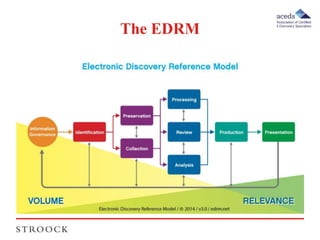
This document summarizes an e-discovery primer presentation given by Royce Cohen and Michael Quartararo of Stroock & Stroock & Lavan LLP. The presentation provides an overview of the key stages of e-discovery as defined by the EDRM model, including information governance, identification, preservation, collection, processing, review, production, and presentation. It also uses a hypothetical litigation scenario to illustrate how these stages would apply in practice to a real legal matter.