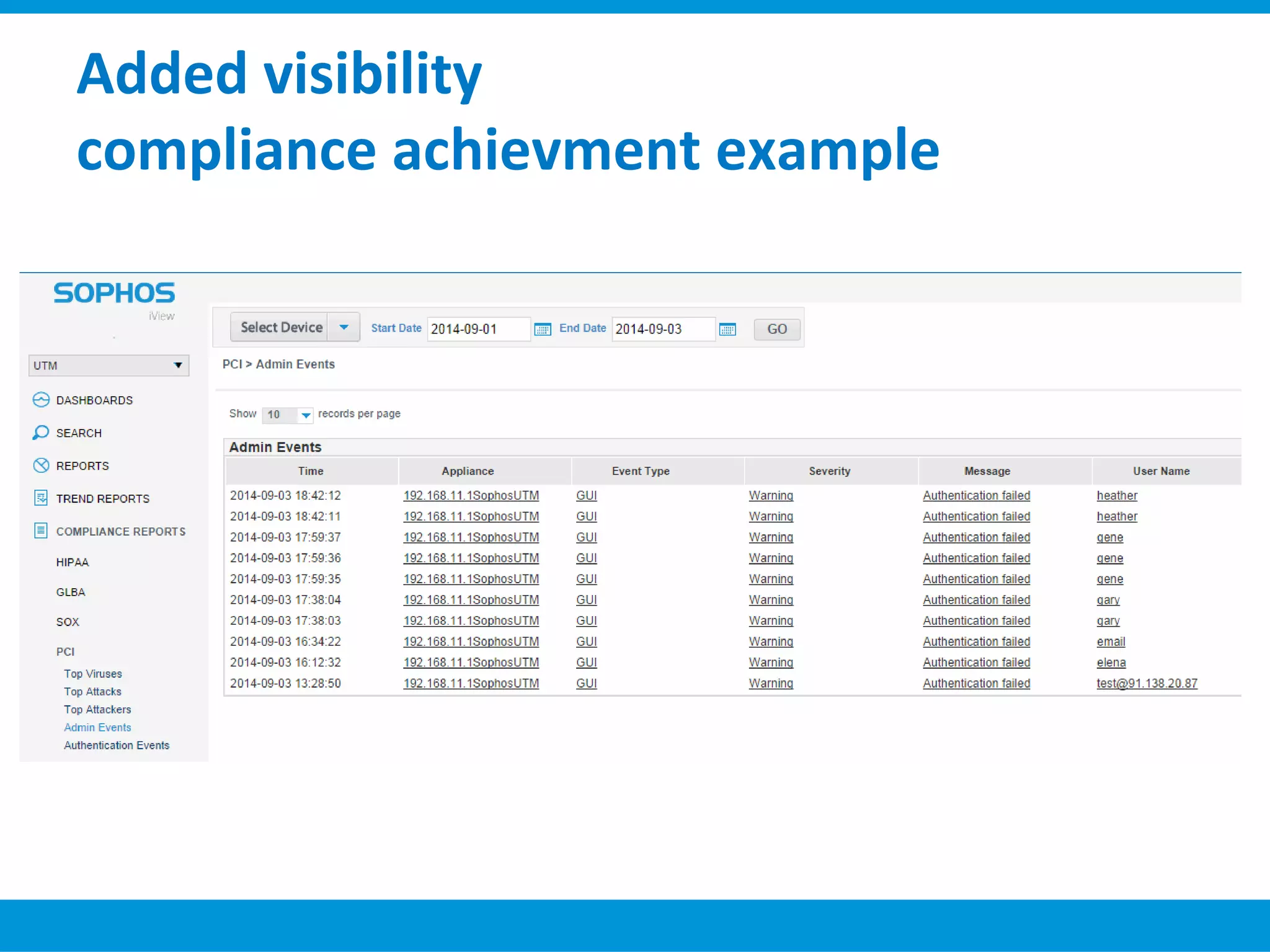
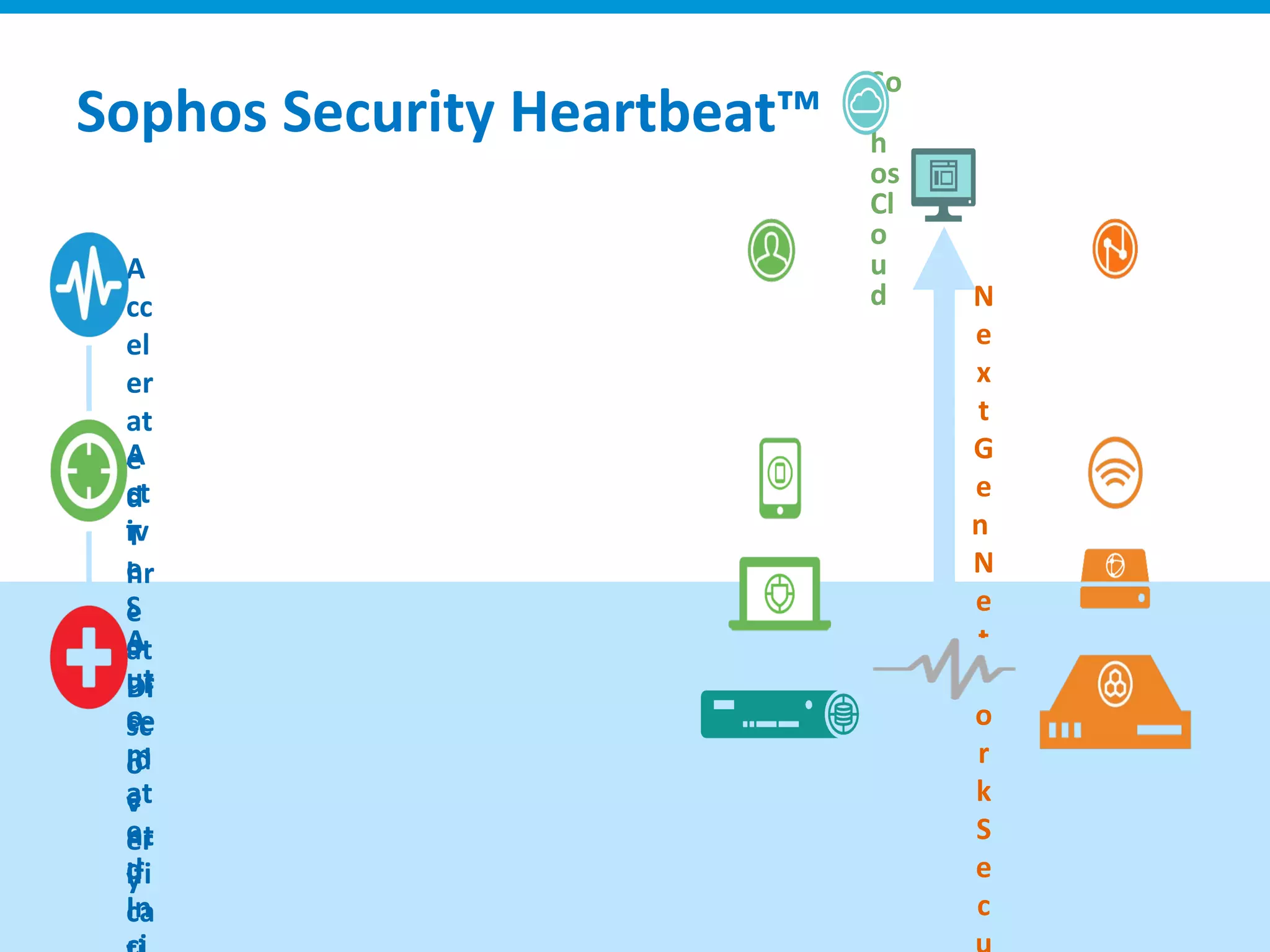
The document discusses Sophos UTM, a unified threat management solution. It summarizes the evolution of firewalls from packet filters to application-level filters. It also discusses how threats like malware, phishing, and SQL injection have changed over time. The document outlines the key features of Sophos UTM, including firewall protection, wireless protection, endpoint protection, network protection, web protection, and email protection. It positions Sophos UTM as providing complete security for organizations through an integrated solution.