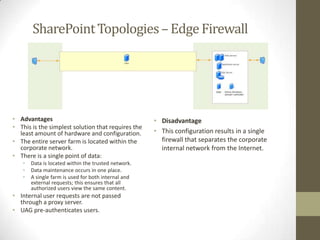
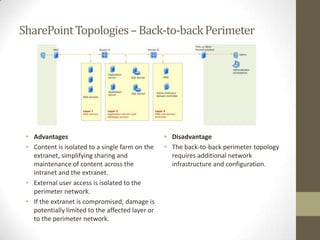
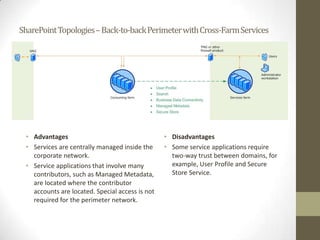
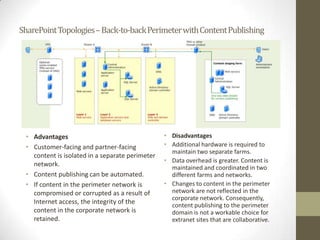
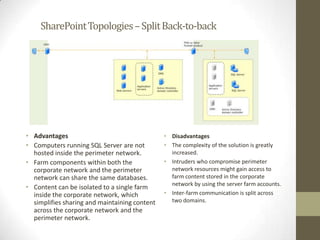
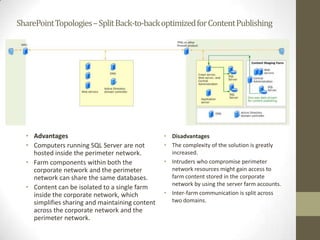
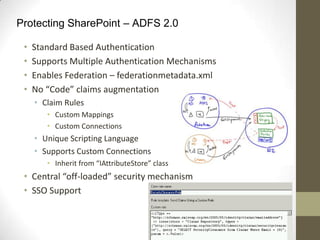
This document provides an overview of securing SharePoint. It discusses SharePoint security in general and different SharePoint topologies including edge firewall, back-to-back perimeter, and split back-to-back configurations. It also covers protecting SharePoint through authentication and authorization, digital rights management, data encryption, and server and general guidelines. Specific techniques discussed include Active Directory Federation Services, Windows firewall policies, SQL server port configuration, and claim attributes.