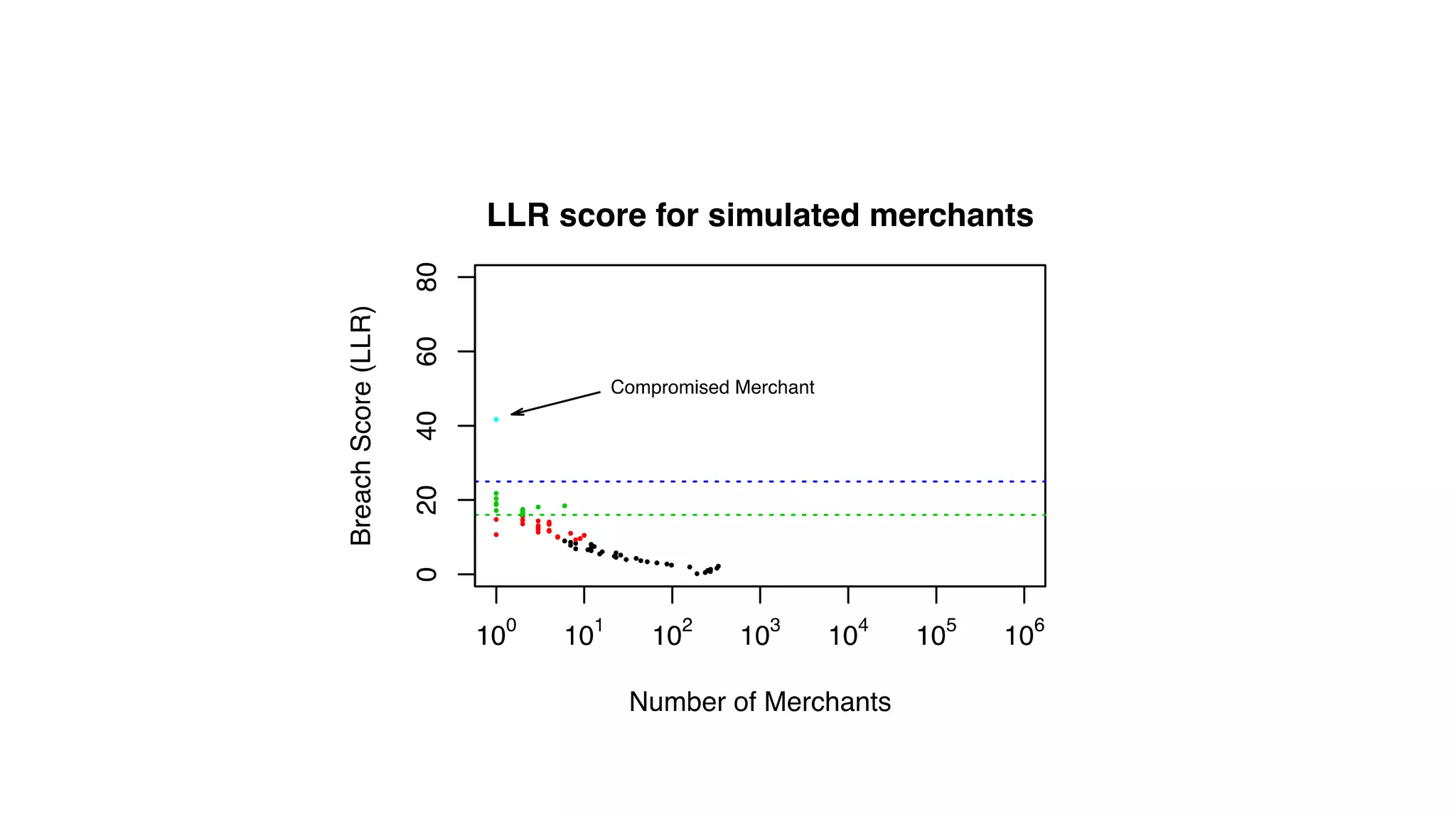
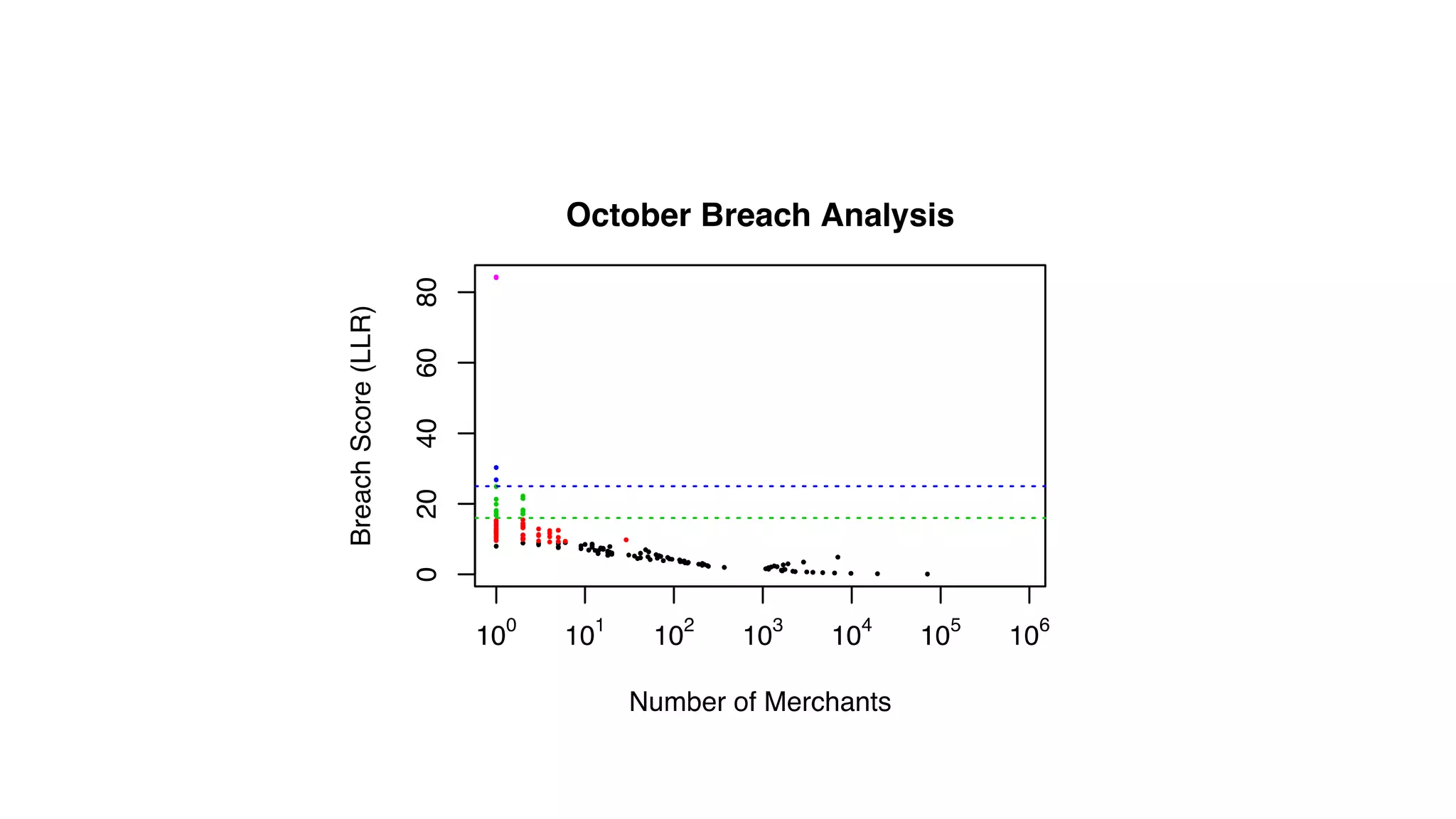
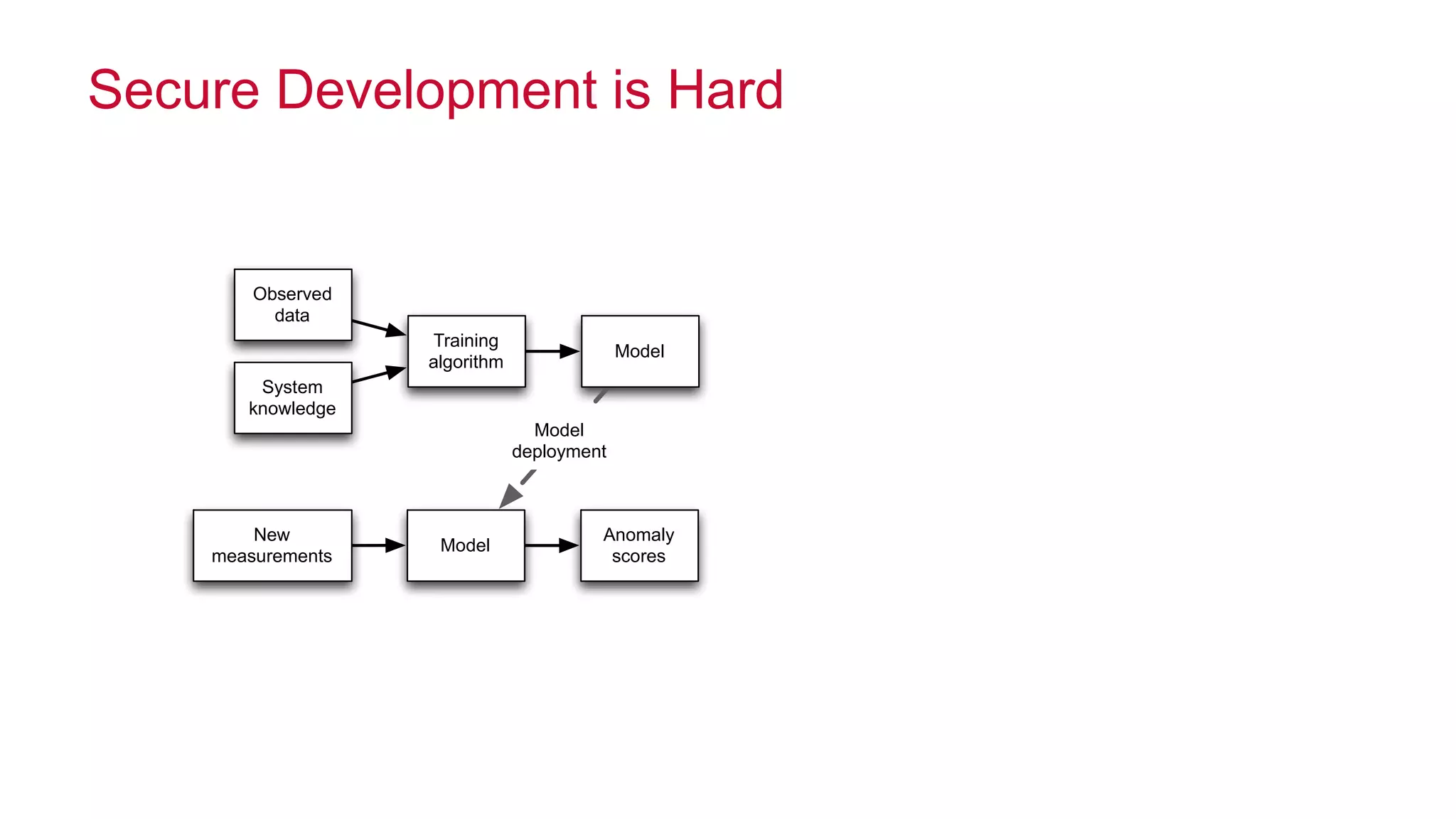
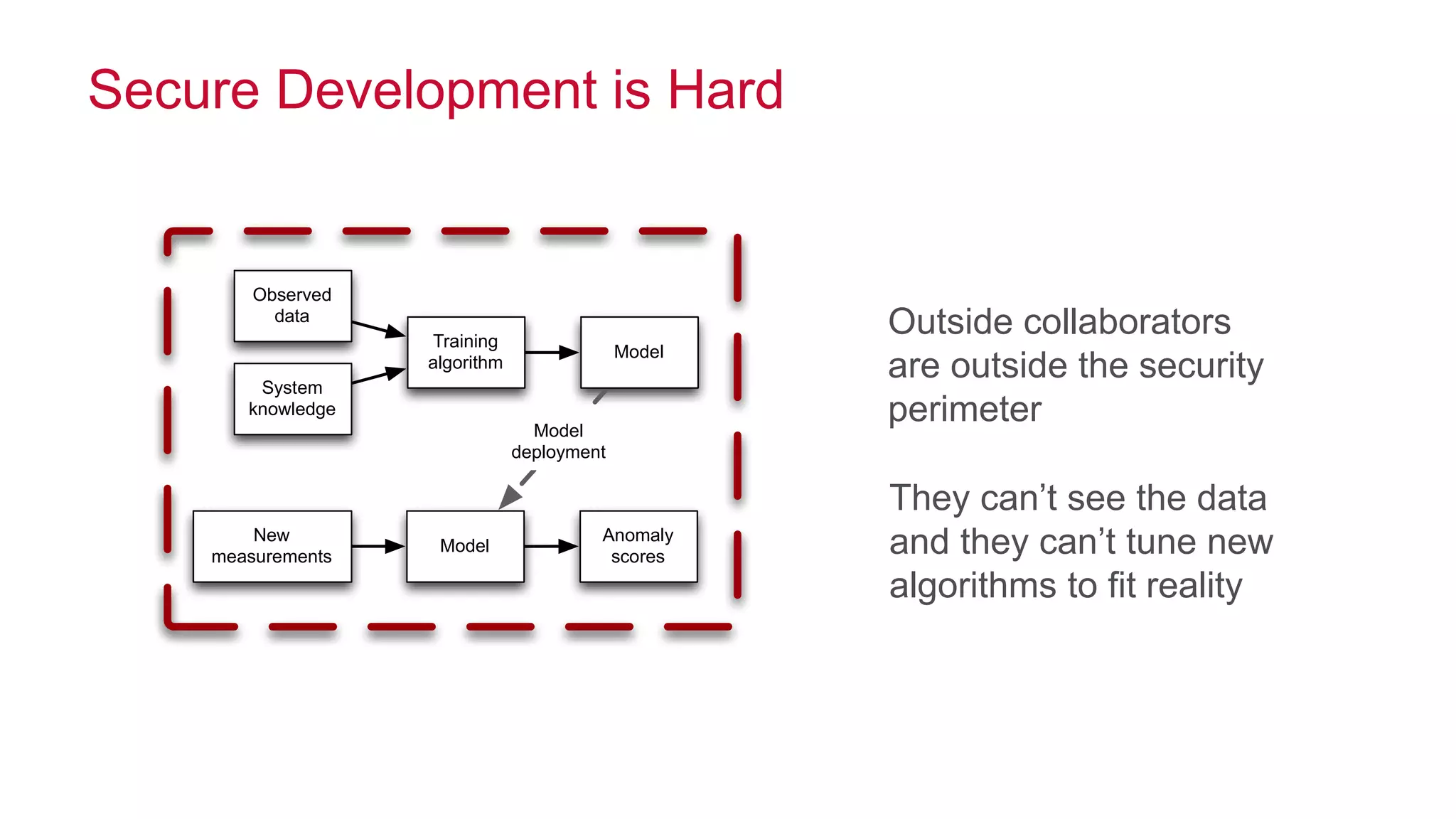
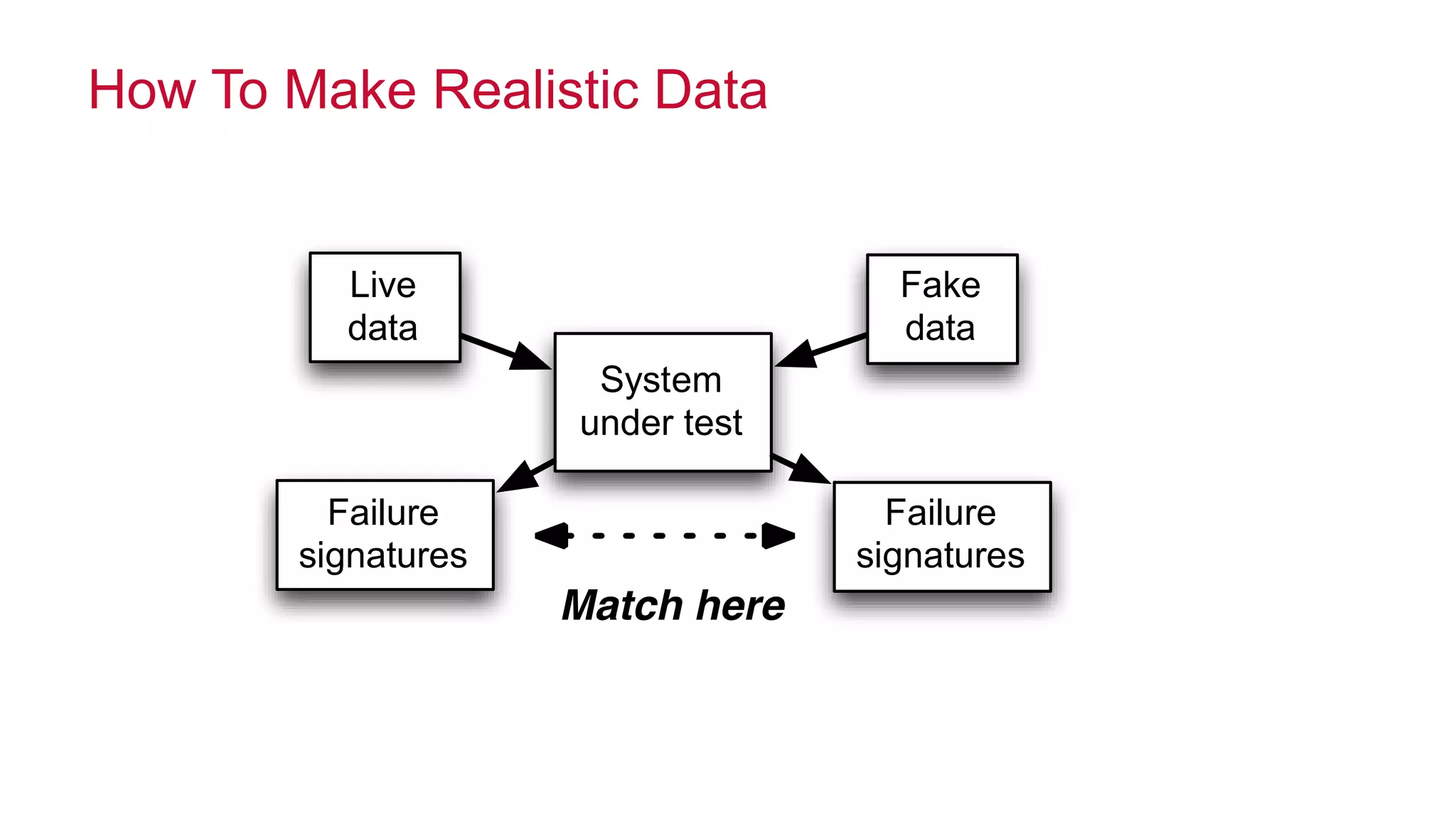
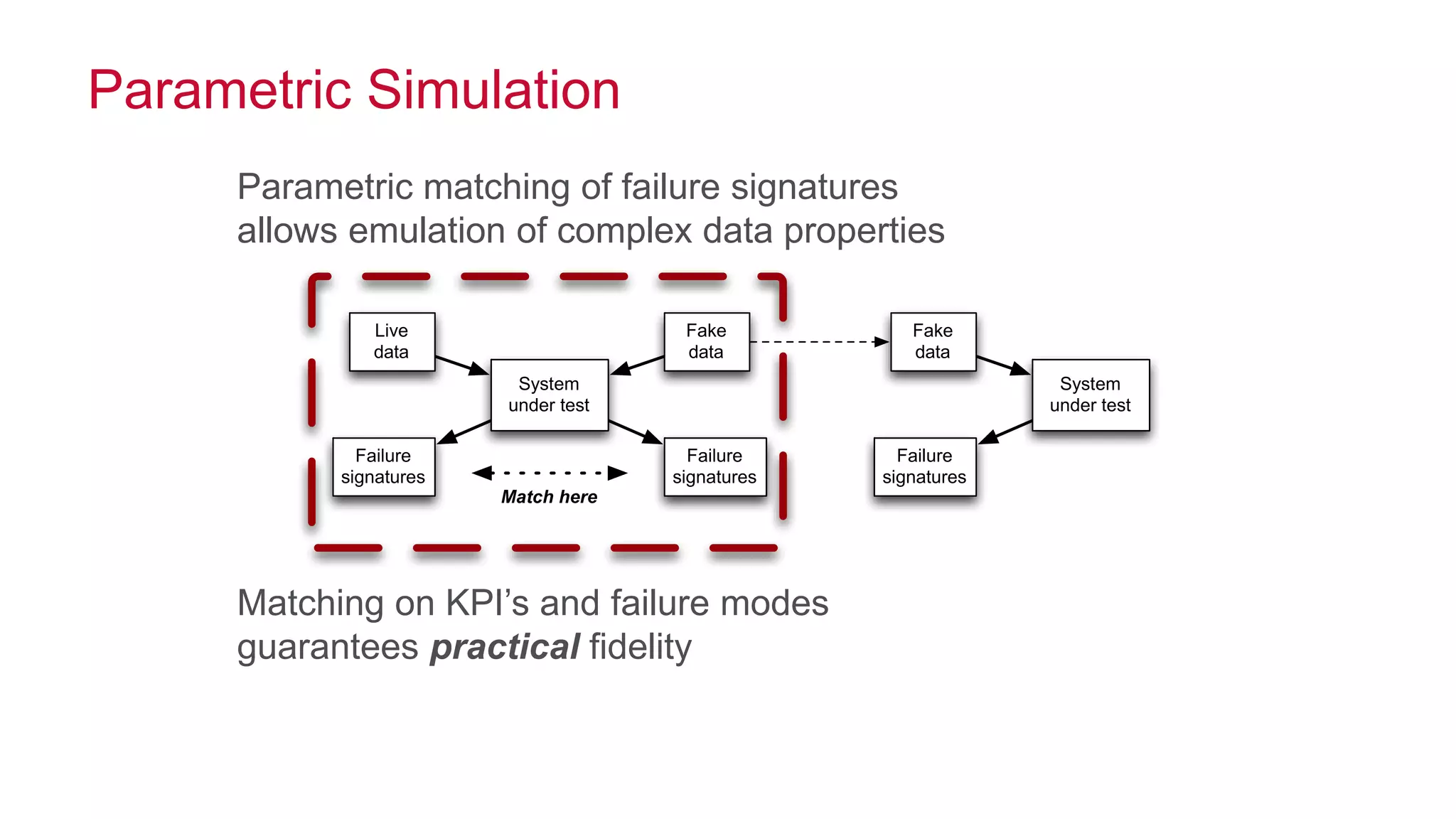
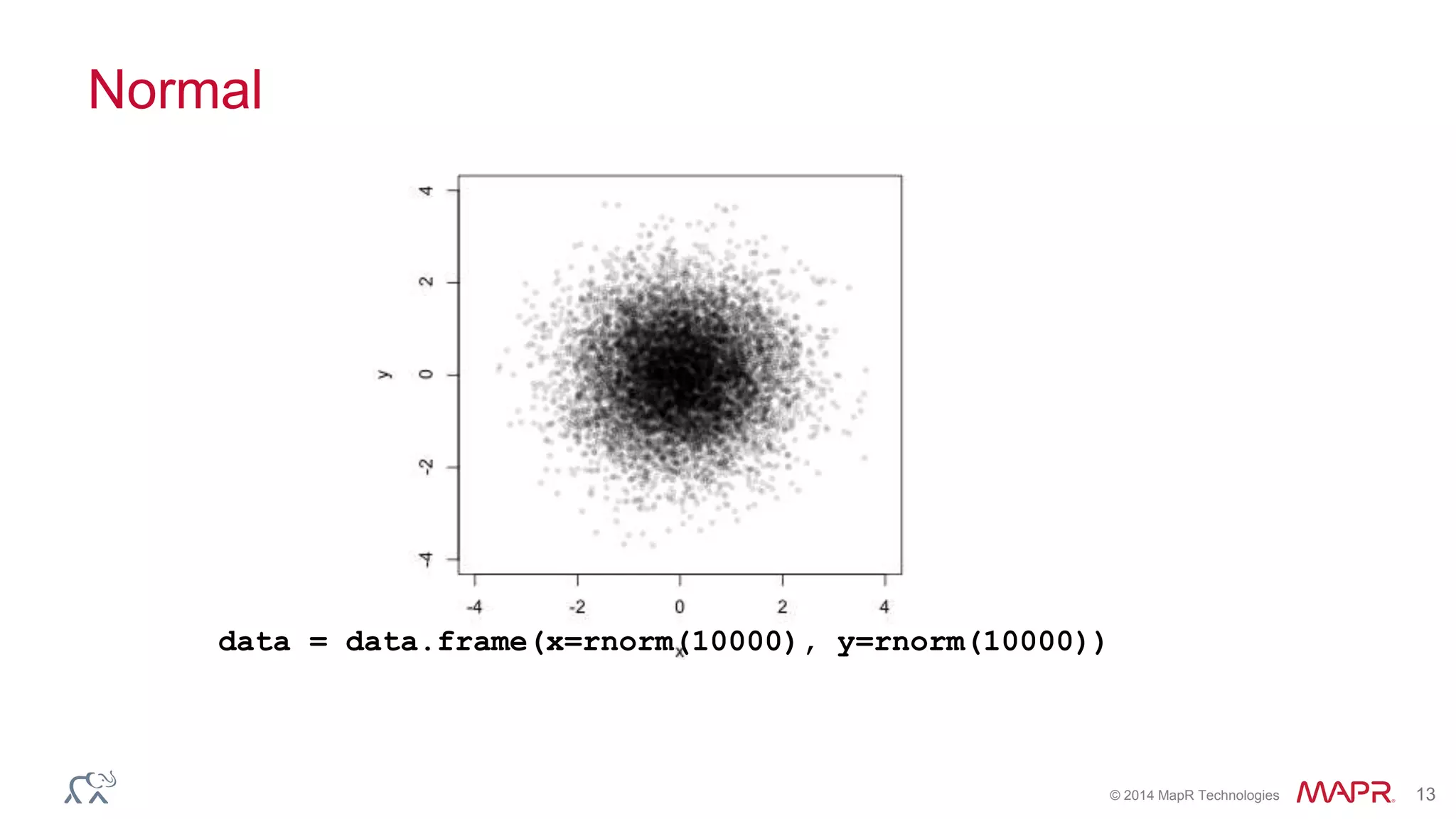
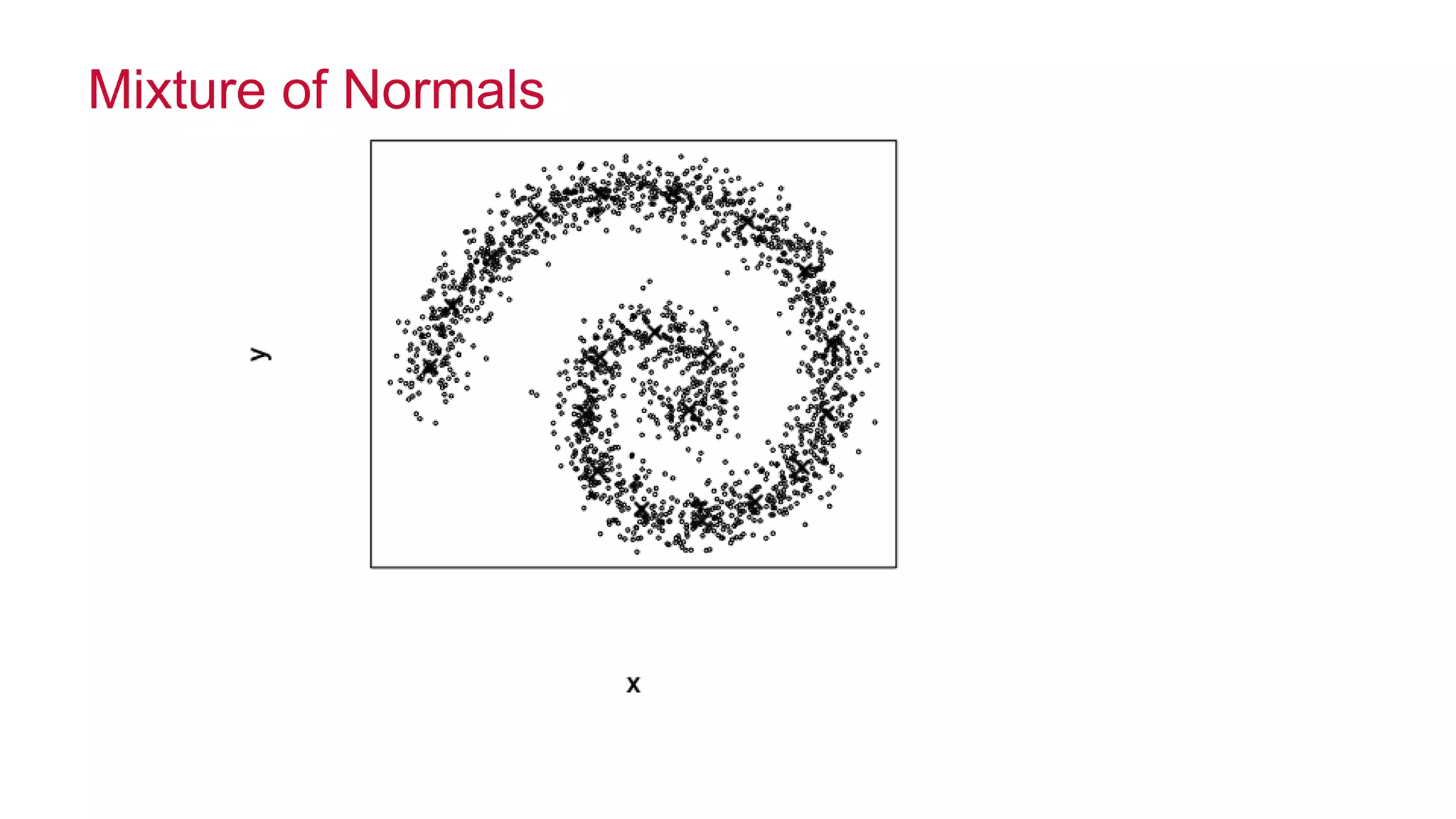
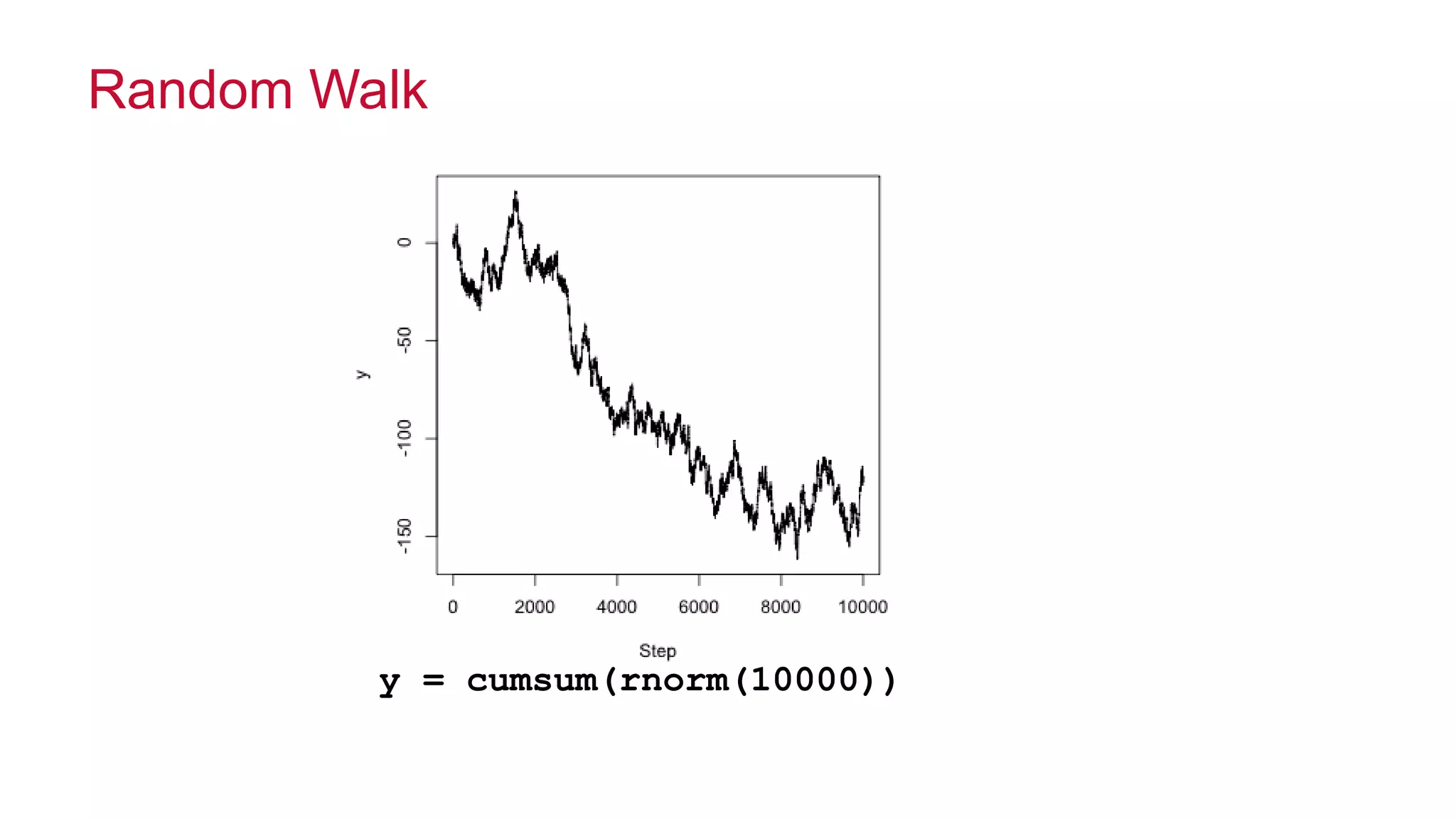
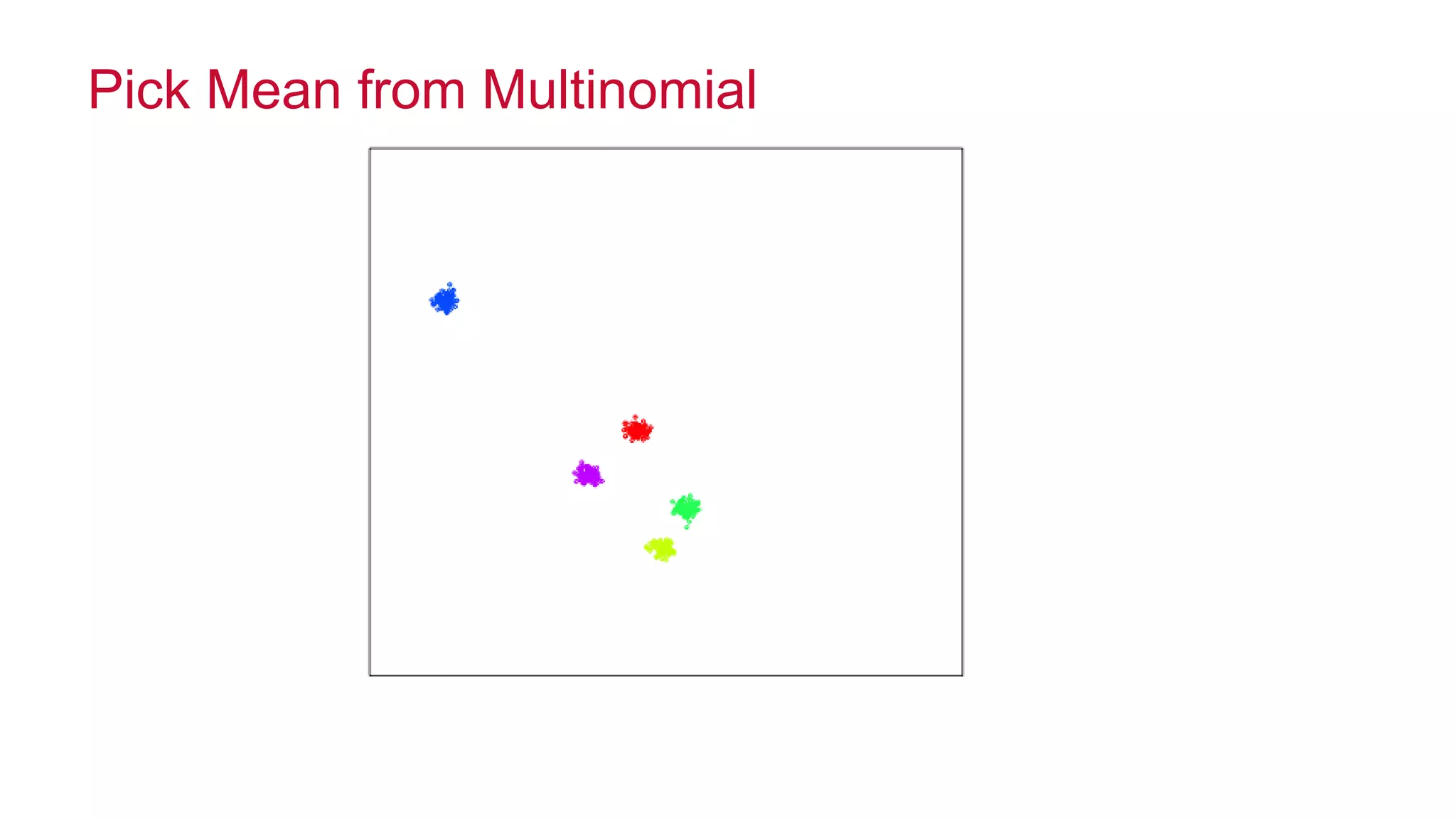
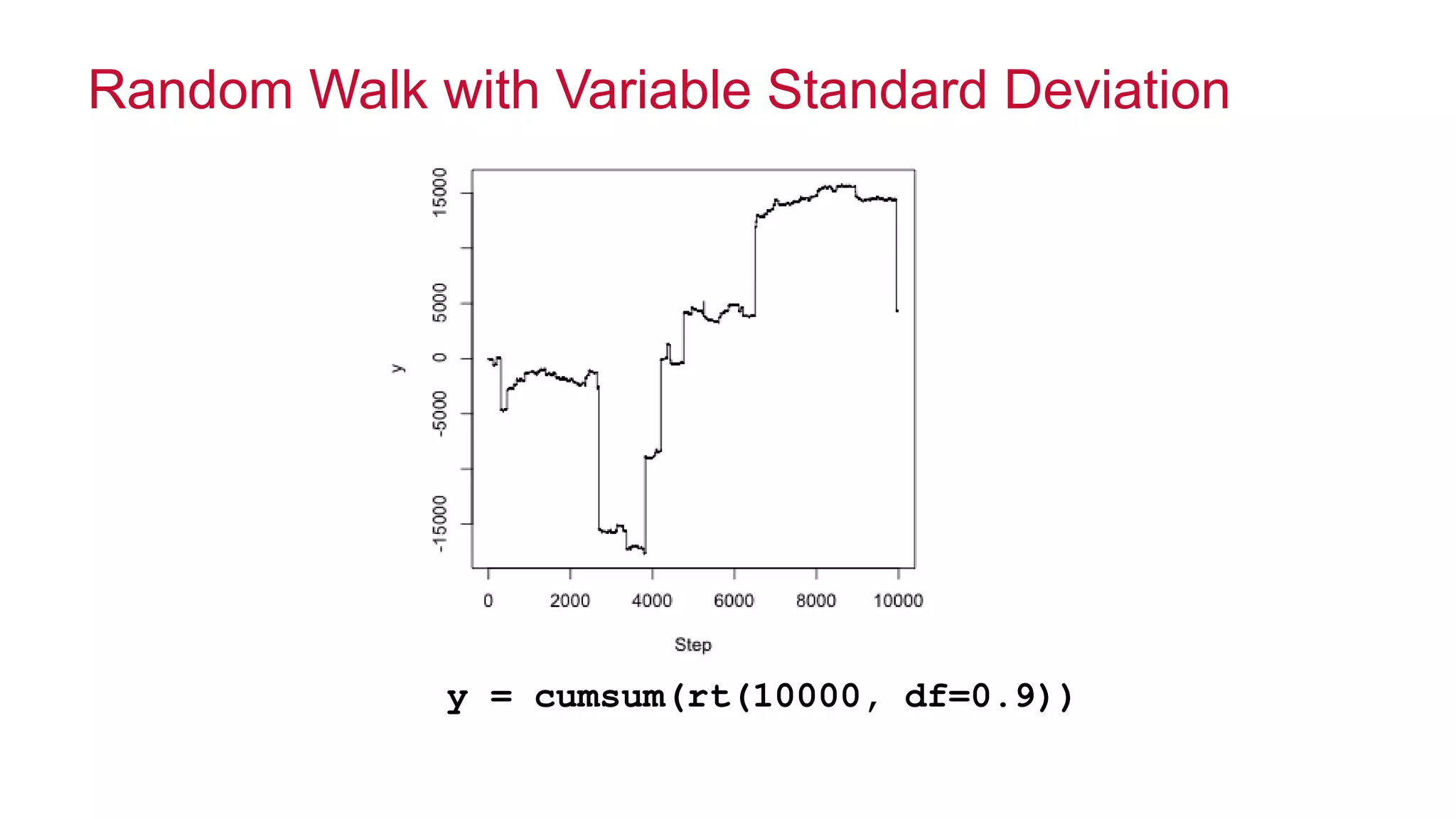
The document features a presentation by Ted Dunning, Chief Applications Architect at MapR Technologies, discussing techniques for anomaly detection and fraud analytics in complex systems. It highlights the challenges of secure development and collaboration on detection algorithms while sharing methods for generating realistic data for testing. Key topics include the simulation of failure signatures, performance metrics, and data generation methods using various statistical distributions.







![© 2014 MapR Technologies 19
Skewed Integers
207 3
203 0
198 7
196 4
195 12
193 10
189 2
187 1
185 13
179 6
178 9
177 5
177 25
174 21
173 8
173 14
170 18
[
{"name":"x", "class":"int", "skew":1}
]](https://image.slidesharecdn.com/realisticsyntheticgenerationallowssecuredevelopment-150611203308-lva1-app6891/75/Realistic-Synthetic-Generation-Allows-Secure-Development-19-2048.jpg)