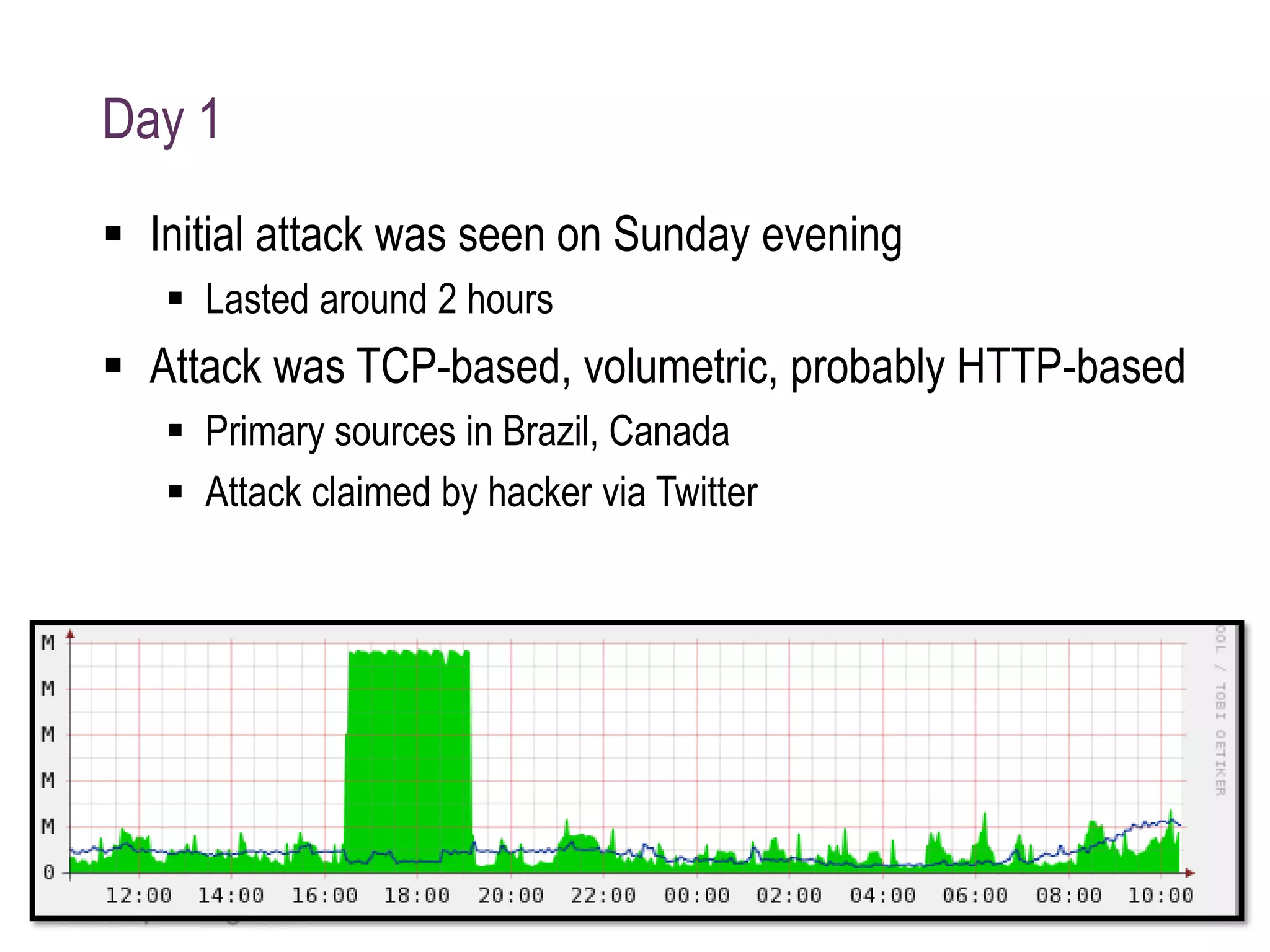
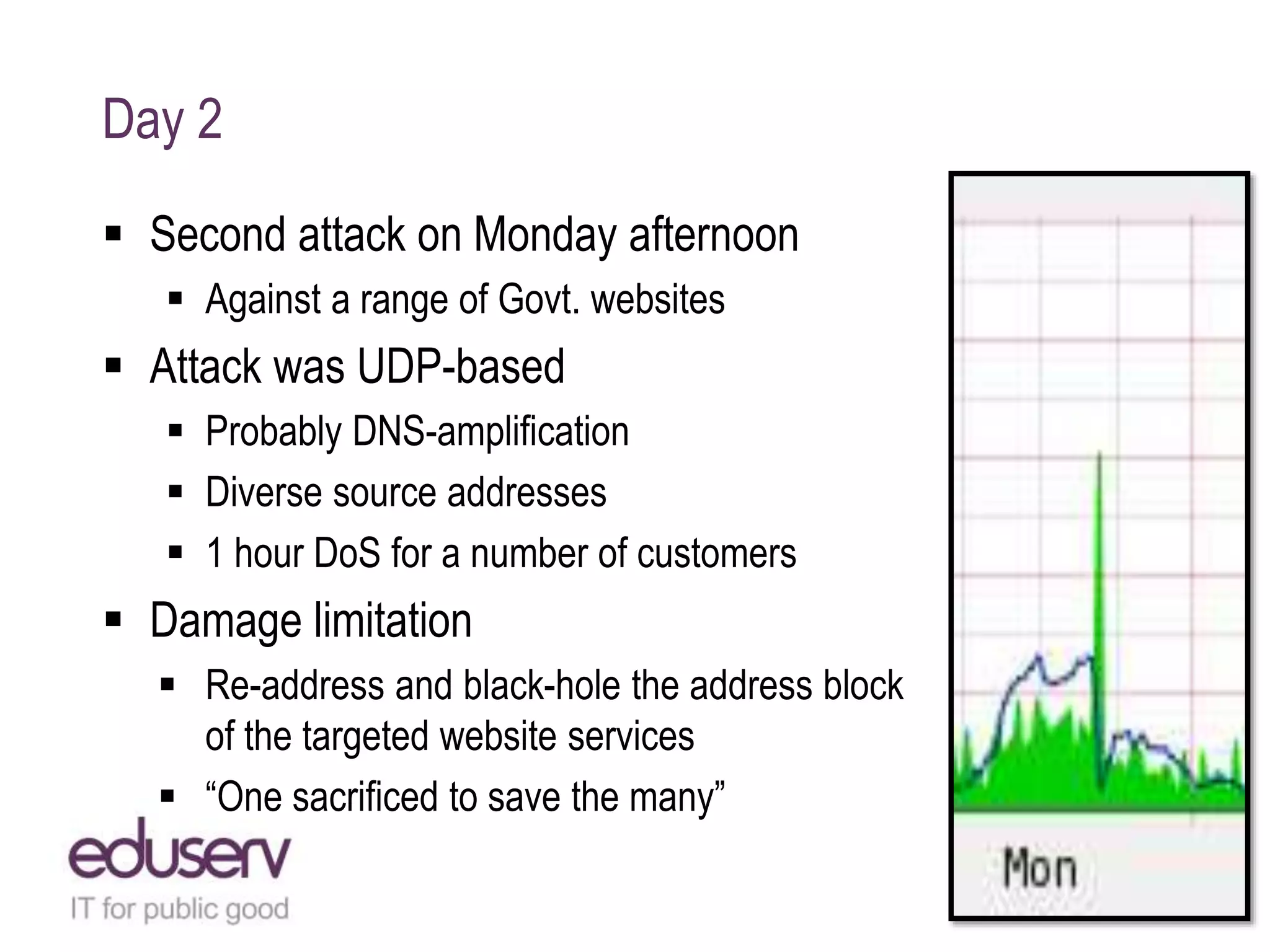
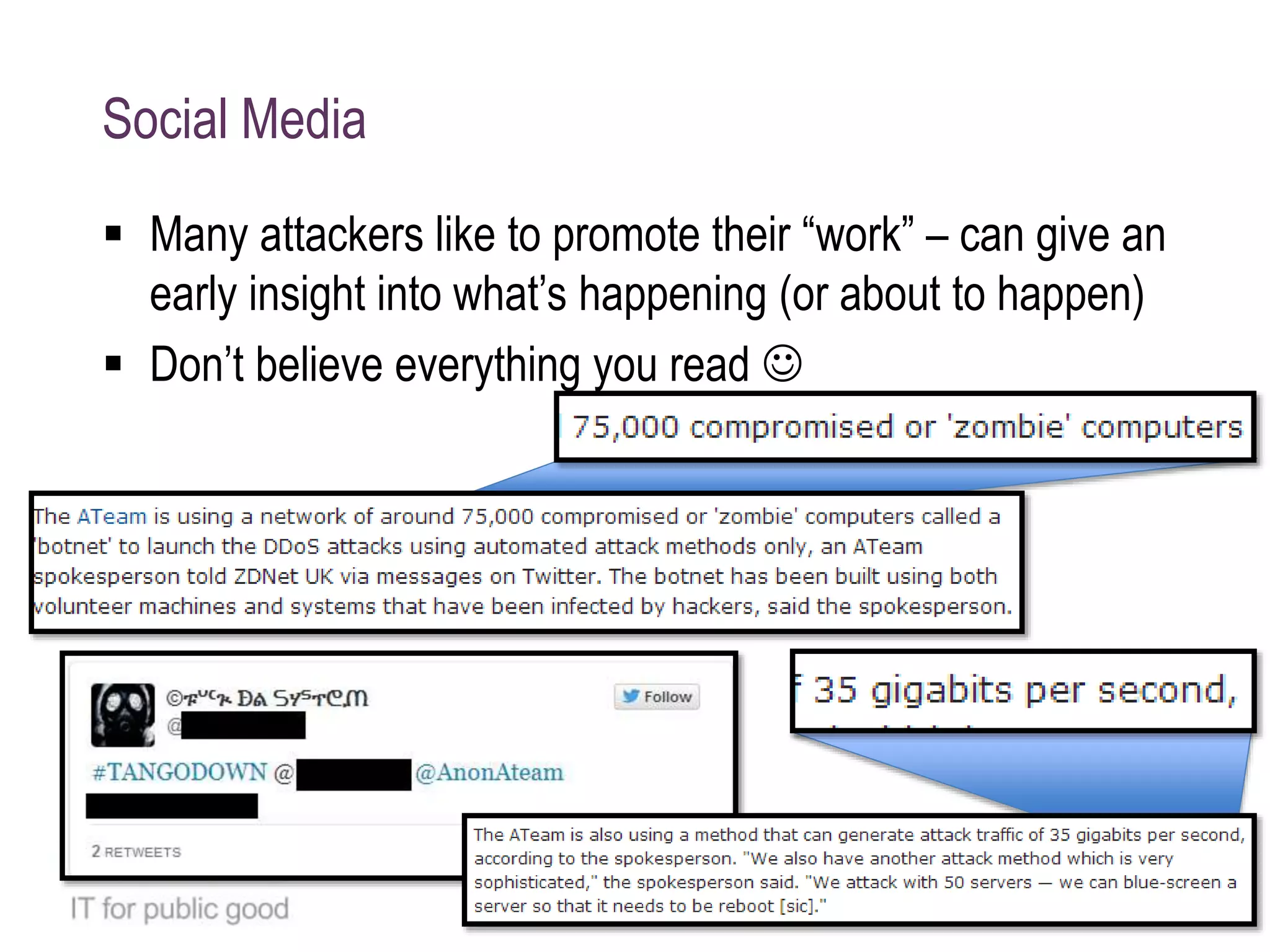
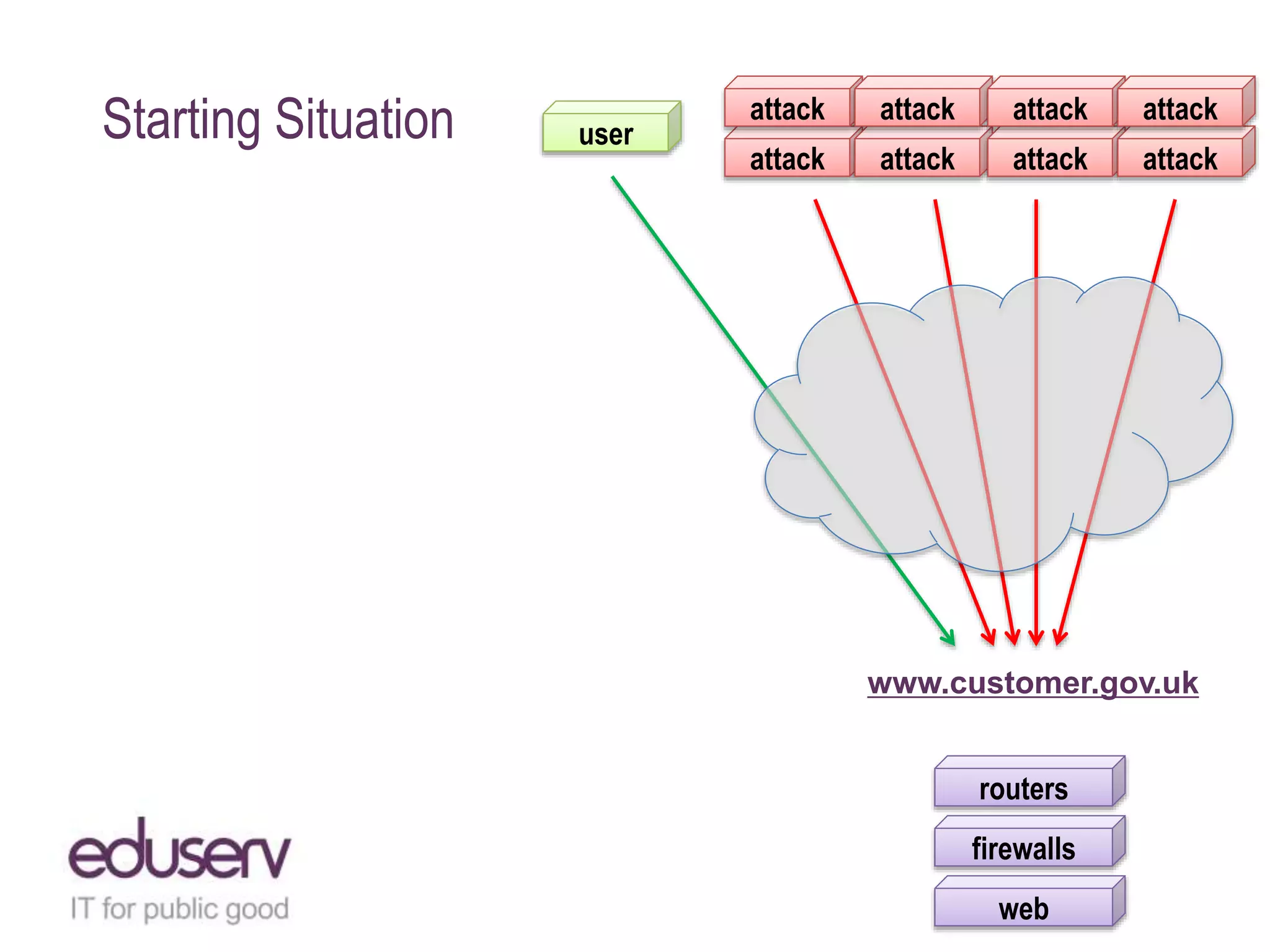
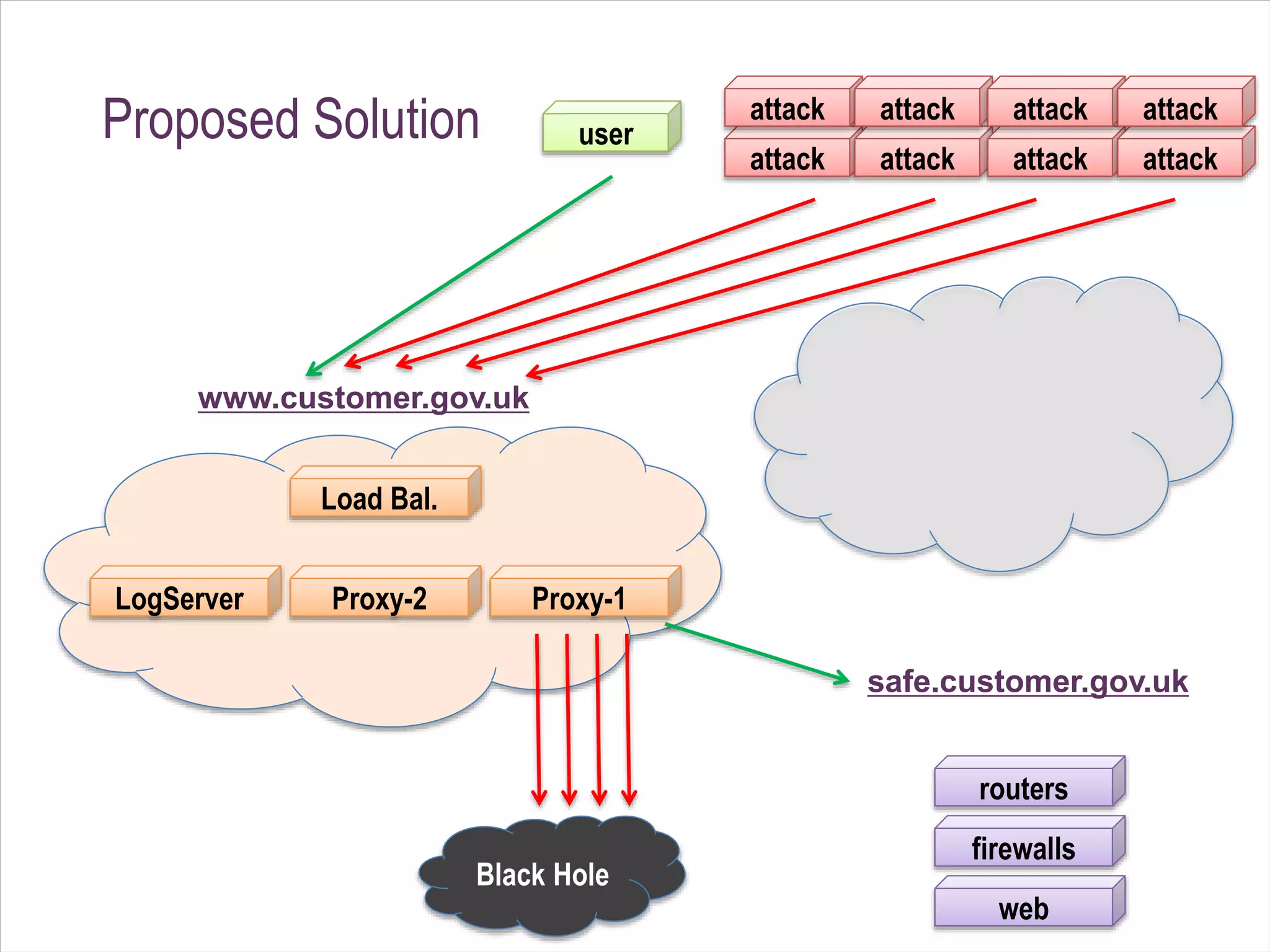
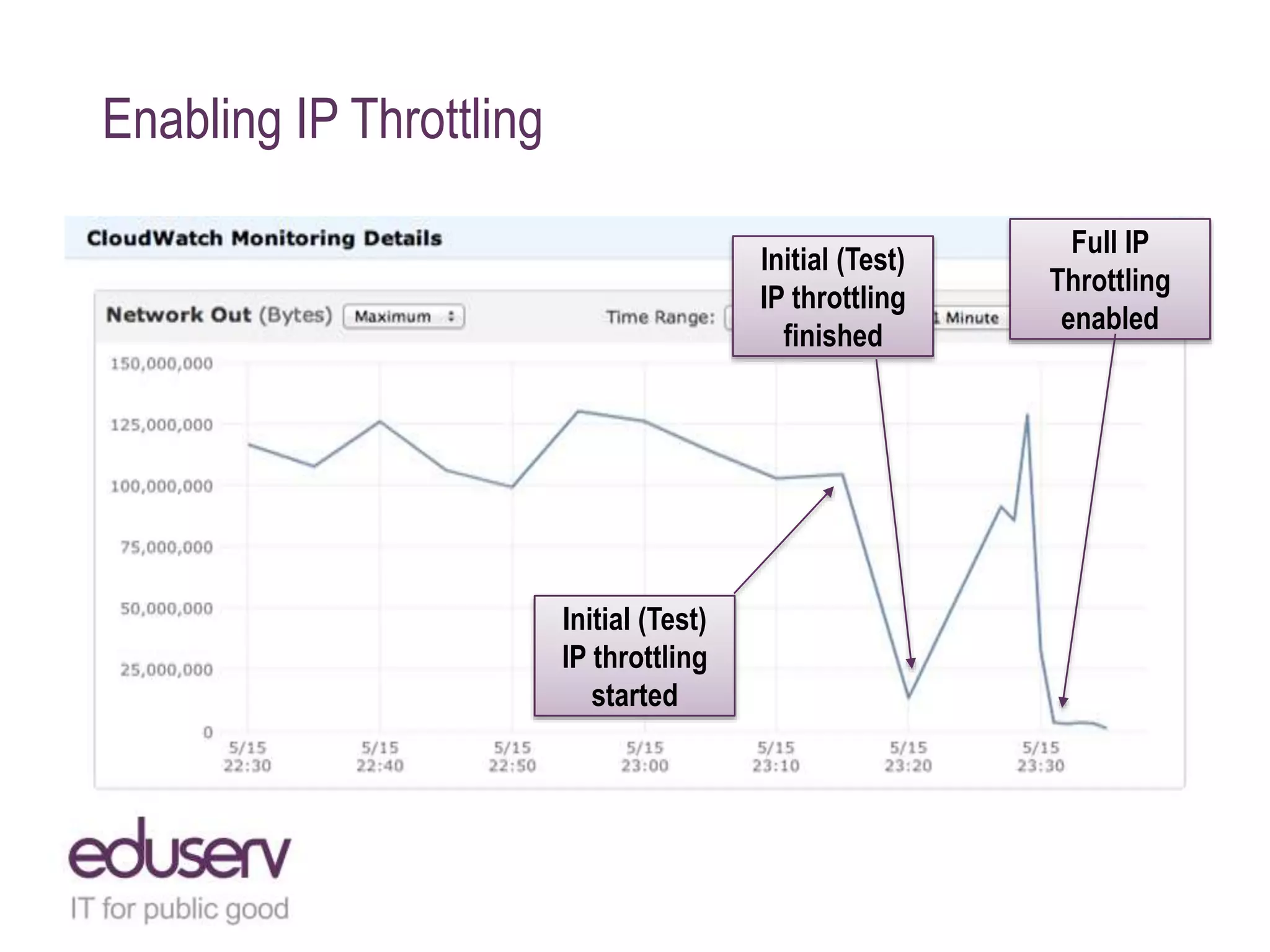
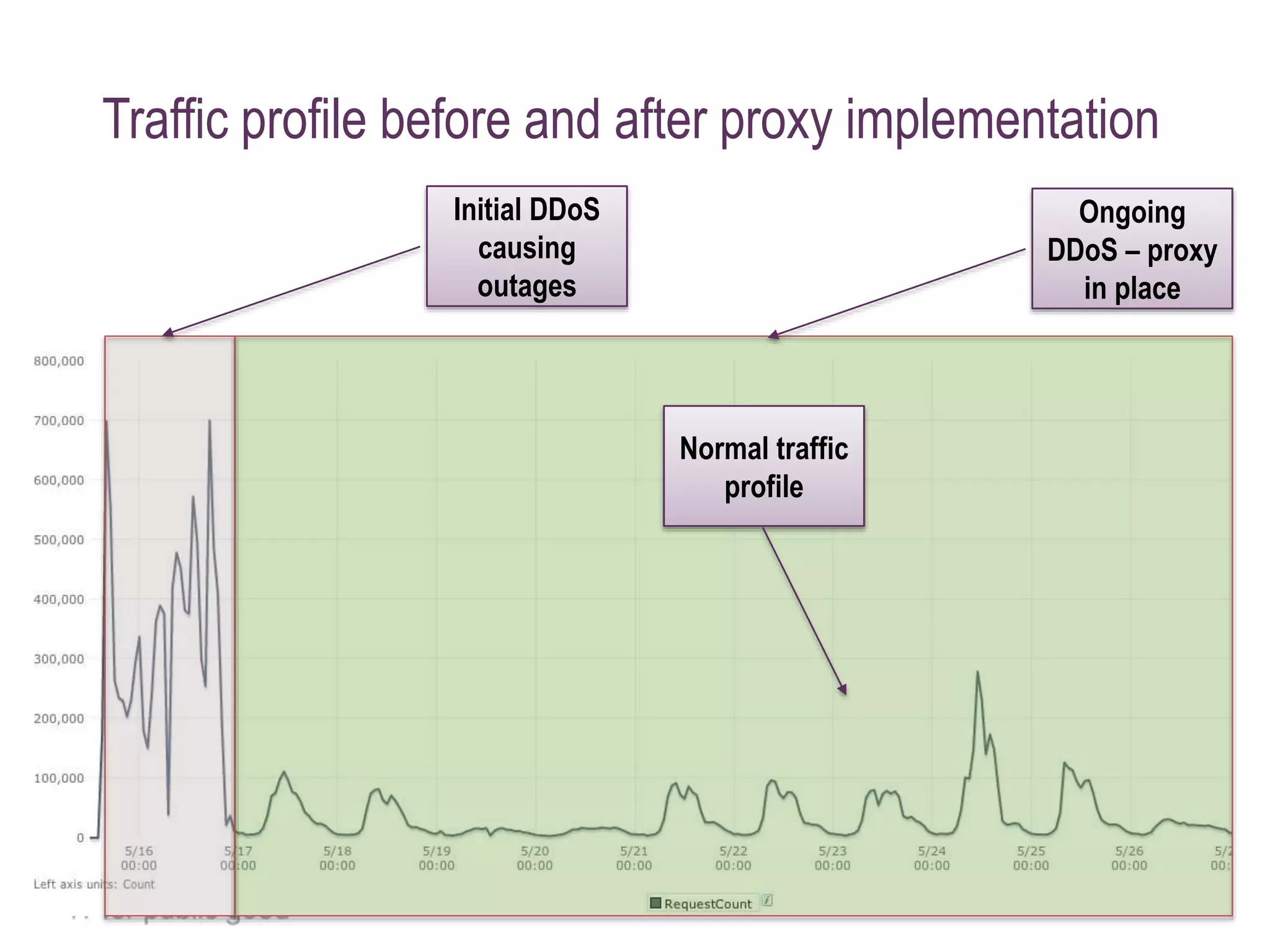
The document details a case study on how Eduserv managed multiple DDoS attacks against its services in January 2015, highlighting attack profiles, mitigation strategies, and lessons learned. It outlines the nature of the attacks, their impact on government websites, and the incident response process including the use of AWS for protection. Key takeaways emphasize the importance of bandwidth, DNS flexibility, real-time monitoring, and social media for preemptive insight into attacks.