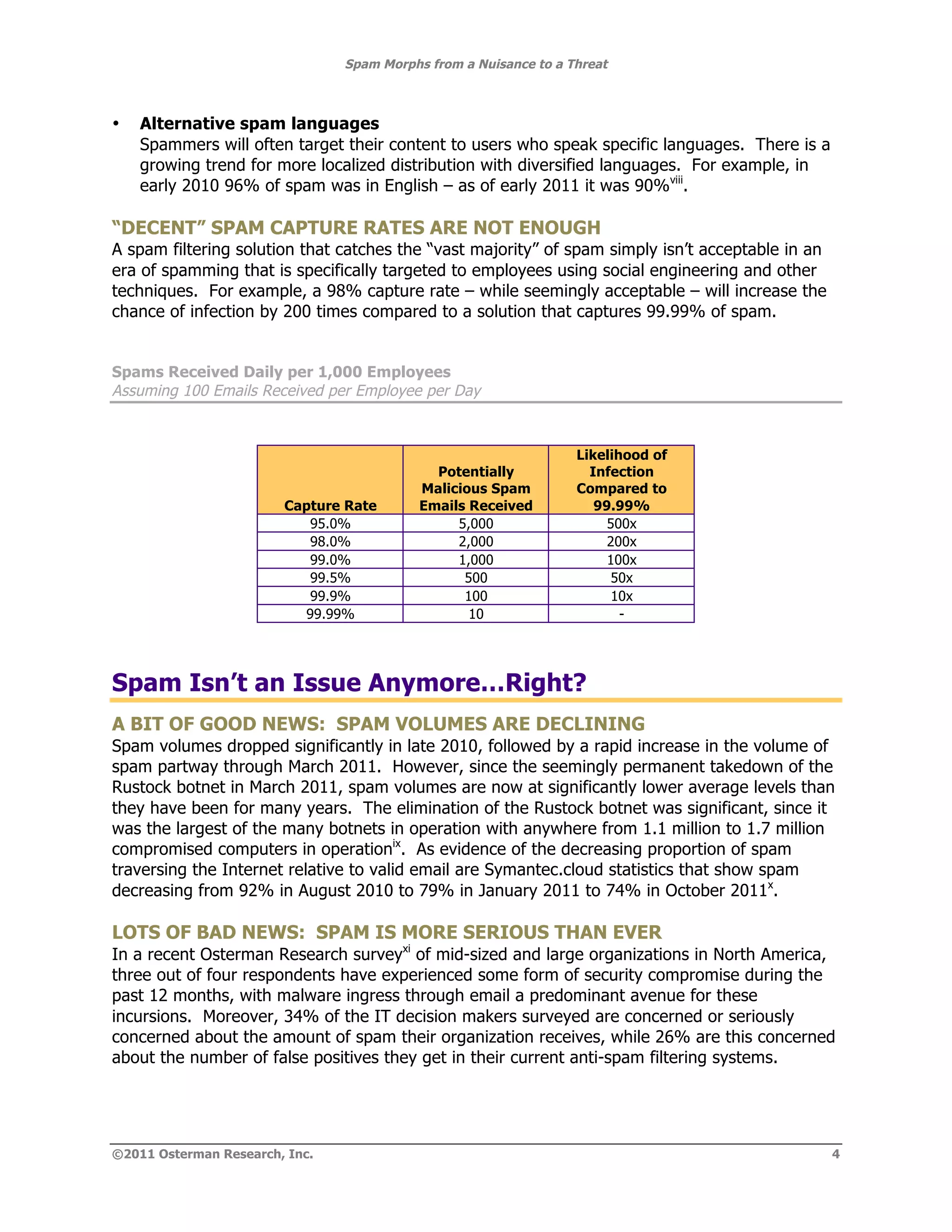
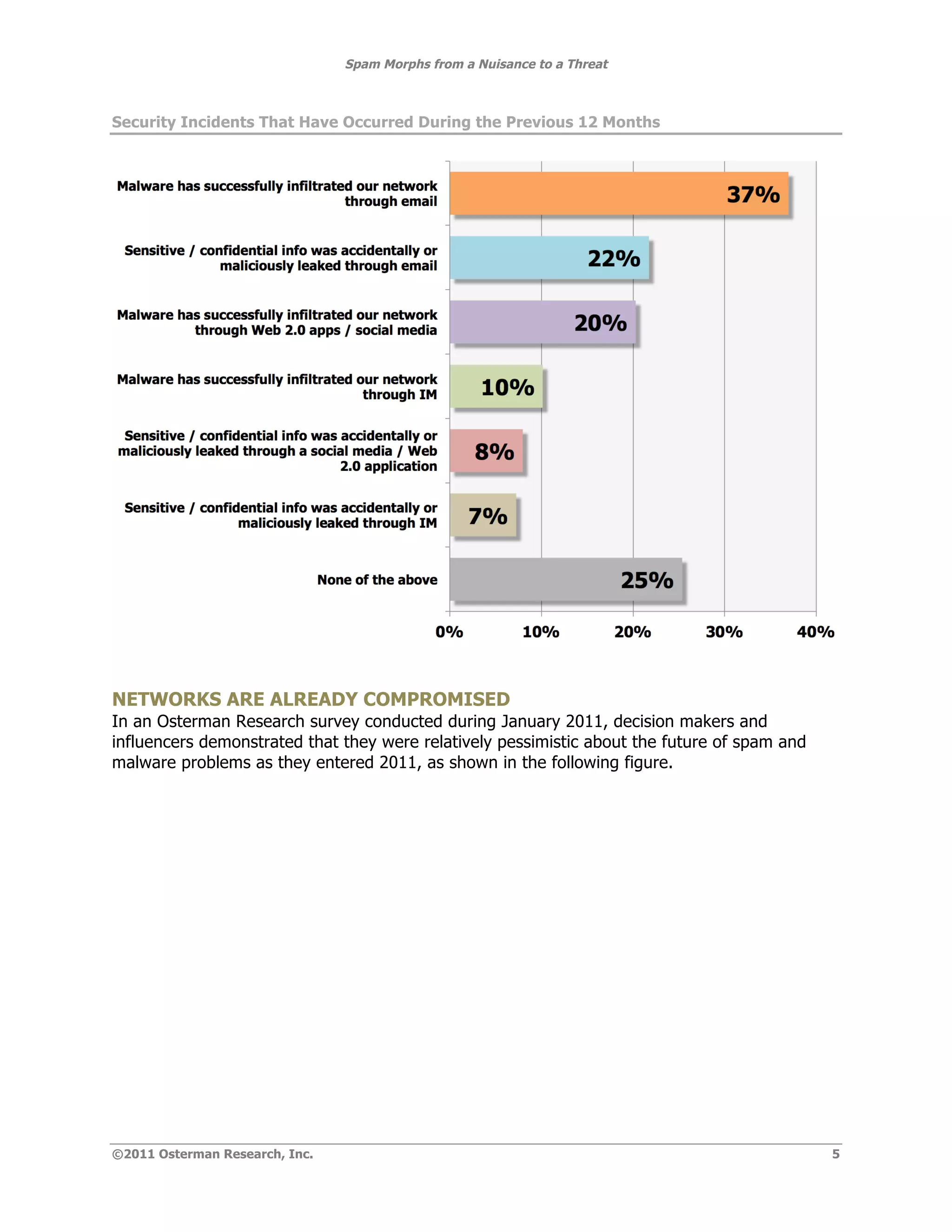
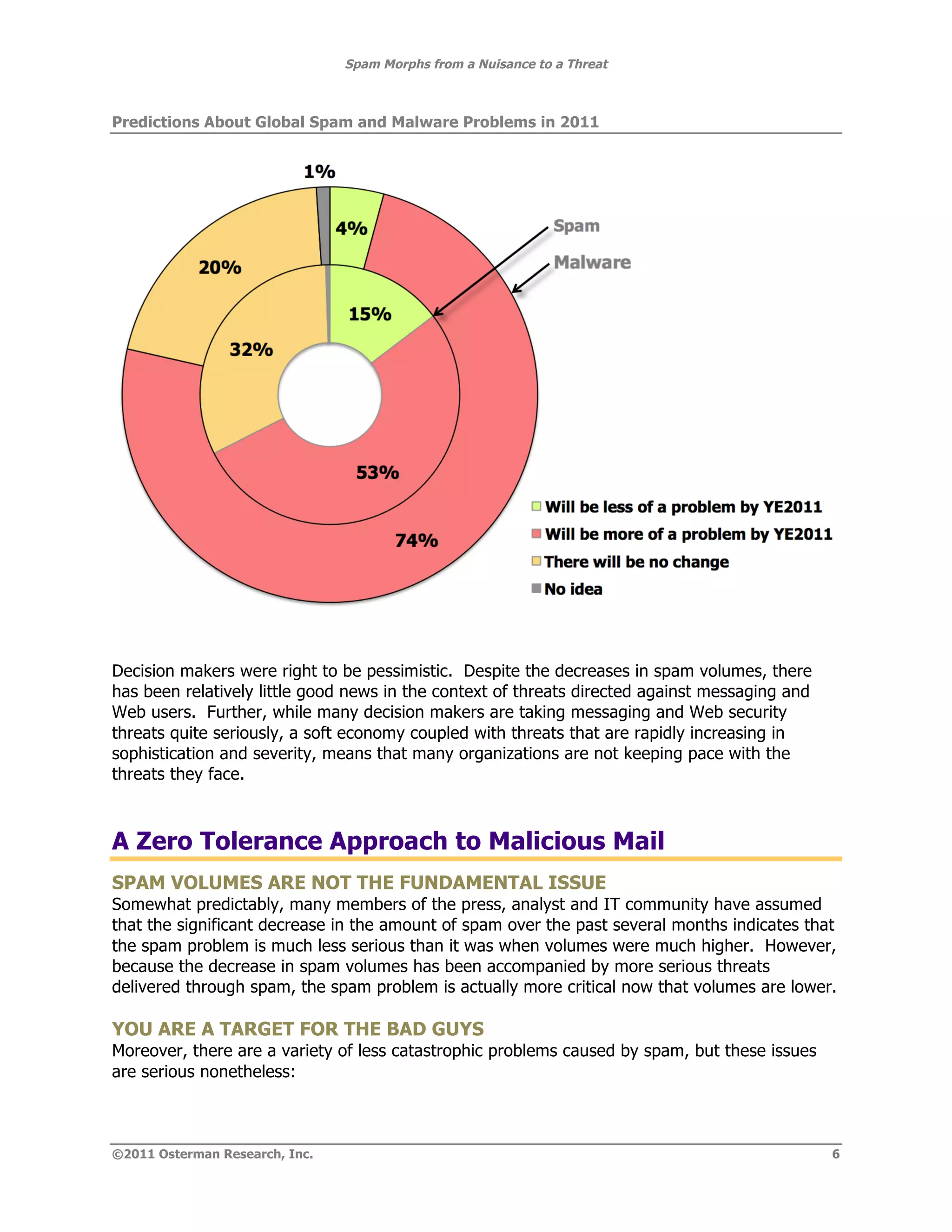
The document summarizes how spam has evolved from a nuisance to a serious threat. While spam volumes are lower than in the past, representing 75% of email rather than 90%, the threat from spam is now greater due to spammers focusing on stealing information rather than selling products, using more sophisticated phishing techniques, and delivering more damaging payloads and links. The key threats are data theft from malware infiltrating corporate networks, hijacking of systems, and launching additional attacks. Decision makers should view spam as a serious threat despite lower volumes.