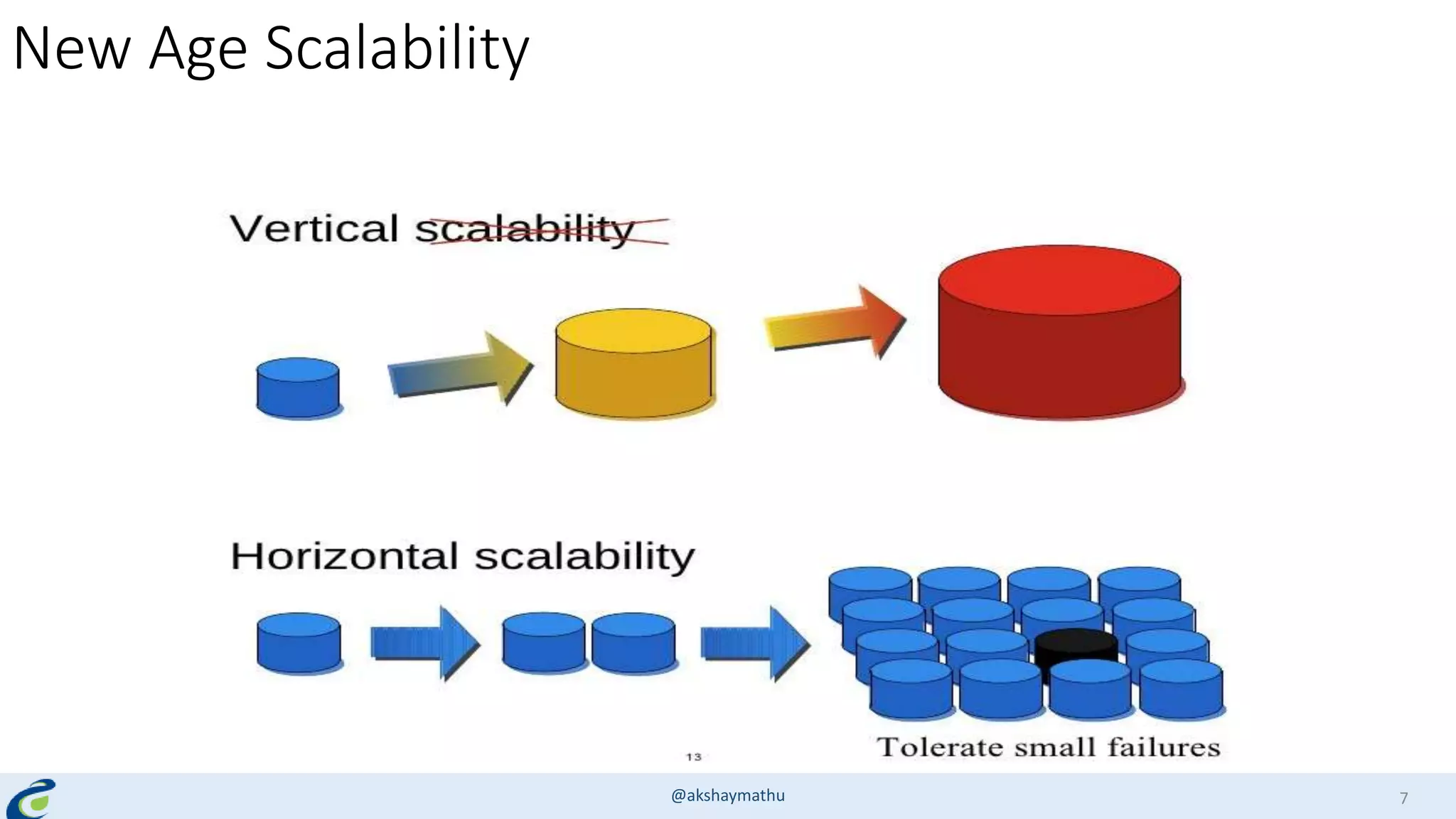
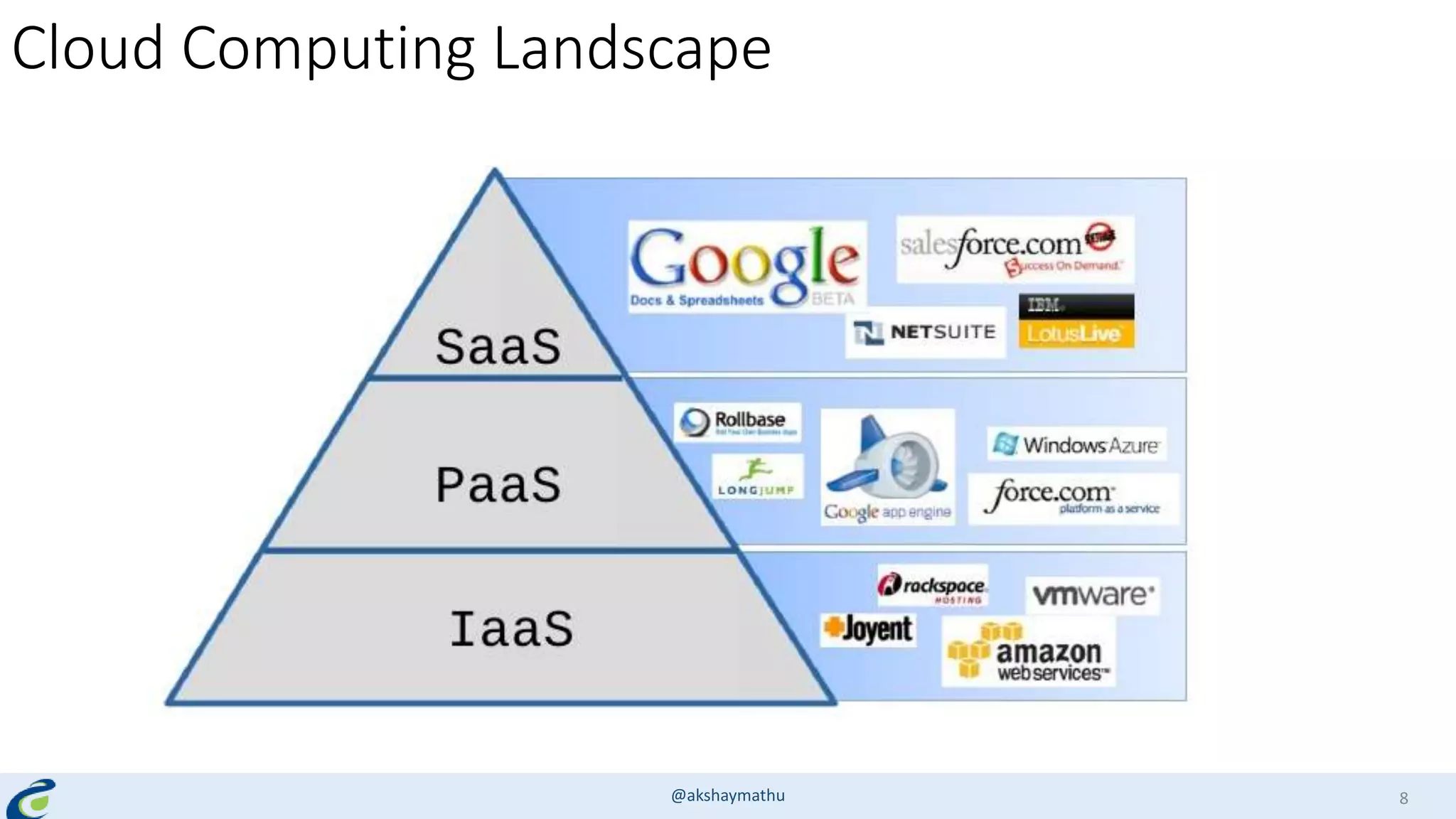
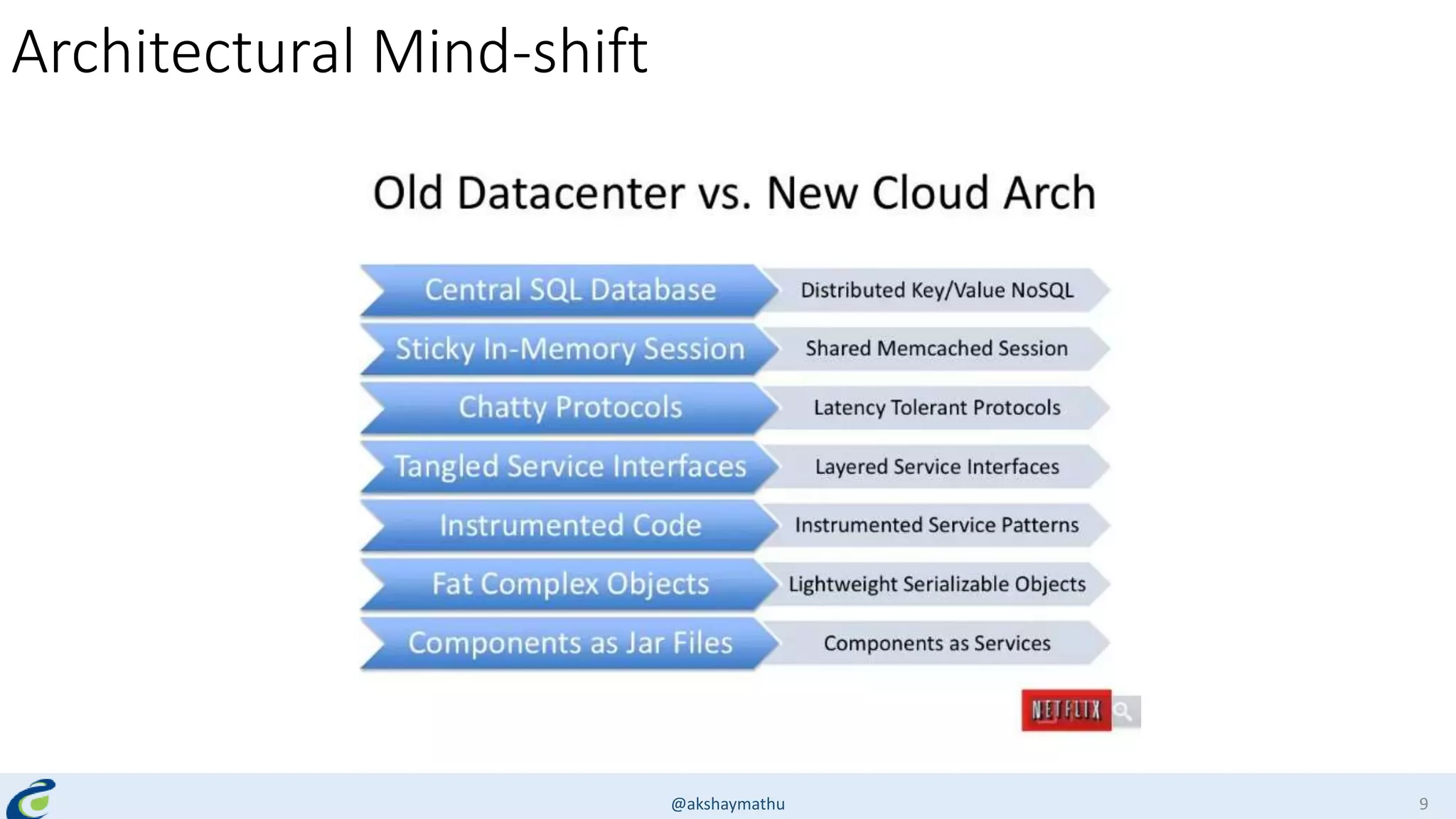
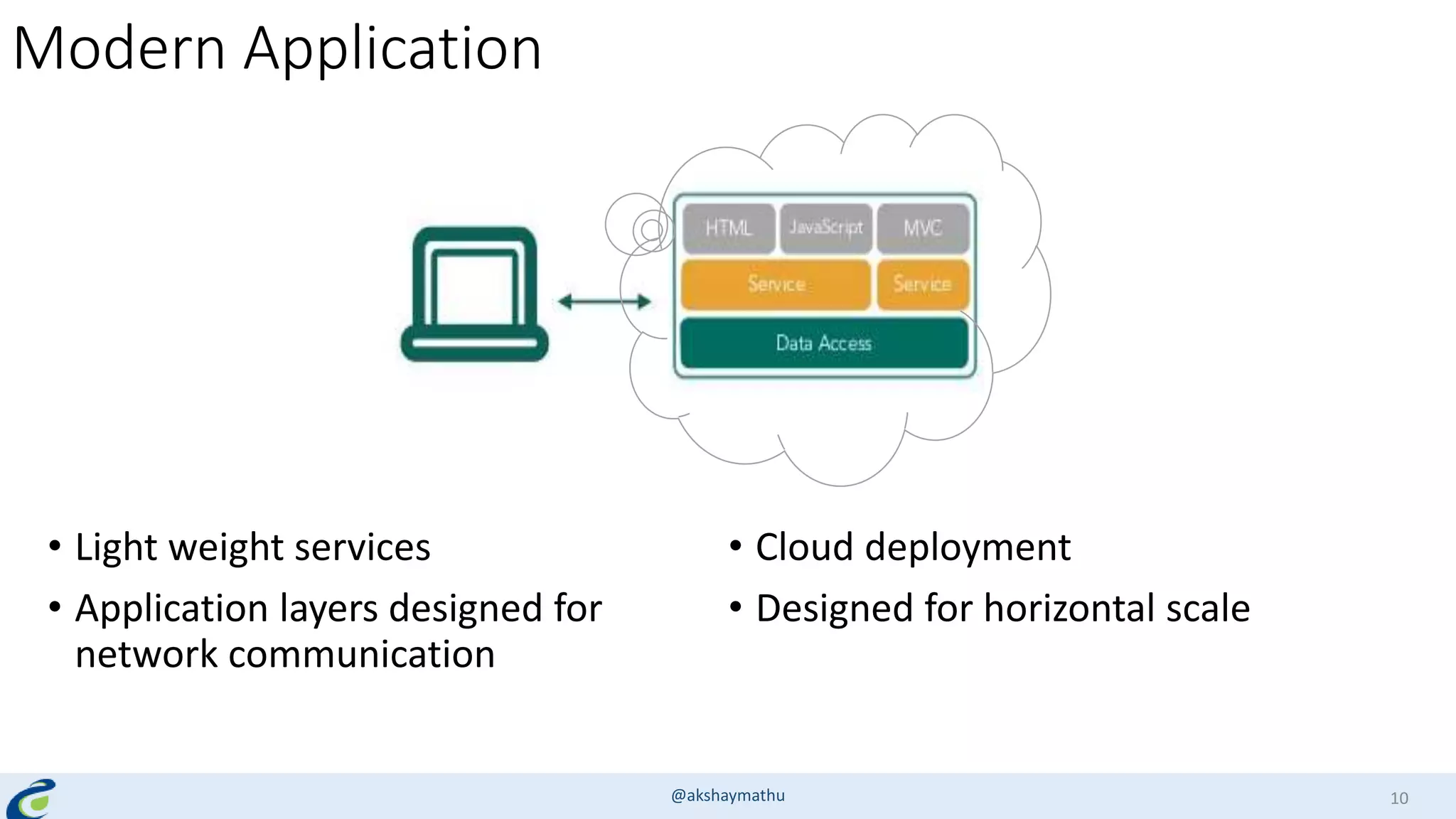
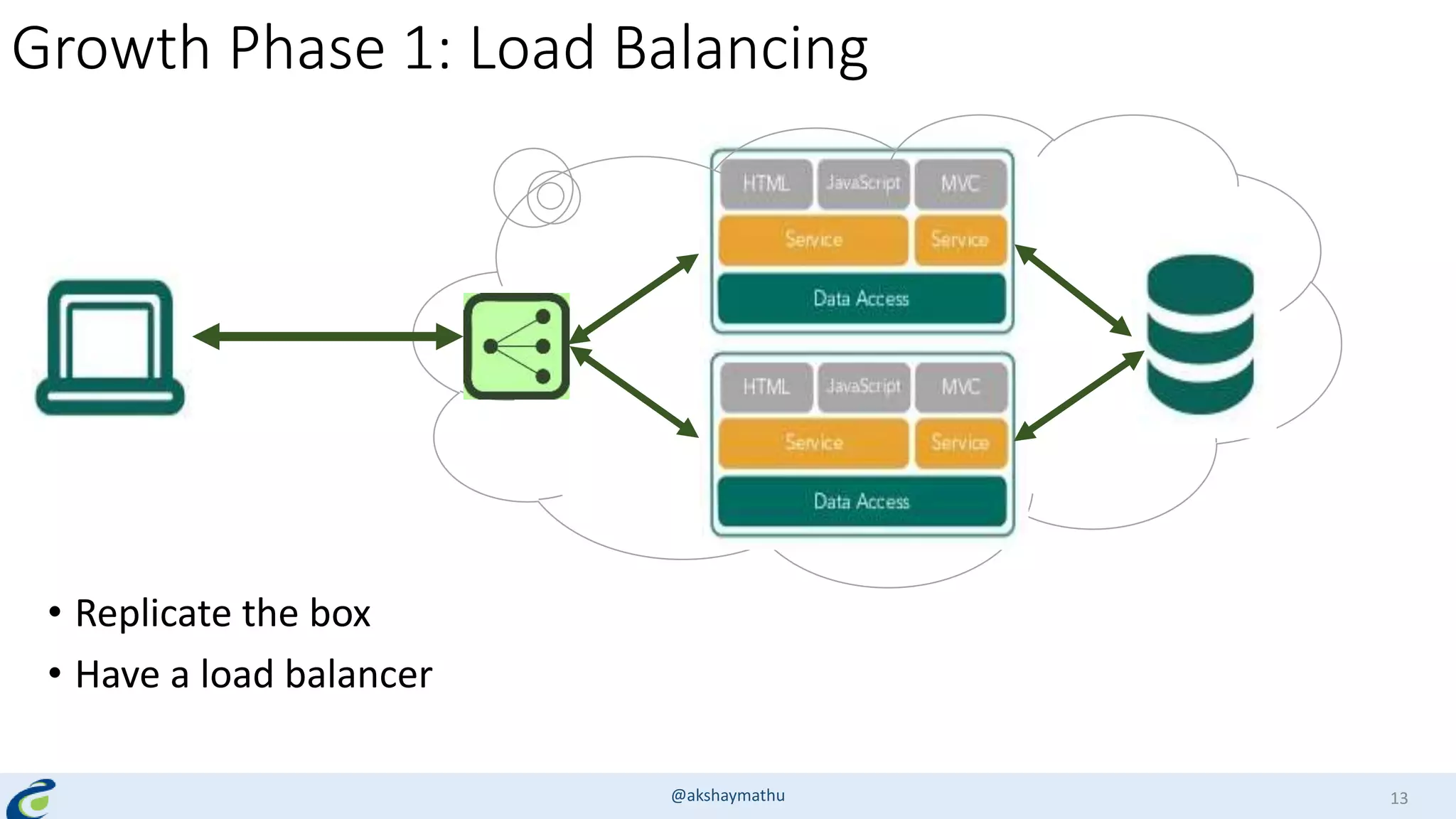
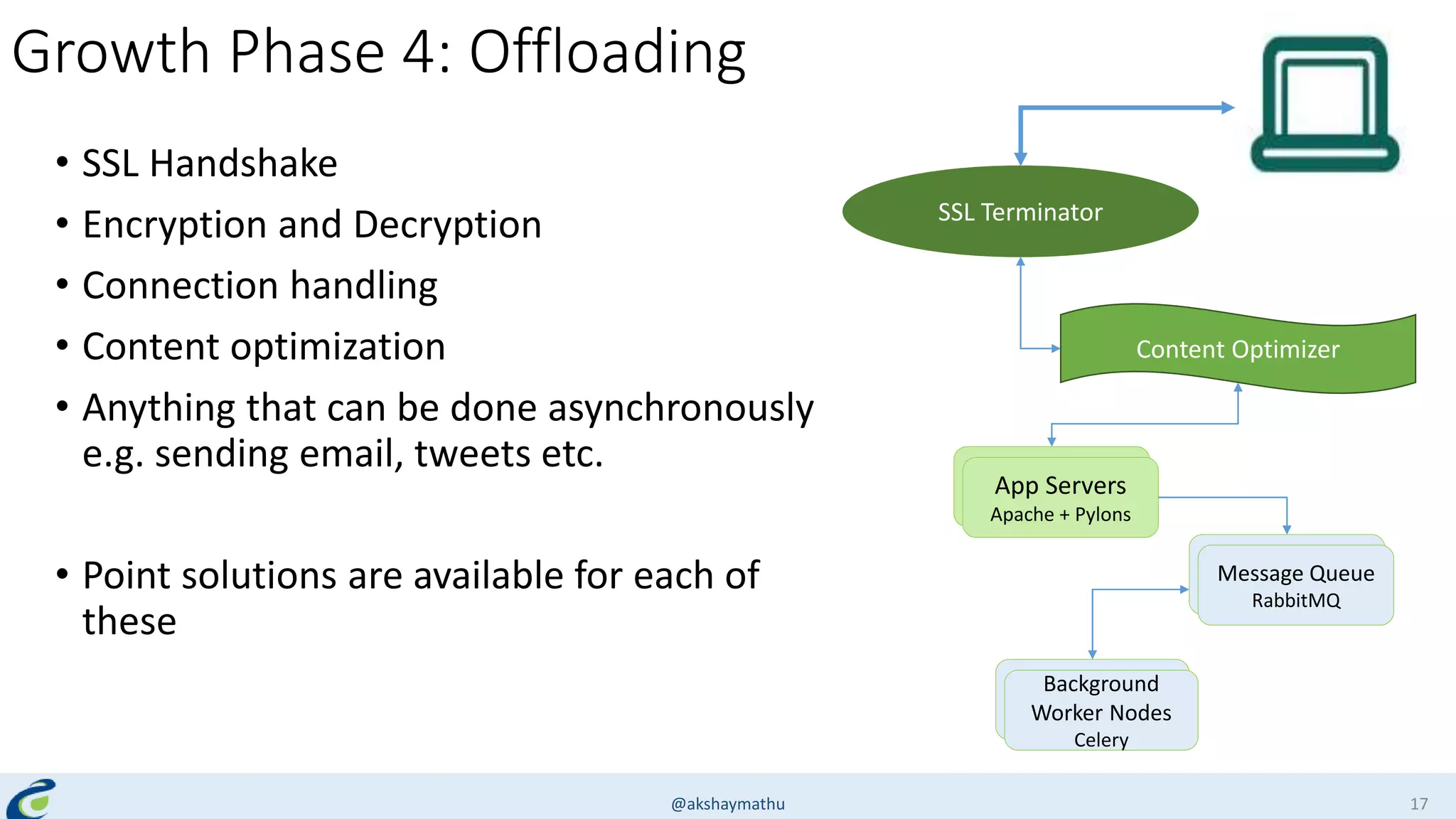
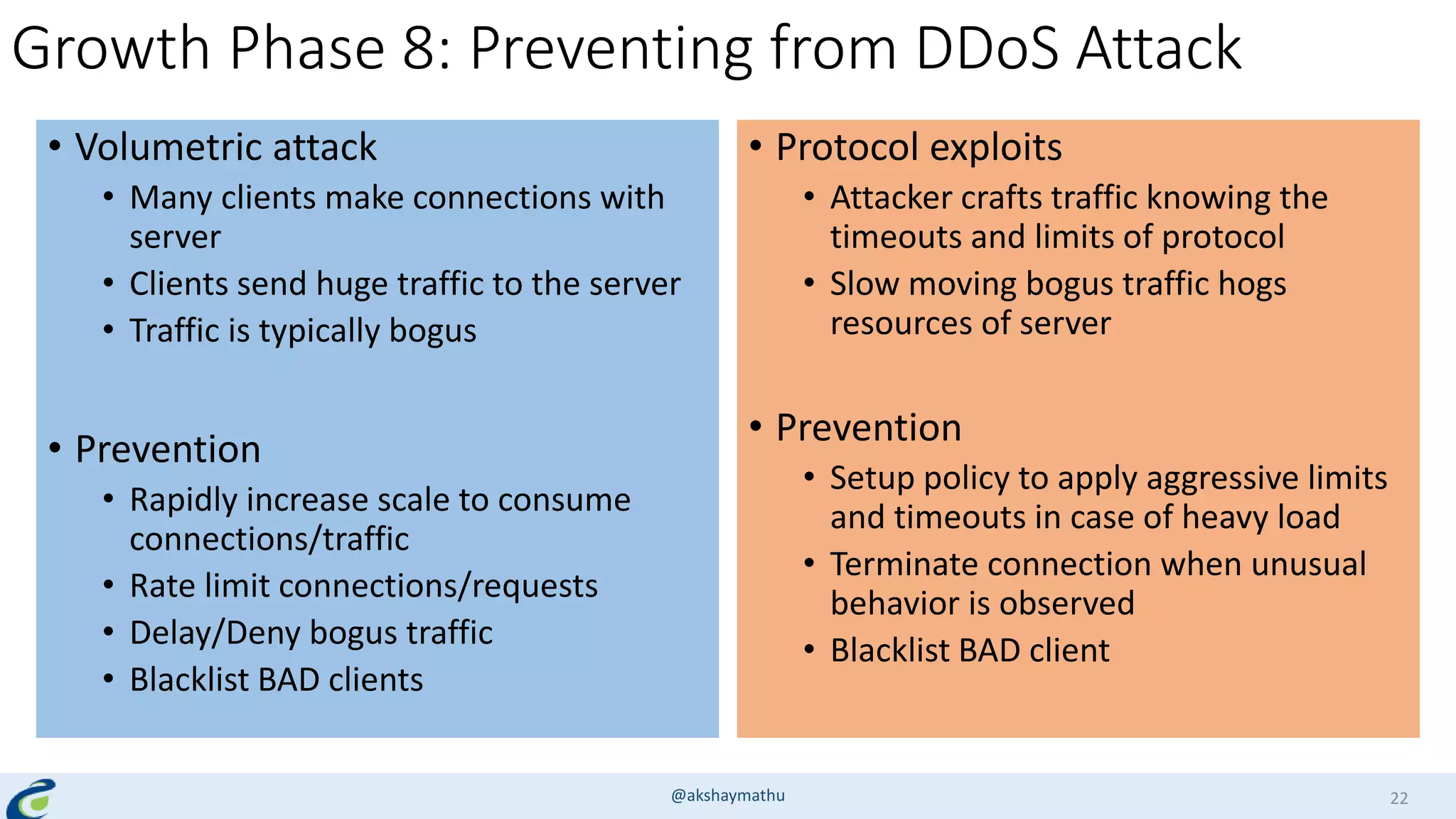
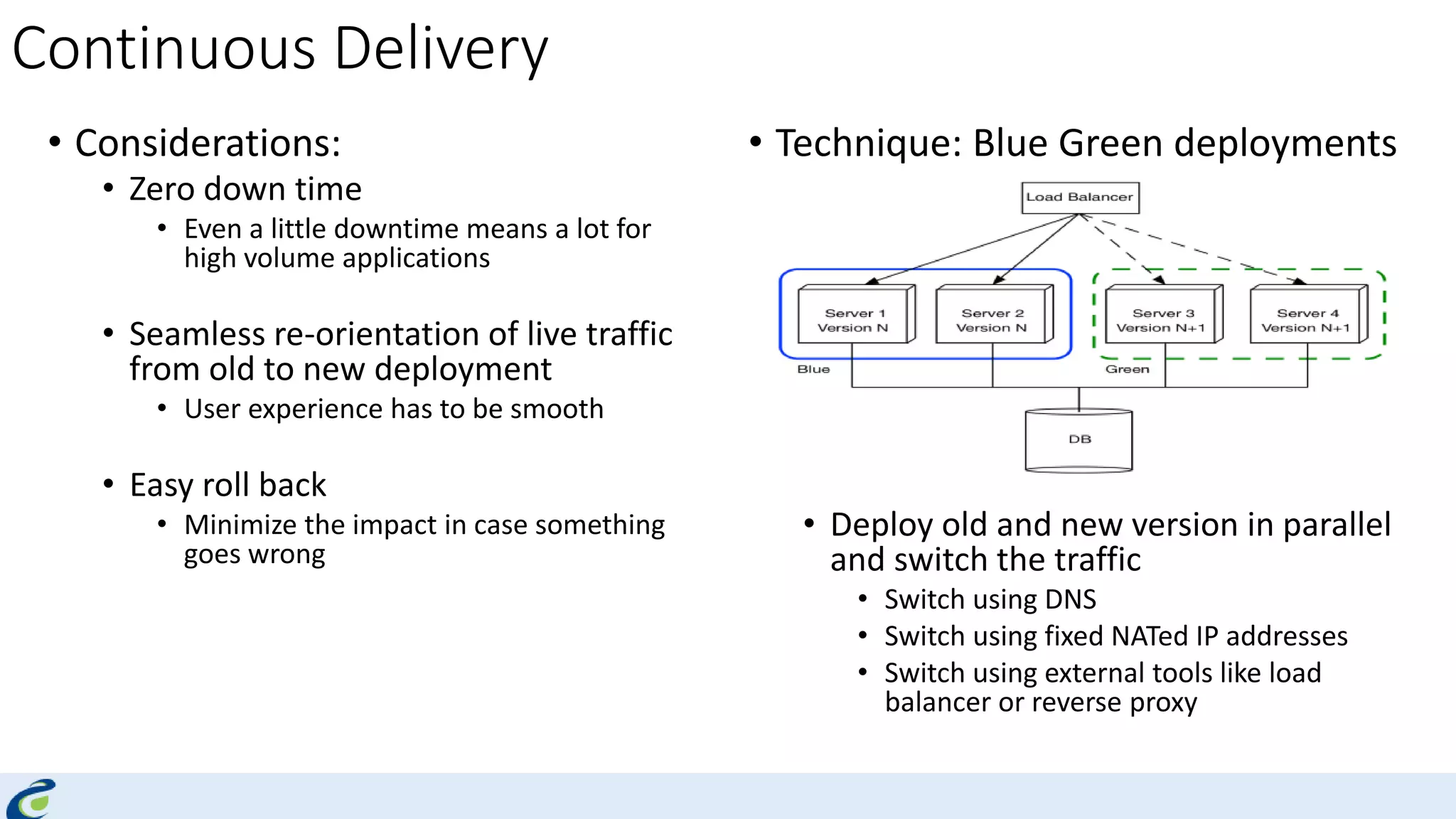
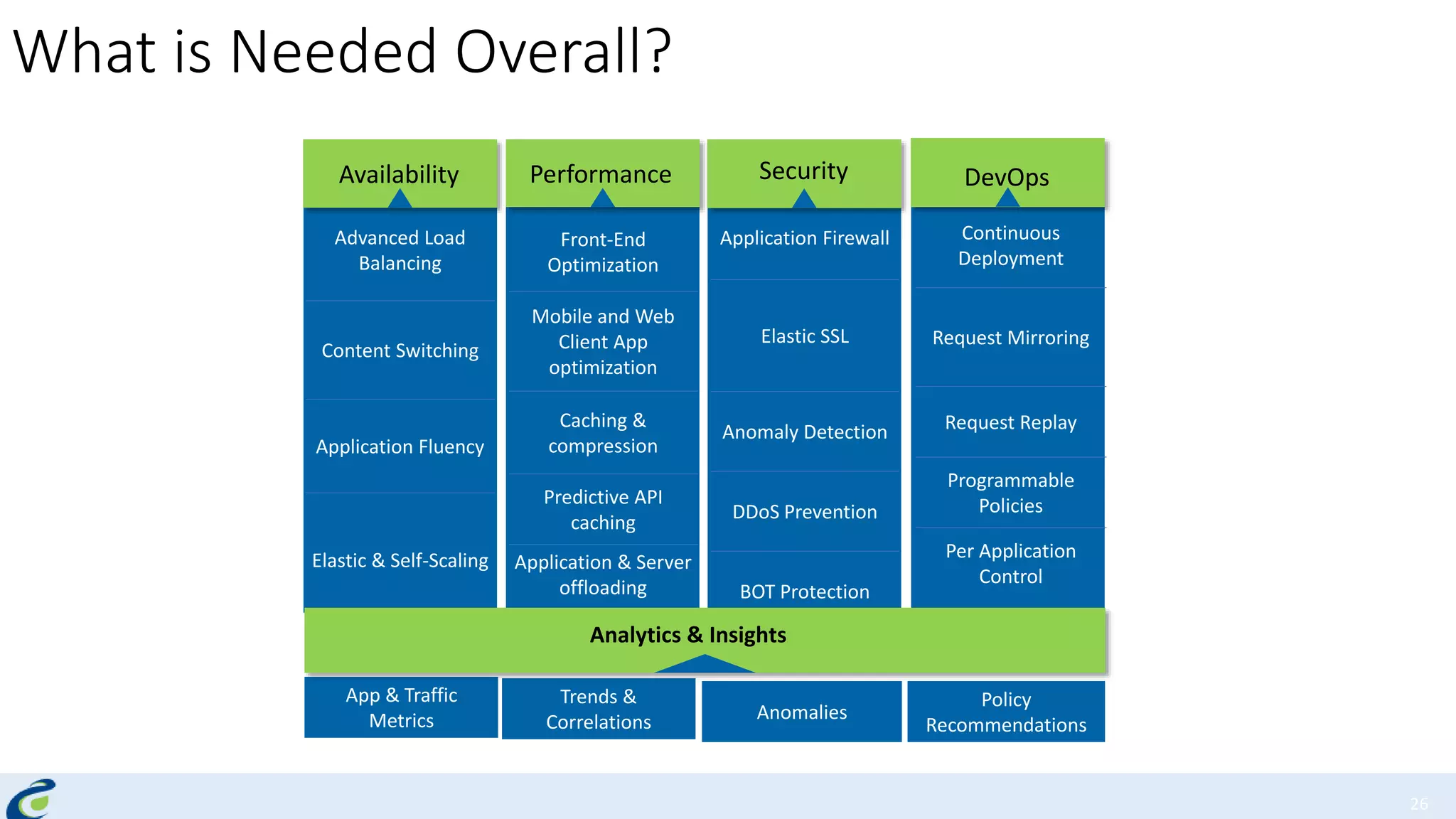
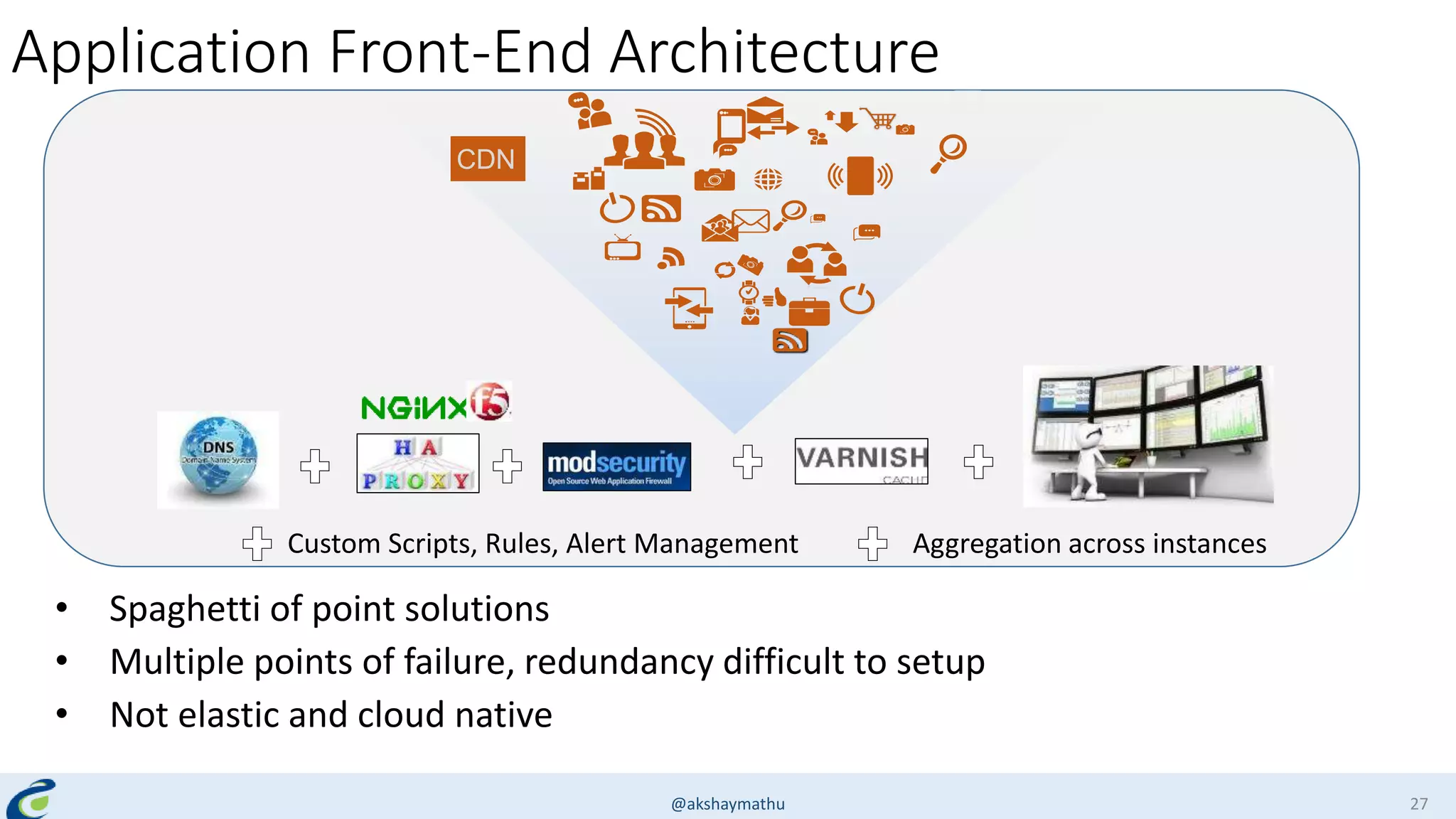
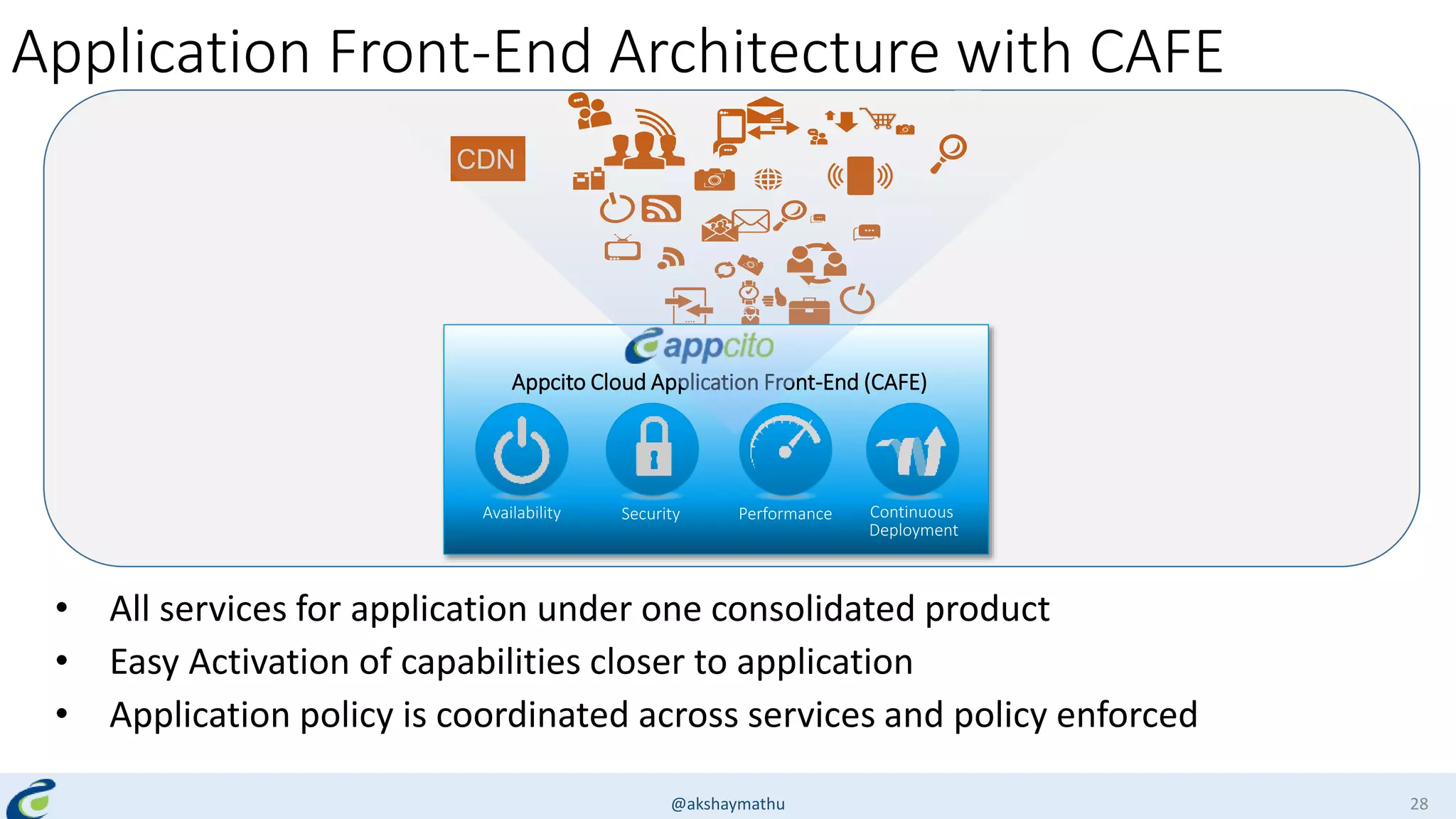
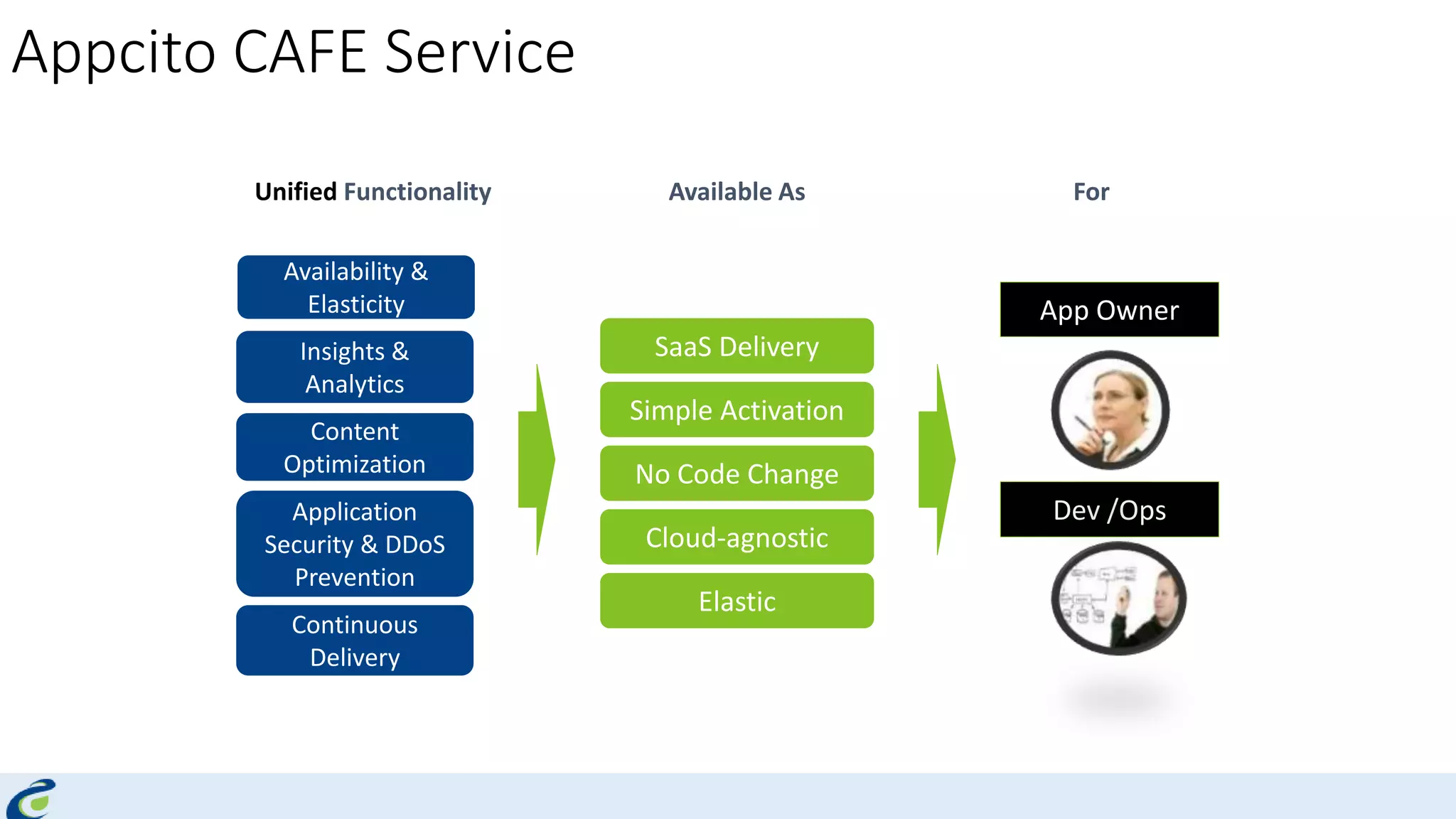
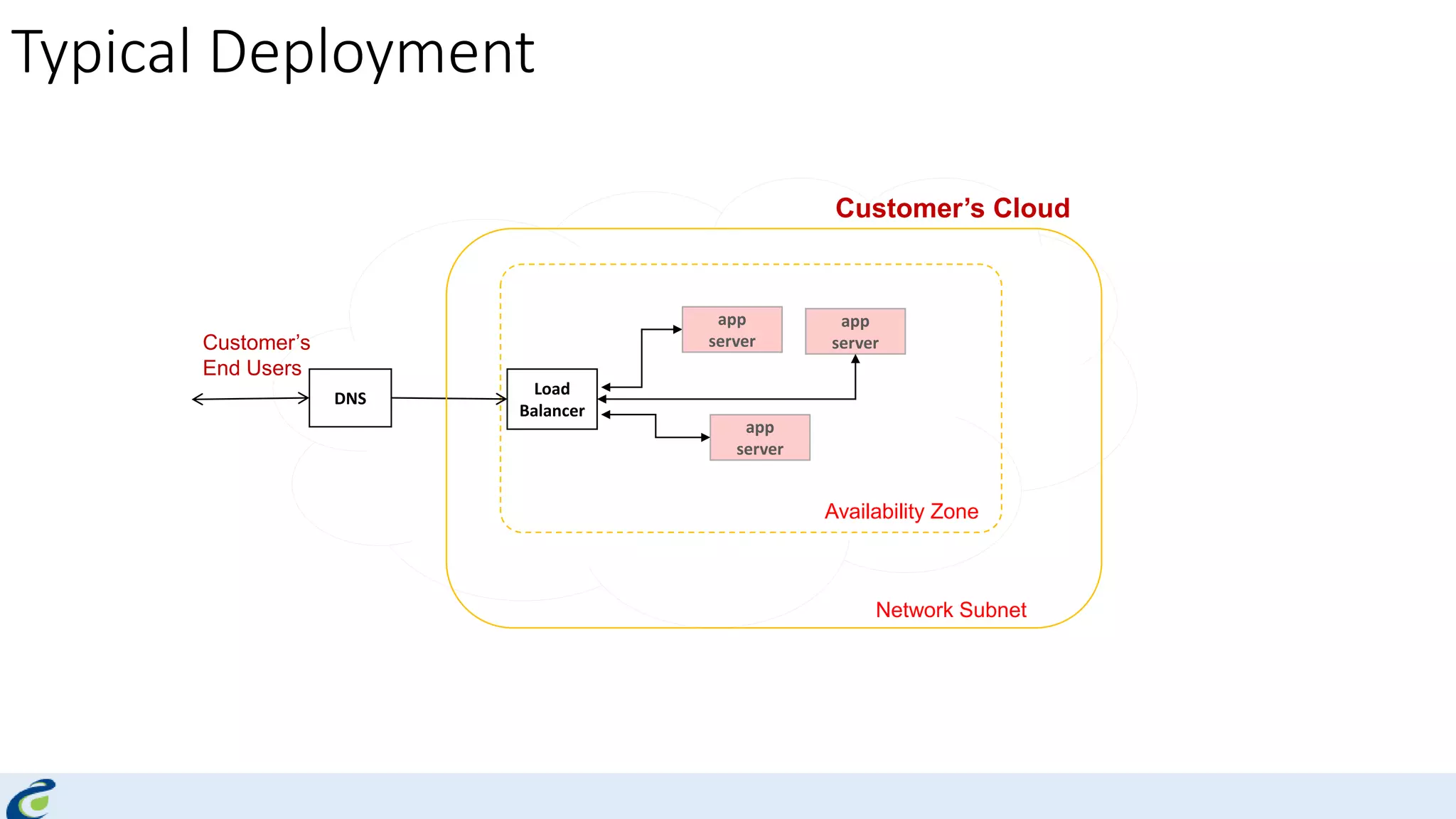
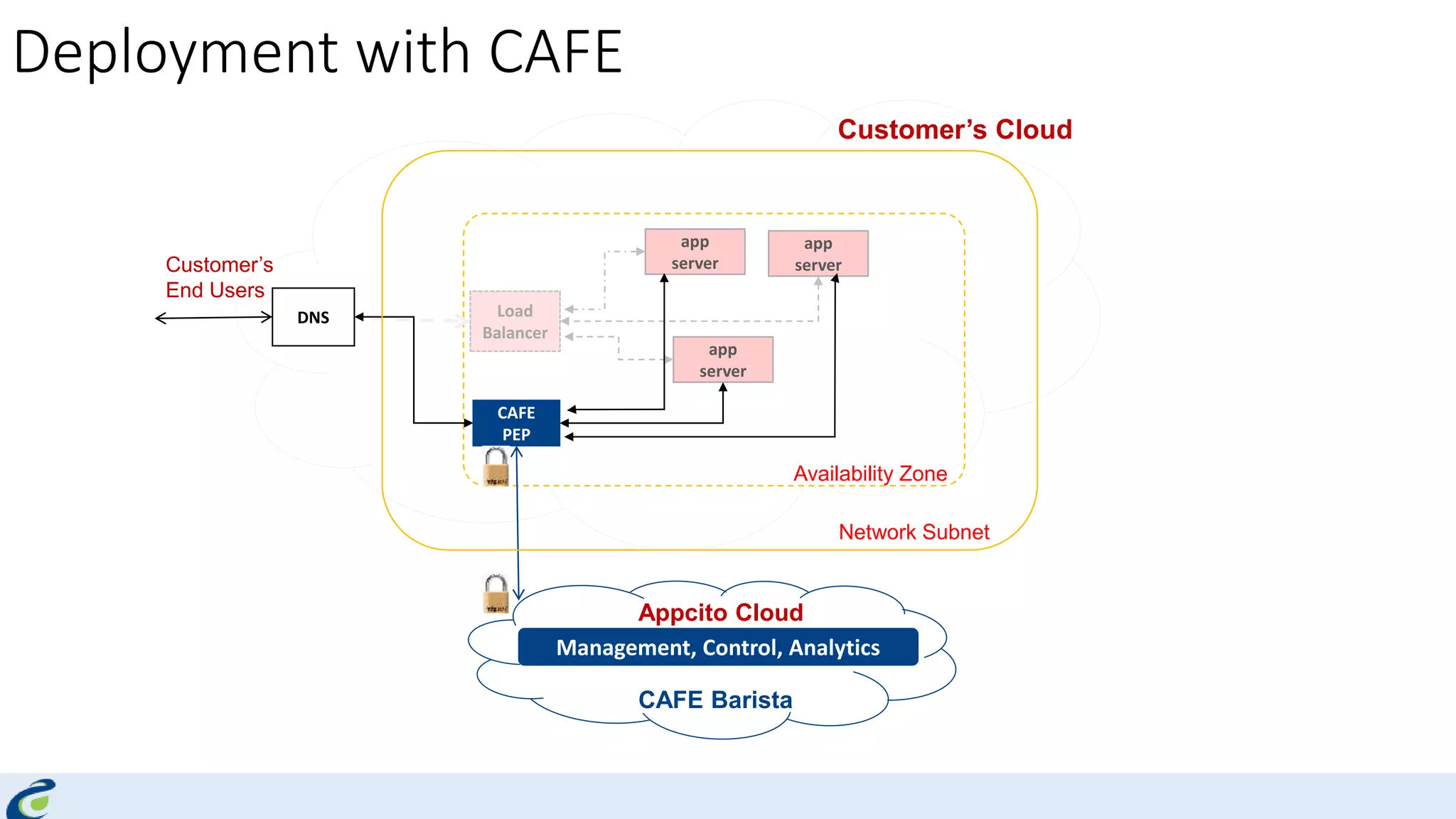
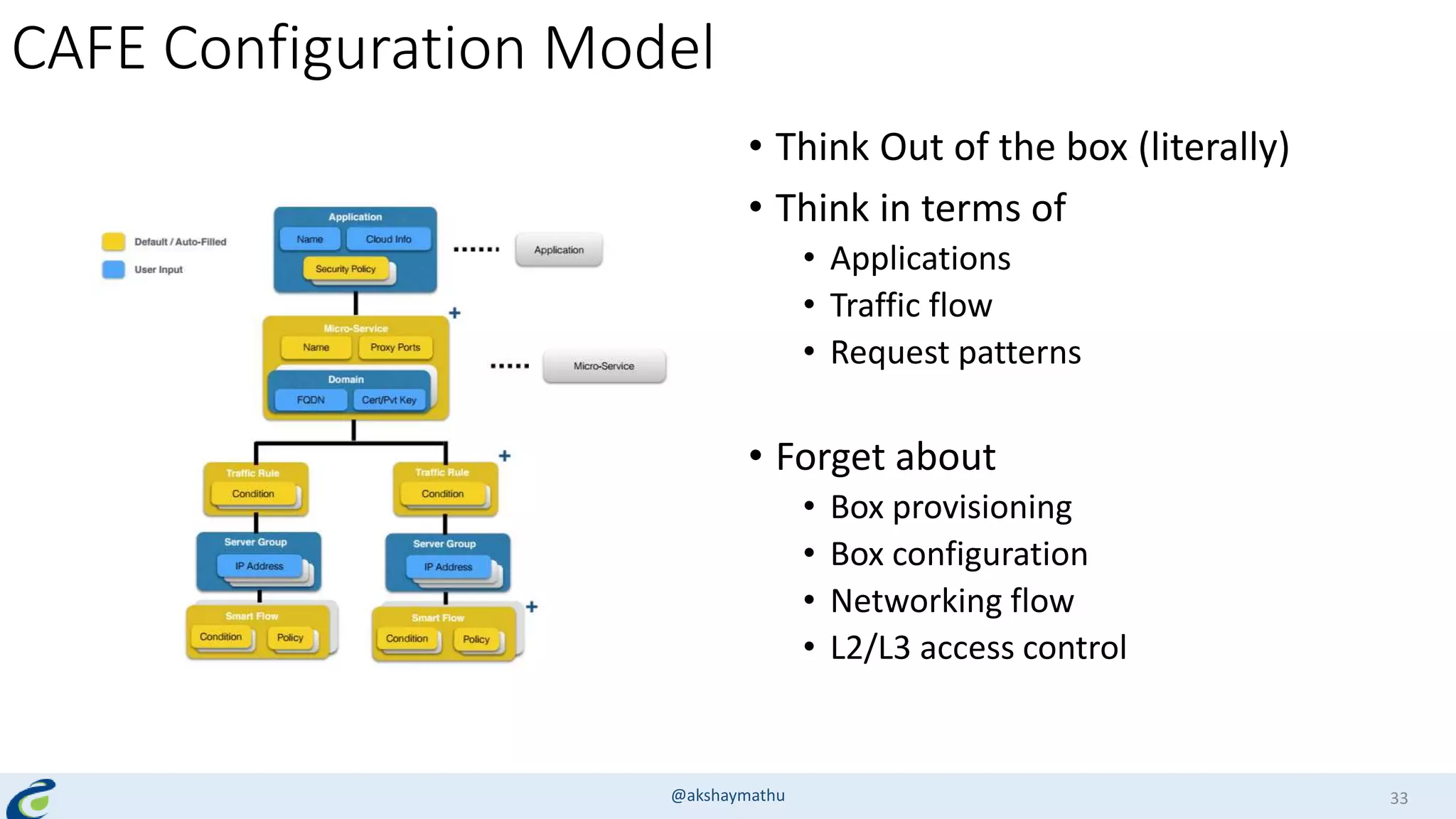
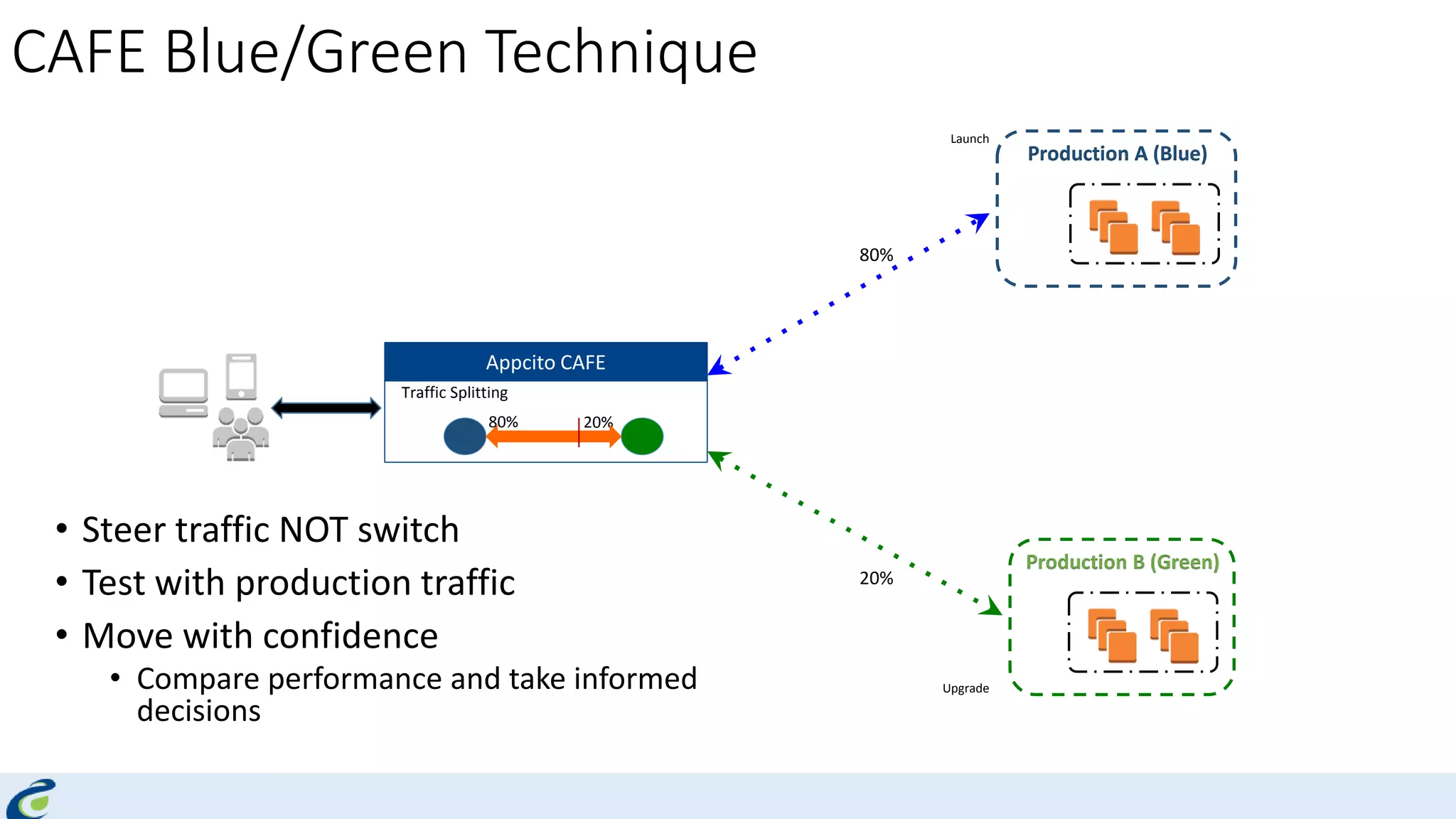
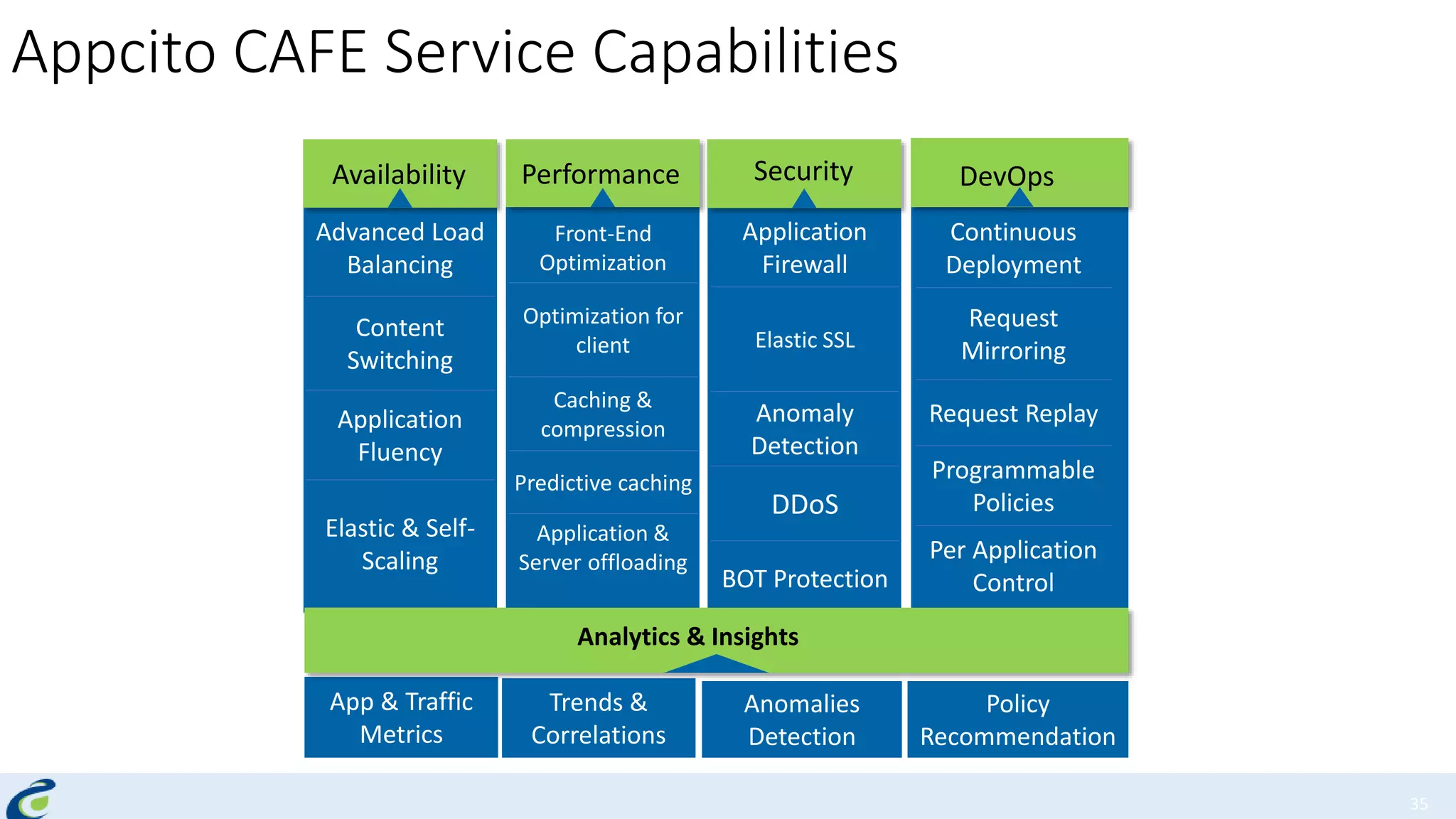
Akshay Mathur gives a presentation on techniques for scaling applications with security and visibility in the cloud. He discusses 8 growth phases applications typically go through including load balancing, gaining insights, content optimization, offloading services, content switching, preventing bot traffic and DDoS attacks, continuous delivery, and the need for a unified cloud application front end solution to manage these phases. He introduces Appcito CAFE as a service that provides capabilities across availability, performance, security and DevOps to simplify application scaling in the cloud.