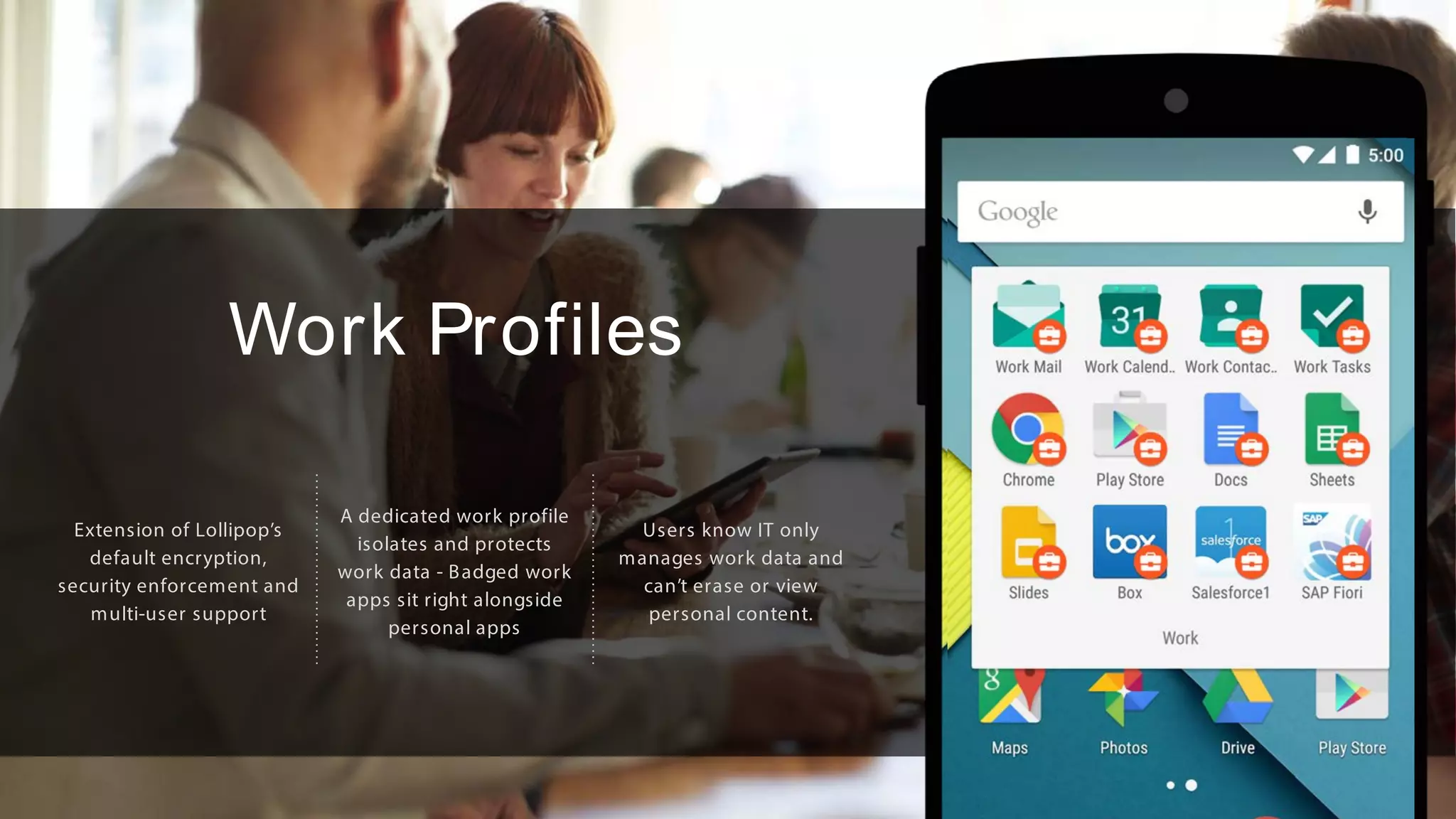
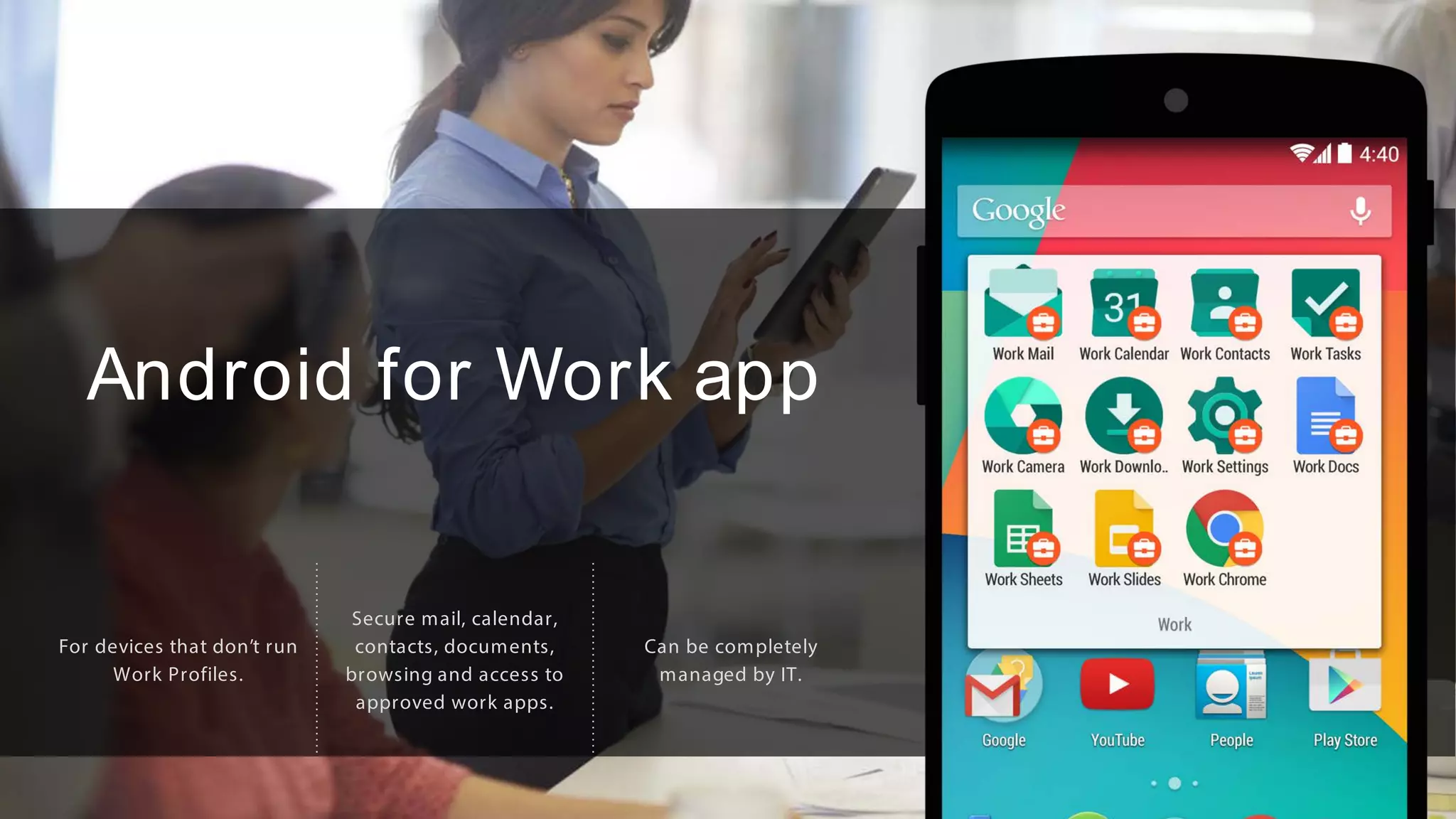
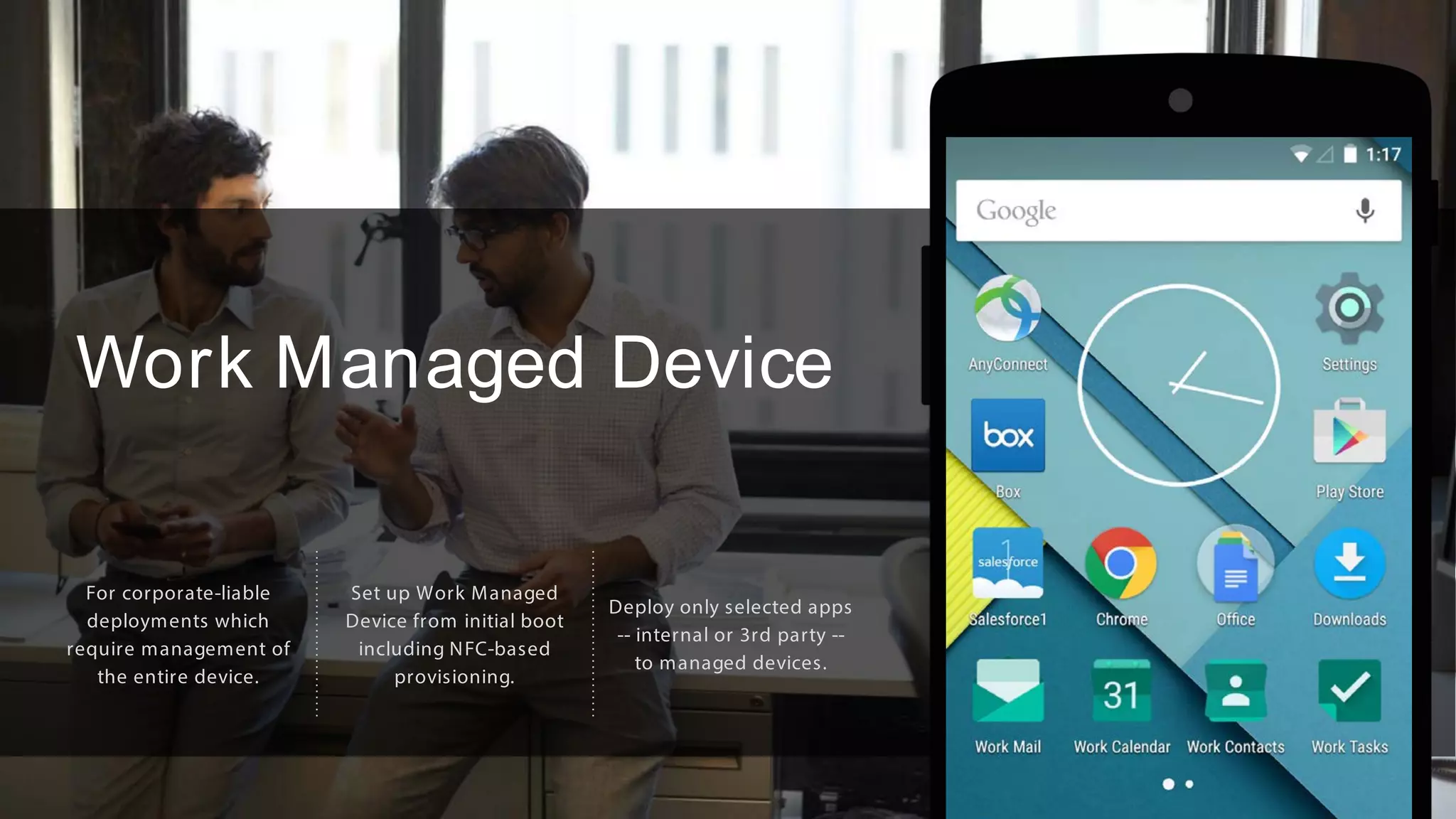
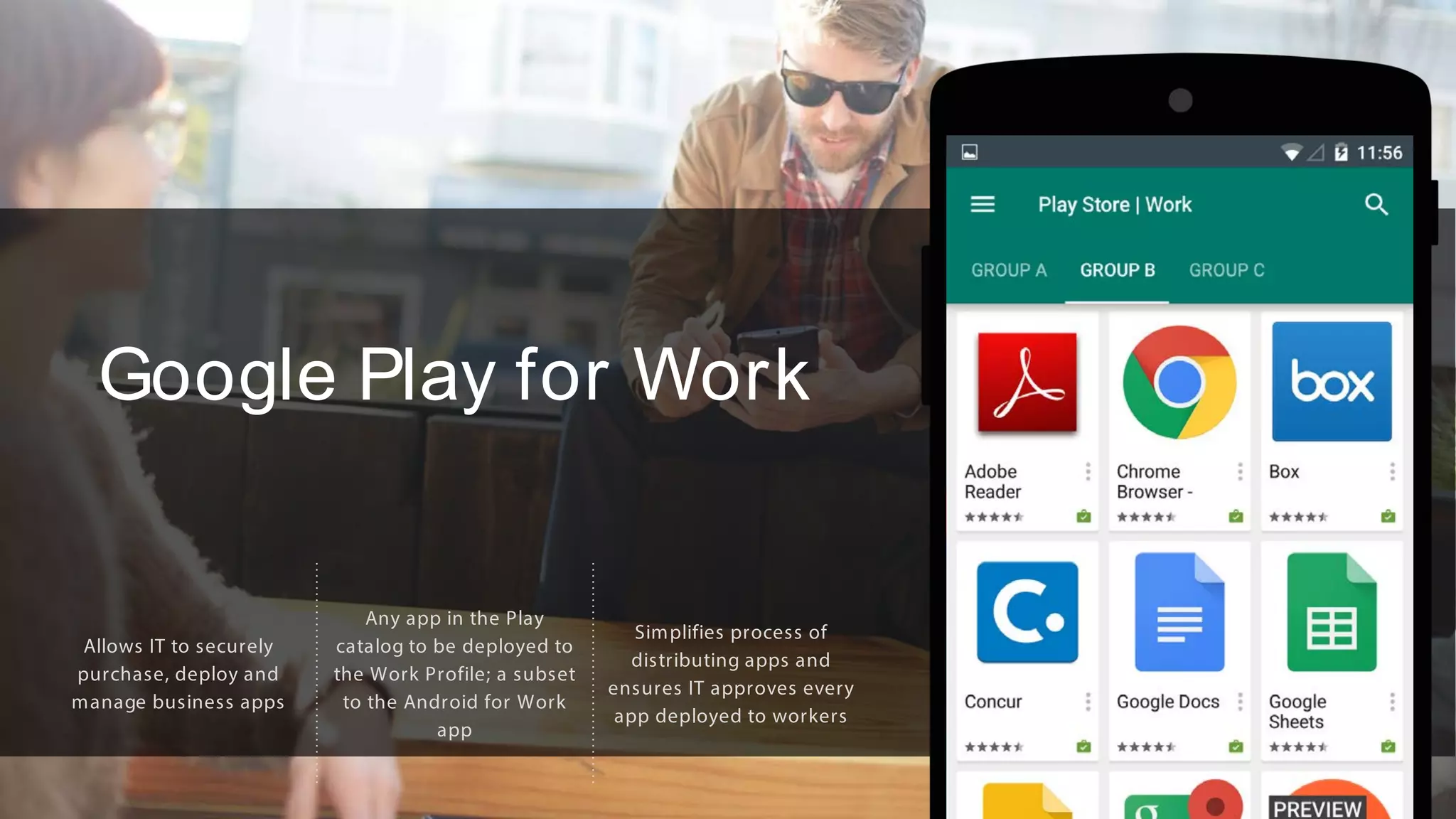
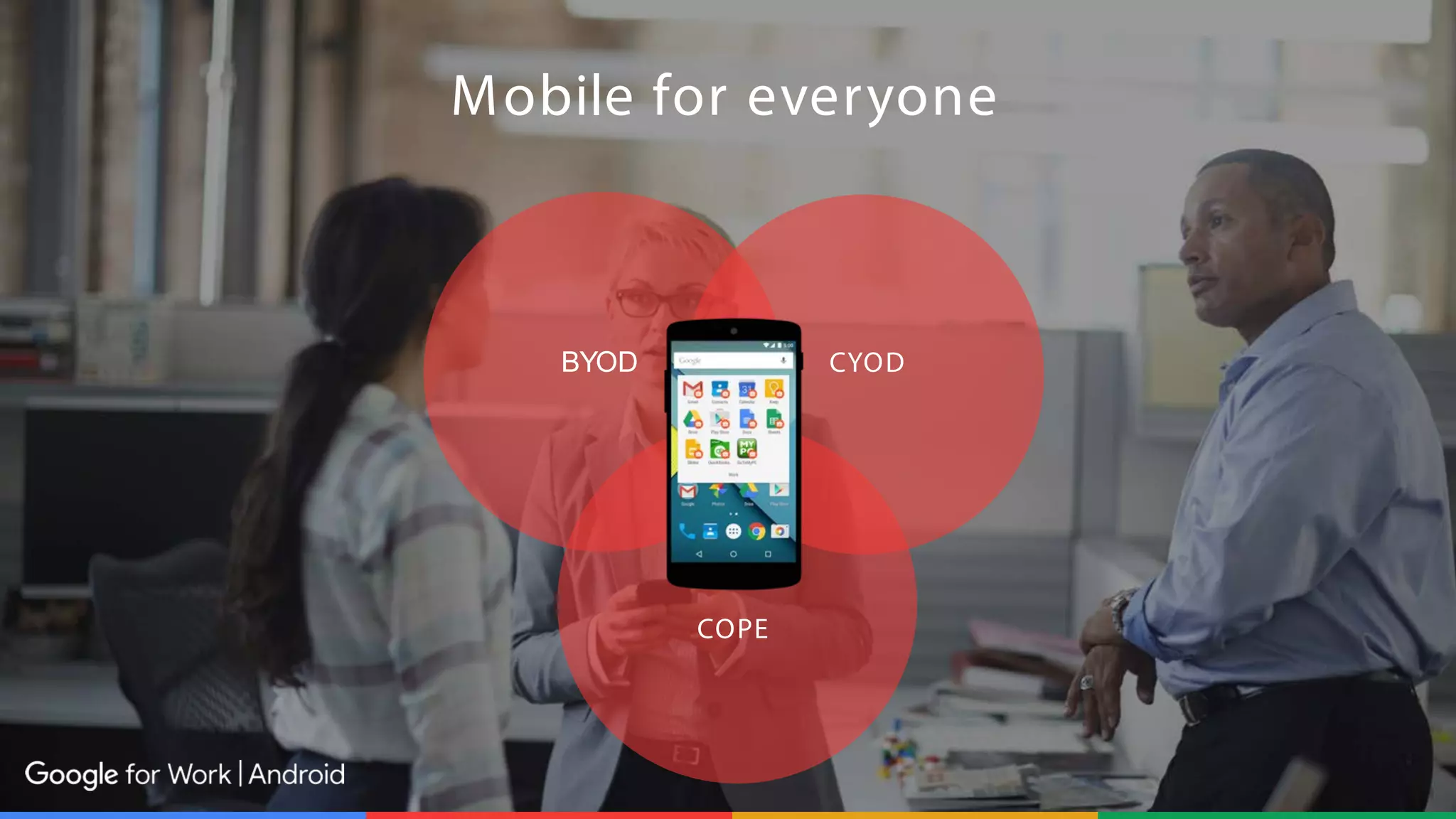
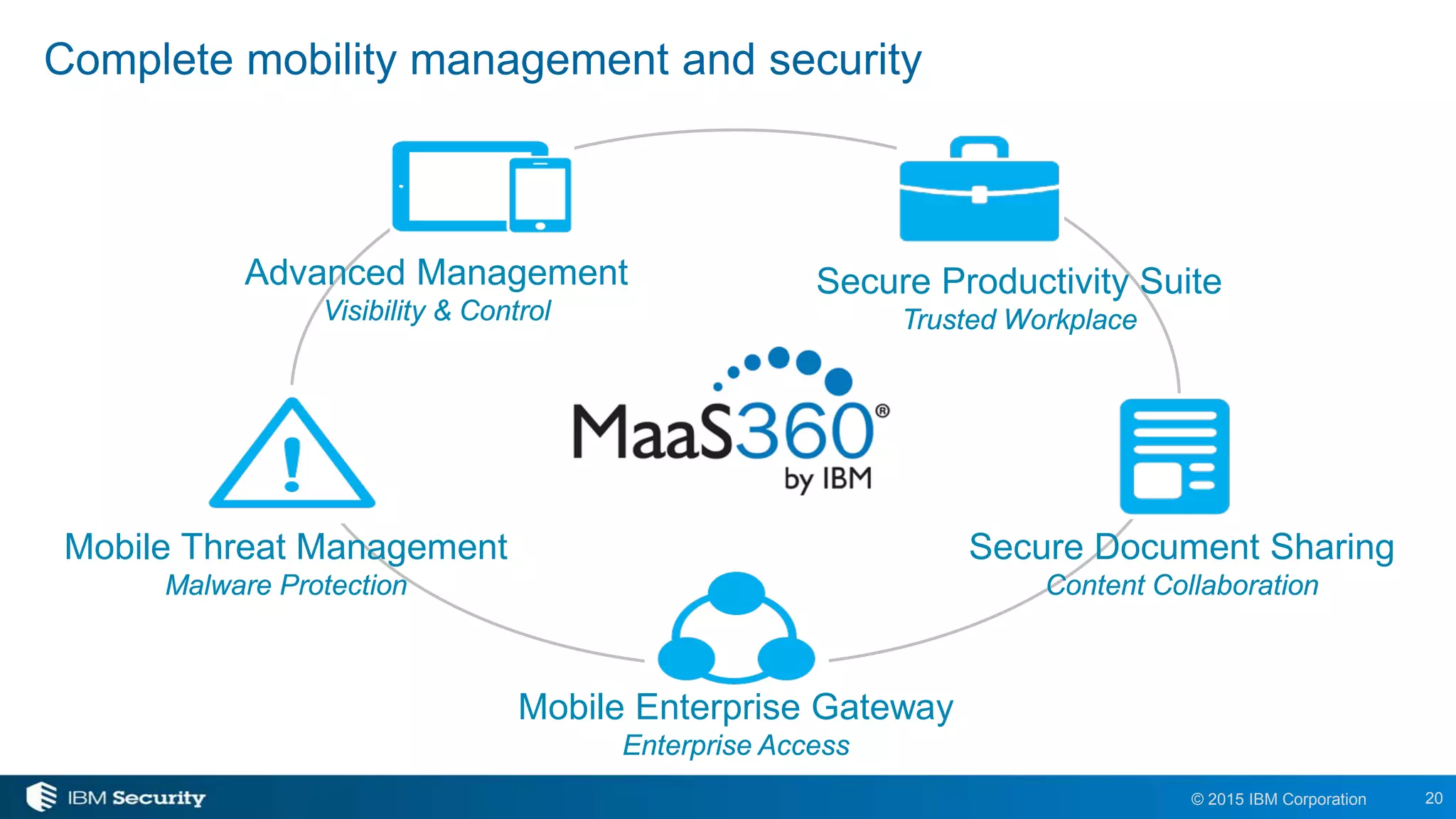
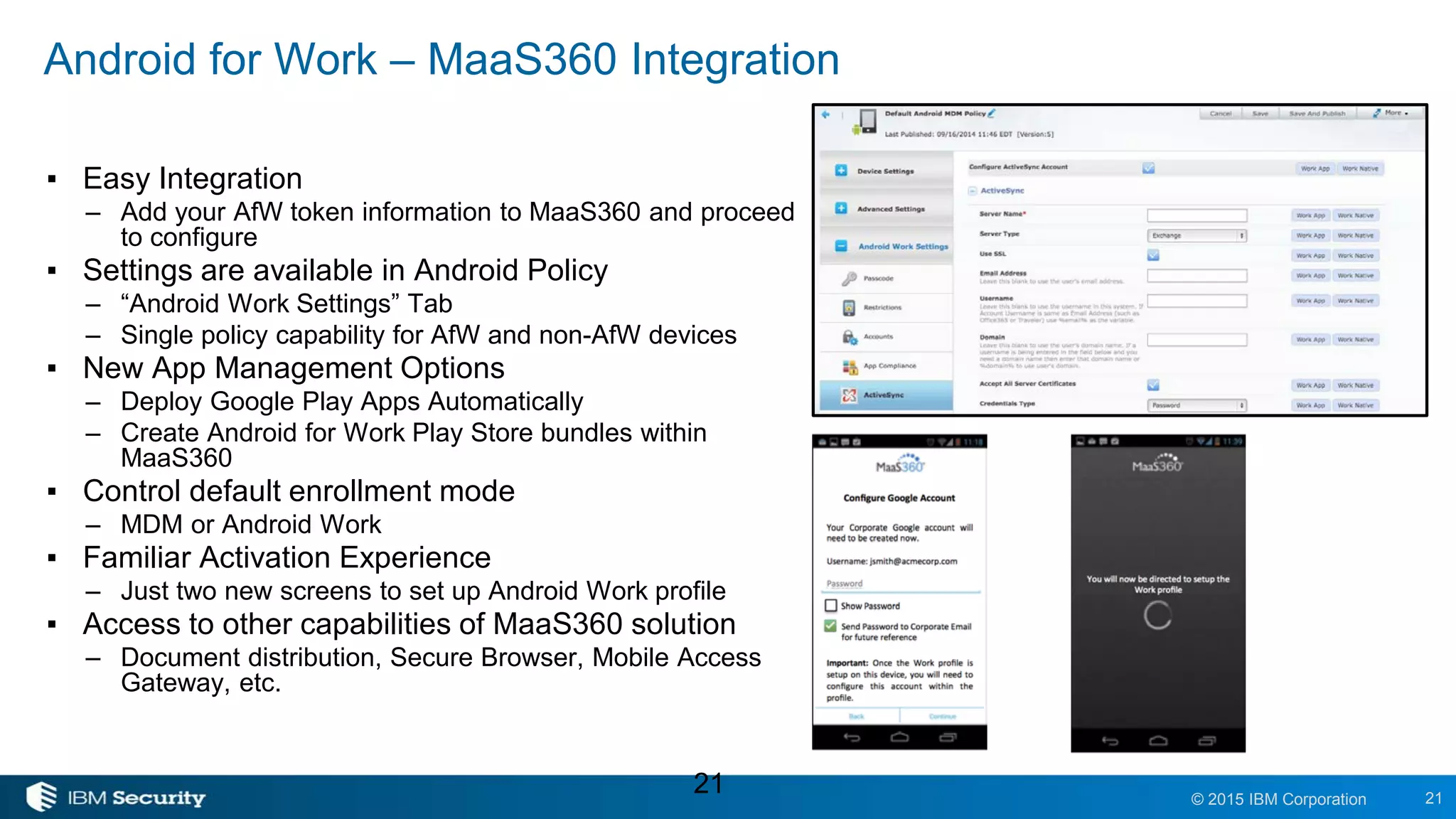
The document outlines the features and benefits of Android for Work and IBM's MaaS360, highlighting their integration for enhanced mobile security and device management. It discusses the setup process, secure management of applications, and the capability to separate work and personal data on devices. Additionally, it emphasizes the ease of use and scalability of MaaS360 in managing mobile environments.