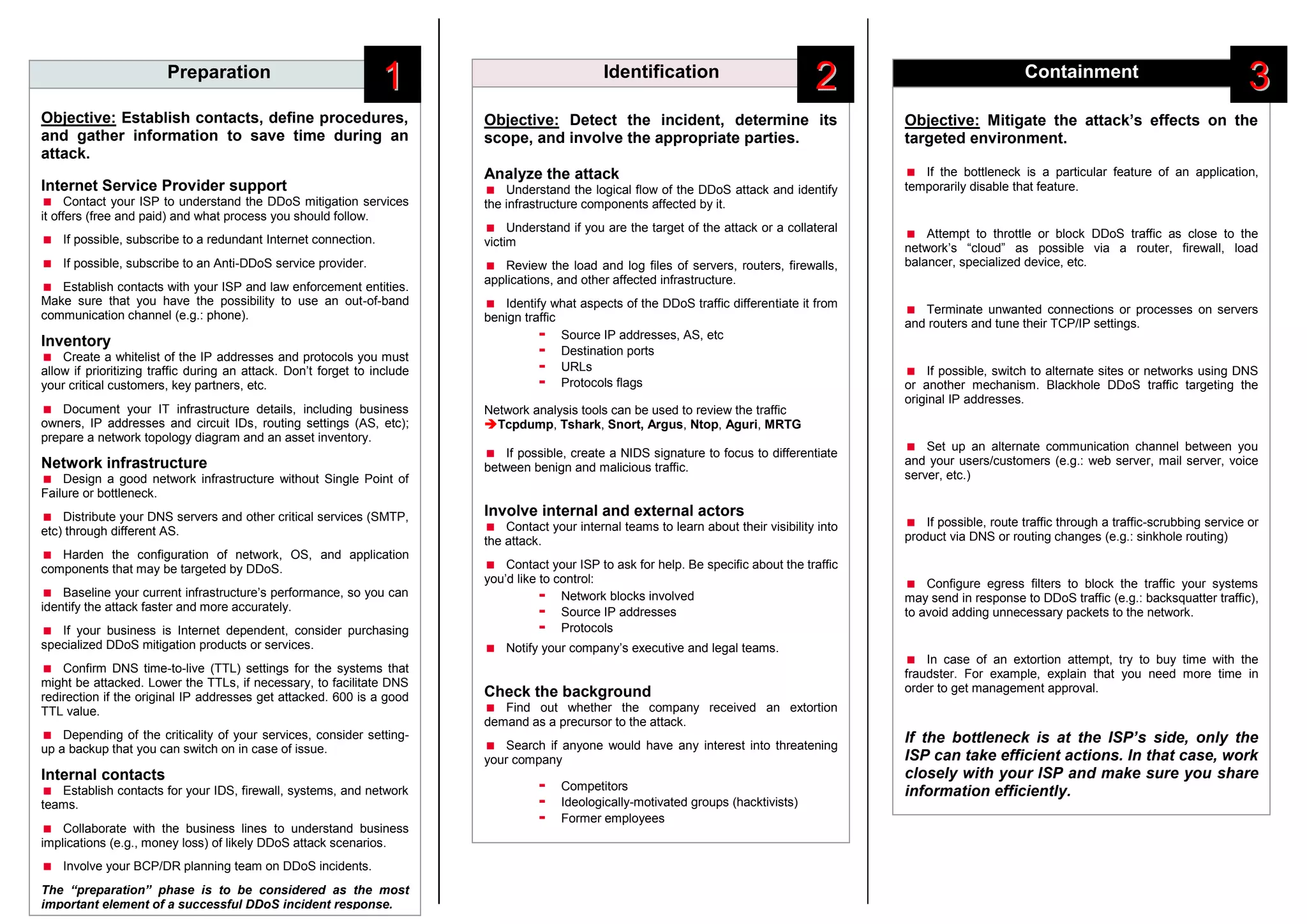
The document outlines a comprehensive methodology for responding to distributed denial of service (DDoS) incidents, emphasizing preparation, identification, containment, remediation, recovery, and aftermath. Key recommendations include establishing contacts with Internet Service Providers (ISPs), creating a detailed inventory of IT infrastructure, and analyzing the attack to mitigate its effects. Additionally, it stresses the importance of documentation and learning from incidents to enhance future defenses.