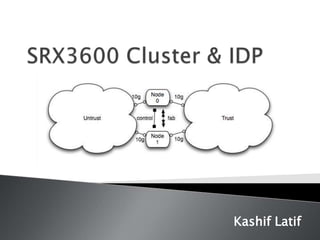
The SRX Clustering Module (SCM) enables dual control link capability for SRX3600 chassis clusters in Junos OS Release 10.2. When deployed in high availability clusters, the SRX cluster module provides full control link redundancy for critical environments utilizing the redundant architecture of SRX3000 series devices. To form a chassis cluster, a pair of the same type of SRX or J-series devices combine to act as a single system enforcing the same security policies, with some differences in required matching components depending on the device type.