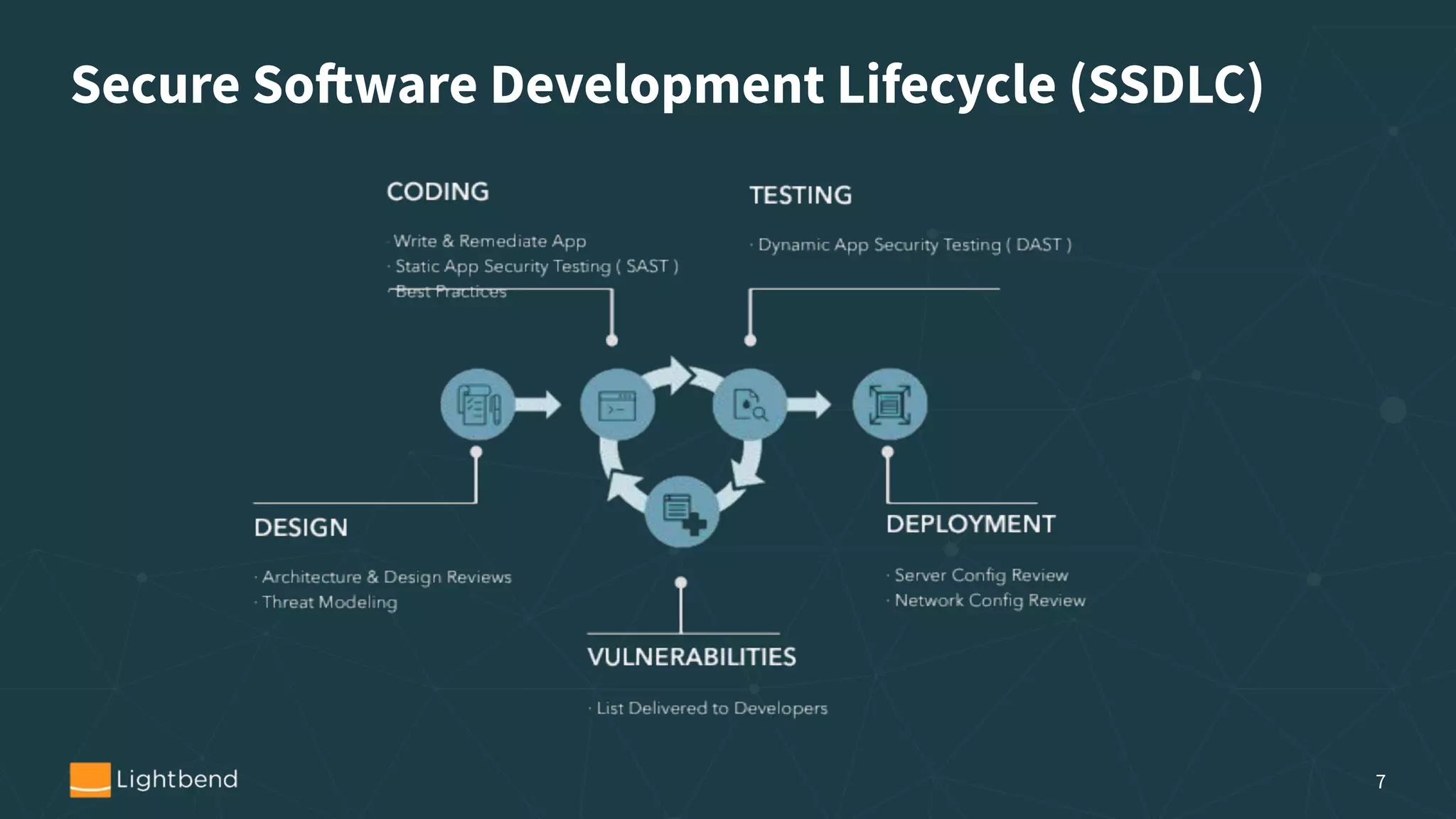
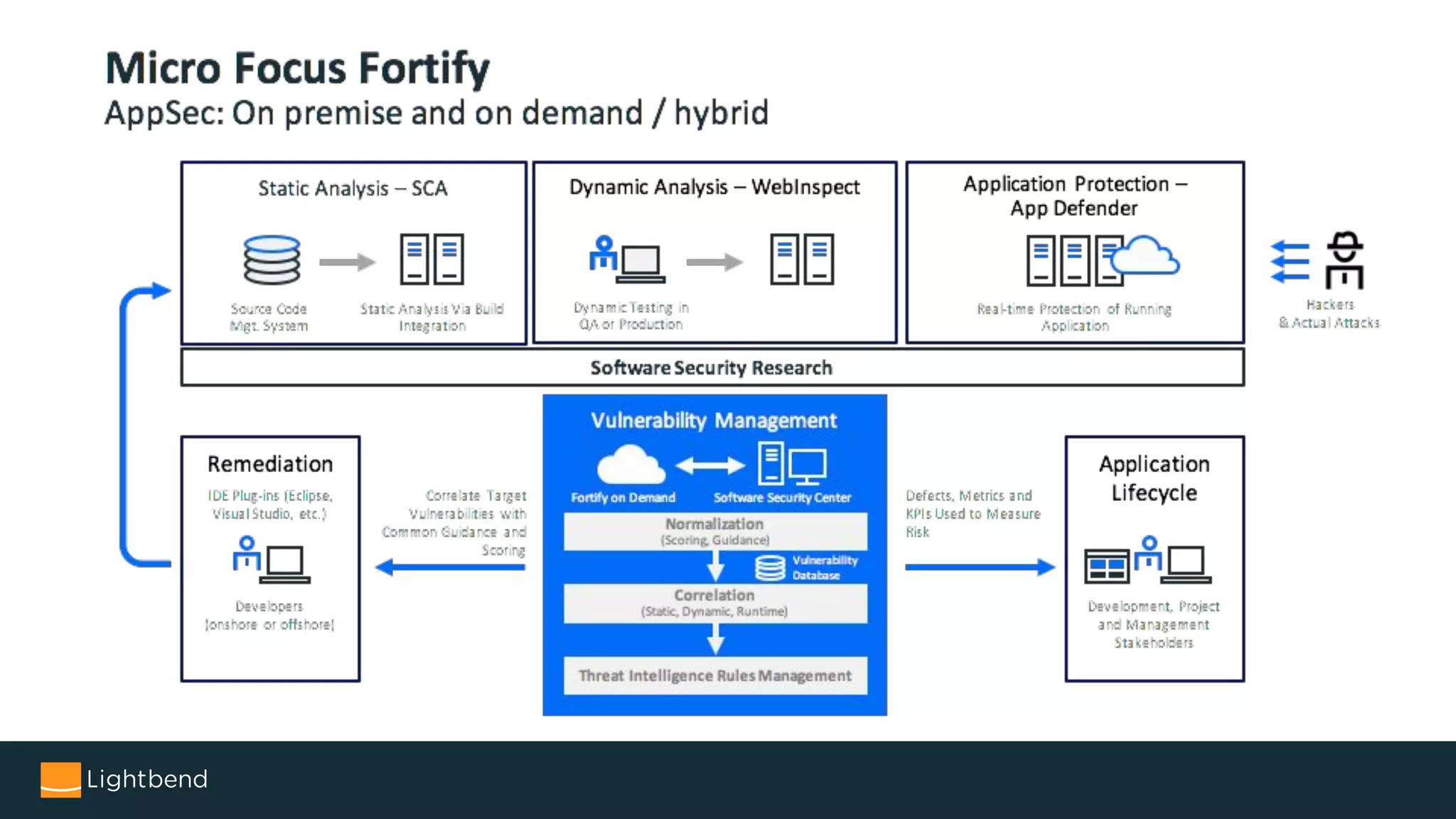
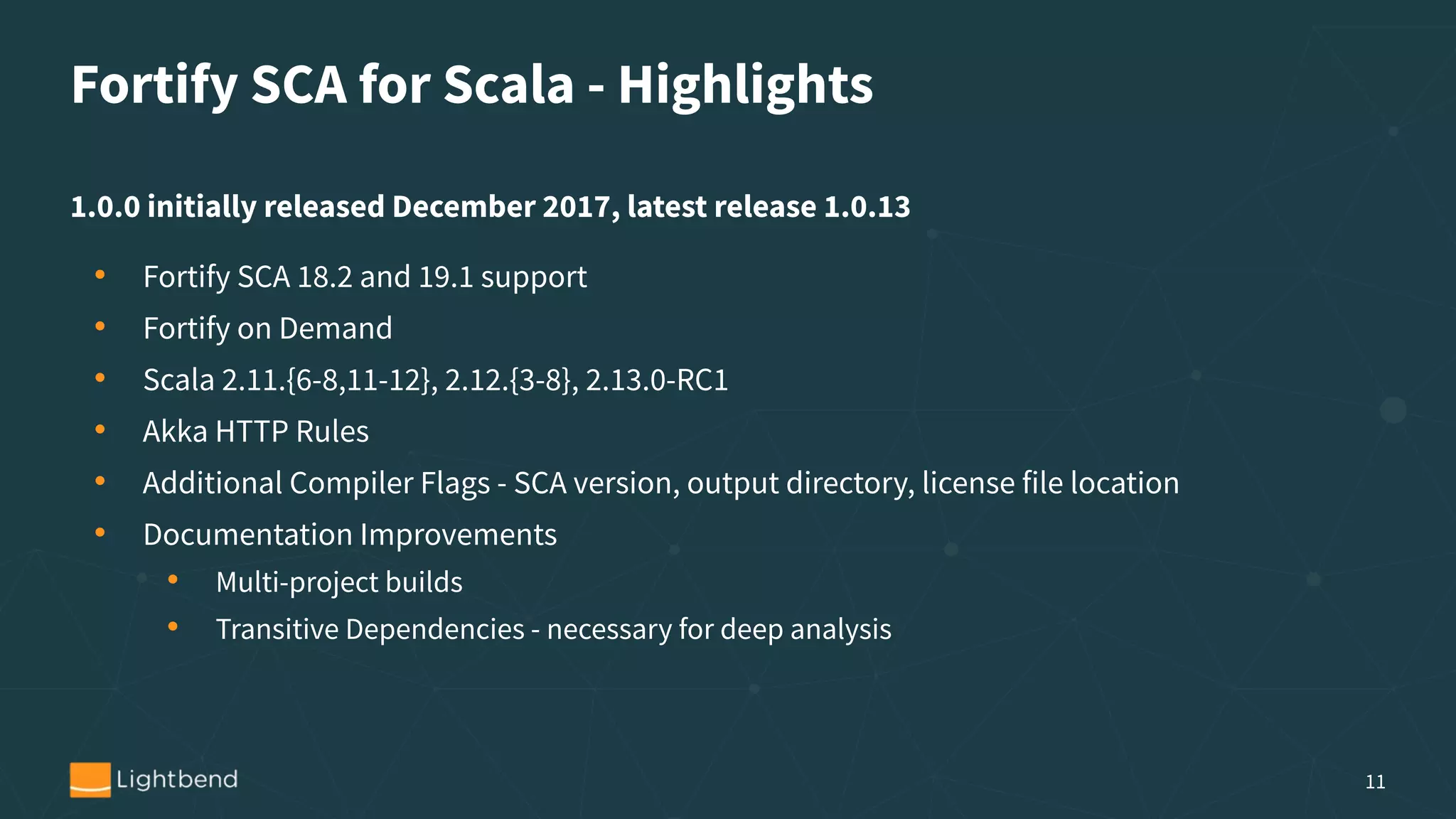
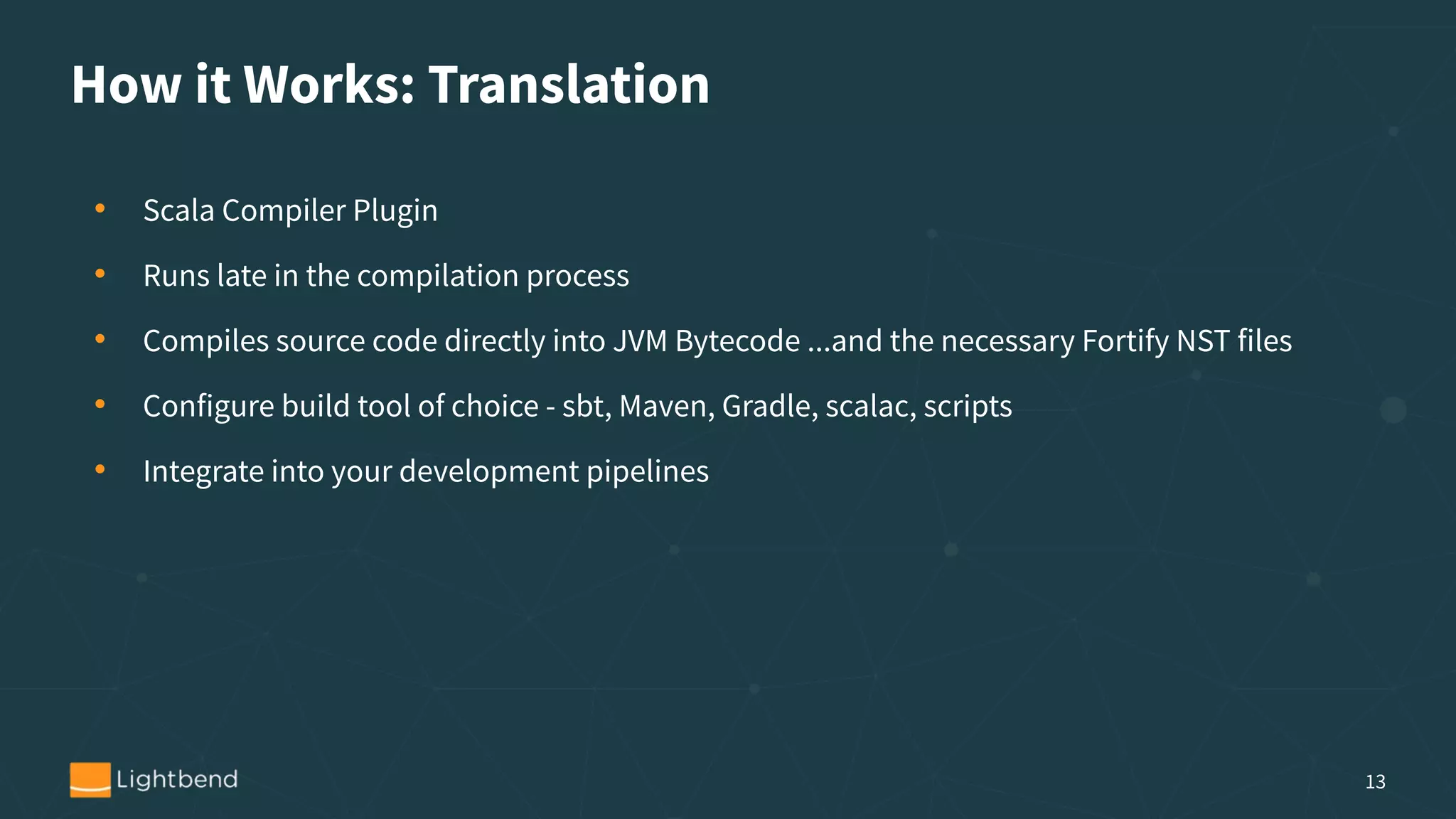
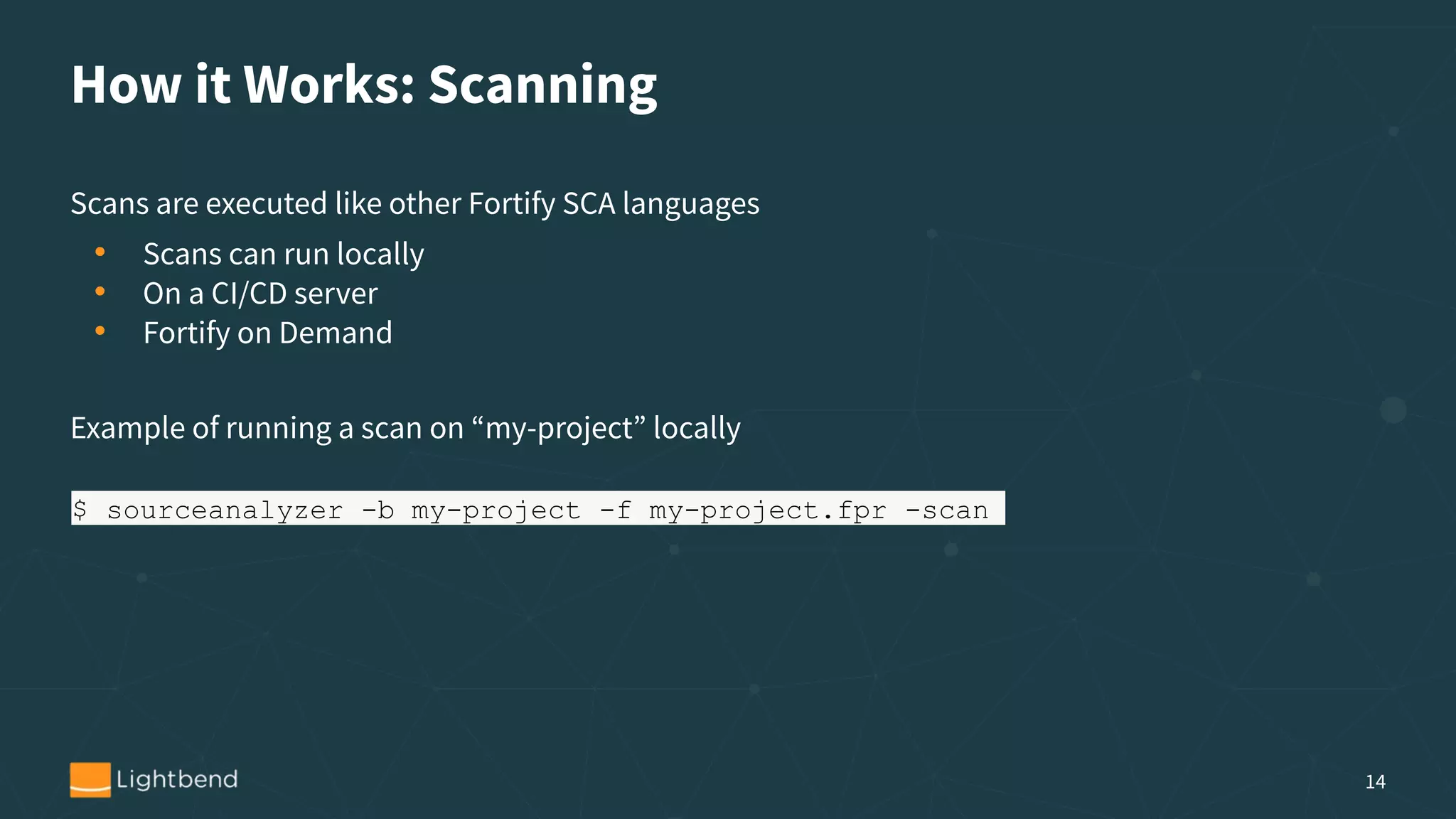
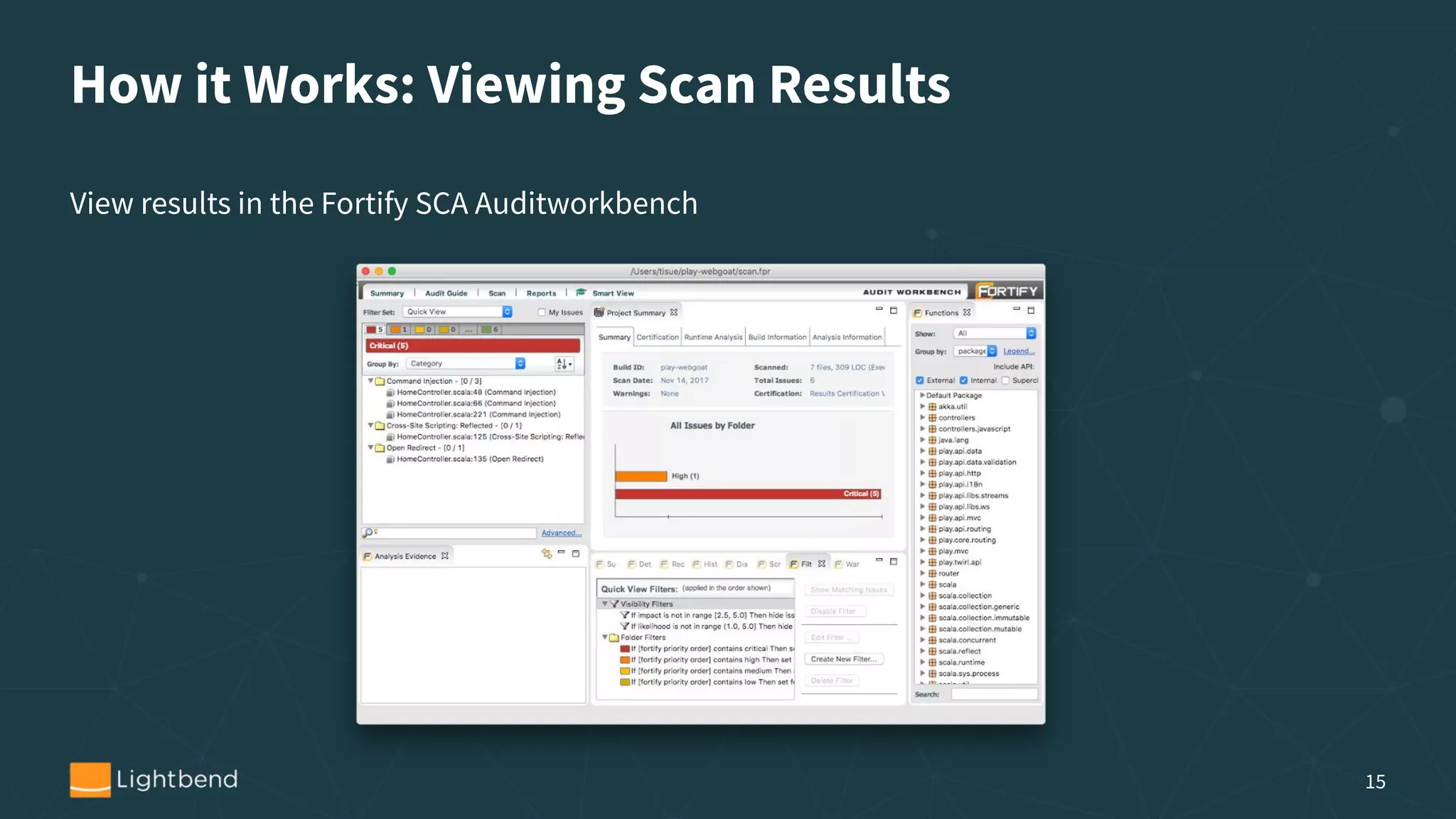
The document discusses the importance of security in software development, particularly focusing on the static analysis of Scala code using Fortify SCA. It highlights the need for organizations to proactively address security vulnerabilities, the cost implications of security breaches, and provides guidance on integrating static analysis into development pipelines. Additionally, it includes personal experiences with identity theft to emphasize vigilance in data security and offers tips for implementing effective security practices.