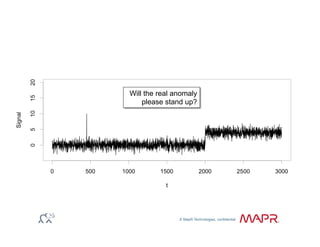
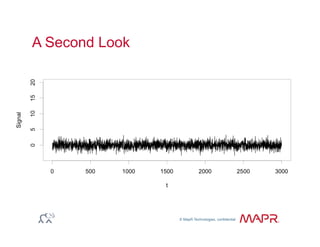
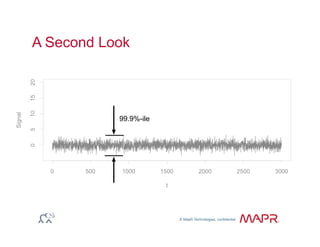
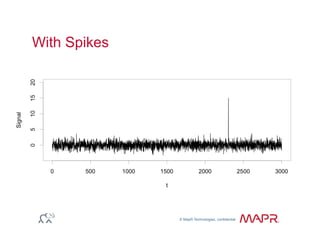
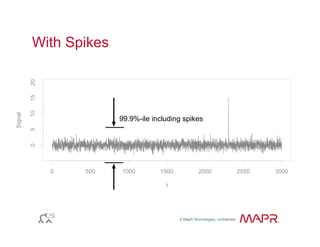
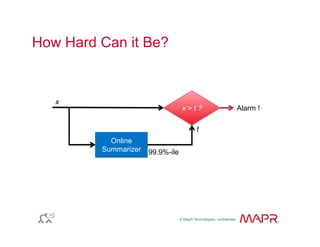
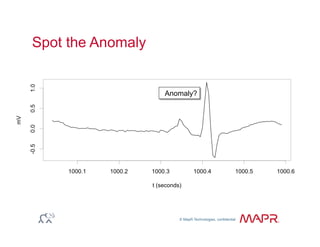
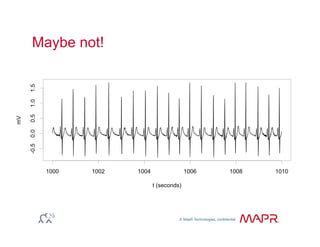
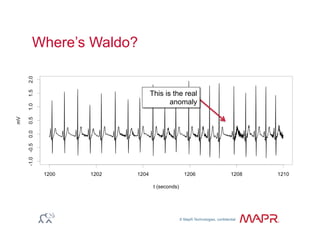
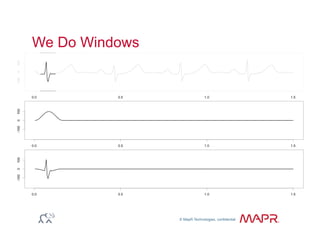
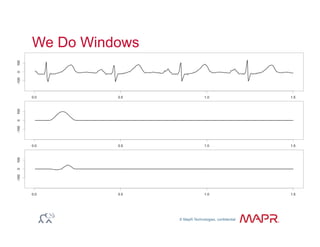
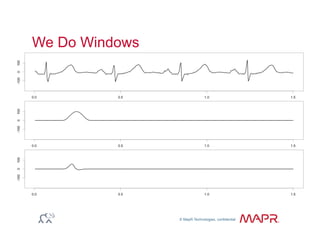
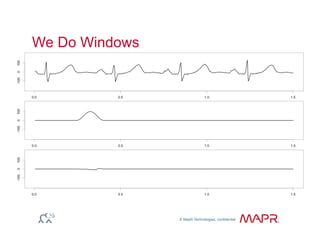
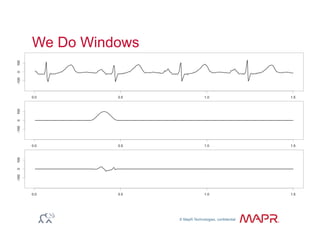
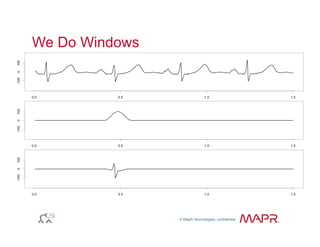
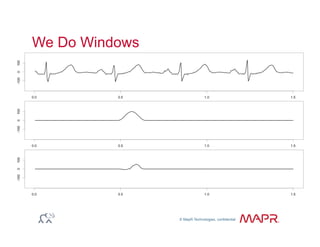
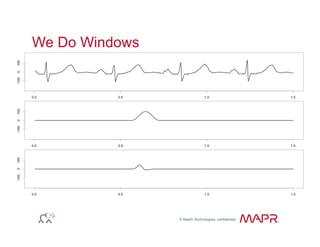
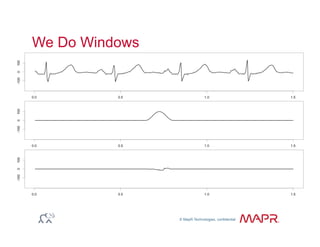
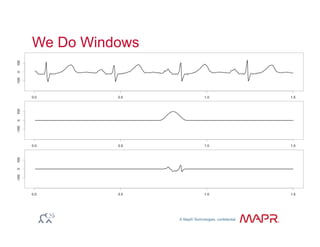
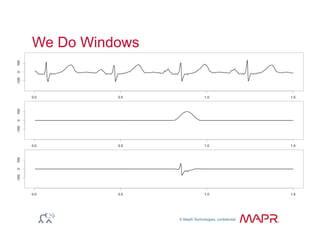
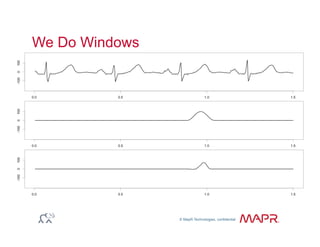
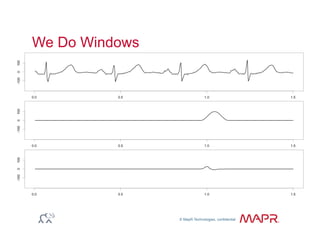
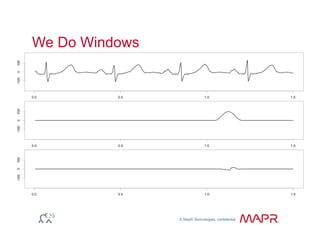
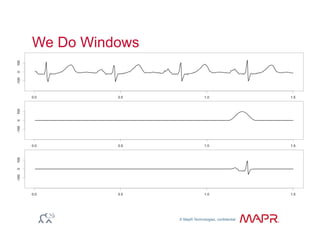
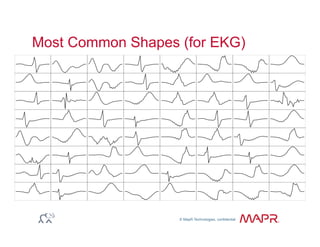
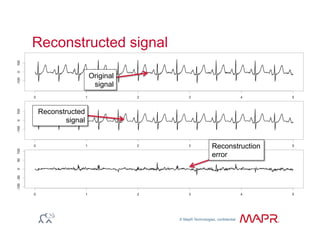
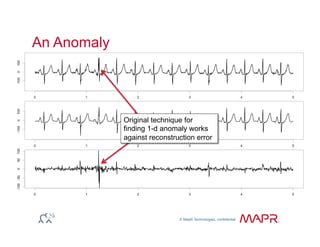
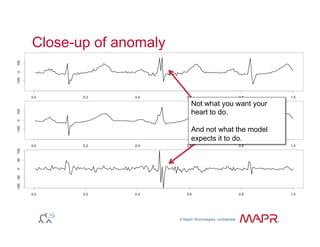
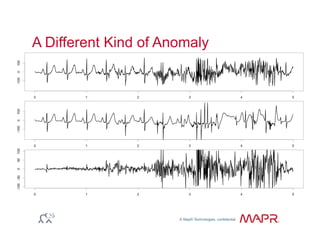
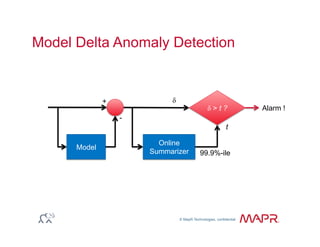
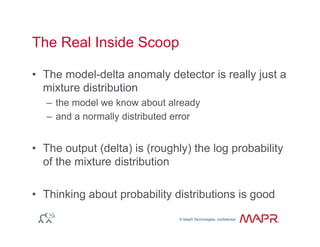
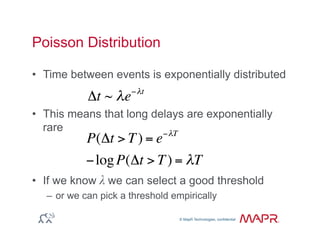
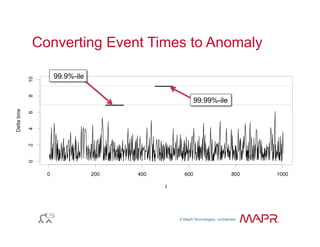
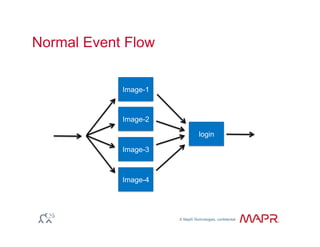
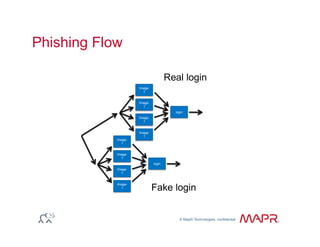
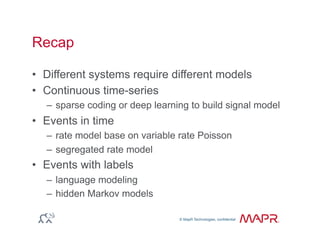
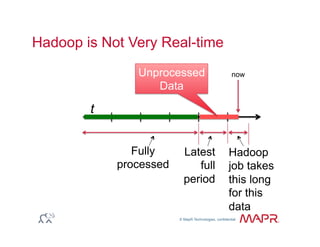
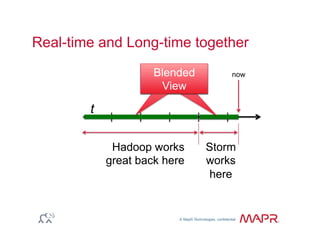
The document provides an overview of anomaly detection, its significance, and various implementation methods. It discusses the challenges of identifying anomalies without incurring high costs from false alarms and false negatives, emphasizing the importance of a well-defined model of 'normal.' Various models and techniques, including online percentile estimation and event stream analysis, are highlighted as solutions for improving anomaly detection accuracy.