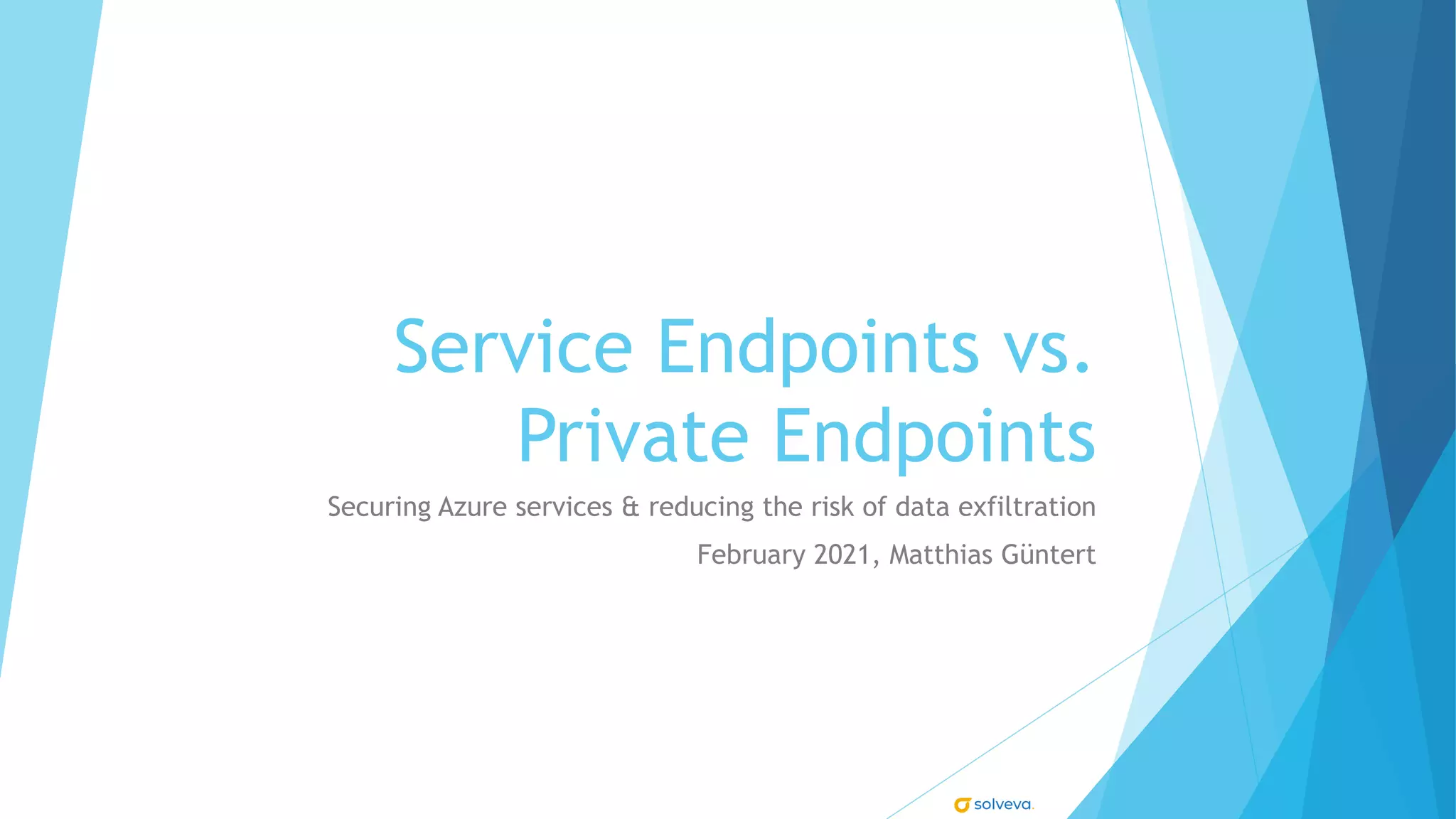
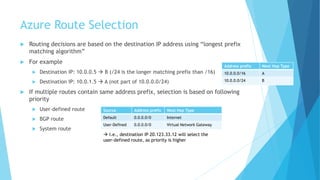
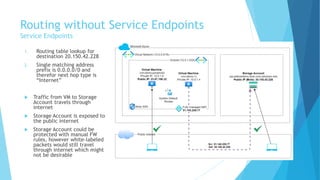
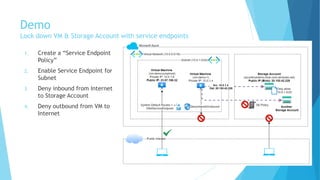
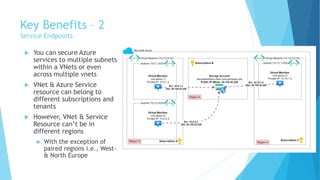
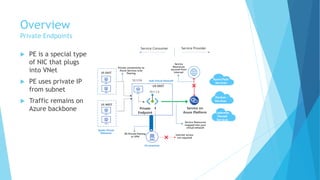
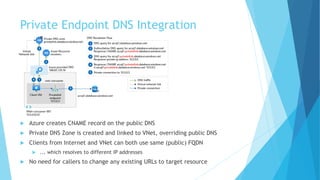
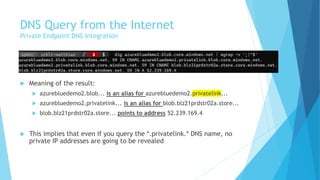
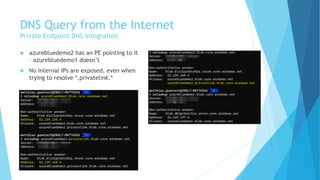
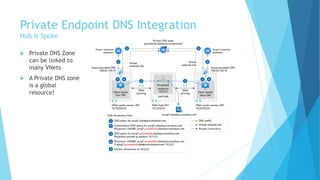
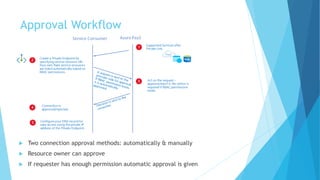
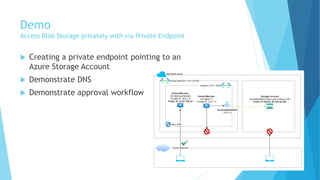
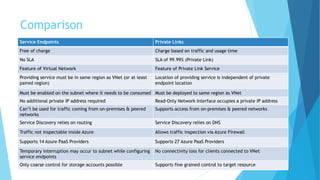
The document explains the differences between Azure Service Endpoints and Private Endpoints, detailing their functionalities, benefits, and limitations. Service Endpoints provide secure connectivity to Azure services without internet exposure and allow for optimized routing, while Private Endpoints create a private link to services, ensuring data exfiltration protection. A side-by-side comparison is provided to help users decide when to use each option based on their needs and conditions.