String Matching Algorithms-The Naive Algorithm
•Download as PPTX, PDF•
2 likes•824 views
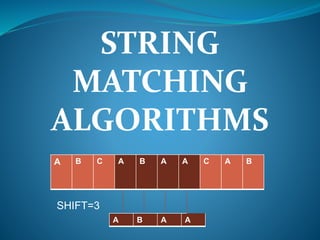
String matching algorithms are used to find patterns within larger strings or texts. The example shows a text string "A B C A B A A C A B" and a pattern "A B A A" with a shift of 3. The naive string matching algorithm is described which compares characters between the text and pattern from index 0 to the string lengths to find all valid shifts where the pattern occurs in the text.
Report
Share
Report
Share
Recommended
Rabin Karp ppt

The Rabin-Karp algorithm is a string-searching algorithm that uses hashing to find patterns in strings.
The Rabin-Karp algorithm makes use of hash functions and the rolling hash technique.
Rabin Karp Algorithm

The presenation gives a brief detail about a searching algorithm known as "Rabin-Karp Algorithm". The presentation contains the history of the algorithm and its working alongwith the example.
String matching algorithms-pattern matching.

Algorithms Discussed
Knuth–Morris–Pratt algorithm
Boyer–Moore string search algorithm
Bitap algorithm (for exact string searching)
-------------------
Checking whether two or more strings are same or not.
Finding a string (pattern) into another string (text). --> Looking for substring
Recommended
Rabin Karp ppt

The Rabin-Karp algorithm is a string-searching algorithm that uses hashing to find patterns in strings.
The Rabin-Karp algorithm makes use of hash functions and the rolling hash technique.
Rabin Karp Algorithm

The presenation gives a brief detail about a searching algorithm known as "Rabin-Karp Algorithm". The presentation contains the history of the algorithm and its working alongwith the example.
String matching algorithms-pattern matching.

Algorithms Discussed
Knuth–Morris–Pratt algorithm
Boyer–Moore string search algorithm
Bitap algorithm (for exact string searching)
-------------------
Checking whether two or more strings are same or not.
Finding a string (pattern) into another string (text). --> Looking for substring
Rabin karp string matching algorithm

This presentation gives the basic idea about the string matching problem and describes Rabin Karp String Matching algorithm.
RABIN KARP ALGORITHM STRING MATCHING

RABIN KARP algorithm with hash function and hash collision, analysis, algorithm and code for implementation. Besides it contains applications of RABIN KARP algorithm also
String matching algorithms

A basic introduction to "String matching algorithms". Useful for Biotechnology, Bioinformatics and Computer science.
String Matching (Naive,Rabin-Karp,KMP)

gives an overview of basic string matching algorithms with examples and pseudocodes
String matching Algorithm by Foysal

Here i discuss 3 algorithm about String matching.
Those algorithm are:
1. The naive algorithm.
2. The Rabin-Krap algorithm.
3. The Knuth-Morris-Pratt algorithm.
i hope,by readinng this slide, it is easy to undarstand those algorithm.
String Matching Finite Automata & KMP Algorithm.

String Matching Finite Automata AND Knuth Morries Pratt(KMP) Algorithm.
String matching algorithm

the string matching problem, classification of the algorithms and their functionality
Naive String Matching Algorithm | Computer Science

In this approach, the pattern is made to slide over text one by one and test for a match. If a match is found while testing, then it returns the starting index number from where the pattern is found in the text and then slides by 1 again to check for subsequent matches of the pattern in the text. Copy the link given below and paste it in new browser window to get more information on Naive String Matching Algorithm:- http://www.transtutors.com/homework-help/computer-science/naive-string-matching-algorithm.aspx
Maximum Matching in General Graphs

In graph theory, a matching is a subset of a graph's edges such hat no two edges meet the same vertex. A matching is maximum if no other matching contains more edges. A trivial solution (exhaustive search) to the problem of finding a maximum matching has exponential complexity. We illustrate polynomial time solutions to the problem that were published between 1965 and 1991.
Travelling Salesman Problem using Partical Swarm Optimization

ILGIN KAVAKLIOGULLARI
Computer Science And Engineering
Student @ Techical University of Sofia
Divide and Conquer - Part 1

Divide and Conquer Algorithms - D&C forms a distinct algorithm design technique in computer science, wherein a problem is solved by repeatedly invoking the algorithm on smaller occurrences of the same problem. Binary search, merge sort, Euclid's algorithm can all be formulated as examples of divide and conquer algorithms. Strassen's algorithm and Nearest Neighbor algorithm are two other examples.
Sum of subset problem.pptx

Subset sum problem is to find subset of elements that are selected from a given set whose sum adds up to a given number K. We are considering the set contains non-negative values. It is assumed that the input set is unique (no duplicates are presented).
Naive string matching

Given presentation tell us about string, string matching and the navie method of string matching. Well this method has O((n-m+1)*m) time complexicity. It also tells the problem with naive approach and gives list of approaches which can be applied to reduce the time complexicity
More Related Content
What's hot
Rabin karp string matching algorithm

This presentation gives the basic idea about the string matching problem and describes Rabin Karp String Matching algorithm.
RABIN KARP ALGORITHM STRING MATCHING

RABIN KARP algorithm with hash function and hash collision, analysis, algorithm and code for implementation. Besides it contains applications of RABIN KARP algorithm also
String matching algorithms

A basic introduction to "String matching algorithms". Useful for Biotechnology, Bioinformatics and Computer science.
String Matching (Naive,Rabin-Karp,KMP)

gives an overview of basic string matching algorithms with examples and pseudocodes
String matching Algorithm by Foysal

Here i discuss 3 algorithm about String matching.
Those algorithm are:
1. The naive algorithm.
2. The Rabin-Krap algorithm.
3. The Knuth-Morris-Pratt algorithm.
i hope,by readinng this slide, it is easy to undarstand those algorithm.
String Matching Finite Automata & KMP Algorithm.

String Matching Finite Automata AND Knuth Morries Pratt(KMP) Algorithm.
String matching algorithm

the string matching problem, classification of the algorithms and their functionality
Naive String Matching Algorithm | Computer Science

In this approach, the pattern is made to slide over text one by one and test for a match. If a match is found while testing, then it returns the starting index number from where the pattern is found in the text and then slides by 1 again to check for subsequent matches of the pattern in the text. Copy the link given below and paste it in new browser window to get more information on Naive String Matching Algorithm:- http://www.transtutors.com/homework-help/computer-science/naive-string-matching-algorithm.aspx
Maximum Matching in General Graphs

In graph theory, a matching is a subset of a graph's edges such hat no two edges meet the same vertex. A matching is maximum if no other matching contains more edges. A trivial solution (exhaustive search) to the problem of finding a maximum matching has exponential complexity. We illustrate polynomial time solutions to the problem that were published between 1965 and 1991.
Travelling Salesman Problem using Partical Swarm Optimization

ILGIN KAVAKLIOGULLARI
Computer Science And Engineering
Student @ Techical University of Sofia
Divide and Conquer - Part 1

Divide and Conquer Algorithms - D&C forms a distinct algorithm design technique in computer science, wherein a problem is solved by repeatedly invoking the algorithm on smaller occurrences of the same problem. Binary search, merge sort, Euclid's algorithm can all be formulated as examples of divide and conquer algorithms. Strassen's algorithm and Nearest Neighbor algorithm are two other examples.
Sum of subset problem.pptx

Subset sum problem is to find subset of elements that are selected from a given set whose sum adds up to a given number K. We are considering the set contains non-negative values. It is assumed that the input set is unique (no duplicates are presented).
Naive string matching

Given presentation tell us about string, string matching and the navie method of string matching. Well this method has O((n-m+1)*m) time complexicity. It also tells the problem with naive approach and gives list of approaches which can be applied to reduce the time complexicity
What's hot (20)
Naive String Matching Algorithm | Computer Science

Naive String Matching Algorithm | Computer Science
Travelling Salesman Problem using Partical Swarm Optimization

Travelling Salesman Problem using Partical Swarm Optimization
Similar to String Matching Algorithms-The Naive Algorithm
String Matching algorithm String Matching algorithm String Matching algorithm

String Matching algorithm
IMPLEMENTATION OF DIFFERENT PATTERN RECOGNITION ALGORITHM 

IMPLEMENTATION OF DIFFERENT PATTERN RECOGNITION ALGORITHM NETAJI SUBHASH ENGINEERING COLLEGE , KOLKATA
WHAT IS PATTERN RECOGNISITION ?
Given a text string T[0..n-1] and a pattern P[0..m-1], find all occurrences of the pattern within the text.
Example: T = 000010001010001 and P = 0001, the occurrences are:
first occurrence starts at T[1]
second occurrence starts at T[5]
third occurrence starts at T[11]
APPLICATION :
Image preprocessing
• Computer vision
• Artificial intelligence
• Radar signal classification/analysis
• Speech recognition/understanding
• Fingerprint identification
• Character (letter or number) recognition
• Handwriting analysis
• Electro-cardiographic signal analysis/understanding
• Medical diagnosis
• Data mining/reduction
ALGORITHM DESCRIPTION
The Knuth-Morris-Pratt (KMP) algorithm:
It was published by Donald E. Knuth, James H.Morris and Vaughan R. Pratt, 1977 in: “Fast Pattern Matching in Strings.“
To illustrate the ideas of the algorithm, consider the following example:T = xyxxyxyxyyxyxyxyyxyxyxxy
And P = xyxyyxyxyxx
it considers shifts in order from 1 to n-m, and determines if the pattern matches at that shift. The difference is that the KMP algorithm uses information gleaned from partial matches of the pattern and text to skip over shifts that are guaranteed not to result in a match.
The text and pattern are included in Figure 1, with numbering, to make it easier to follow.
1.Consider the situation when P[1……3] is successfully matched with T[1……..3]. We then find a mismatch: P[4] = T[4]. Based on our knowledge that P[1…… 3] =T[1…… 3], and ignoring symbols of the pattern and text after position 3, what can we deduce about where a potential match might be? In this case, the algorithm slides the pattern 2 positions to the right so that P[1] is lined up with T[3]. The next comparison is between P[2] and T[4].
P: x y x y y x y x y x x
q: 1 2 3 4 5 6 7 8 9 10 11
_(q): 0 0 1 2 0 3
Table 1: Table of values for pattern P.
Time Complexity :
The call to compute prefix is O(m)
using q as the value of the potential function, we argue in the same manner as above to show the loop is O(n)
Therefore the overall complexity is O(m + n)
Boyer-Moore algorithm:
It was developed by Bob Boyer and J Strother Moore in 1977. The algorithm preprocesses the pattern string that is being searched in text string.
String pattern matching - Boyer-Moore:
This algorithm uses fail-functions to shift the pattern efficiently. Boyer-Moore starts however at the end of the pattern, which can result in larger shifts.Two heuristics are used:1: if we encounter a mismatch at character c in Q, we can shift to the first occurrence of c in P from the right:
Q a b c a b c d g a b c e a b c d a c e d
P a b c e b c d
a b c e b c d
(restart here)
Time Complexity:
• performs the comparisons from right to left;
• preprocessing phase in O(m+ ) tString Searching and Matching

Novel Approach for String Searching and Matching using American Standard Code for Information Interchange Value
Commentz-Walter: Any Better than Aho-Corasick for Peptide Identification? 

An algorithm for locating all occurrences of a finite number of keywords in an arbitrary string, also known as multiple strings matching, is commonly required in information retrieval (such as sequence analysis, evolutionary biological studies, gene/protein identification and network intrusion detection) and text editing applications. Although Aho-Corasick was one of the commonly used exact multiple strings matching algorithm, Commentz-Walter has been introduced as a better alternative in the recent past. Comments-Walter algorithm combines ideas from both Aho-Corasick and Boyer Moore. Large scale rapid and accurate peptide identification is critical in computational proteomics. In this paper, we have critically analyzed the time complexity of Aho-Corasick and Commentz-Walter for their suitability in large scale peptide identification. According to the results we obtained for our dataset, we conclude that Aho-Corasick is performing better than Commentz-Walter as opposed to the common beliefs.
Gp 27[string matching].pptx![Gp 27[string matching].pptx](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Gp 27[string matching].pptx](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
It is string matching pattern from large text.it contains pseudo code, algorithm, advantages, drawbacks, conclusion and references as well.
String Match | Computer Science

Matching the String with a pattern is known as String Match”. Now, what are these strings and patterns? Alright, the string is that which is to be checked entered by the user and is matched with the pattern which is already in the database. Copy the link given below and paste it in new browser window to get more information on String Match:- www.transtutors.com/homework-help/computer-science/string-match.aspx
Row enumeration by Carpenter algorithm_ANIKET CHOUDHURY

This topic is from the subject DATA MINING.
It shows how efficiently data can be mined for a huge medical data base.
An Application of Pattern matching for Motif Identification

Pattern matching is one of the central and most widely studied problem in theoretical computer science. Solutions to the problem play an important role in many areas of science and information processing. Its performance has great impact on many applications including database query, text processing and DNA sequence analysis. In general Pattern matching algorithms are based on the shift value, the direction of the sliding window and the order in which comparisons are made. The performance of the algorithms can be enhanced to a great extent by a larger shift value and less number of comparison to get the shift value. In this paper we proposed an algorithm, for finding motif in DNA sequence. The algorithm is based on preprocessing of the pattern string(motif) by considering four consecutive nucleotides of the DNA that immediately follow the aligned pattern window in an event of mismatch between pattern(motif) and DNA sequence .Theoretically, we found the proposed algorithms work efficiently for motif identification.
Similar to String Matching Algorithms-The Naive Algorithm (18)
String_Matching_algorithm String_Matching_algorithm .pptx

String_Matching_algorithm String_Matching_algorithm .pptx
String Matching algorithm String Matching algorithm String Matching algorithm

String Matching algorithm String Matching algorithm String Matching algorithm
IMPLEMENTATION OF DIFFERENT PATTERN RECOGNITION ALGORITHM 

IMPLEMENTATION OF DIFFERENT PATTERN RECOGNITION ALGORITHM
Commentz-Walter: Any Better than Aho-Corasick for Peptide Identification? 

Commentz-Walter: Any Better than Aho-Corasick for Peptide Identification?
Row enumeration by Carpenter algorithm_ANIKET CHOUDHURY

Row enumeration by Carpenter algorithm_ANIKET CHOUDHURY
An Application of Pattern matching for Motif Identification

An Application of Pattern matching for Motif Identification
More from Adeel Rasheed
Multan to Sukkur Motorway (M5)

In these slides i describe the cost, history and other important information related to Multan to Sukkur Motorway (M5).
R Studio (Report)

In this file, I describe all the important points about R Studio with proper headings.
History of computer (1st to 5th Generations)

In these slides, I describe all the important points about all generations of computers. History of computer (1st to 5th Generations)
CSS Cascade Style Sheet

On these slides. I explain all the properties and values of CSS Cascade Style Sheet (CSS).
How to define CSS class or id. How to implement CSS on the HTML page.
Zooming and Its Types

On these slides, I describe all the important heading about Zooming and Its Types. For any Suggestion Contact me.
User Interface & Its Types

In these slides i describe user interface also its types. And put the other useful and important headings on it.
Questions About Android Application Development

In this file i describe all the important questions about android application development.
What is Android?
What is an Activity?
Describe android application architecture?
What is explicit intent?
What is APK format?
What is implicit intent?
What language does Android support to develop an application?
Human and Machine Learning

On these slides i describe all the important information about Human and Machine Learning.
Human & Machine Learning is very important topic.
Connection Establishment & Flow and Congestion Control

On these slides i describe all the detail about Connection Establishment & Flow and Congestion Control. For more detail visit: https://chauhantricks.blogspot.com/
IP Address - IPv4 & IPv6

On these slides i describe all the important points about IP Addressing and also describe the IPv4 and IPv6.
Computer Crime

On these slides i describe all the important points of computer crime with detail. For more detail visit: https://chauhantricks.blogspot.com/
Privacy and Security Information

On these slides i describe all the contents about Privacy and Security Information.
Code of Conduct - Code of Practice & Standards

In which we explain introduction, importance, sections, steps of creation, responsibilities, violations and some other important contents about codes of conduct.
Self Adaptive Systems

The complexity of current software-based systems has led the software engineering community to look for inspiration in diverse related fields (e.g., robotics, artificial intelligence) as well as other areas (e.g., biology) to find new ways of designing and managing systems and services.
Ethernet - LAN

Ethernet is a family of computer networking technologies for local area networks (LANs) and metropolitan area networks (MANs). It was commercially introduced in 1980 and first standardized in 1983 as IEEE 802.3, and has since been refined to support higher bit rates and longer link distances.
Synchronous and Asynchronous Transmission

On these slides i describe short detail about Synchronous and Asynchronous Transmission.
Intel Microprocessors 8086 Documentation

On this file i provide all the documentation of Intel Microprocessors 8086 for assignment and project.
Applications of Computer

On this document i describe most important application or users of computer.
More from Adeel Rasheed (20)
Connection Establishment & Flow and Congestion Control

Connection Establishment & Flow and Congestion Control
Recently uploaded
How world-class product teams are winning in the AI era by CEO and Founder, P...

How world-class product teams are winning in the AI era by CEO and Founder, Product School
Bits & Pixels using AI for Good.........

A whirlwind tour of tech & AI for socio-environmental impact.
State of ICS and IoT Cyber Threat Landscape Report 2024 preview

The IoT and OT threat landscape report has been prepared by the Threat Research Team at Sectrio using data from Sectrio, cyber threat intelligence farming facilities spread across over 85 cities around the world. In addition, Sectrio also runs AI-based advanced threat and payload engagement facilities that serve as sinks to attract and engage sophisticated threat actors, and newer malware including new variants and latent threats that are at an earlier stage of development.
The latest edition of the OT/ICS and IoT security Threat Landscape Report 2024 also covers:
State of global ICS asset and network exposure
Sectoral targets and attacks as well as the cost of ransom
Global APT activity, AI usage, actor and tactic profiles, and implications
Rise in volumes of AI-powered cyberattacks
Major cyber events in 2024
Malware and malicious payload trends
Cyberattack types and targets
Vulnerability exploit attempts on CVEs
Attacks on counties – USA
Expansion of bot farms – how, where, and why
In-depth analysis of the cyber threat landscape across North America, South America, Europe, APAC, and the Middle East
Why are attacks on smart factories rising?
Cyber risk predictions
Axis of attacks – Europe
Systemic attacks in the Middle East
Download the full report from here:
https://sectrio.com/resources/ot-threat-landscape-reports/sectrio-releases-ot-ics-and-iot-security-threat-landscape-report-2024/
Securing your Kubernetes cluster_ a step-by-step guide to success !

Today, after several years of existence, an extremely active community and an ultra-dynamic ecosystem, Kubernetes has established itself as the de facto standard in container orchestration. Thanks to a wide range of managed services, it has never been so easy to set up a ready-to-use Kubernetes cluster.
However, this ease of use means that the subject of security in Kubernetes is often left for later, or even neglected. This exposes companies to significant risks.
In this talk, I'll show you step-by-step how to secure your Kubernetes cluster for greater peace of mind and reliability.
Slack (or Teams) Automation for Bonterra Impact Management (fka Social Soluti...

Sidekick Solutions uses Bonterra Impact Management (fka Social Solutions Apricot) and automation solutions to integrate data for business workflows.
We believe integration and automation are essential to user experience and the promise of efficient work through technology. Automation is the critical ingredient to realizing that full vision. We develop integration products and services for Bonterra Case Management software to support the deployment of automations for a variety of use cases.
This video focuses on the notifications, alerts, and approval requests using Slack for Bonterra Impact Management. The solutions covered in this webinar can also be deployed for Microsoft Teams.
Interested in deploying notification automations for Bonterra Impact Management? Contact us at sales@sidekicksolutionsllc.com to discuss next steps.
Dev Dives: Train smarter, not harder – active learning and UiPath LLMs for do...

💥 Speed, accuracy, and scaling – discover the superpowers of GenAI in action with UiPath Document Understanding and Communications Mining™:
See how to accelerate model training and optimize model performance with active learning
Learn about the latest enhancements to out-of-the-box document processing – with little to no training required
Get an exclusive demo of the new family of UiPath LLMs – GenAI models specialized for processing different types of documents and messages
This is a hands-on session specifically designed for automation developers and AI enthusiasts seeking to enhance their knowledge in leveraging the latest intelligent document processing capabilities offered by UiPath.
Speakers:
👨🏫 Andras Palfi, Senior Product Manager, UiPath
👩🏫 Lenka Dulovicova, Product Program Manager, UiPath
DevOps and Testing slides at DASA Connect

My and Rik Marselis slides at 30.5.2024 DASA Connect conference. We discuss about what is testing, then what is agile testing and finally what is Testing in DevOps. Finally we had lovely workshop with the participants trying to find out different ways to think about quality and testing in different parts of the DevOps infinity loop.
Software Delivery At the Speed of AI: Inflectra Invests In AI-Powered Quality

In this insightful webinar, Inflectra explores how artificial intelligence (AI) is transforming software development and testing. Discover how AI-powered tools are revolutionizing every stage of the software development lifecycle (SDLC), from design and prototyping to testing, deployment, and monitoring.
Learn about:
• The Future of Testing: How AI is shifting testing towards verification, analysis, and higher-level skills, while reducing repetitive tasks.
• Test Automation: How AI-powered test case generation, optimization, and self-healing tests are making testing more efficient and effective.
• Visual Testing: Explore the emerging capabilities of AI in visual testing and how it's set to revolutionize UI verification.
• Inflectra's AI Solutions: See demonstrations of Inflectra's cutting-edge AI tools like the ChatGPT plugin and Azure Open AI platform, designed to streamline your testing process.
Whether you're a developer, tester, or QA professional, this webinar will give you valuable insights into how AI is shaping the future of software delivery.
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

In this session I delve into the encryption technology used in Microsoft 365 and Microsoft Purview. Including the concepts of Customer Key and Double Key Encryption.
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar
UiPath Test Automation using UiPath Test Suite series, part 3

Welcome to UiPath Test Automation using UiPath Test Suite series part 3. In this session, we will cover desktop automation along with UI automation.
Topics covered:
UI automation Introduction,
UI automation Sample
Desktop automation flow
Pradeep Chinnala, Senior Consultant Automation Developer @WonderBotz and UiPath MVP
Deepak Rai, Automation Practice Lead, Boundaryless Group and UiPath MVP
GenAISummit 2024 May 28 Sri Ambati Keynote: AGI Belongs to The Community in O...

“AGI should be open source and in the public domain at the service of humanity and the planet.”
GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...

Effective Application Security in Software Delivery lifecycle using Deployment Firewall and DBOM
The modern software delivery process (or the CI/CD process) includes many tools, distributed teams, open-source code, and cloud platforms. Constant focus on speed to release software to market, along with the traditional slow and manual security checks has caused gaps in continuous security as an important piece in the software supply chain. Today organizations feel more susceptible to external and internal cyber threats due to the vast attack surface in their applications supply chain and the lack of end-to-end governance and risk management.
The software team must secure its software delivery process to avoid vulnerability and security breaches. This needs to be achieved with existing tool chains and without extensive rework of the delivery processes. This talk will present strategies and techniques for providing visibility into the true risk of the existing vulnerabilities, preventing the introduction of security issues in the software, resolving vulnerabilities in production environments quickly, and capturing the deployment bill of materials (DBOM).
Speakers:
Bob Boule
Robert Boule is a technology enthusiast with PASSION for technology and making things work along with a knack for helping others understand how things work. He comes with around 20 years of solution engineering experience in application security, software continuous delivery, and SaaS platforms. He is known for his dynamic presentations in CI/CD and application security integrated in software delivery lifecycle.
Gopinath Rebala
Gopinath Rebala is the CTO of OpsMx, where he has overall responsibility for the machine learning and data processing architectures for Secure Software Delivery. Gopi also has a strong connection with our customers, leading design and architecture for strategic implementations. Gopi is a frequent speaker and well-known leader in continuous delivery and integrating security into software delivery.
Neuro-symbolic is not enough, we need neuro-*semantic*

Neuro-symbolic (NeSy) AI is on the rise. However, simply machine learning on just any symbolic structure is not sufficient to really harvest the gains of NeSy. These will only be gained when the symbolic structures have an actual semantics. I give an operational definition of semantics as “predictable inference”.
All of this illustrated with link prediction over knowledge graphs, but the argument is general.
To Graph or Not to Graph Knowledge Graph Architectures and LLMs

Reflecting on new architectures for knowledge based systems in light of generative ai
Accelerate your Kubernetes clusters with Varnish Caching

A presentation about the usage and availability of Varnish on Kubernetes. This talk explores the capabilities of Varnish caching and shows how to use the Varnish Helm chart to deploy it to Kubernetes.
This presentation was delivered at K8SUG Singapore. See https://feryn.eu/presentations/accelerate-your-kubernetes-clusters-with-varnish-caching-k8sug-singapore-28-2024 for more details.
UiPath Test Automation using UiPath Test Suite series, part 4

Welcome to UiPath Test Automation using UiPath Test Suite series part 4. In this session, we will cover Test Manager overview along with SAP heatmap.
The UiPath Test Manager overview with SAP heatmap webinar offers a concise yet comprehensive exploration of the role of a Test Manager within SAP environments, coupled with the utilization of heatmaps for effective testing strategies.
Participants will gain insights into the responsibilities, challenges, and best practices associated with test management in SAP projects. Additionally, the webinar delves into the significance of heatmaps as a visual aid for identifying testing priorities, areas of risk, and resource allocation within SAP landscapes. Through this session, attendees can expect to enhance their understanding of test management principles while learning practical approaches to optimize testing processes in SAP environments using heatmap visualization techniques
What will you get from this session?
1. Insights into SAP testing best practices
2. Heatmap utilization for testing
3. Optimization of testing processes
4. Demo
Topics covered:
Execution from the test manager
Orchestrator execution result
Defect reporting
SAP heatmap example with demo
Speaker:
Deepak Rai, Automation Practice Lead, Boundaryless Group and UiPath MVP
Recently uploaded (20)
How world-class product teams are winning in the AI era by CEO and Founder, P...

How world-class product teams are winning in the AI era by CEO and Founder, P...
State of ICS and IoT Cyber Threat Landscape Report 2024 preview

State of ICS and IoT Cyber Threat Landscape Report 2024 preview
Securing your Kubernetes cluster_ a step-by-step guide to success !

Securing your Kubernetes cluster_ a step-by-step guide to success !
Slack (or Teams) Automation for Bonterra Impact Management (fka Social Soluti...

Slack (or Teams) Automation for Bonterra Impact Management (fka Social Soluti...
Dev Dives: Train smarter, not harder – active learning and UiPath LLMs for do...

Dev Dives: Train smarter, not harder – active learning and UiPath LLMs for do...
FIDO Alliance Osaka Seminar: Passkeys and the Road Ahead.pdf

FIDO Alliance Osaka Seminar: Passkeys and the Road Ahead.pdf
Software Delivery At the Speed of AI: Inflectra Invests In AI-Powered Quality

Software Delivery At the Speed of AI: Inflectra Invests In AI-Powered Quality
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

Encryption in Microsoft 365 - ExpertsLive Netherlands 2024
FIDO Alliance Osaka Seminar: FIDO Security Aspects.pdf

FIDO Alliance Osaka Seminar: FIDO Security Aspects.pdf
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf
UiPath Test Automation using UiPath Test Suite series, part 3

UiPath Test Automation using UiPath Test Suite series, part 3
GenAISummit 2024 May 28 Sri Ambati Keynote: AGI Belongs to The Community in O...

GenAISummit 2024 May 28 Sri Ambati Keynote: AGI Belongs to The Community in O...
GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...

GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...
Neuro-symbolic is not enough, we need neuro-*semantic*

Neuro-symbolic is not enough, we need neuro-*semantic*
To Graph or Not to Graph Knowledge Graph Architectures and LLMs

To Graph or Not to Graph Knowledge Graph Architectures and LLMs
Accelerate your Kubernetes clusters with Varnish Caching

Accelerate your Kubernetes clusters with Varnish Caching
UiPath Test Automation using UiPath Test Suite series, part 4

UiPath Test Automation using UiPath Test Suite series, part 4
String Matching Algorithms-The Naive Algorithm
- 1. STRING MATCHING ALGORITHMS A B C A B A A C A B SHIFT=3 A B A A
- 2. BY: Adeel Rasheed For More Slides and Information Visit: https://chauhantricks.blogspot.com/
- 3. WHAT IS STRING MATCHING • In computer science, string searching algorithms, sometimes called string matching algorithms, that try to find a place where one or several string (also called pattern) are found within a larger string or text.
- 4. EXAMPLE STRING MATCHING PROBLEM TEXTA B C A B A A C A B SHIFT=3 A B A A
- 5. Types of SMA The Naive string-matching algorithm The Rabin-Krap algorithm String matching with finite automata The Knuth-Morris-Pratt algorithm
- 6. THE NAIVE ALGORITHM The idea of the naive solution is just to make a comparison character by character of the text for all pattern. It returns all the valid shifts found. P=Pattern T=Text S=Shift
- 7. THE NAIVE ALGORITHM T[n]=T[0,1…n-1] P[m]=P[0,1…m-1] NAIVE-STRING-MATCHER(T,P) 1) n = T.length 2) m = P.length 3) for s=0 to n-m 4) if P[0…m-1]==T[s+0….s+m-1] 5) print” Pattern occurs with shift ” s
- 8. EXAMPLE SUPPOSE, T=1011101110 P=111 FIND ALL VALIDSHIFT…… 1 0 1 1 1 0 1 1 1 0 1 1 1P=Patter n T=Text S=0
- 9. 1 0 1 1 1 0 1 1 1 0 1 1 1 S=1
- 10. 1 0 1 1 1 0 1 1 1 0 1 1 1 S=2 So, S=2 is a valid shift…
- 11. 1 0 1 1 1 0 1 1 1 0 S=3 1 1 1
- 12. 1 0 1 1 1 0 1 1 1 0 S=4 1 1 1
- 13. 1 0 1 1 1 0 1 1 1 0 1 1 1 S=5
- 14. 1 0 1 1 1 0 1 1 1 0 S=6 1 1 1 So, S=6 is a valid shift…
- 15. 1 0 1 1 1 0 1 1 1 0 1 1 1 S=7
