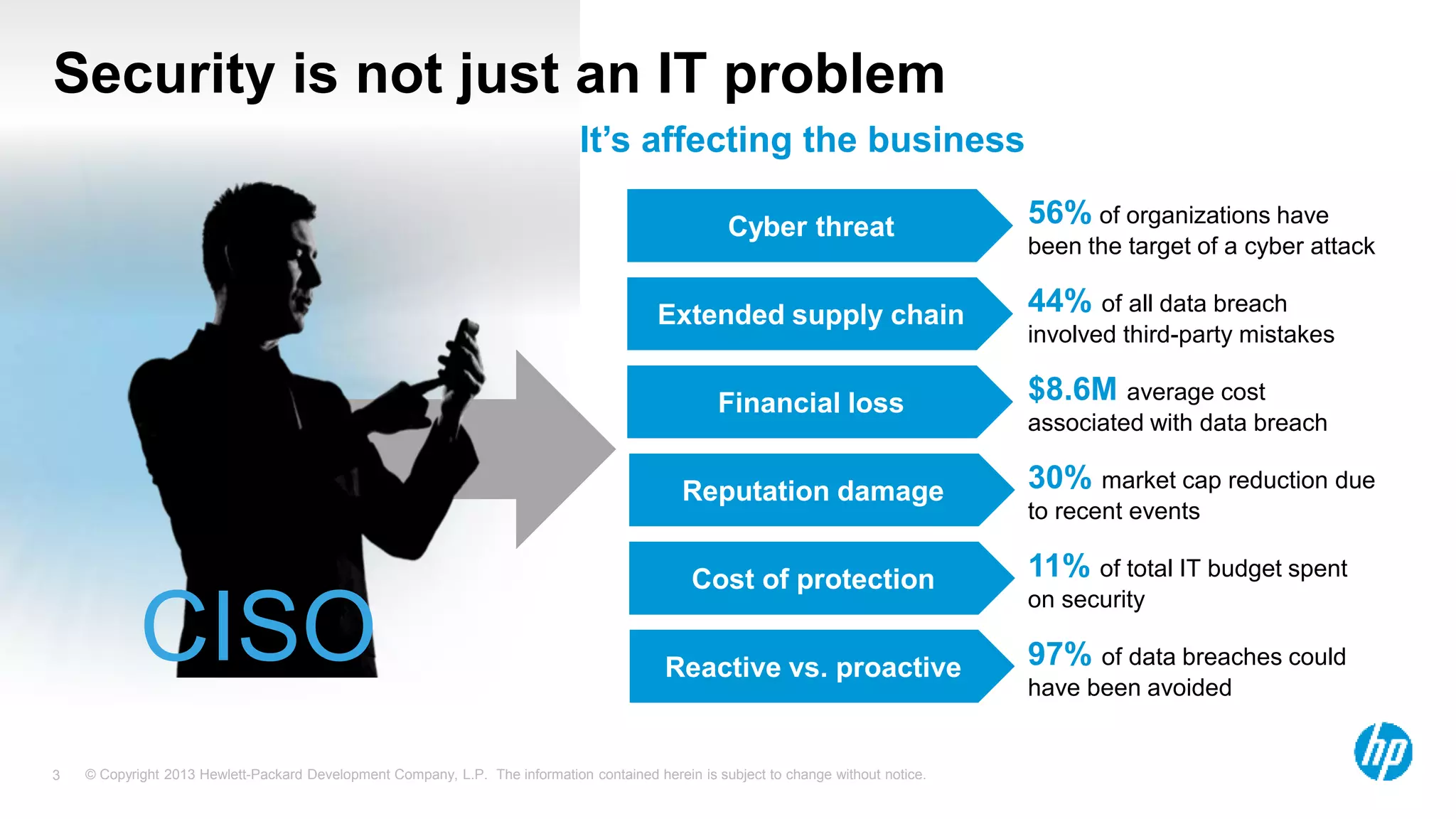
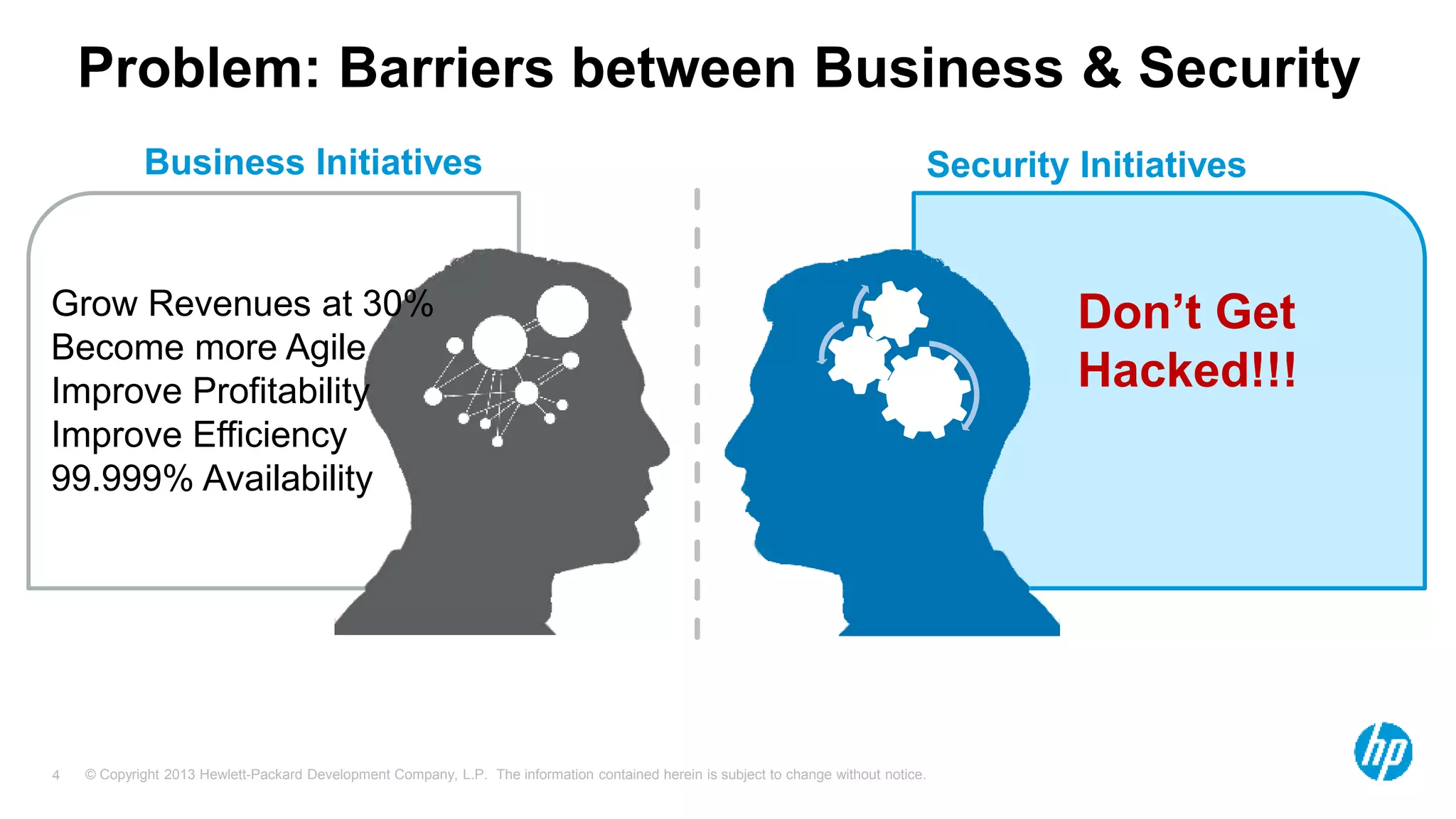
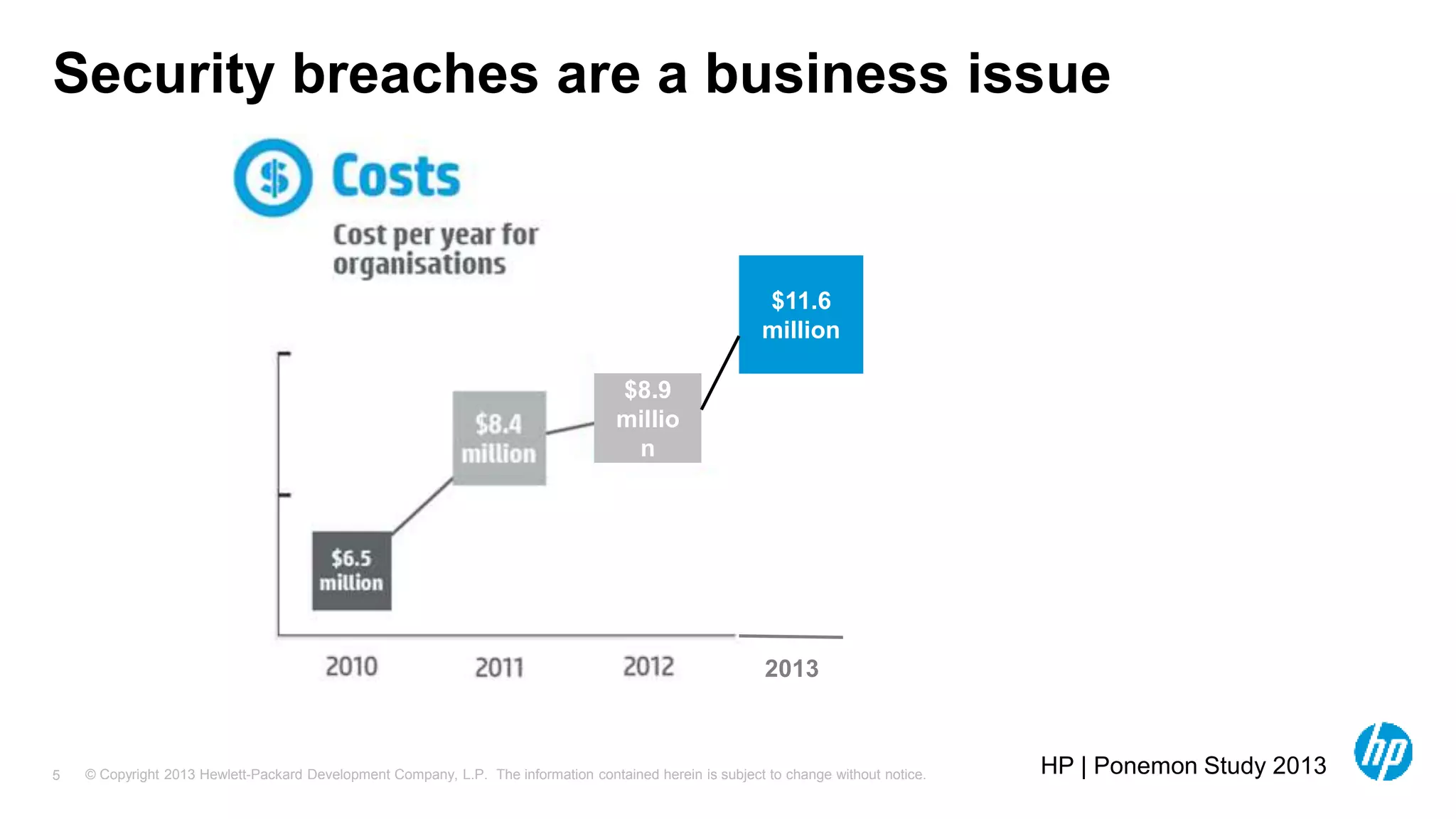
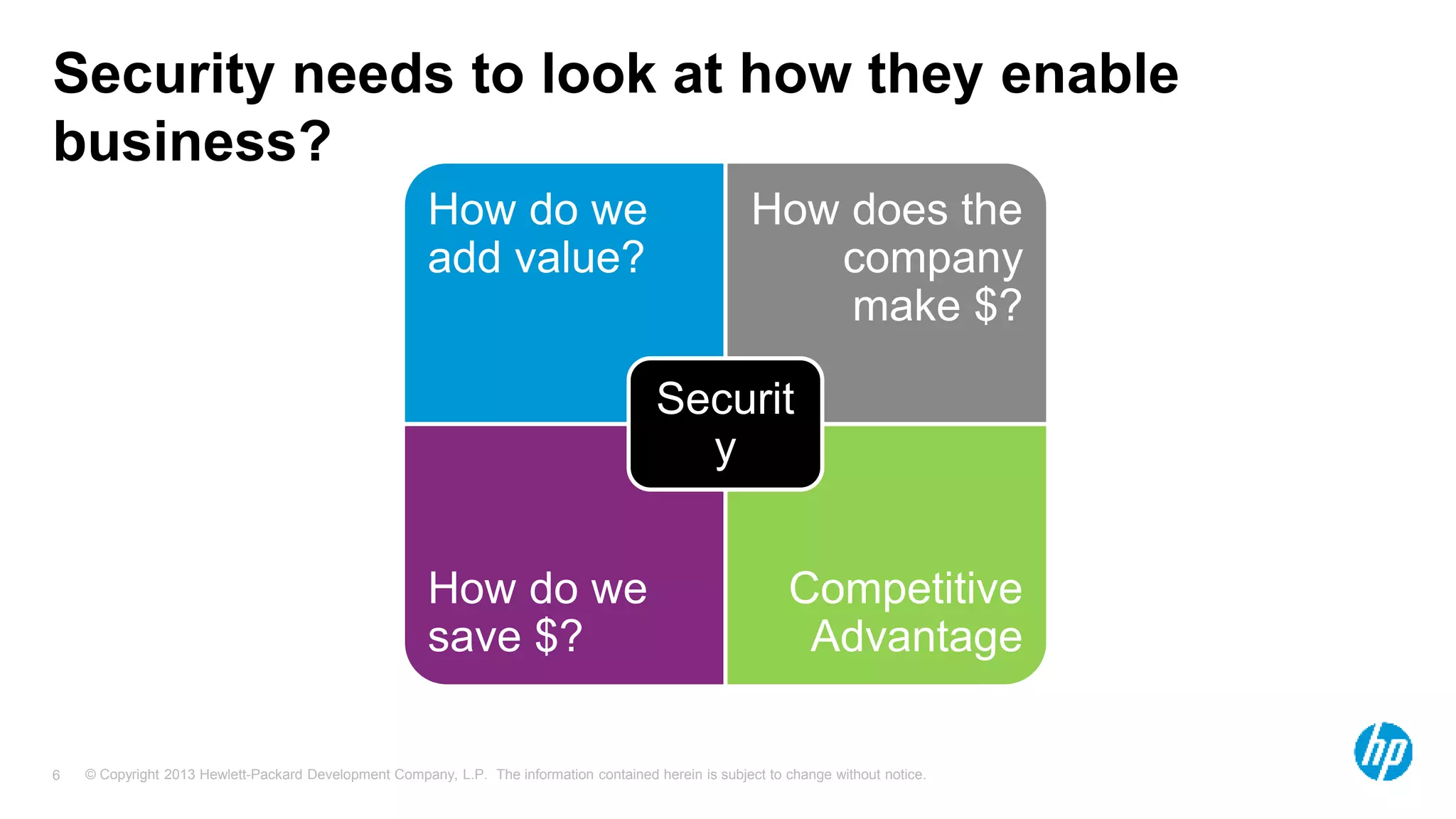
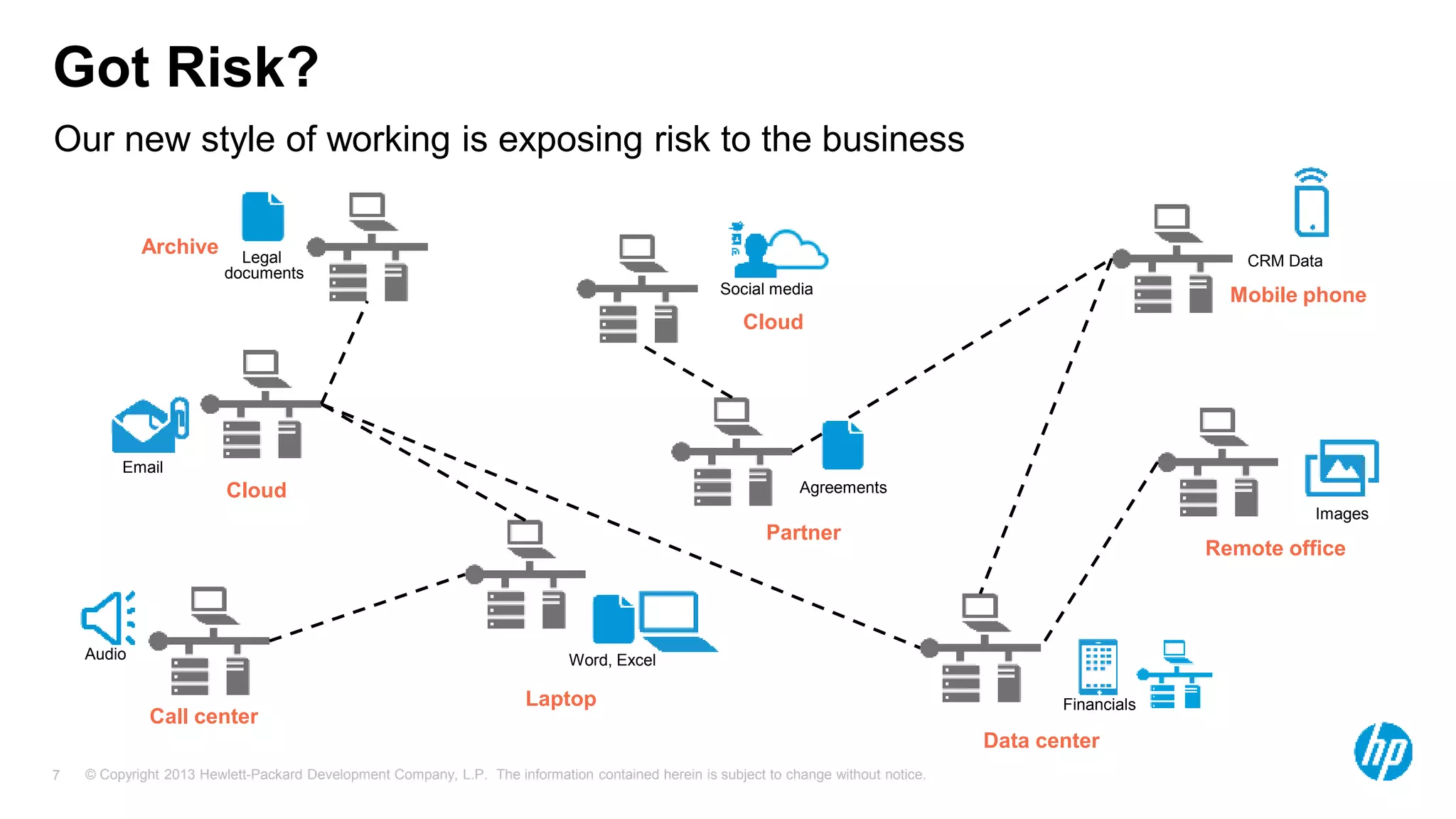
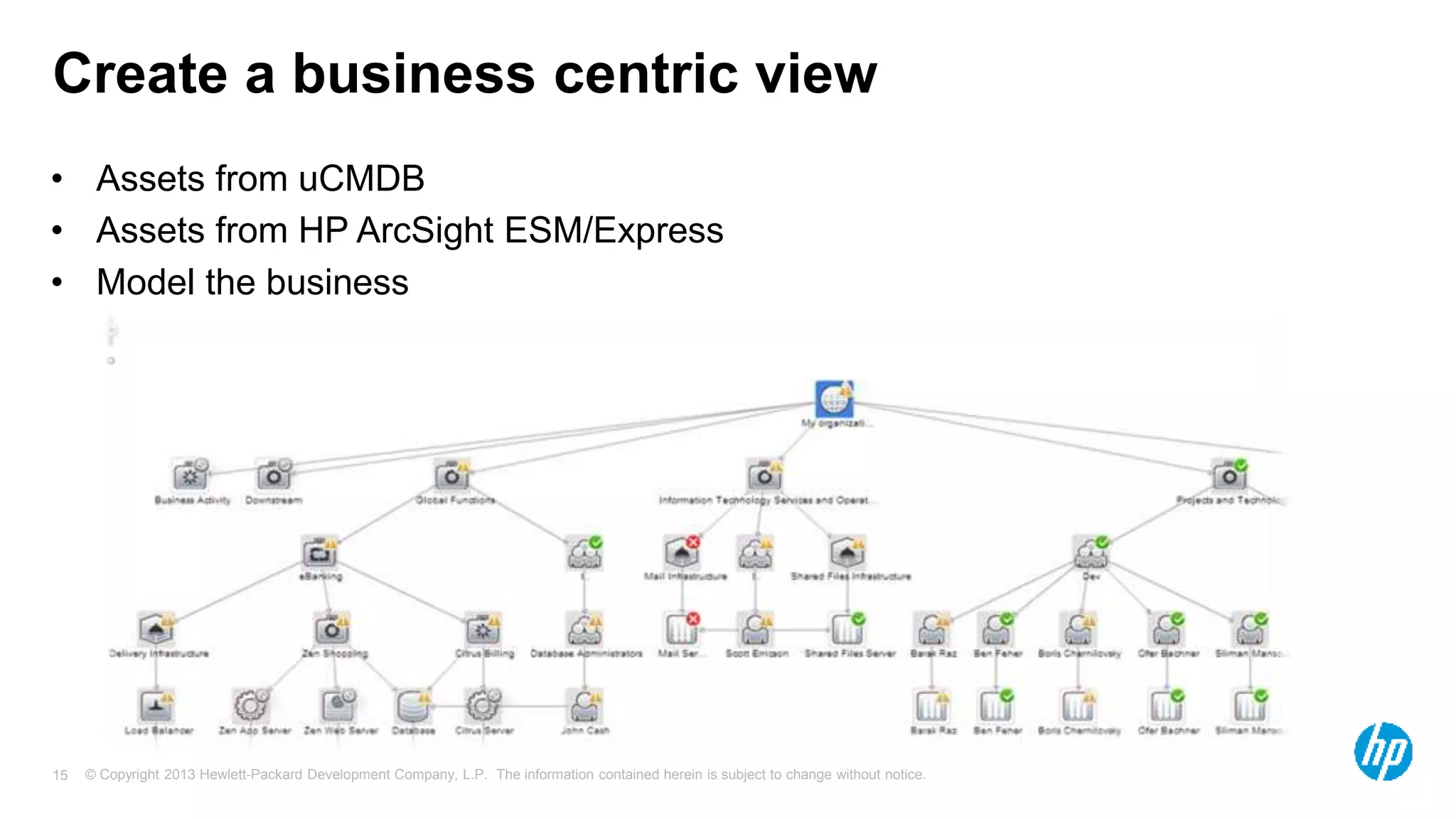
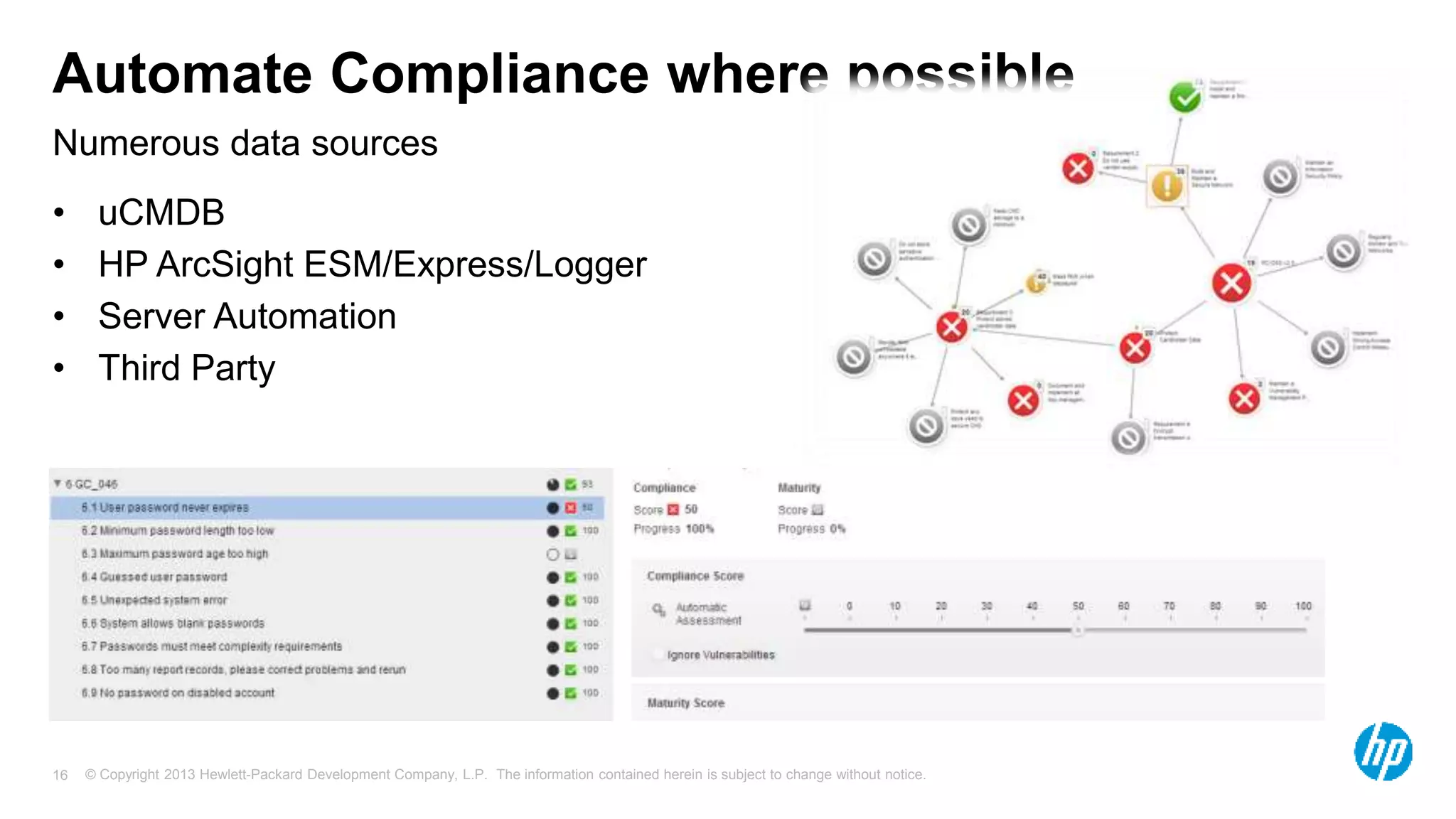
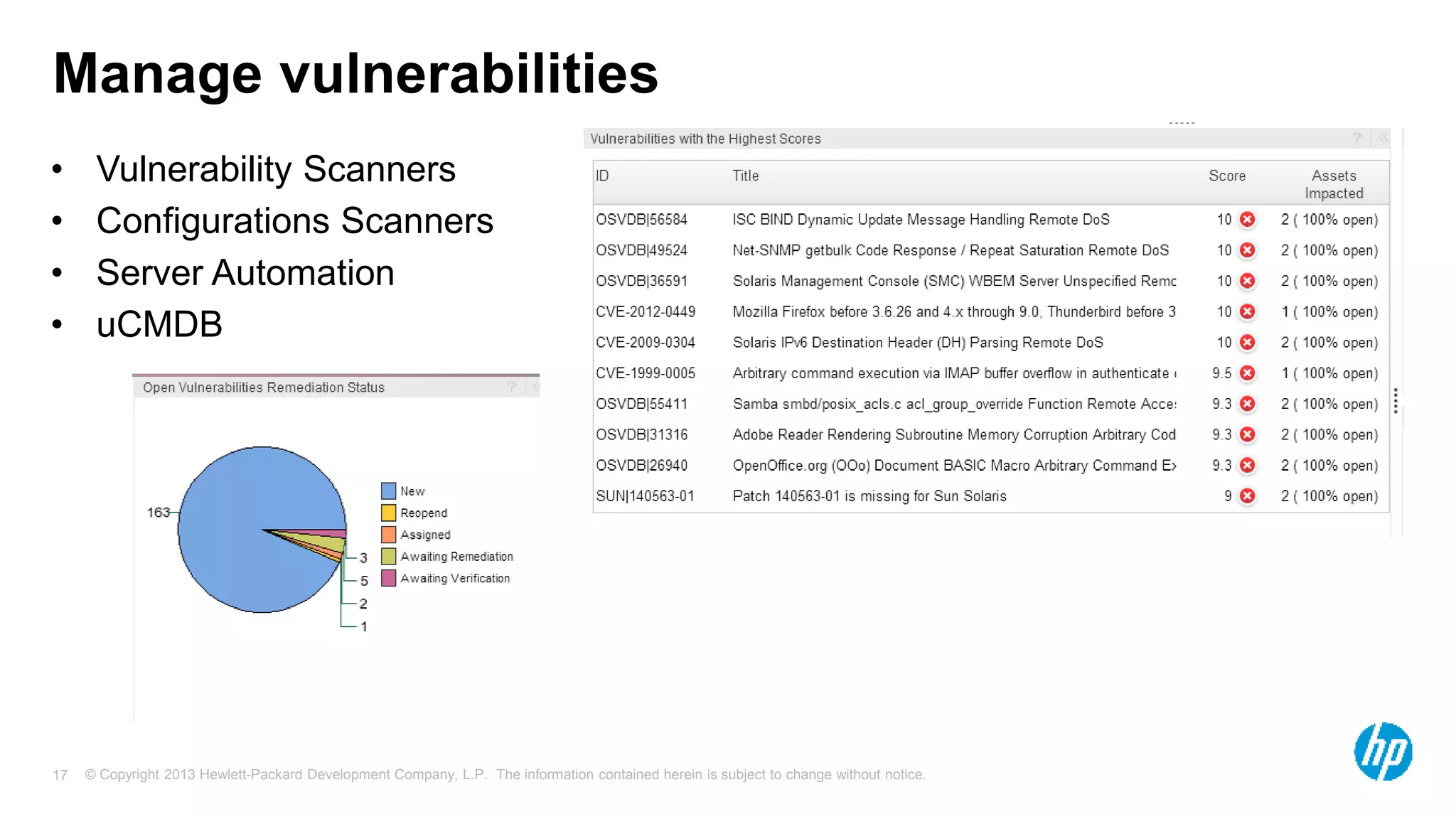
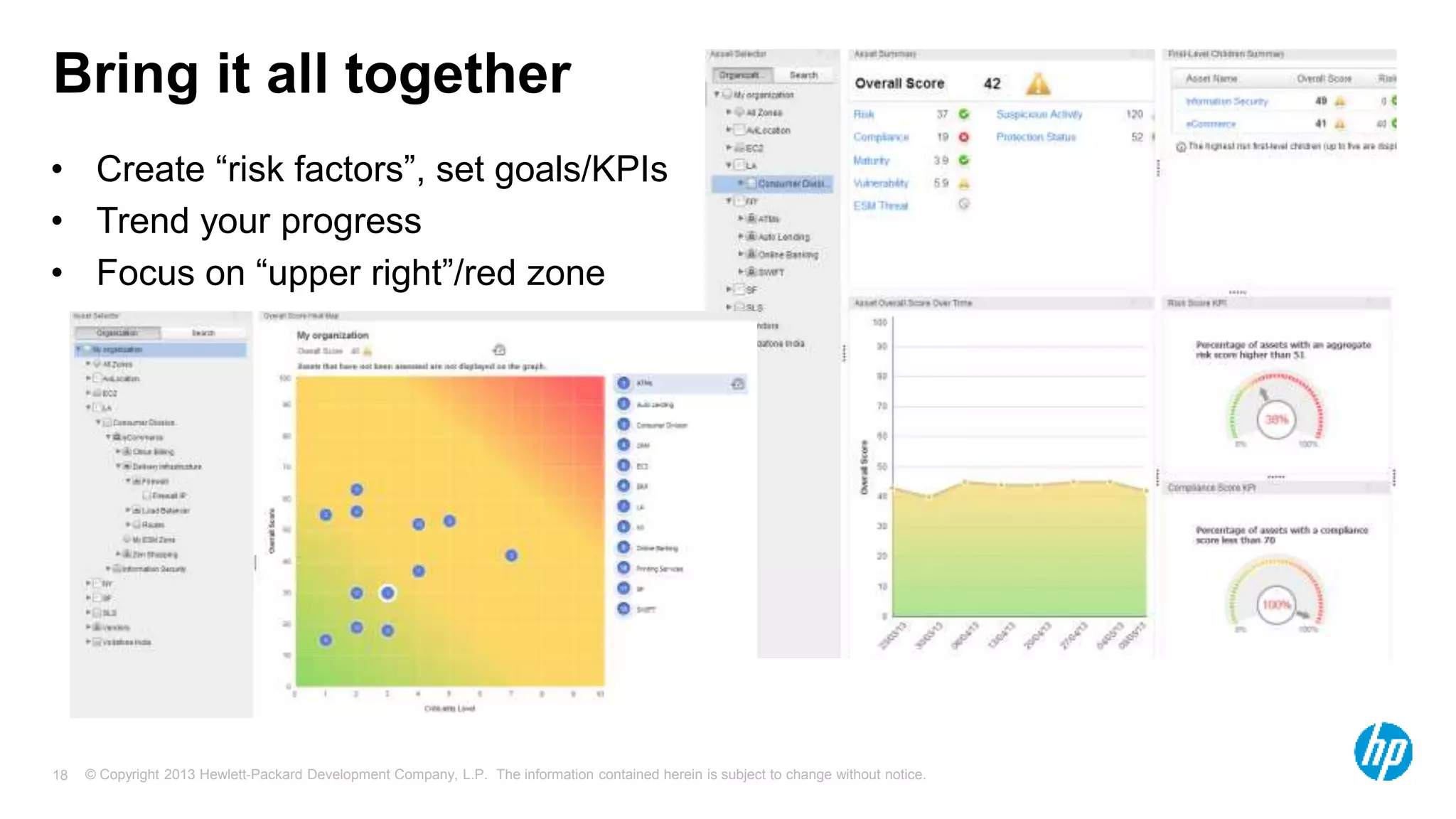
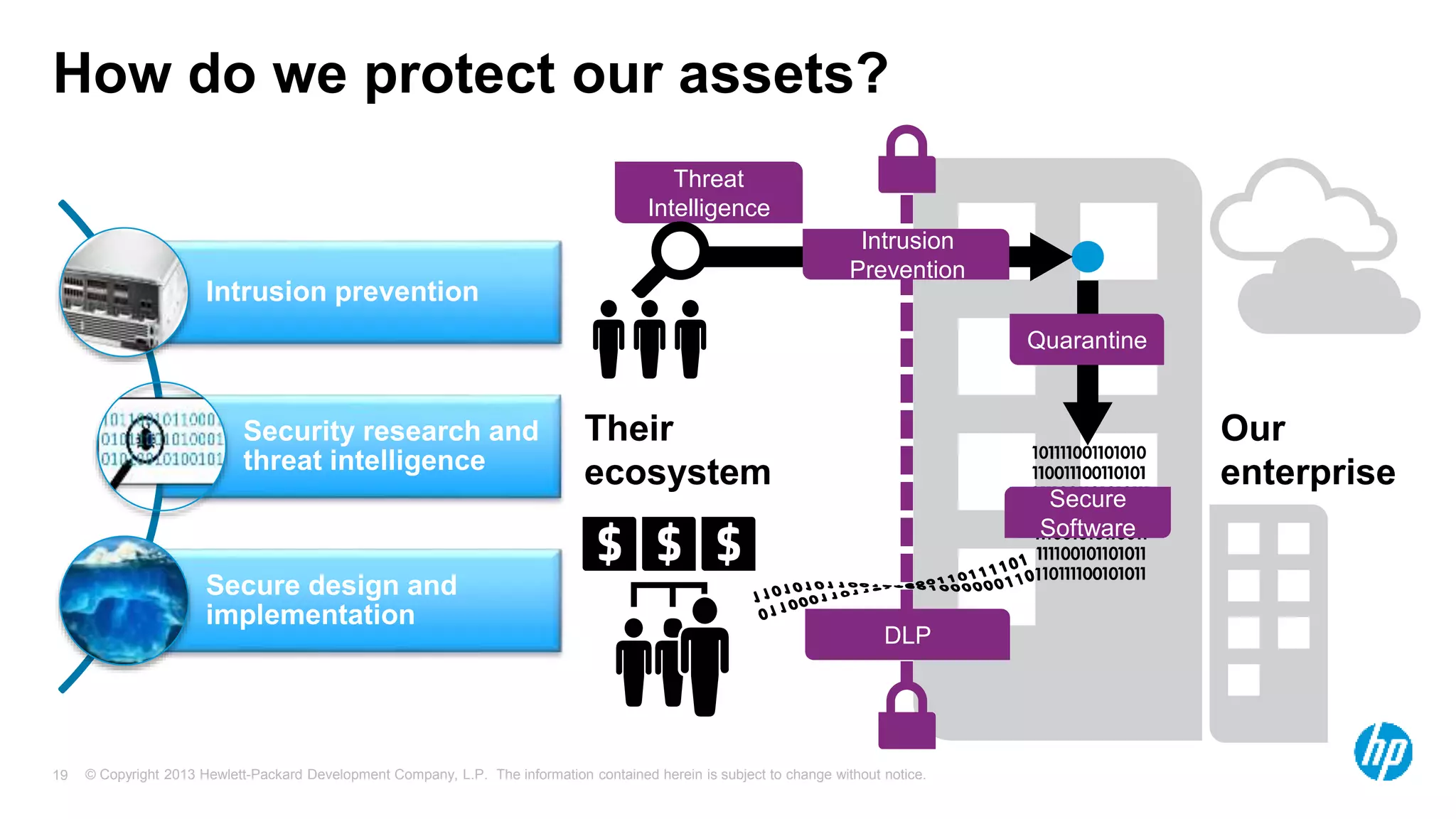
The document discusses the importance of integrating security initiatives with business objectives, emphasizing that cybersecurity is a crucial business issue rather than just an IT concern. It highlights the significant costs associated with data breaches and outlines strategies for aligning security efforts with organizational goals, including effective communication of risk in business terms. The document also provides actionable tips for improving security posture through small, incremental improvements and leveraging existing data.