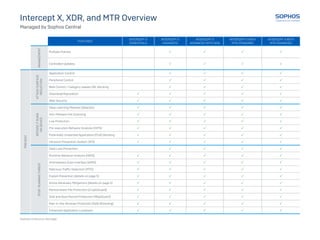
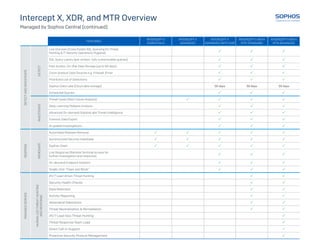
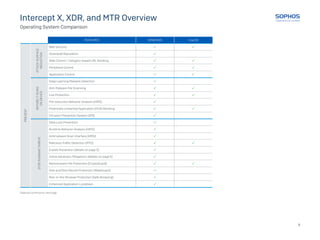
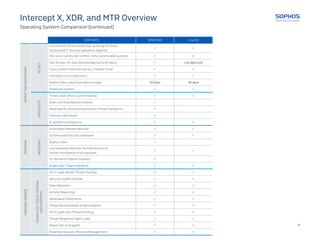
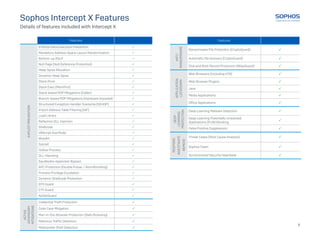
This document provides an overview and comparison of Sophos' Intercept X, XDR, and MTR cybersecurity products. It outlines the key features included in each product related to preventing attacks, detecting threats before and as they run on devices, investigating incidents, and responding to threats. It also summarizes the additional capabilities provided by Sophos' Managed Threat Response services, such as 24/7 threat hunting, security health checks, and direct support from a threat response team.