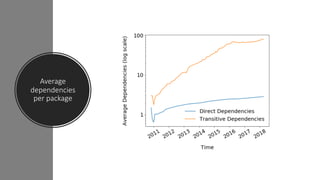
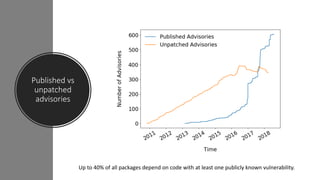
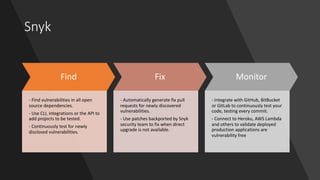
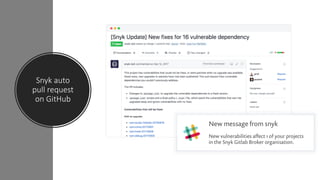
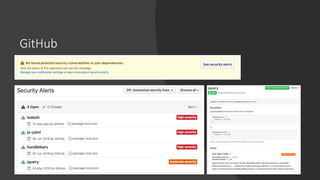
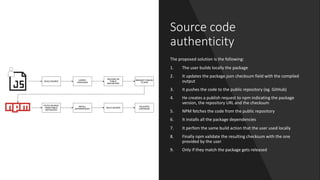
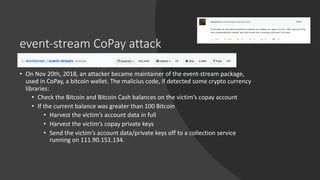
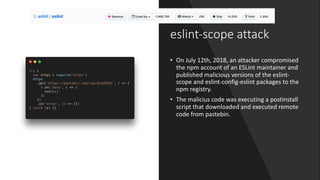
The npm ecosystem faces security threats from vulnerable dependencies and malicious packages. Tools like npm audit and Snyk help identify vulnerabilities, but up to 40% of packages still depend on code with known issues. Additionally, without source code authenticity checks, attackers can compromise packages by publishing code that differs from open source repositories. High profile incidents include stealing funds from a Bitcoin wallet and executing remote code through compromised packages. The ecosystem would benefit from solutions that verify source code integrity during publication to registry.