Embed presentation
Downloaded 43 times

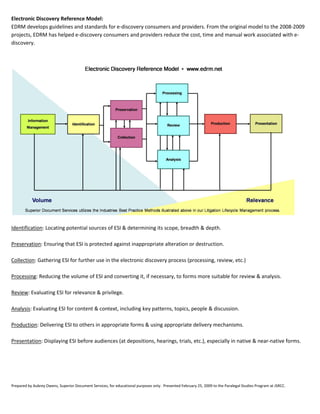


The document discusses the crucial role of litigation paralegals in managing case details, assisting attorneys in trial preparation, and overseeing the organization of legal information. It highlights the importance of electronic discovery (e-discovery), detailing processes such as identification, preservation, collection, and review of electronically stored information (ESI). Additionally, it emphasizes technology's impact on improving the efficiency of document search and retrieval, and outlines guidelines for compliance in the discovery process.


