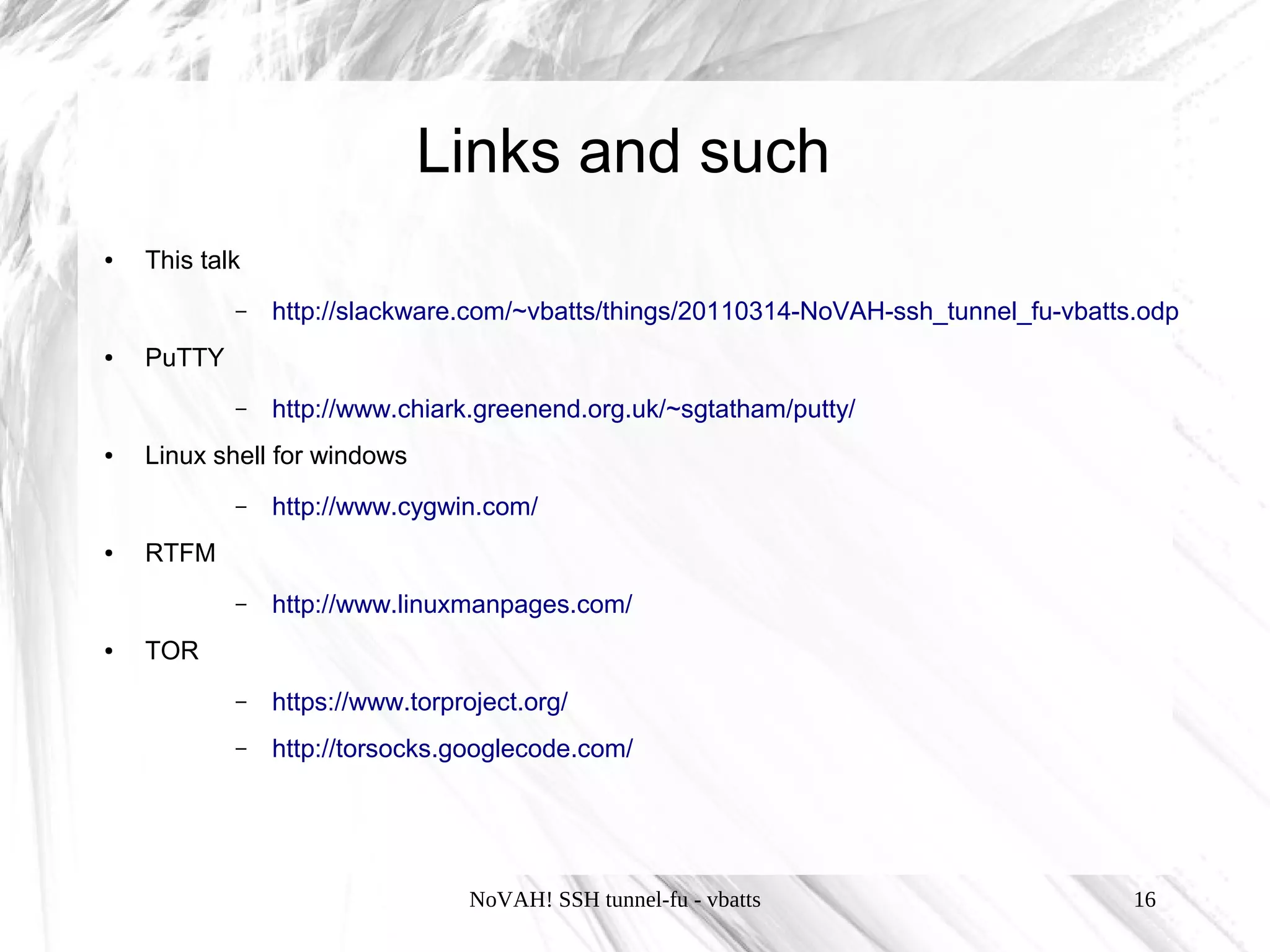
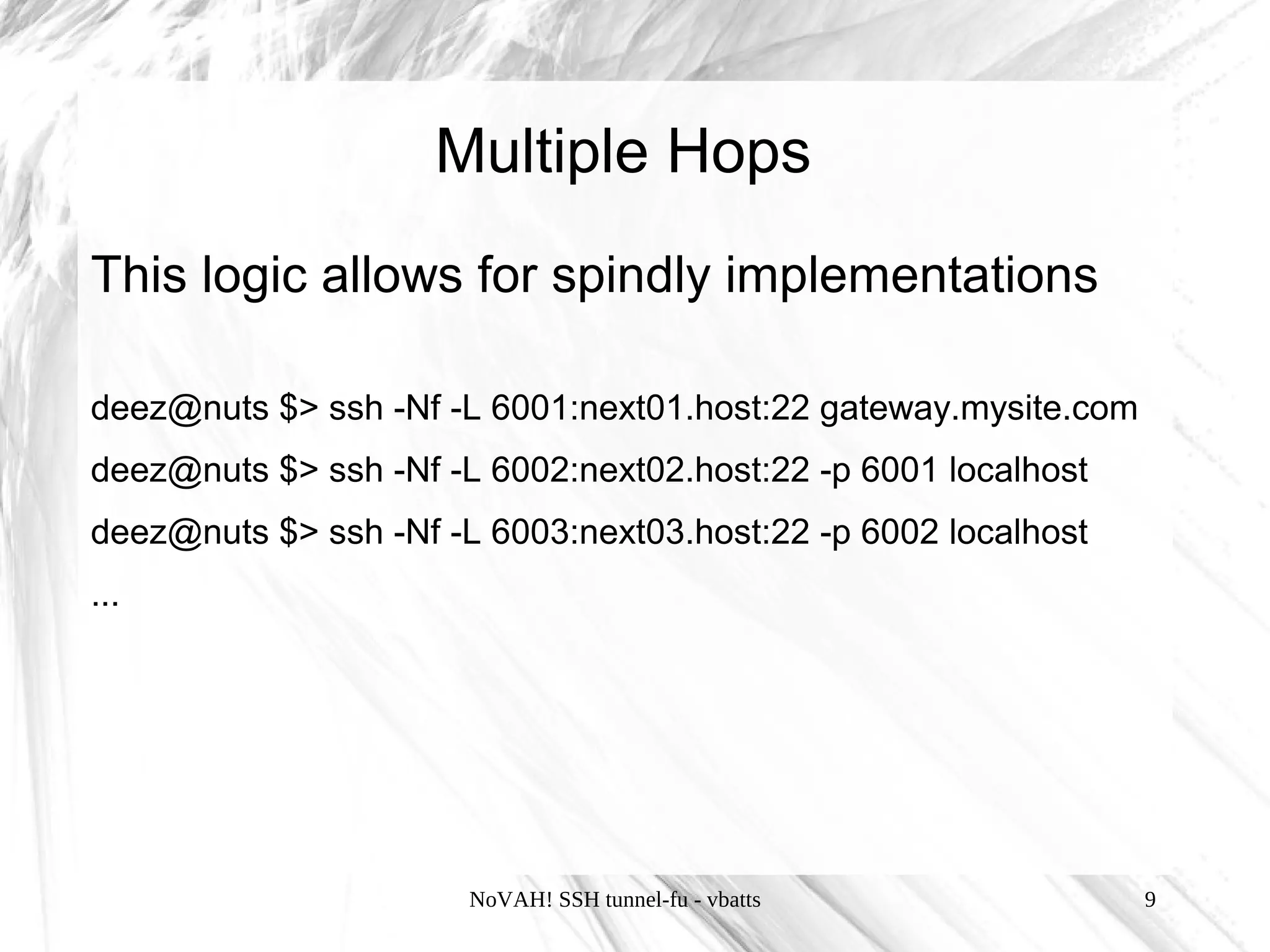
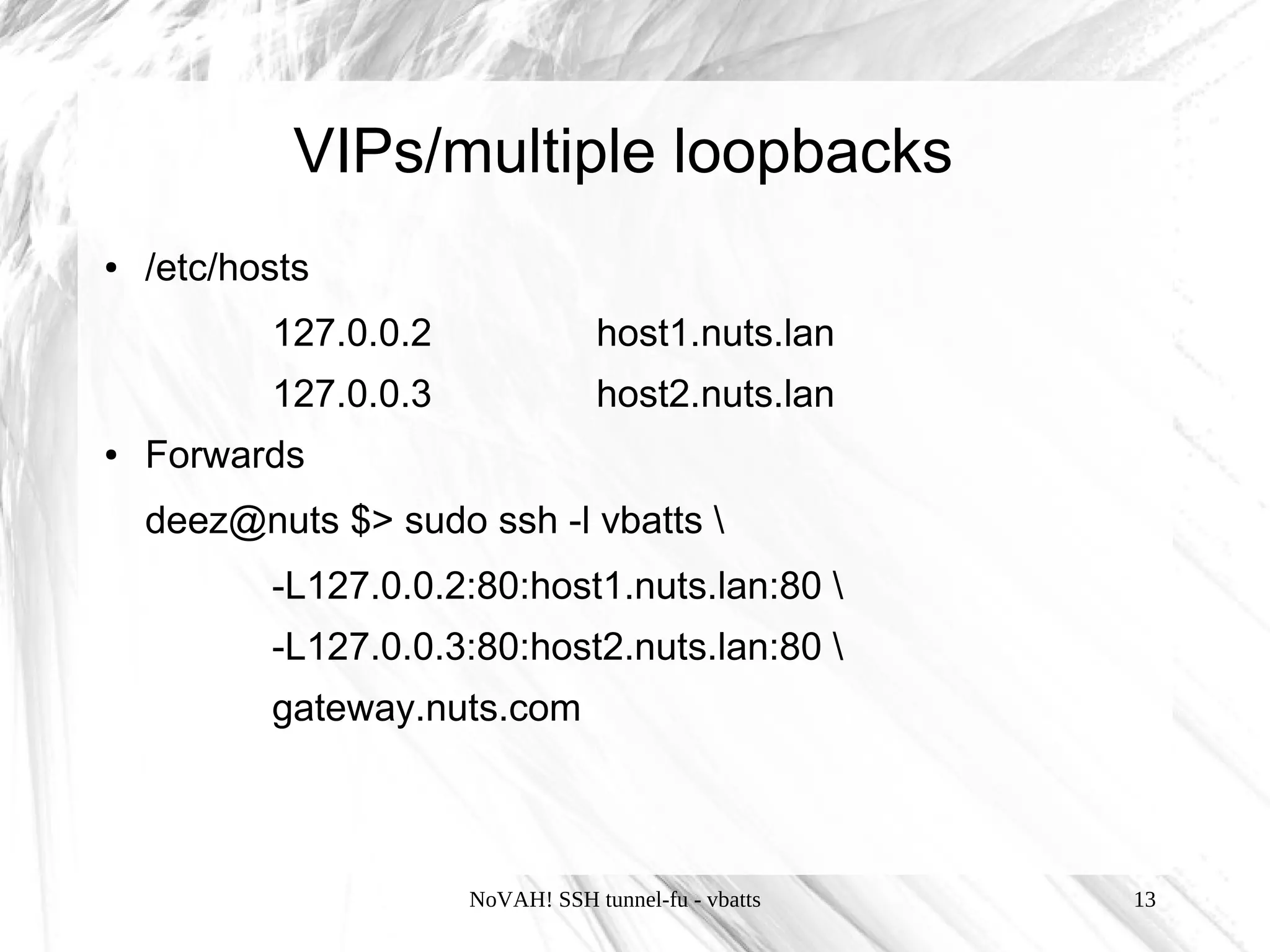
This document discusses using SSH tunnels, known as "SSH tunnel-fu", to securely forward network connections over an encrypted SSH connection. It describes three types of SSH tunnels - local, remote, and dynamic tunnels - and how to configure each using SSH flags or the SSH configuration file. It also provides examples of using tunnels to access internal servers remotely, create SOCKS proxies, and set up multi-hop tunnels through gateway hosts.





![Forwards
● Local
– ssh flag: -L [bind_address:]port:host:hostport
– ssh_config: LocalForward
● Remote
– ssh flag: -R [bind_address:]port:host:hostport
– ssh_config: RemoteForward
● Dynamic
– ssh flag: -D [bind_address:]port
– ssh_config: DynamicForward
– Currently SOCKS4 and SOCKS5 proxy allowed
NoVAH! SSH tunnel-fu - vbatts 6](https://image.slidesharecdn.com/20110314-novah-sshtunnelfu-vbatts-121128100123-phpapp01/75/SSH-Tunnel-Fu-NoVaH-2011-6-2048.jpg)
![Forwards
● Local
– ssh flag: -L [bind_address:]port:host:hostport
– ssh_config: LocalForward
● Remote
– ssh flag: -R [bind_address:]port:host:hostport
– ssh_config: RemoteForward
● Dynamic
– ssh flag: -D [bind_address:]port
– ssh_config: DynamicForward
– Currently SOCKS4 and SOCKS5 proxy allowed
NoVAH! SSH tunnel-fu - vbatts 7](https://image.slidesharecdn.com/20110314-novah-sshtunnelfu-vbatts-121128100123-phpapp01/75/SSH-Tunnel-Fu-NoVaH-2011-7-2048.jpg)
![Forwards
● Local
– ssh flag: -L [bind_address:]port:host:hostport
– ssh_config: LocalForward
● Remote
– ssh flag: -R [bind_address:]port:host:hostport
– ssh_config: RemoteForward
● Dynamic
– ssh flag: -D [bind_address:]port
– ssh_config: DynamicForward
– Currently SOCKS4 and SOCKS5 proxy allowed
NoVAH! SSH tunnel-fu - vbatts 8](https://image.slidesharecdn.com/20110314-novah-sshtunnelfu-vbatts-121128100123-phpapp01/75/SSH-Tunnel-Fu-NoVaH-2011-8-2048.jpg)
![In Session
~# List forwarded connections
~C Open command line.
Primarily for -L, -R or -D and also
-KR[bind_address:]port
NoVAH! SSH tunnel-fu - vbatts 10](https://image.slidesharecdn.com/20110314-novah-sshtunnelfu-vbatts-121128100123-phpapp01/75/SSH-Tunnel-Fu-NoVaH-2011-10-2048.jpg)
![To loopback or not?
● the [bind_address] can be very handy
● default bind_address is 127.0.0.1 (localhost)
● ADVISORY: don't forget about your firewall configuration
● ADVISORY: privileged ports require root
● allows a local system to serve local traffic to a remote
destination
deez@lappy $> ssh -L0.0.0.0:3389:winderz.nuts.lan gateway.nuts.com
NoVAH! SSH tunnel-fu - vbatts 11](https://image.slidesharecdn.com/20110314-novah-sshtunnelfu-vbatts-121128100123-phpapp01/75/SSH-Tunnel-Fu-NoVaH-2011-11-2048.jpg)


![Proxying
● Privoxy
deez@lappy $> ssh -L8118:localhost:8118 myhome.dyndns.org
● DNS Leakage :(
– Frequent and common
– [insert tor here]
● The Onion Router and helpers like torsocks
allow anonymized, encrypted and DNS leak-
safe traffic for a host of applications
– https://www.torproject.org/
– http://torsocks.googlecode.com/
NoVAH! SSH tunnel-fu - vbatts 15](https://image.slidesharecdn.com/20110314-novah-sshtunnelfu-vbatts-121128100123-phpapp01/75/SSH-Tunnel-Fu-NoVaH-2011-15-2048.jpg)