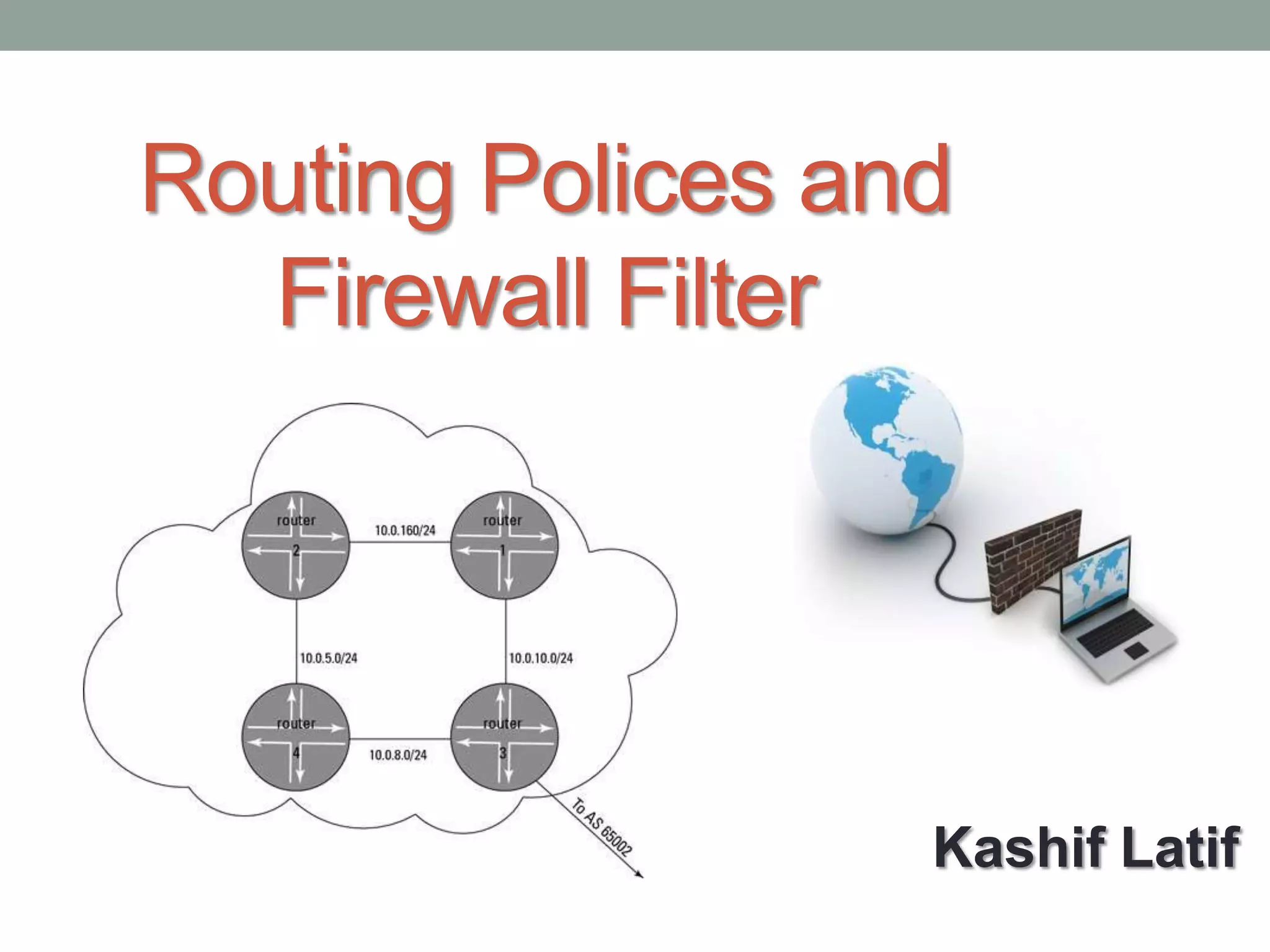
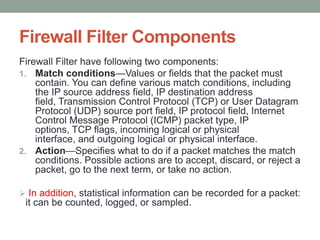
The document discusses routing policies and firewall filters in Junos, explaining that routing policies allow modification of the routing policy framework to control which routes are placed in or advertised from the routing table, while firewall filters can filter packets based on their components and perform actions on matching packets to restrict traffic passing through a routing platform. Key components of routing policies and firewall filters are also outlined such as match conditions, actions, supported standards, and common uses of creating routing policies and firewall filter components.