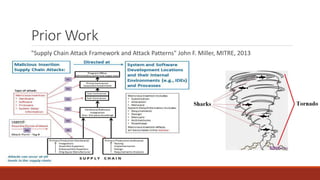
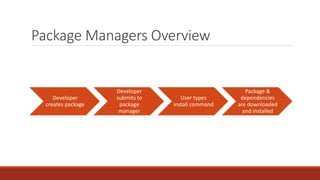
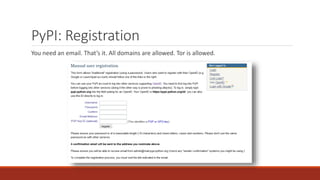
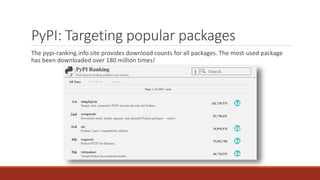
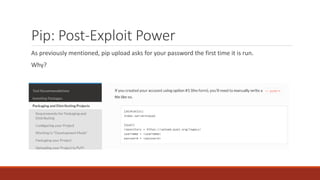
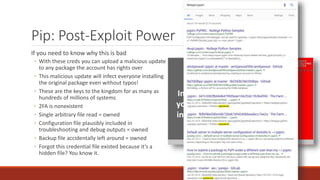
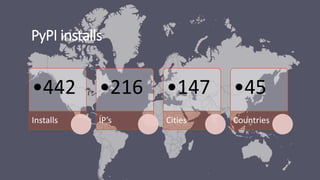
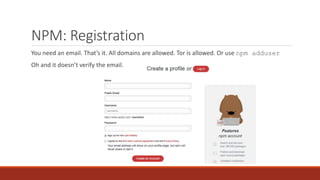
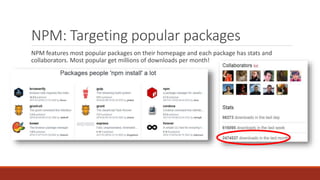
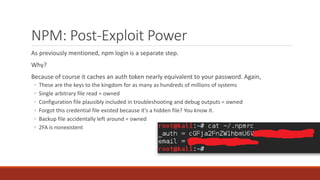
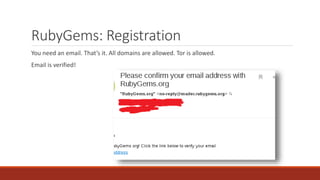
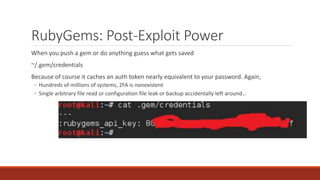
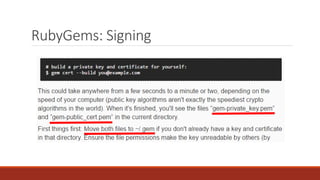
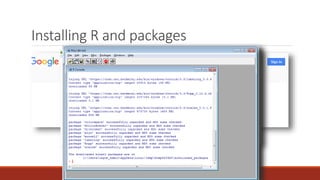
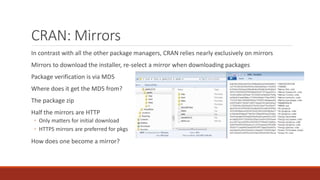
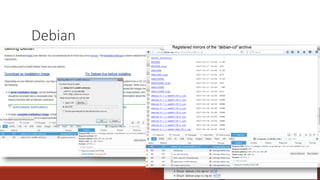
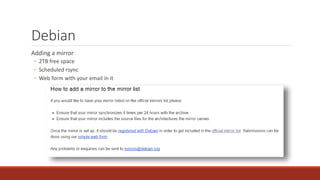
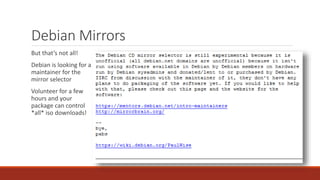
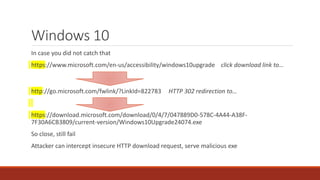
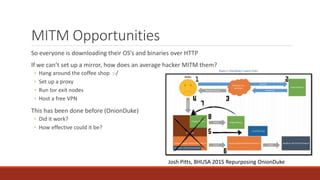
The document summarizes various software supply chain attacks targeting popular package managers like PyPI and NPM. It outlines how easy it is to anonymously register and submit malicious packages to these repositories due to lack of security measures. The attacks discussed include typosquatting popular packages, submitting packages to the wrong repository, compromising repository mirrors, and taking over developer accounts to publish backdoored updates. It then provides examples of actual attacks performed on PyPI and NPM, where packages mimicking popular ones were uploaded to call home with installation details, revealing hundreds of installations and IPs across many countries.