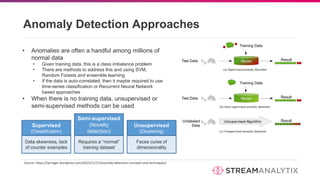
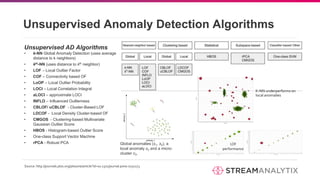
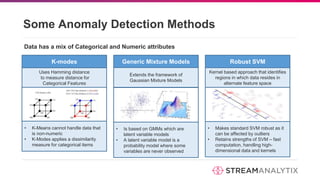
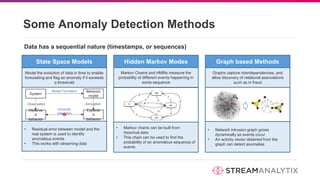
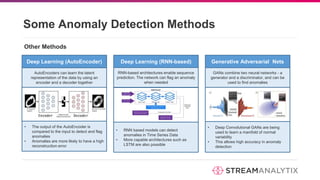
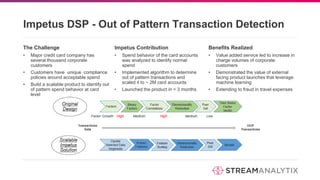
The document discusses anomaly detection methodologies and their implementations using Spark, presented by experts at a meetup in December 2017. It highlights various applications across sectors such as finance, healthcare, and manufacturing, emphasizing the significance of detecting unusual patterns to prevent fraud, operational inefficiencies, and service disruptions. Additionally, it outlines different algorithms and approaches for anomaly detection, showcasing their effectiveness in real-time data analysis.