Embed presentation



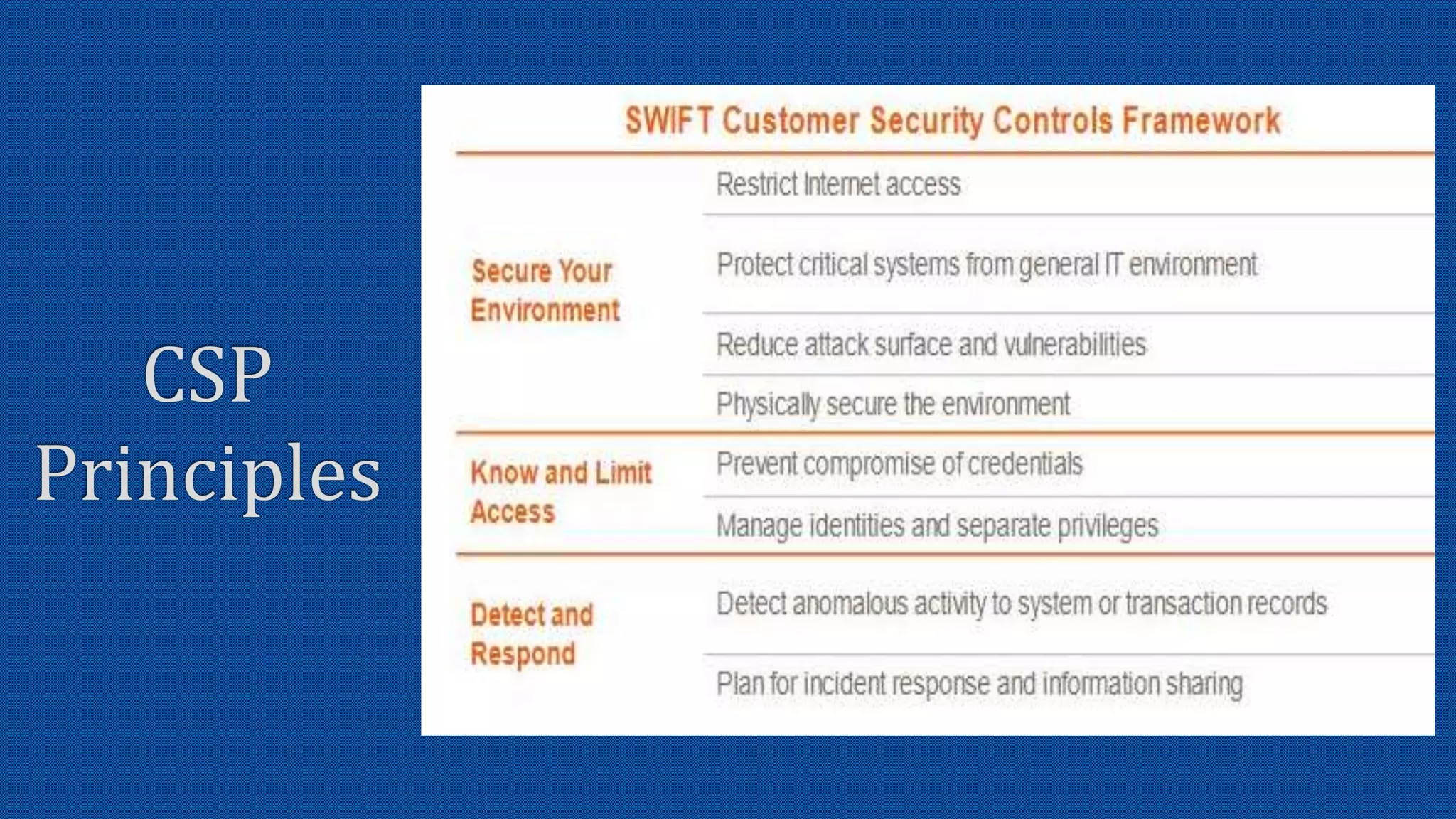
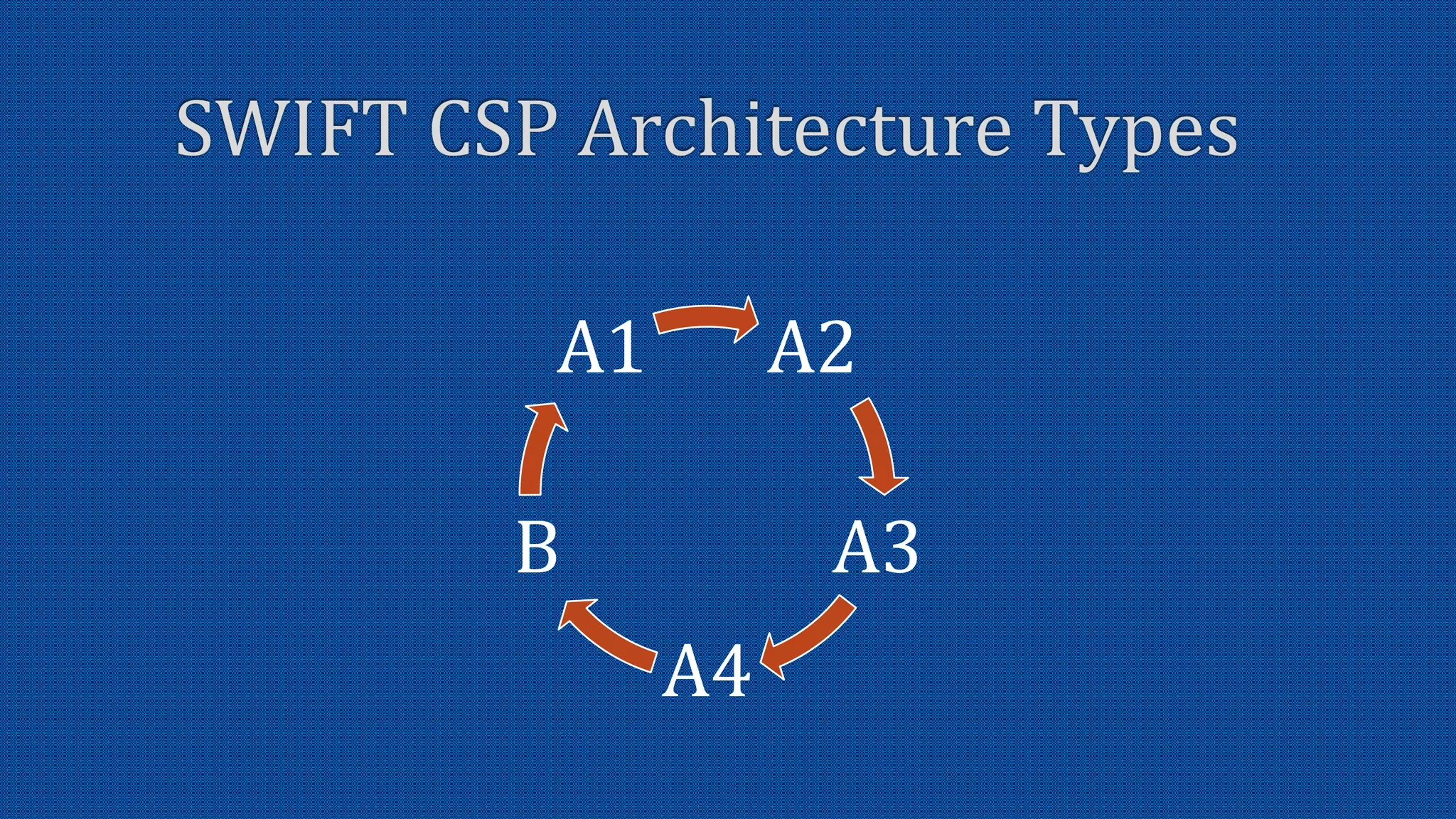
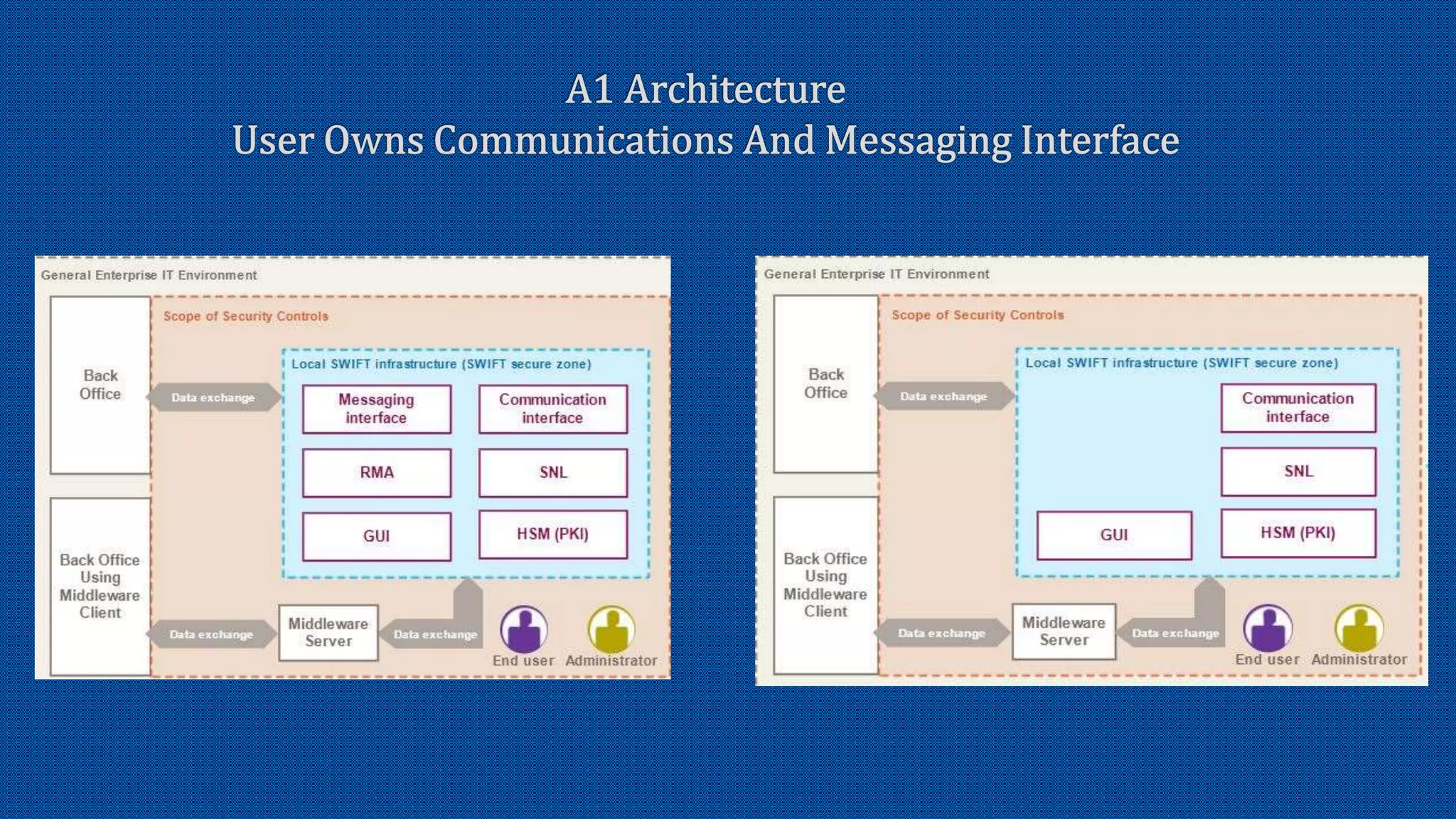
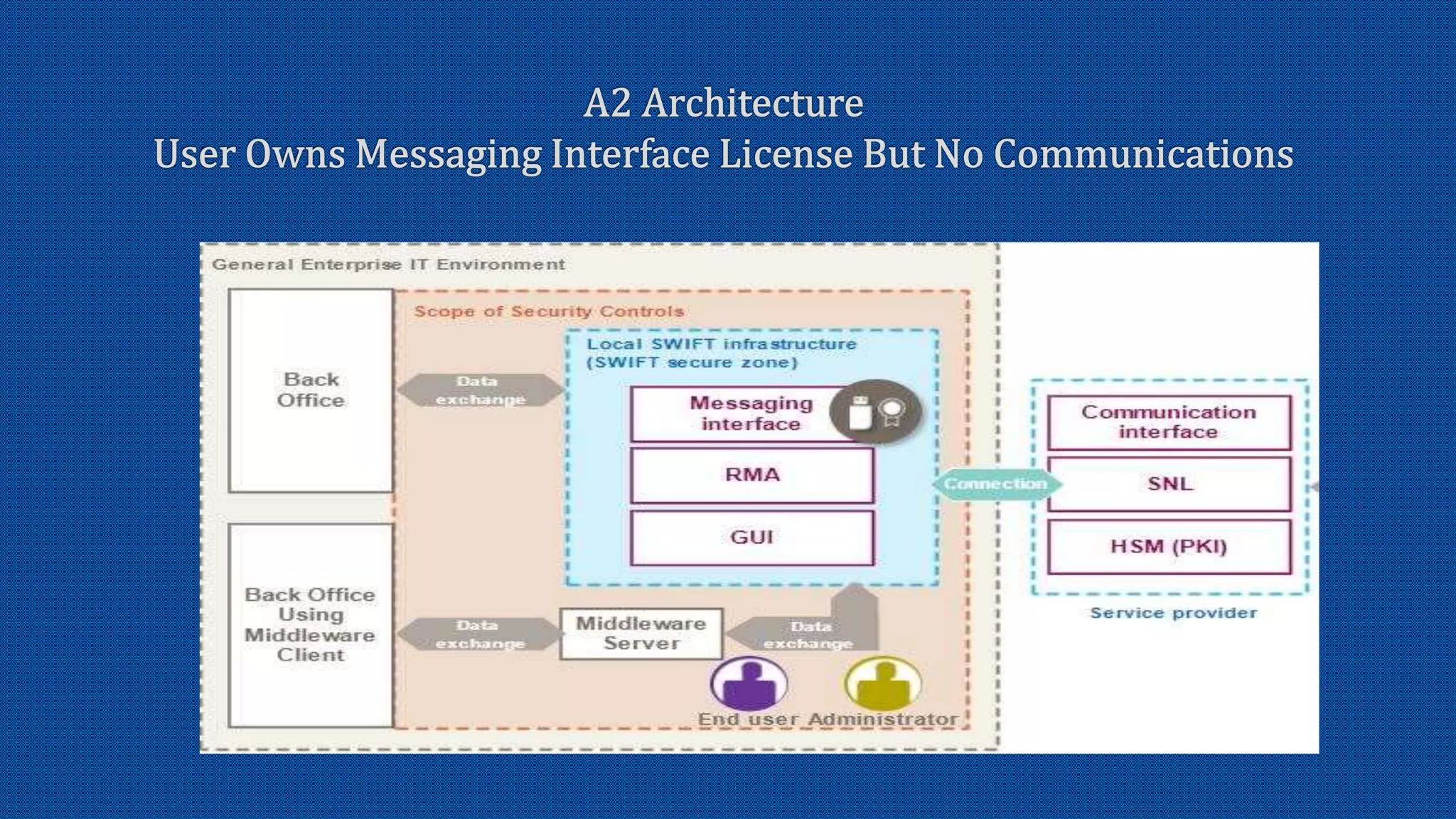
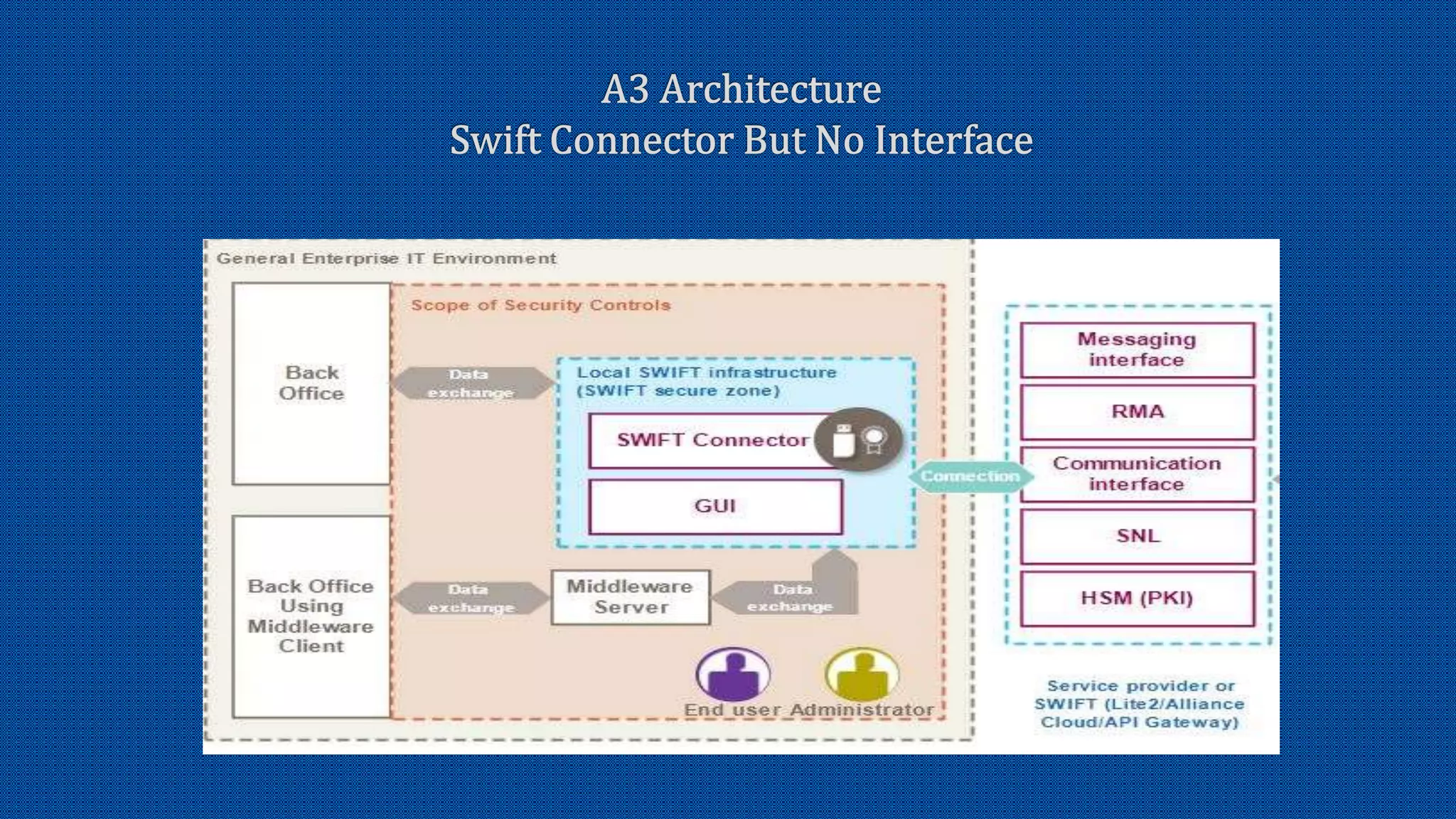
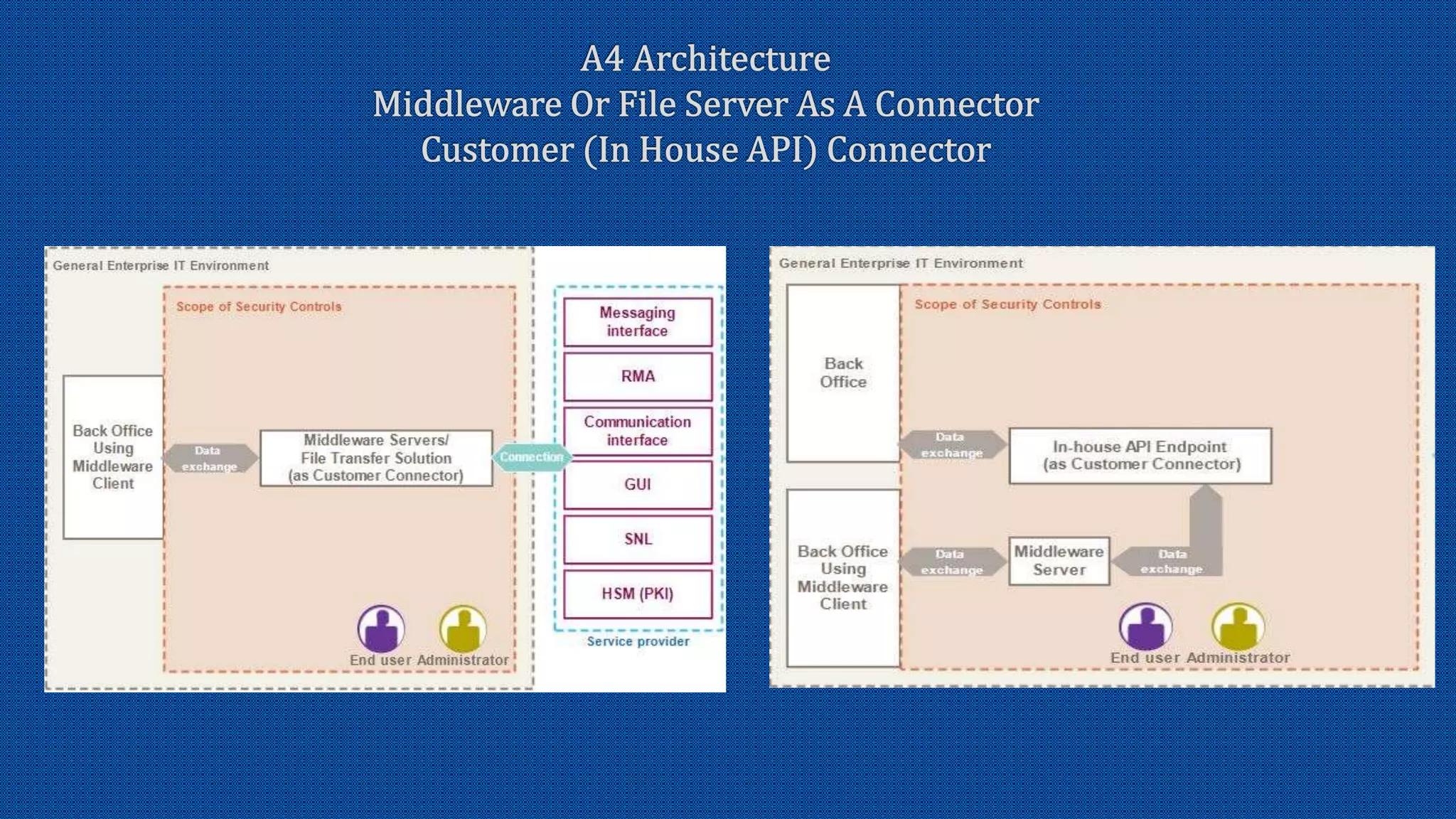
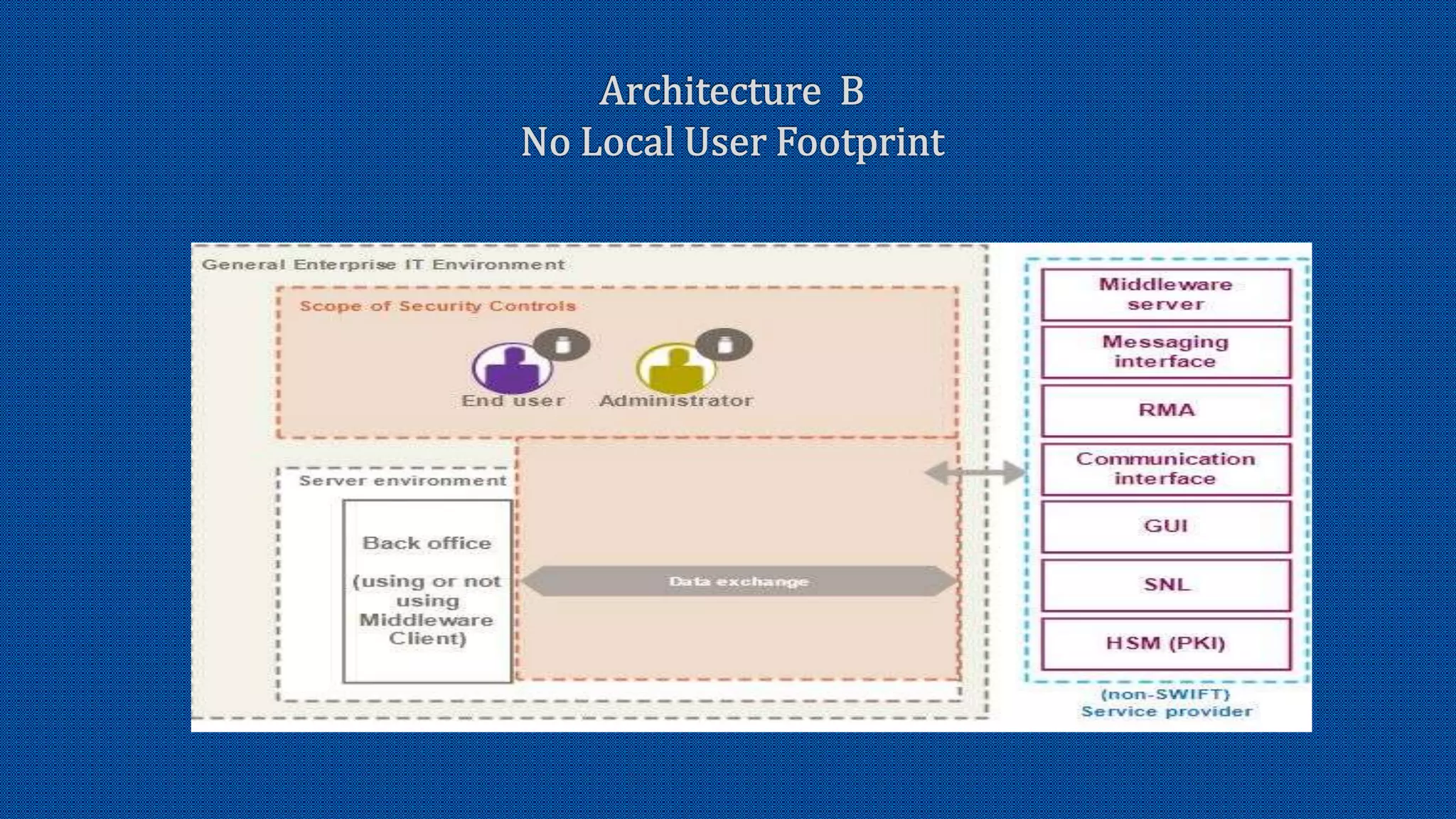
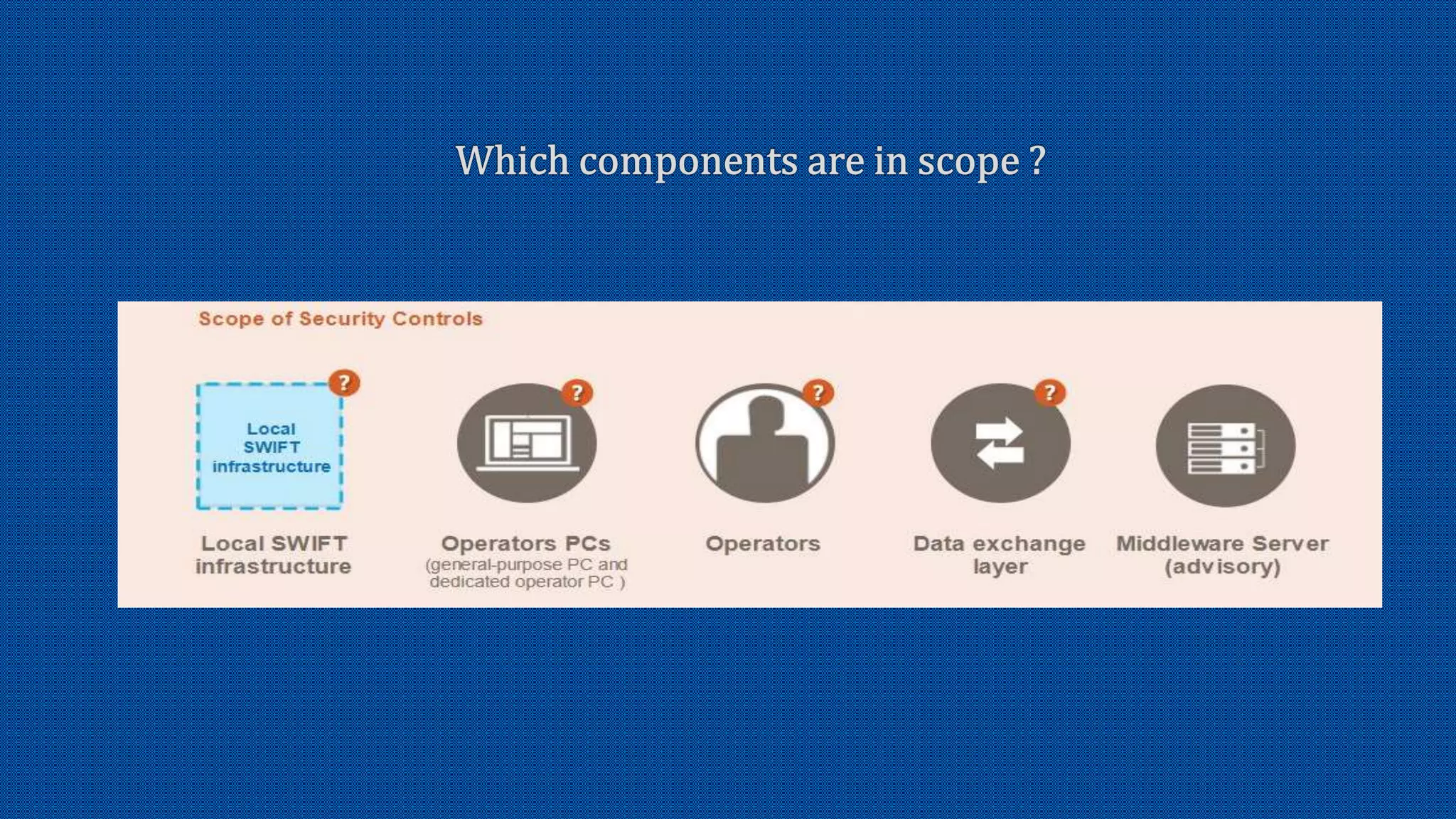
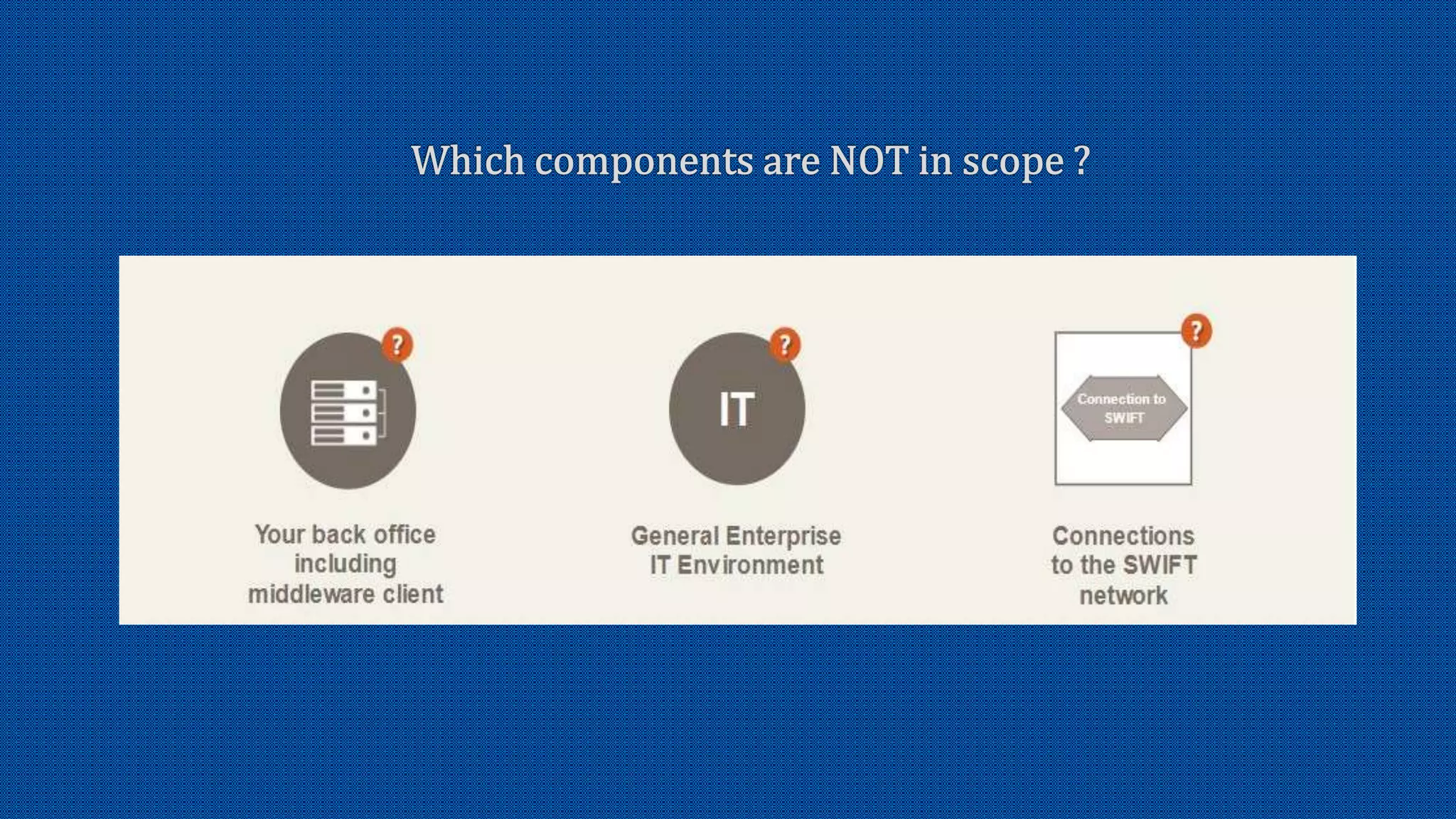



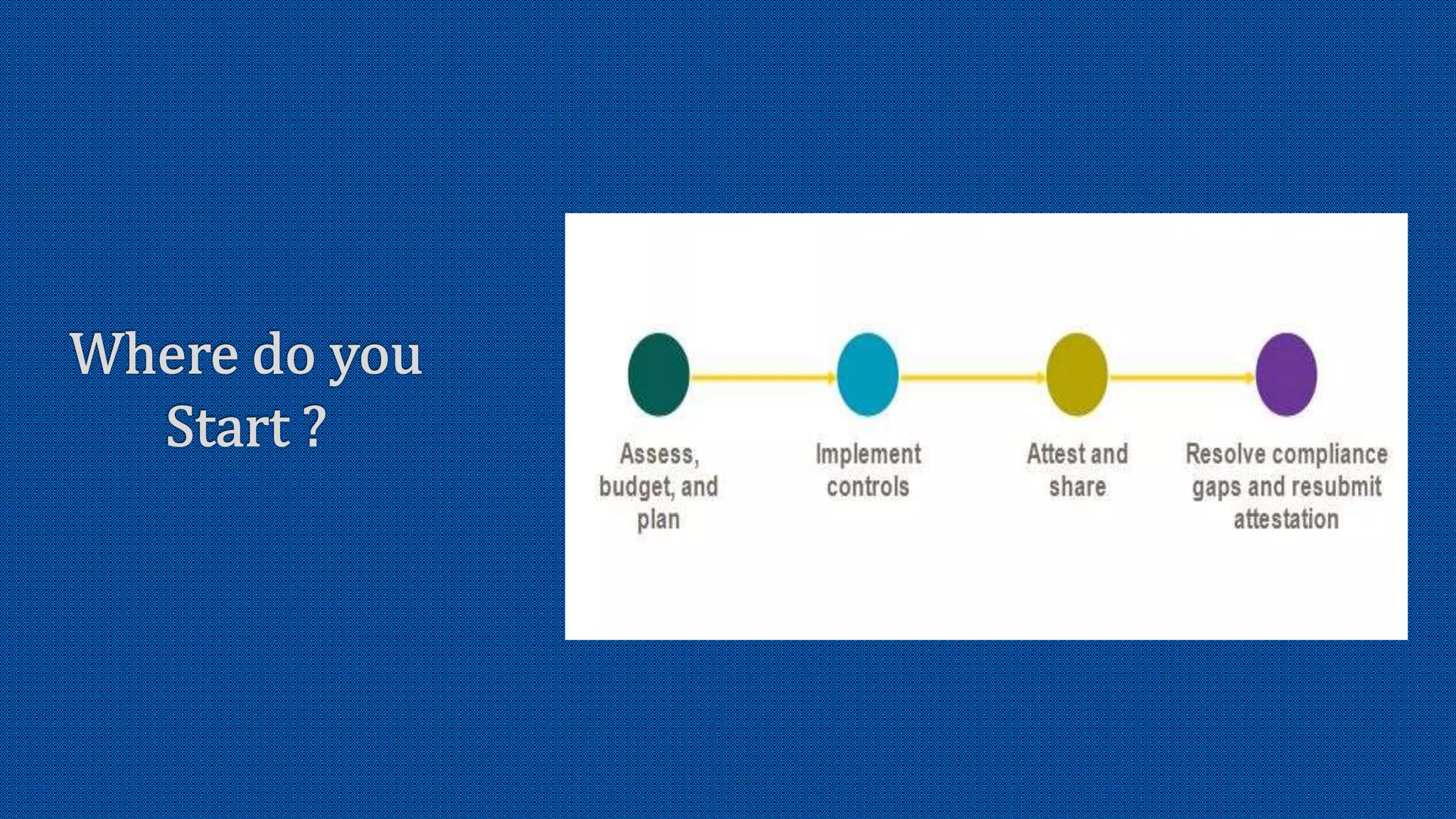
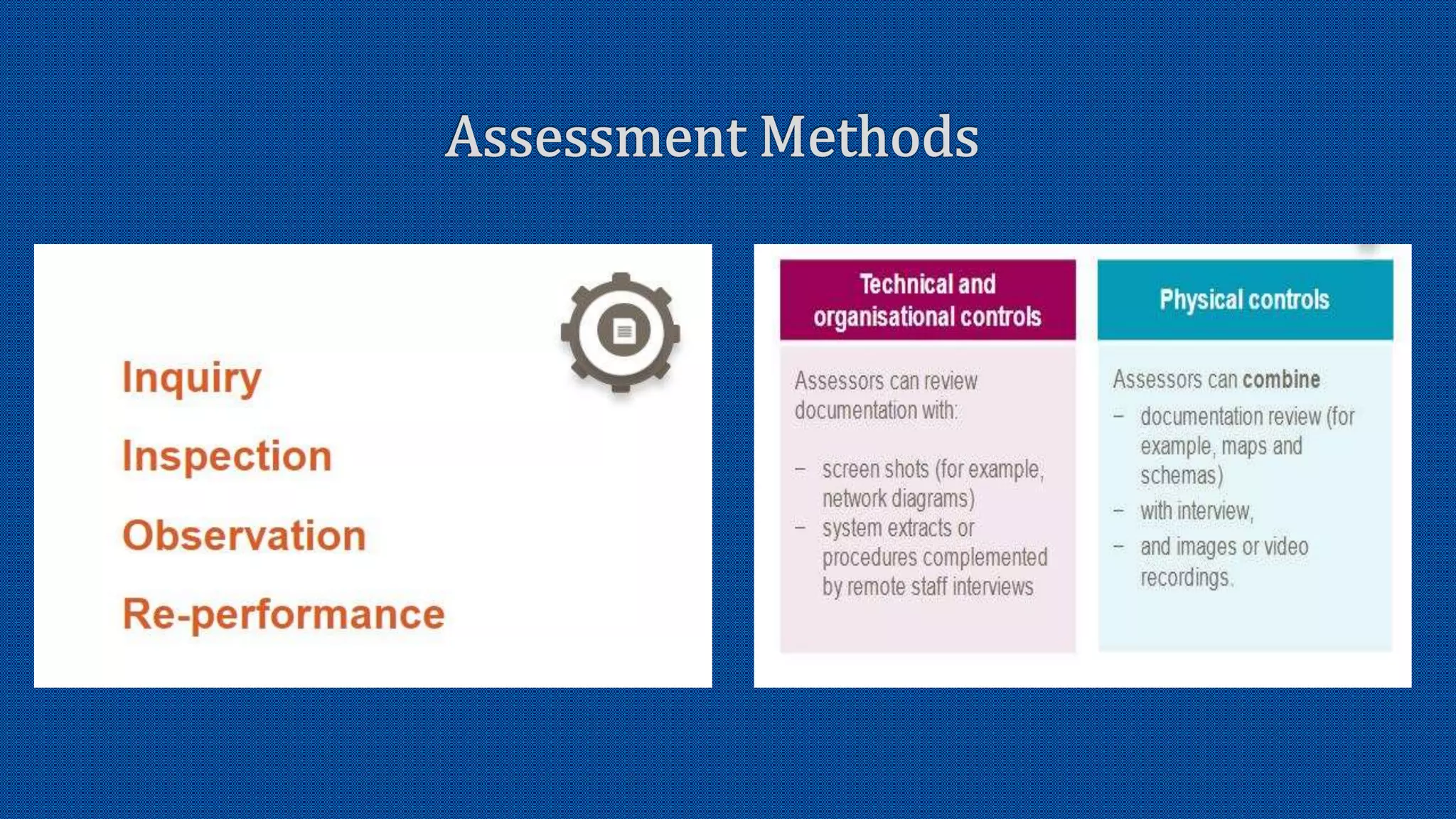

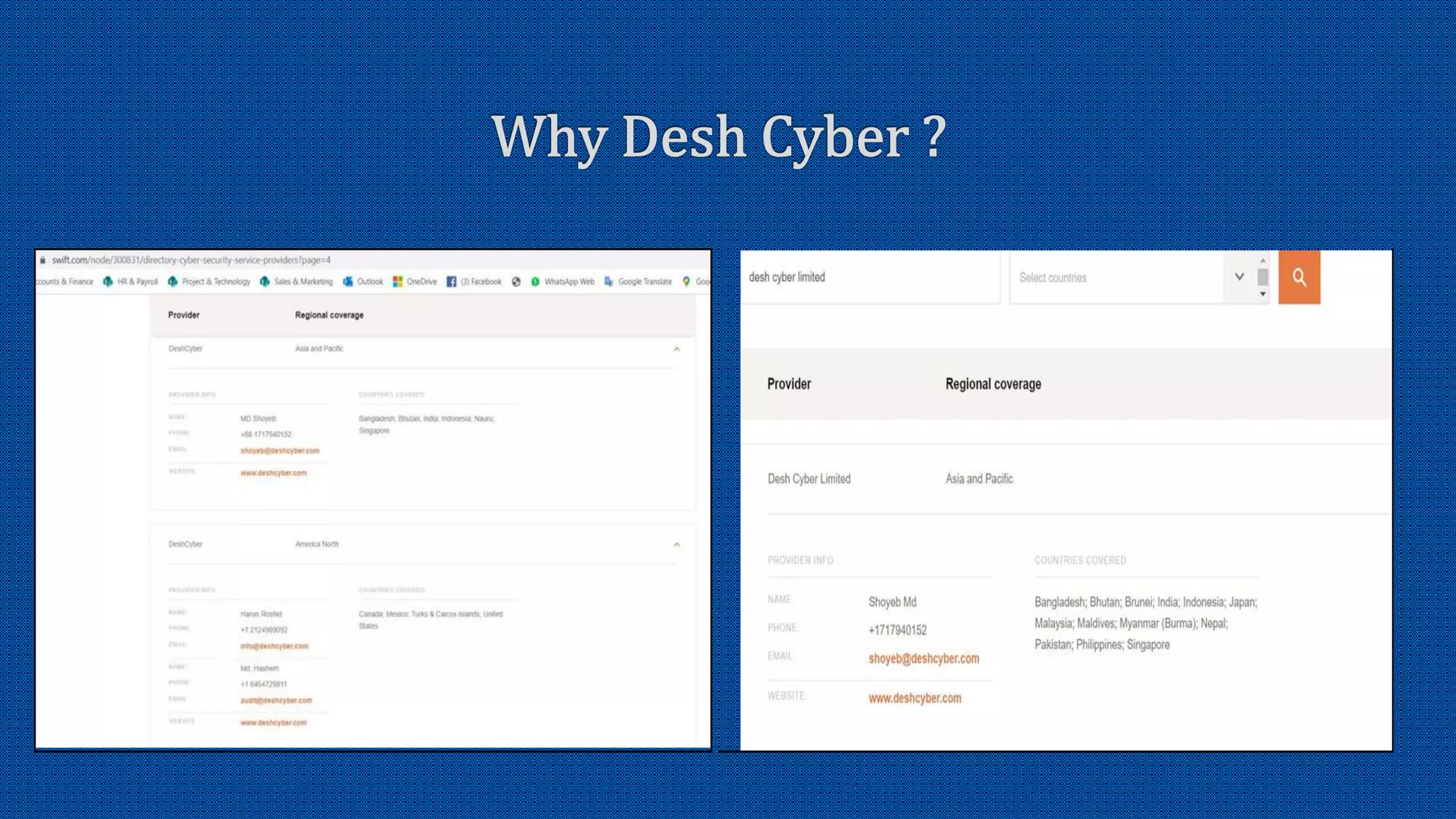

The document discusses the activation of an 8-character BIC in a live environment and highlights the connection through a service provider. It emphasizes the organization's strong commitment to cyber security services, extensive experience with cyber security frameworks, and adherence to SWIFT customer security control and audit guidelines. Additionally, it underscores the organization's strategic focus and reputable standing within the financial industry.



















