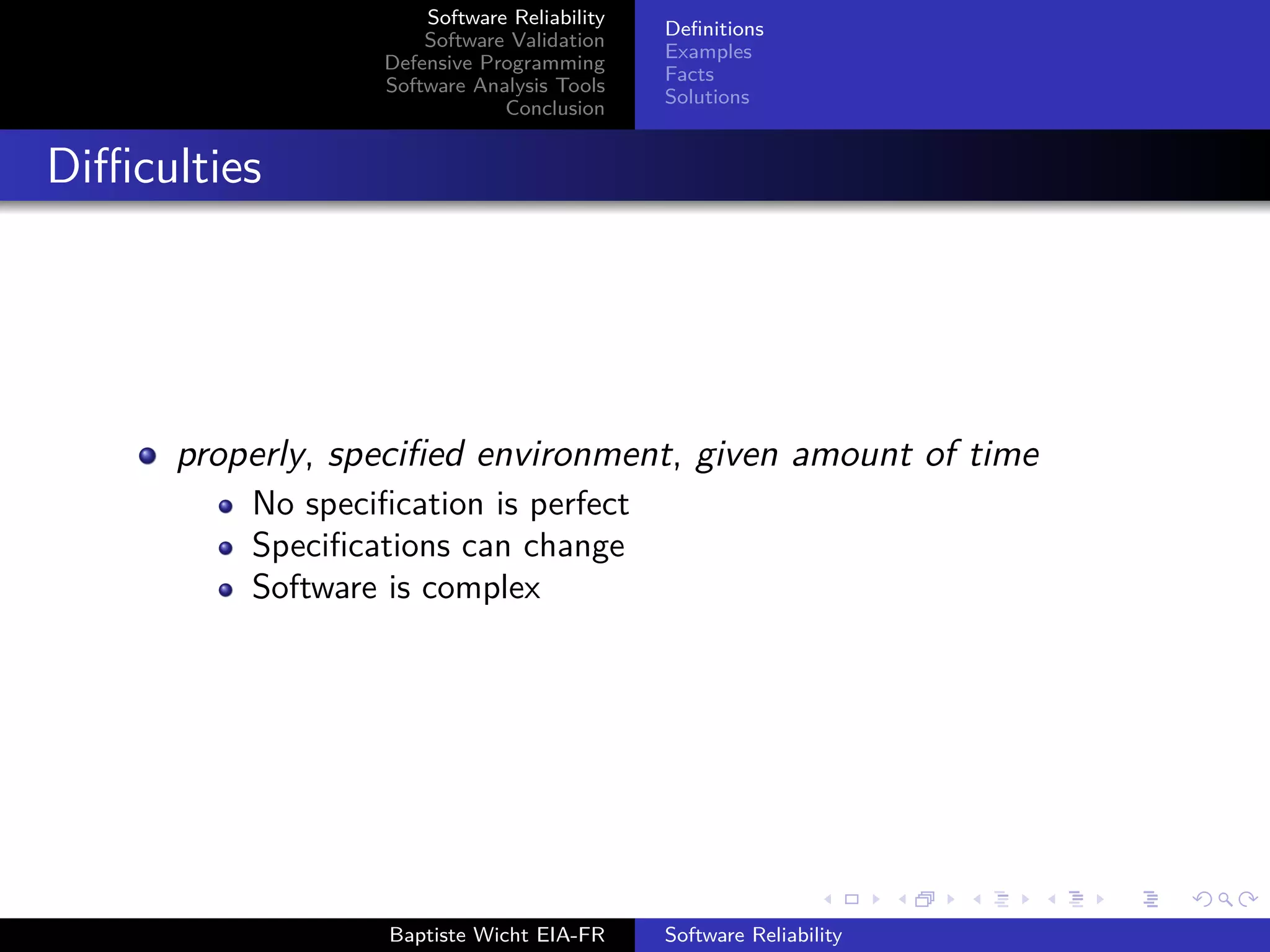
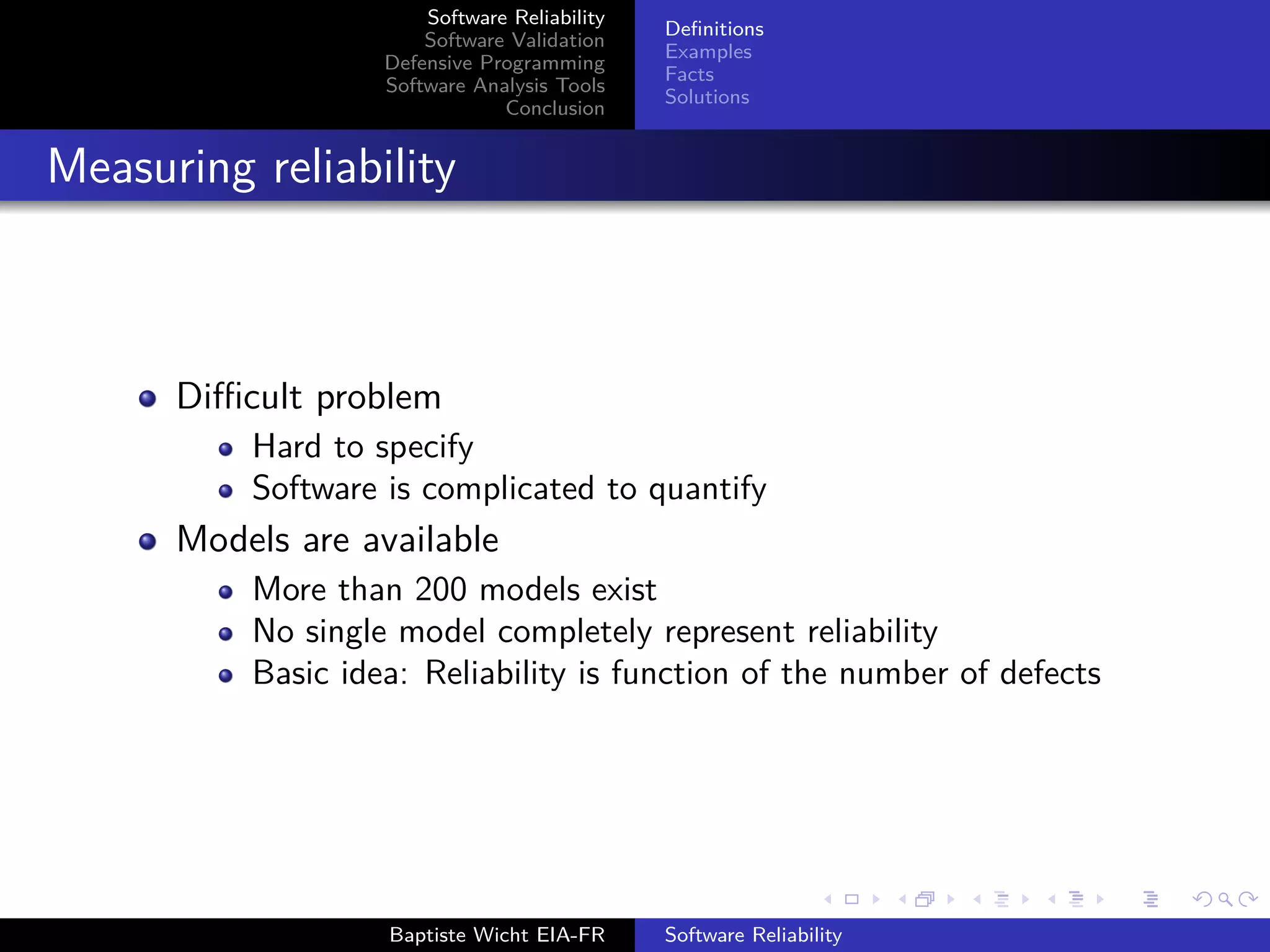
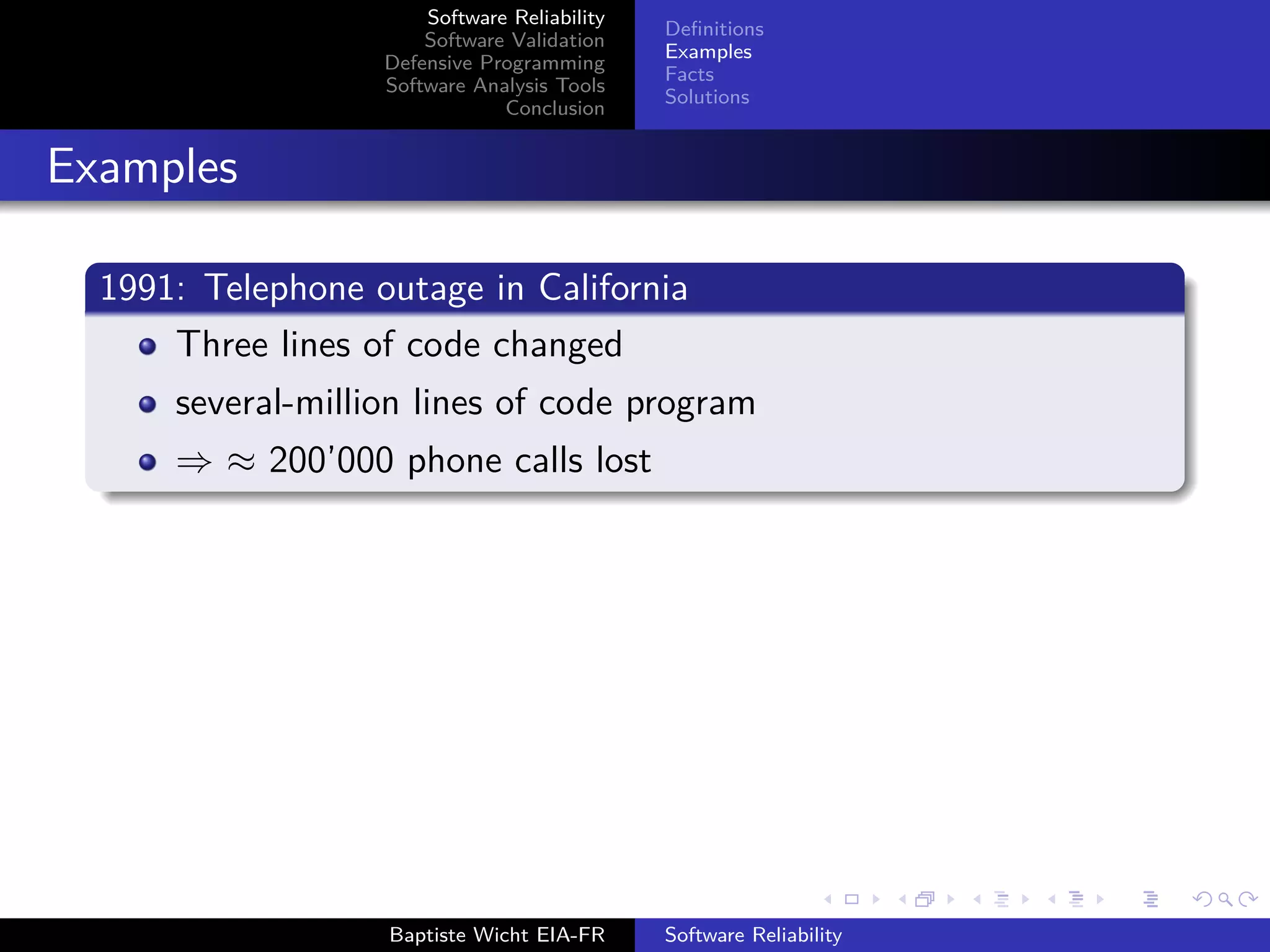
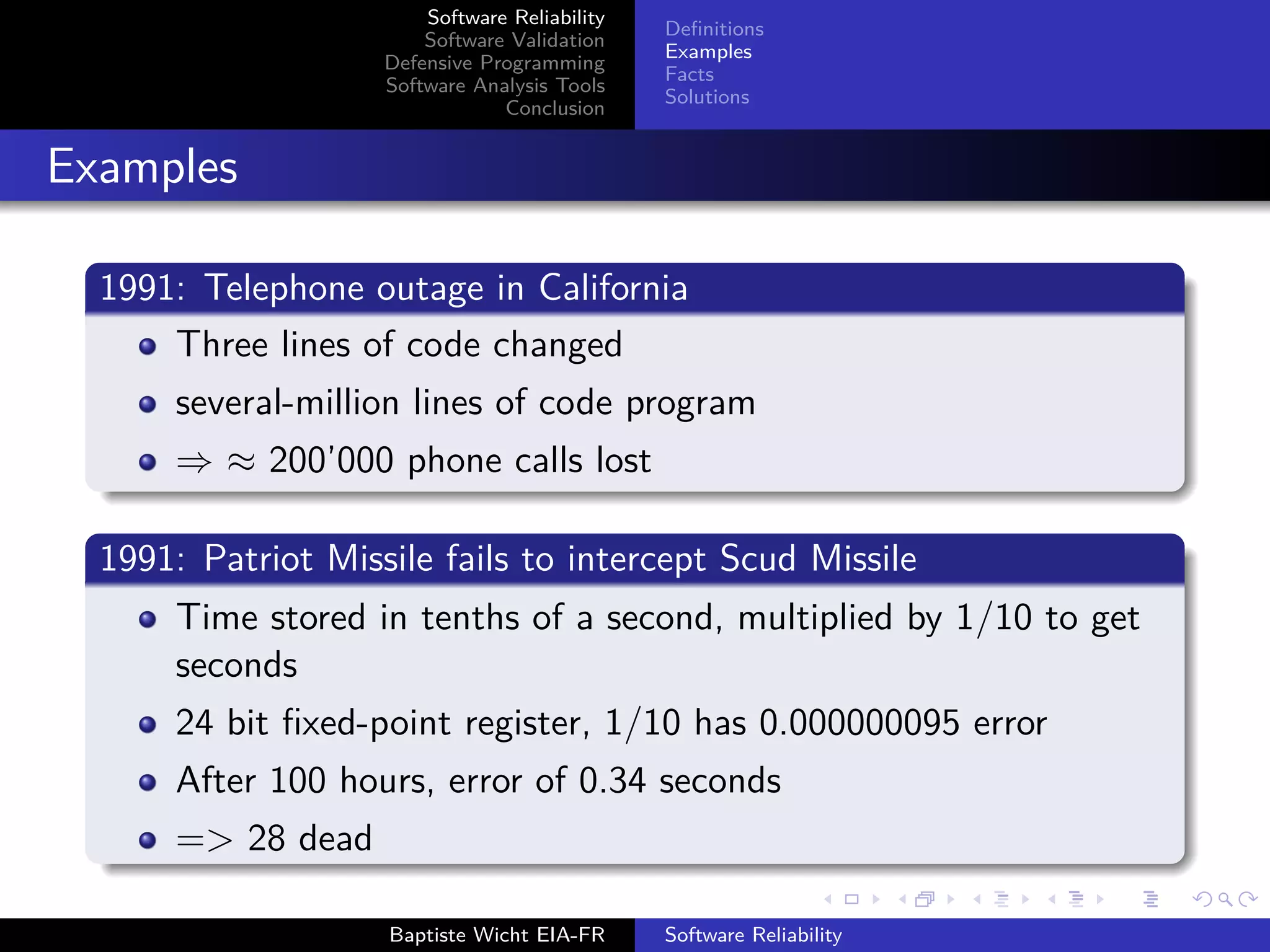
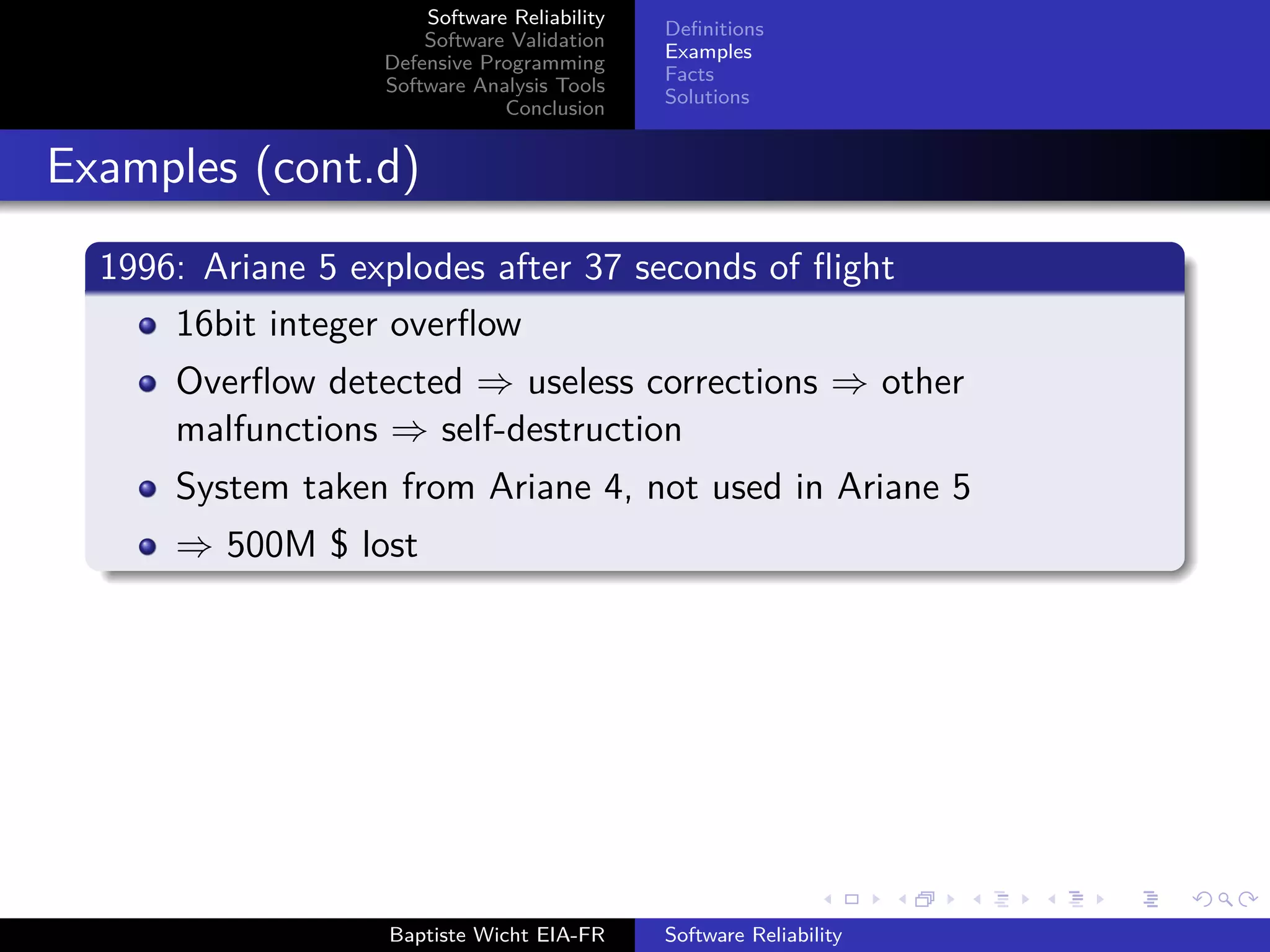
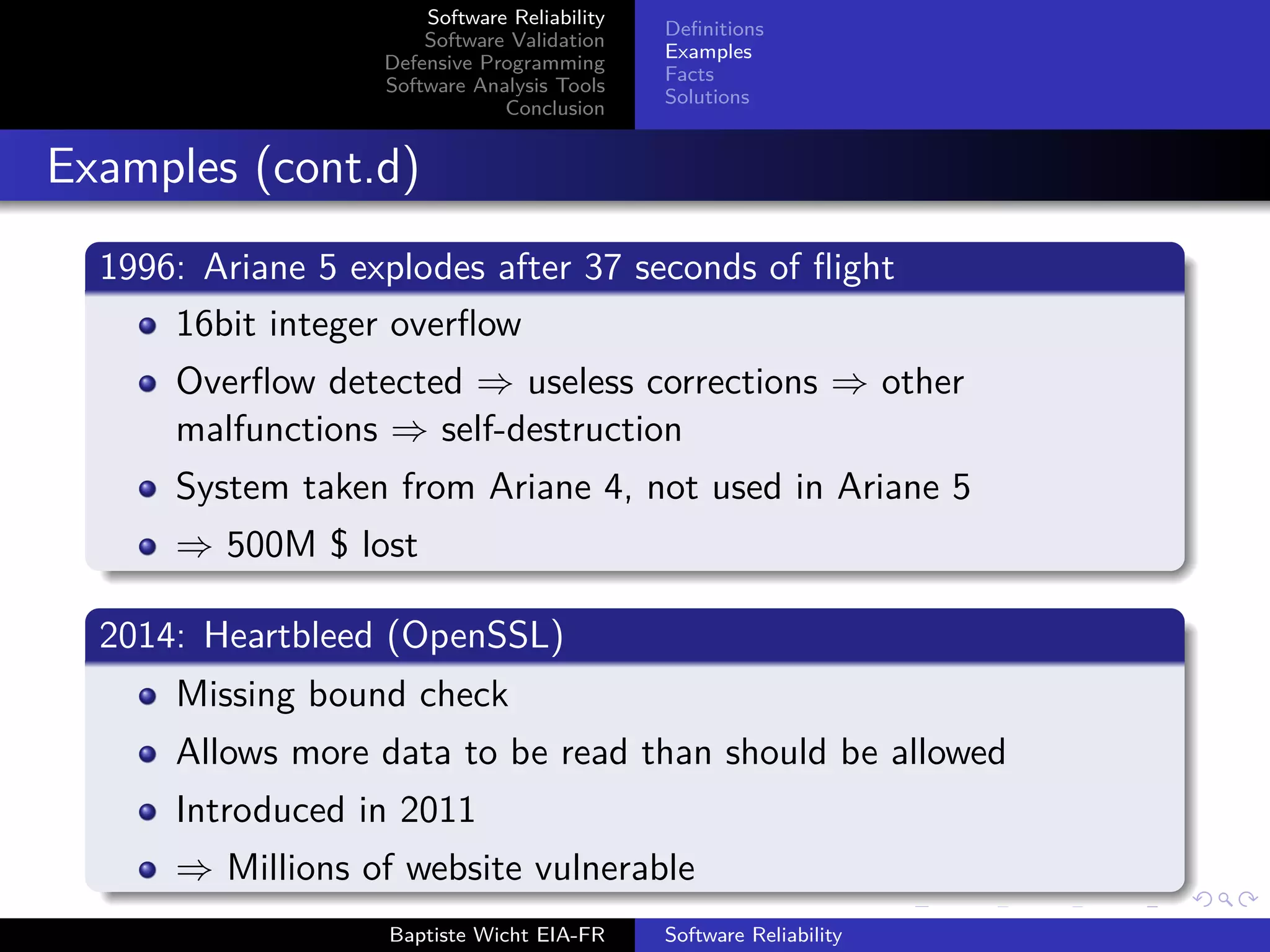
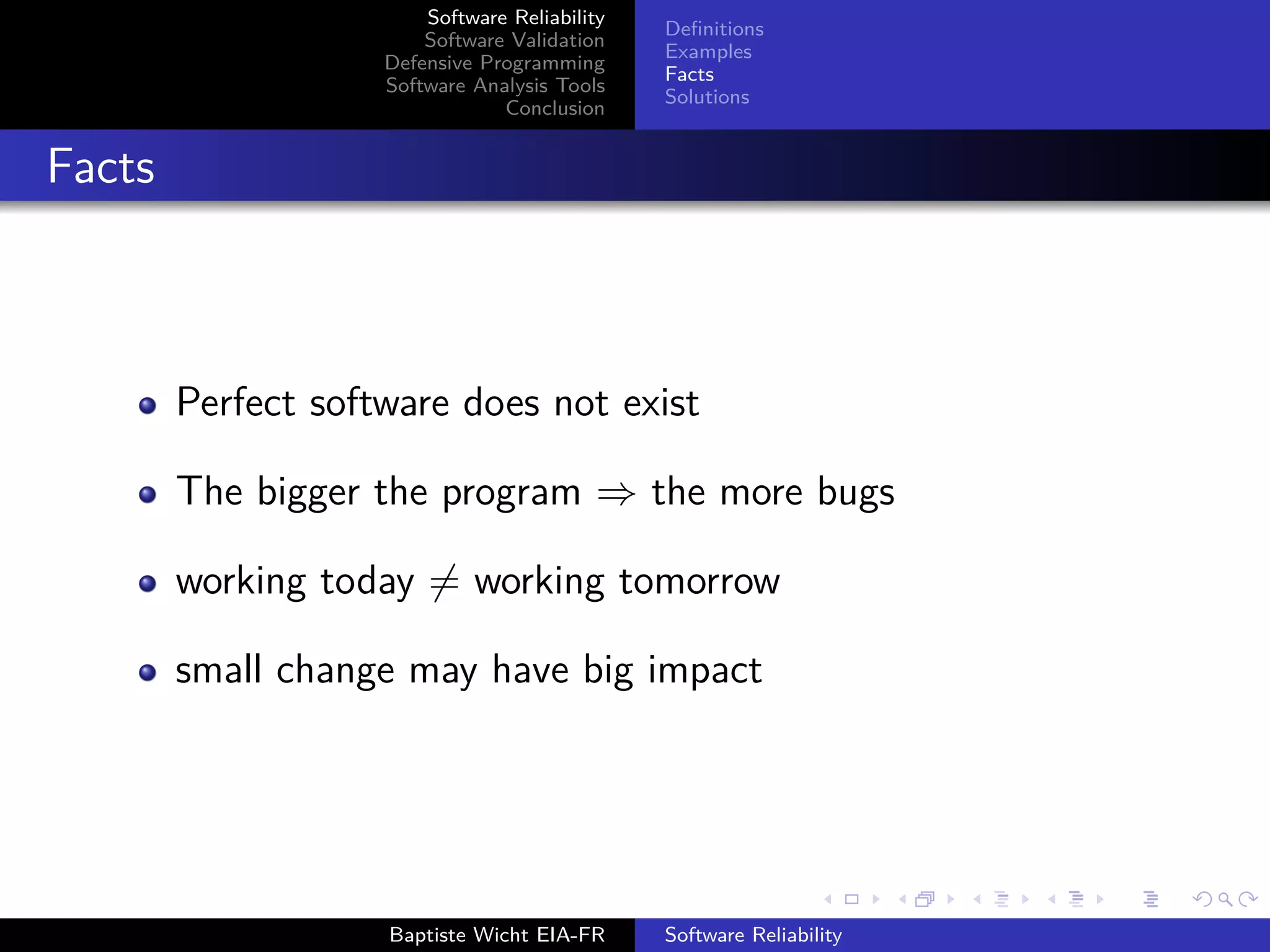
The document discusses software reliability, validation, defensive programming, and analysis tools, emphasizing the challenges in ensuring software operates correctly under specified conditions. It highlights various incidents where reliability failures occurred and presents solutions through testing and error-checking methodologies. The conclusion stresses the necessity of comprehensive unit and integration testing, as well as the use of analysis tools to improve software reliability.


![Software Reliability
Software Validation
Defensive Programming
Software Analysis Tools
Conclusion
Language Features
Contract Programming
Conclusion
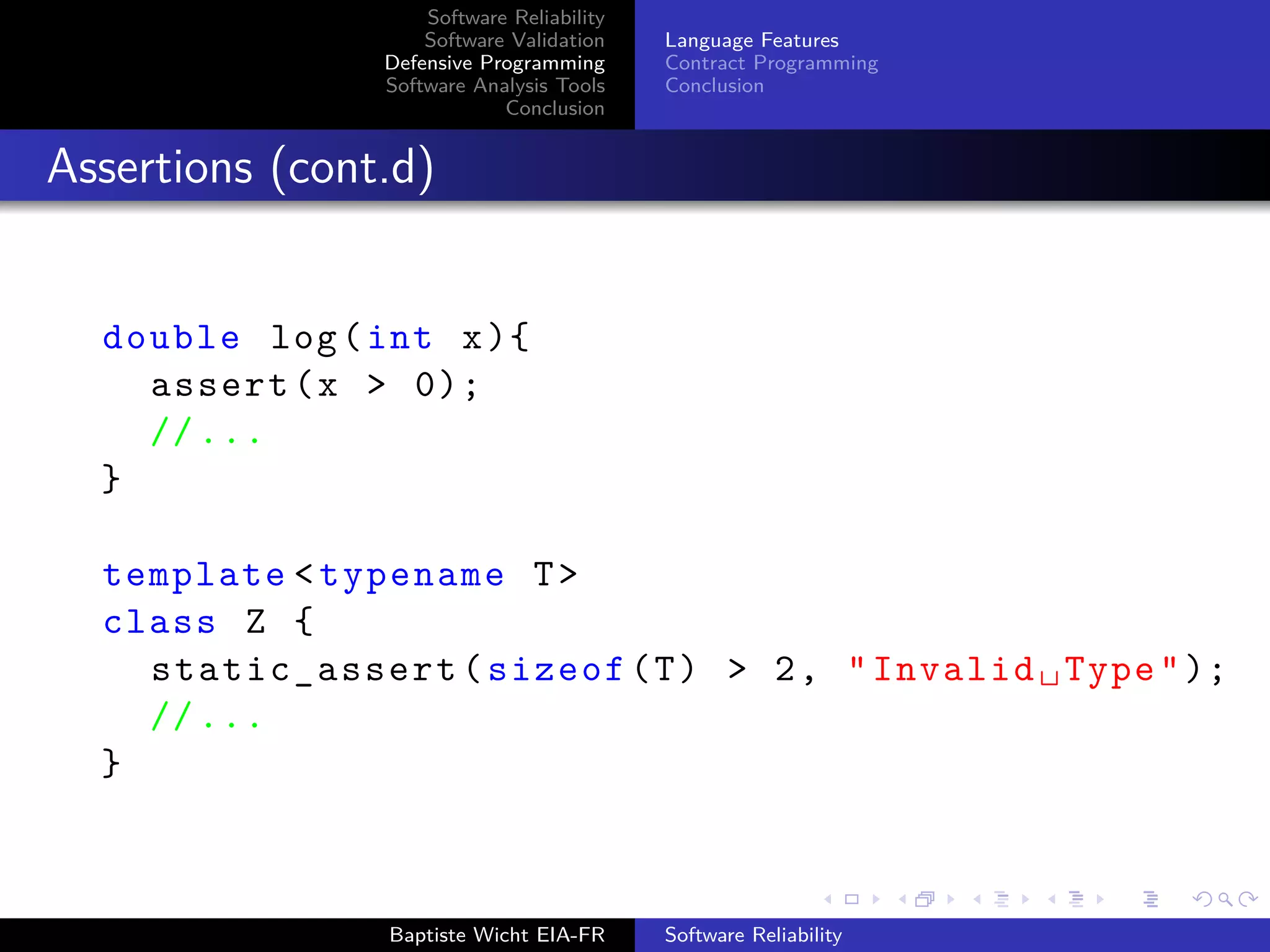
Language Features
Different languages provide different level of security
int array [100];
int b = array [100]; // What should happen ?
Baptiste Wicht EIA-FR Software Reliability](https://image.slidesharecdn.com/softwarereliability-140606124250-phpapp01/75/Software-reliability-21-2048.jpg)
![Software Reliability
Software Validation
Defensive Programming
Software Analysis Tools
Conclusion
Language Features
Contract Programming
Conclusion
Language Features
Different languages provide different level of security
int array [100];
int b = array [100]; // What should happen ?
C/C++: Undefined
Java/Python: Runtime error
Generally: lower level ⇒ harder to debug
Baptiste Wicht EIA-FR Software Reliability](https://image.slidesharecdn.com/softwarereliability-140606124250-phpapp01/75/Software-reliability-22-2048.jpg)



![Software Reliability
Software Validation
Defensive Programming
Software Analysis Tools
Conclusion
Compilers
Tools
Exercises
SonarQube
Conclusion
Heap Overrun
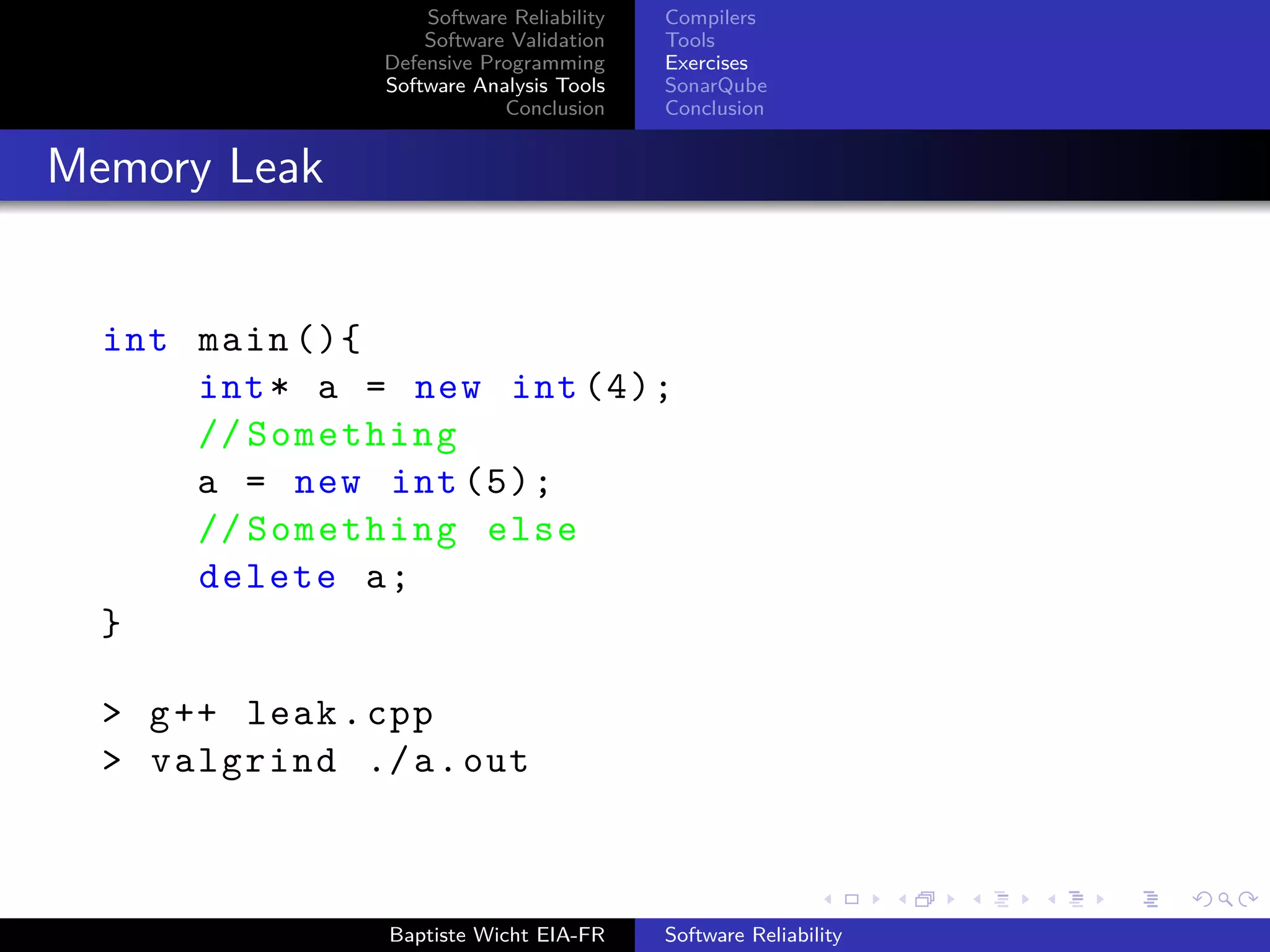
int main (){
int* heap = new int [5];
heap [5] = 42;
delete [] heap;
return 0;
}
> g++ -g heap_overrun.cpp
> valgrind ./a.out
Baptiste Wicht EIA-FR Software Reliability](https://image.slidesharecdn.com/softwarereliability-140606124250-phpapp01/75/Software-reliability-41-2048.jpg)
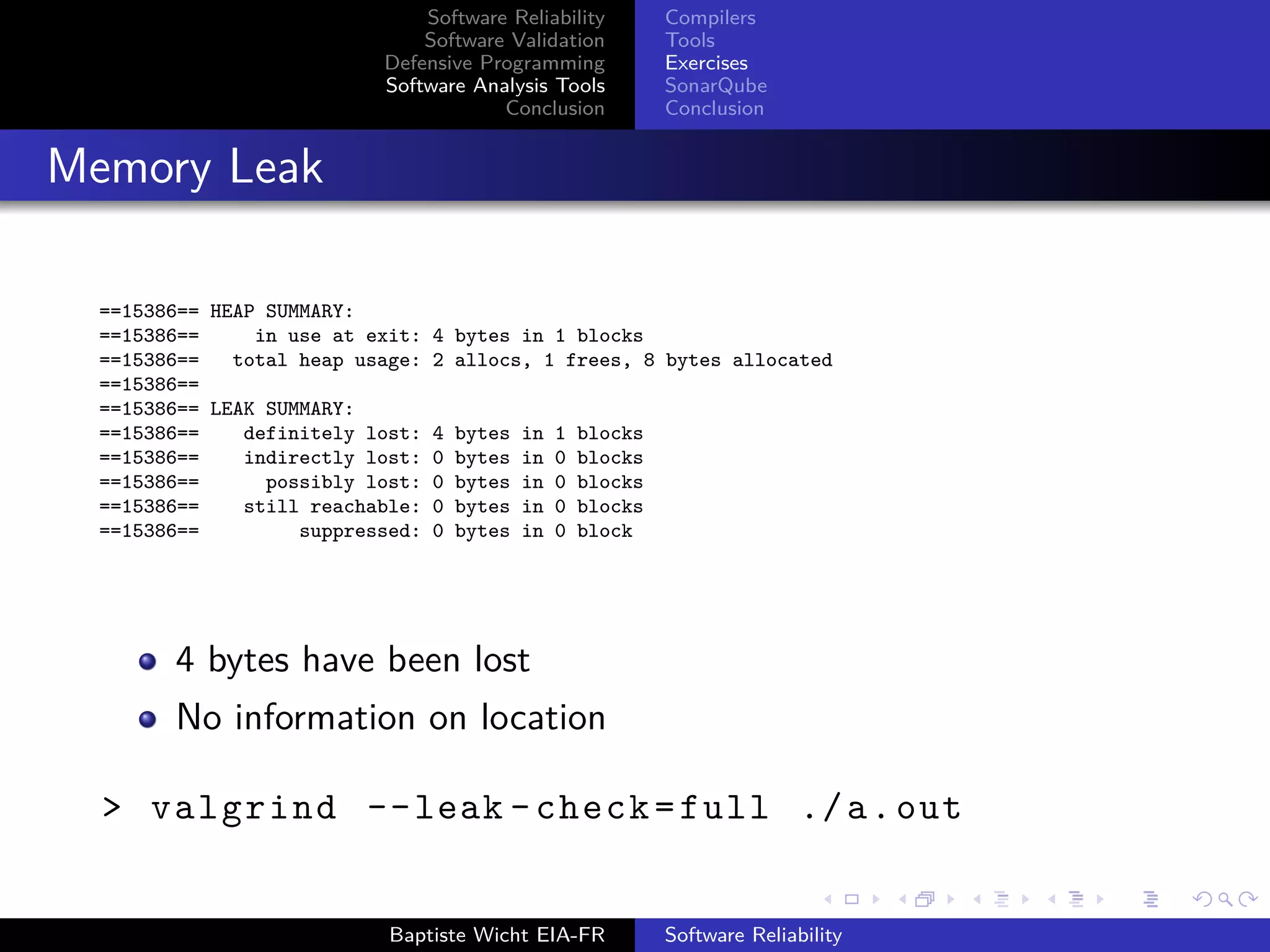
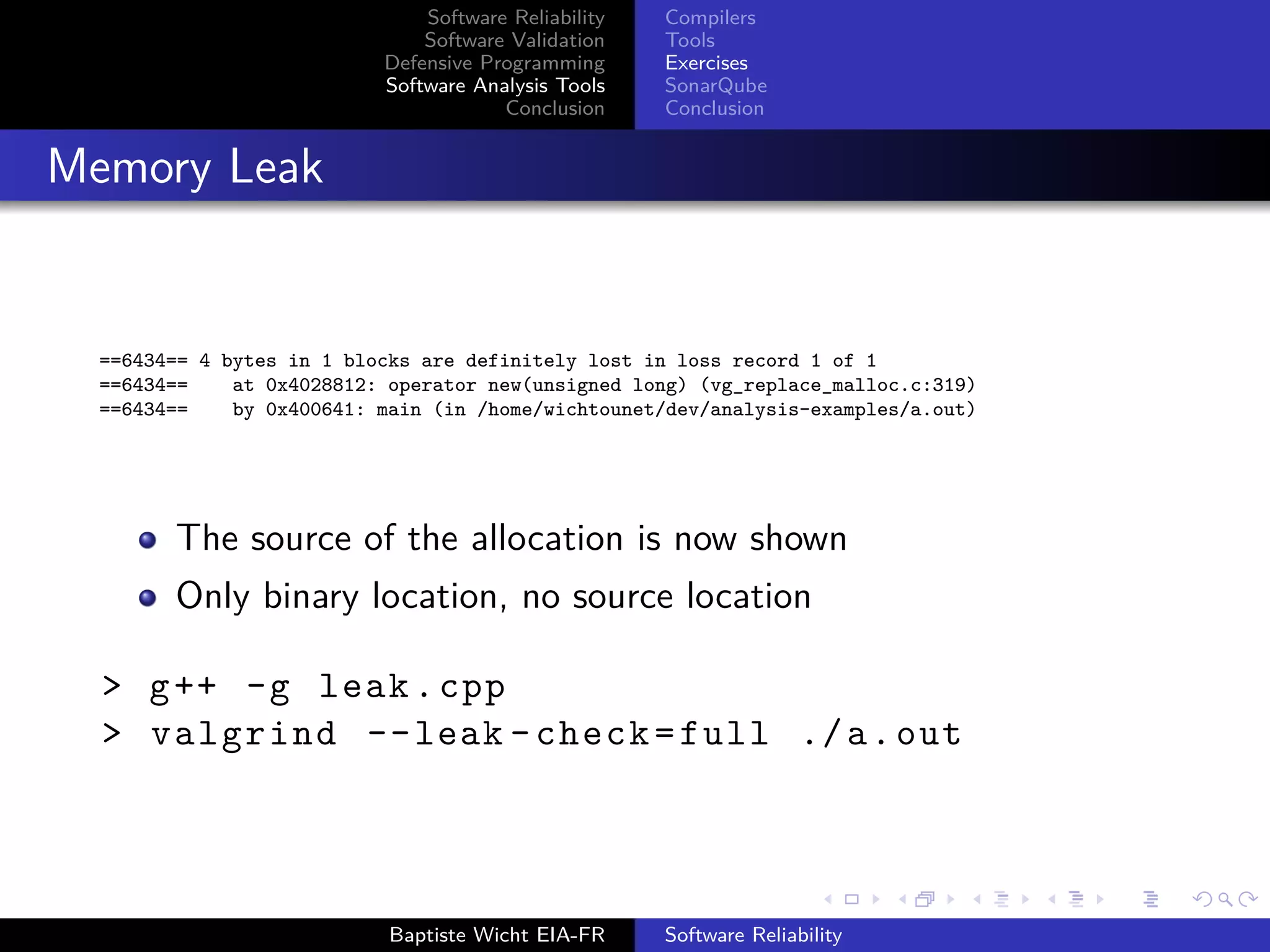
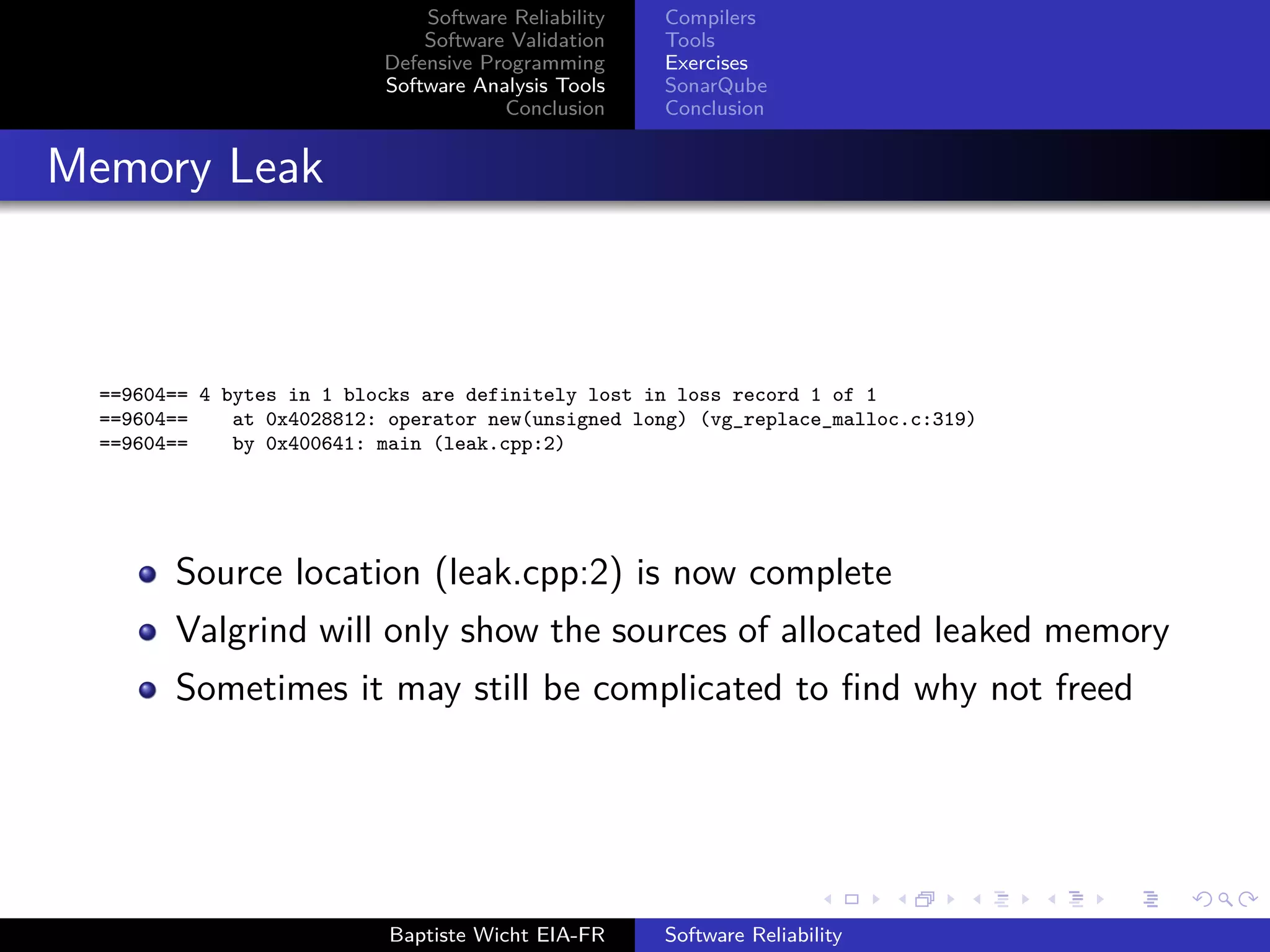
 (vg_replace_malloc.c:384)
==16922== by 0x400641: main (heap_overrun.cpp:2)
Source location of the invalid write (heap overrun.cpp:4)
Source location of the allocation (heap overrun.cpp:2)
> valgrind --leak -check=full ./a.out
Baptiste Wicht EIA-FR Software Reliability](https://image.slidesharecdn.com/softwarereliability-140606124250-phpapp01/75/Software-reliability-42-2048.jpg)
![Software Reliability
Software Validation
Defensive Programming
Software Analysis Tools
Conclusion
Compilers
Tools
Exercises
SonarQube
Conclusion
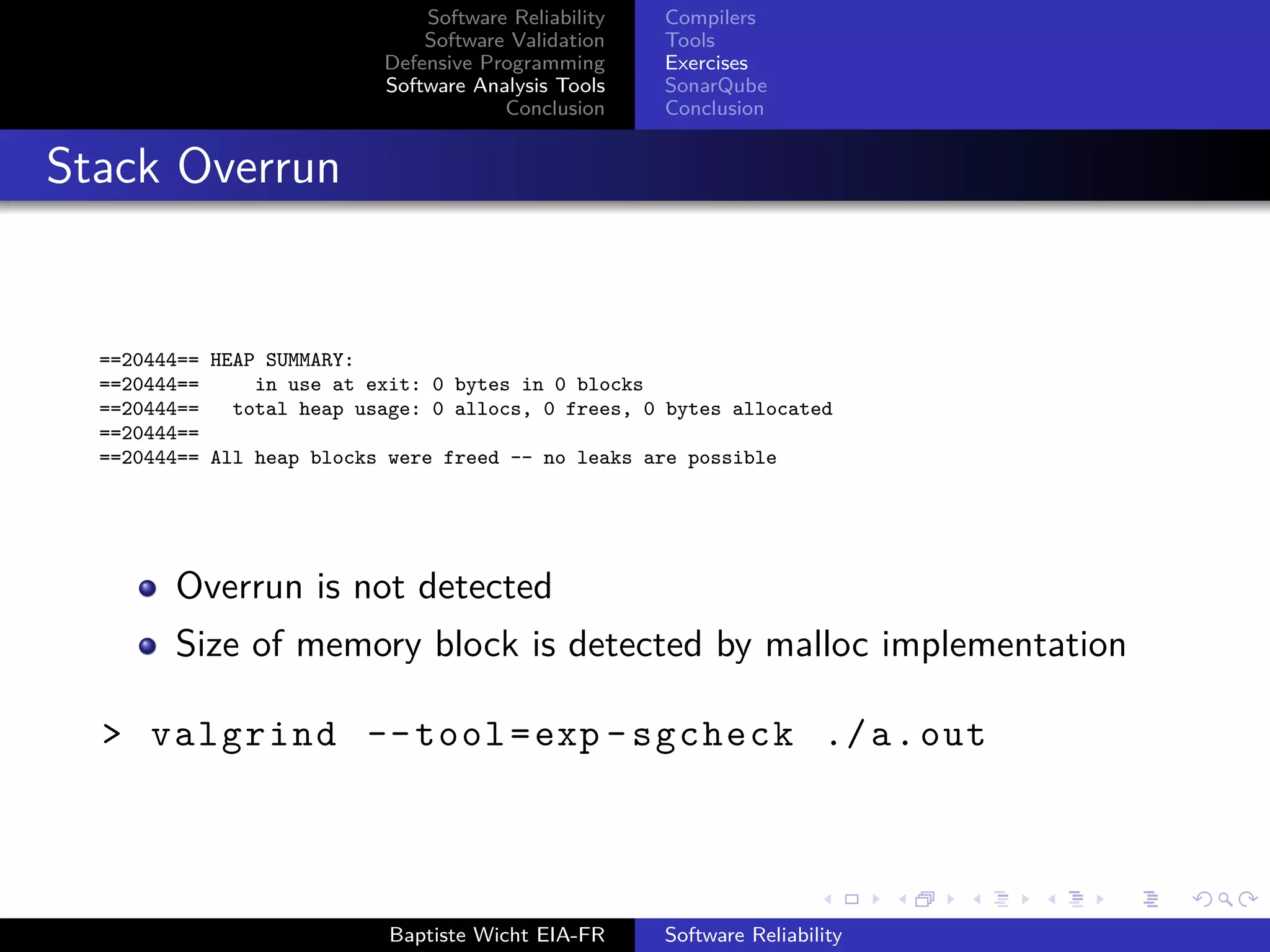
Stack Overrun
int main (){
int i, a[10];
for (i = 0; i <= 10; i++)
a[i] = 42;
return 0;
}
> g++ -g stack_overrun.cpp
> valgrind ./a.out
Baptiste Wicht EIA-FR Software Reliability](https://image.slidesharecdn.com/softwarereliability-140606124250-phpapp01/75/Software-reliability-43-2048.jpg)
![Software Reliability
Software Validation
Defensive Programming
Software Analysis Tools
Conclusion
Compilers
Tools
Exercises
SonarQube
Conclusion
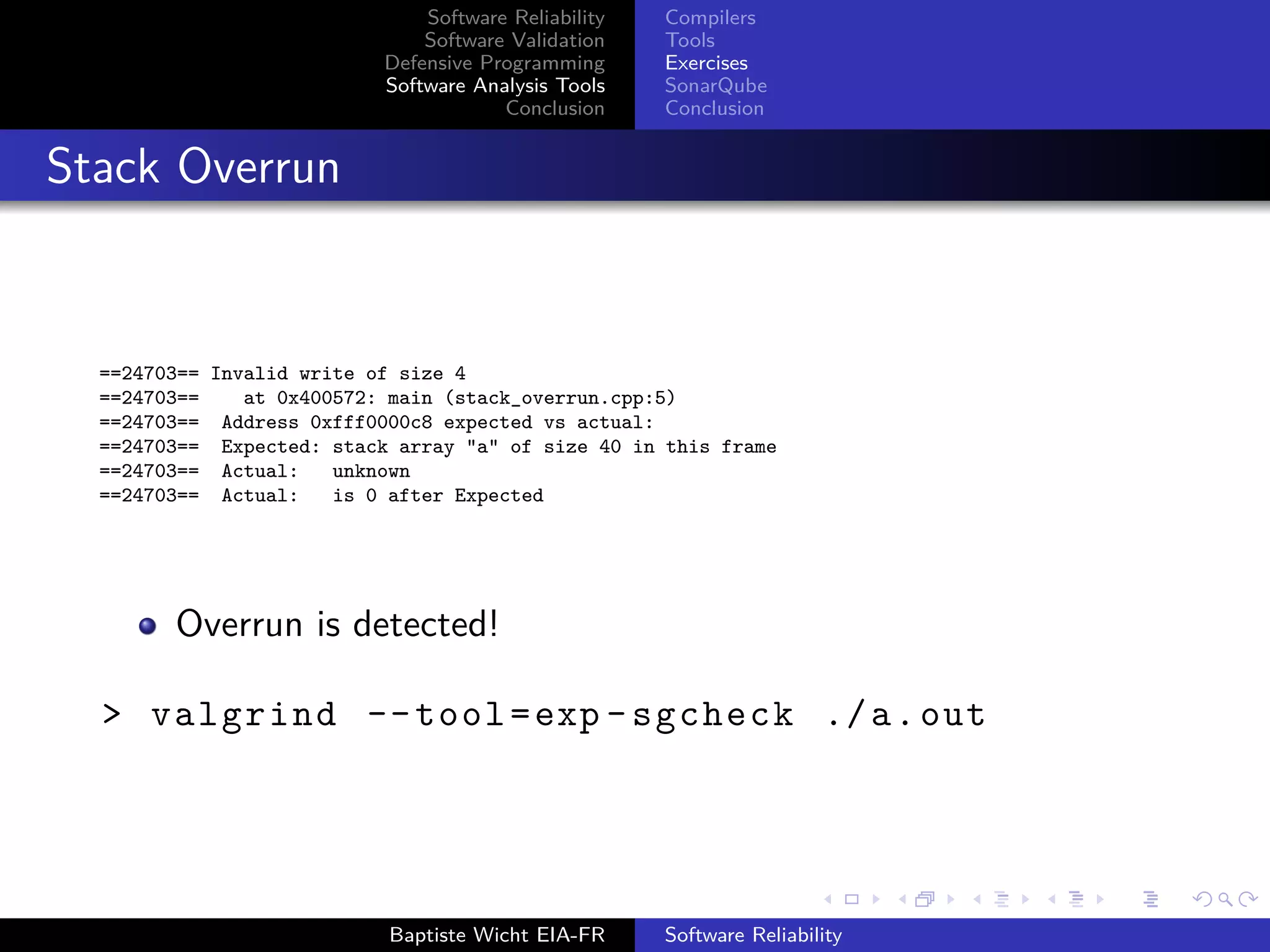
Stack Overrun 2
int main (){
int stack [5];
stack [5] = 0;
return 0;
}
> g++ -g stack_overrun_2 .cpp
> valgrind --tool=exp -sgcheck ./a.out
Baptiste Wicht EIA-FR Software Reliability](https://image.slidesharecdn.com/softwarereliability-140606124250-phpapp01/75/Software-reliability-46-2048.jpg)
![Software Reliability
Software Validation
Defensive Programming
Software Analysis Tools
Conclusion
Compilers
Tools
Exercises
SonarQube
Conclusion
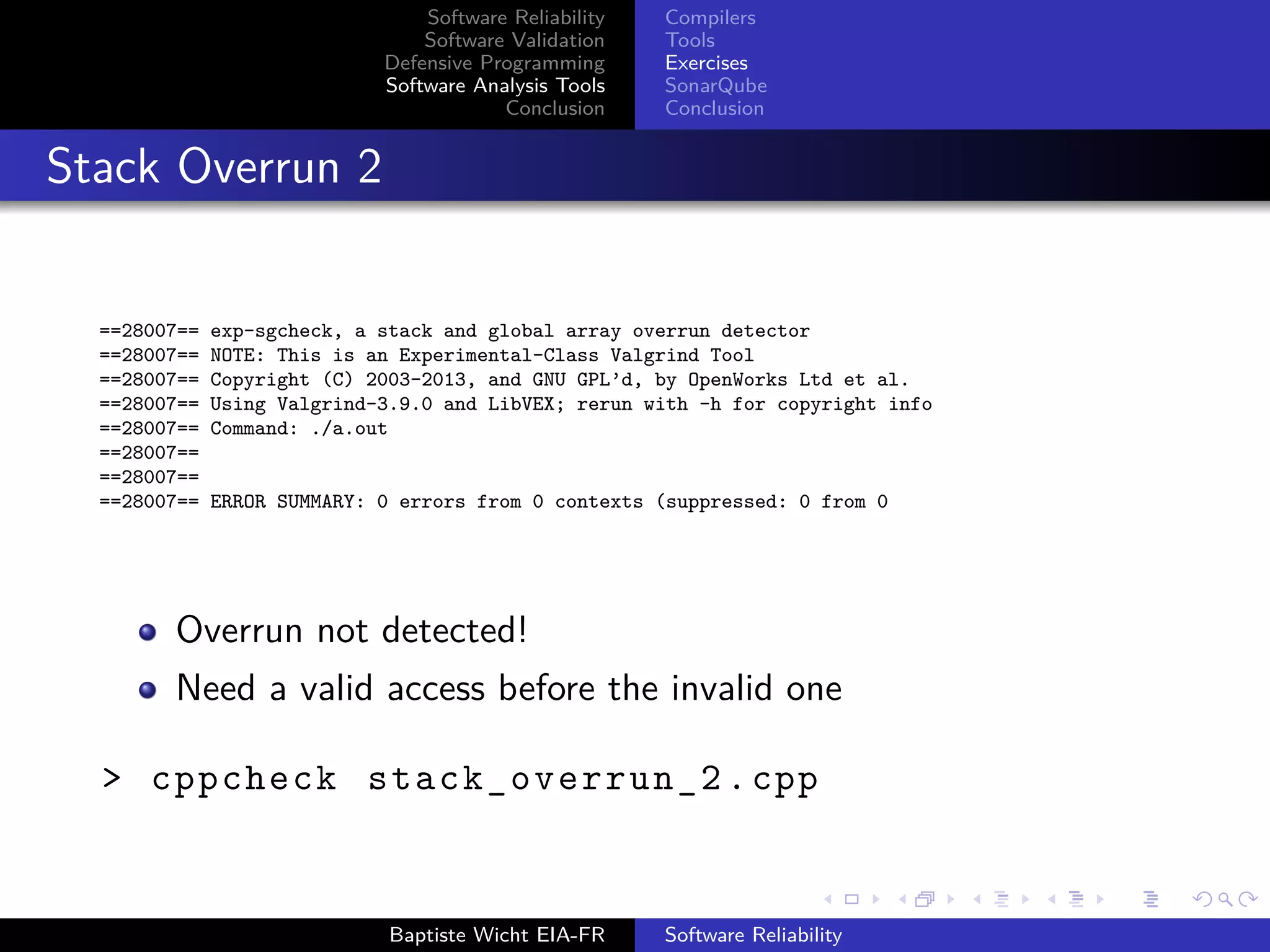
Stack Overrun 2
Checking stack_overrun_2.cpp...
[stack_overrun_2.cpp:4]: (error) Array ’stack[5]’ accessed at index 5, which is out of bounds.
Overrun detected!
Tools put together are very powerful
Baptiste Wicht EIA-FR Software Reliability](https://image.slidesharecdn.com/softwarereliability-140606124250-phpapp01/75/Software-reliability-48-2048.jpg)
![Software Reliability
Software Validation
Defensive Programming
Software Analysis Tools
Conclusion
Compilers
Tools
Exercises
SonarQube
Conclusion
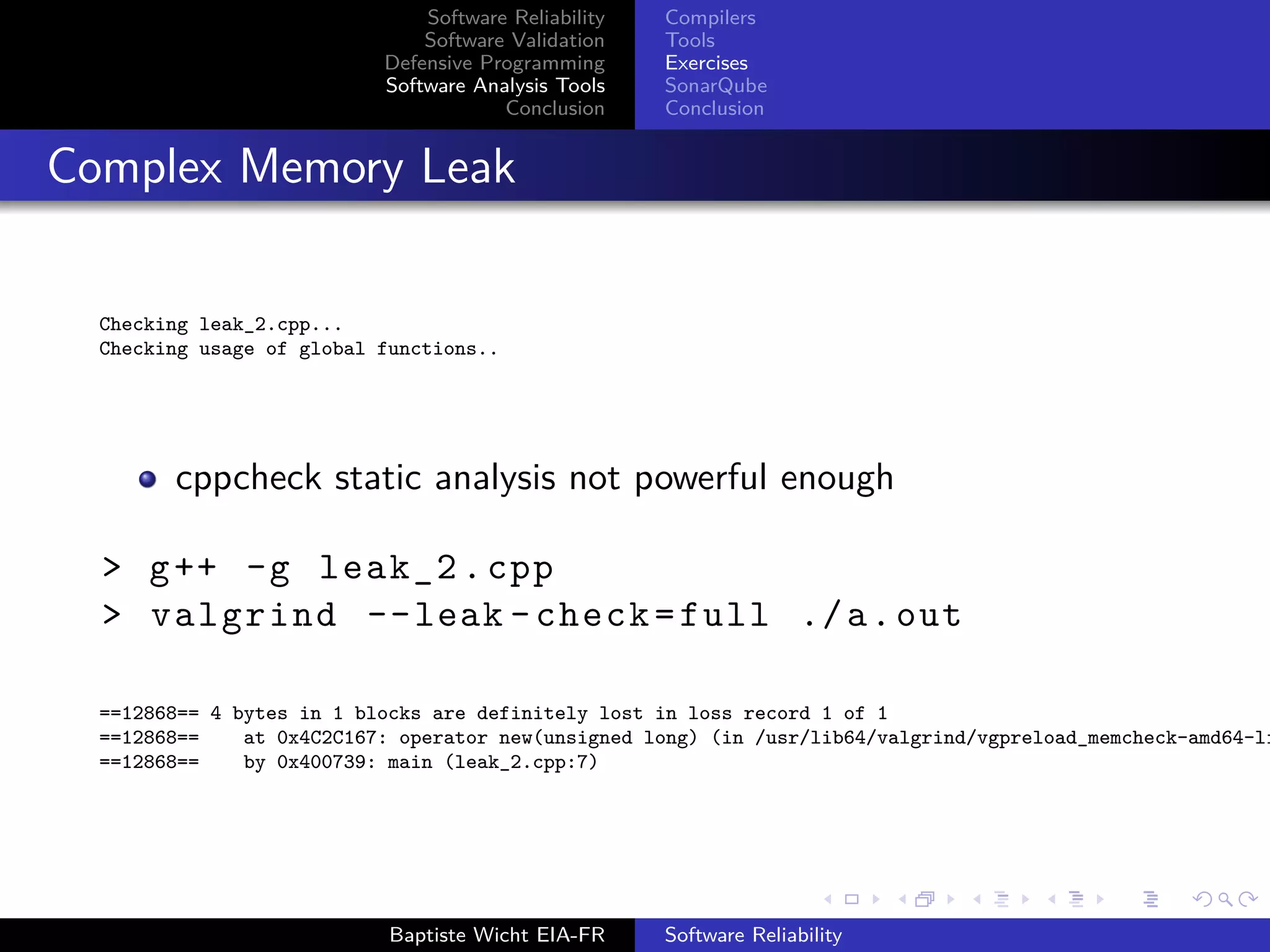
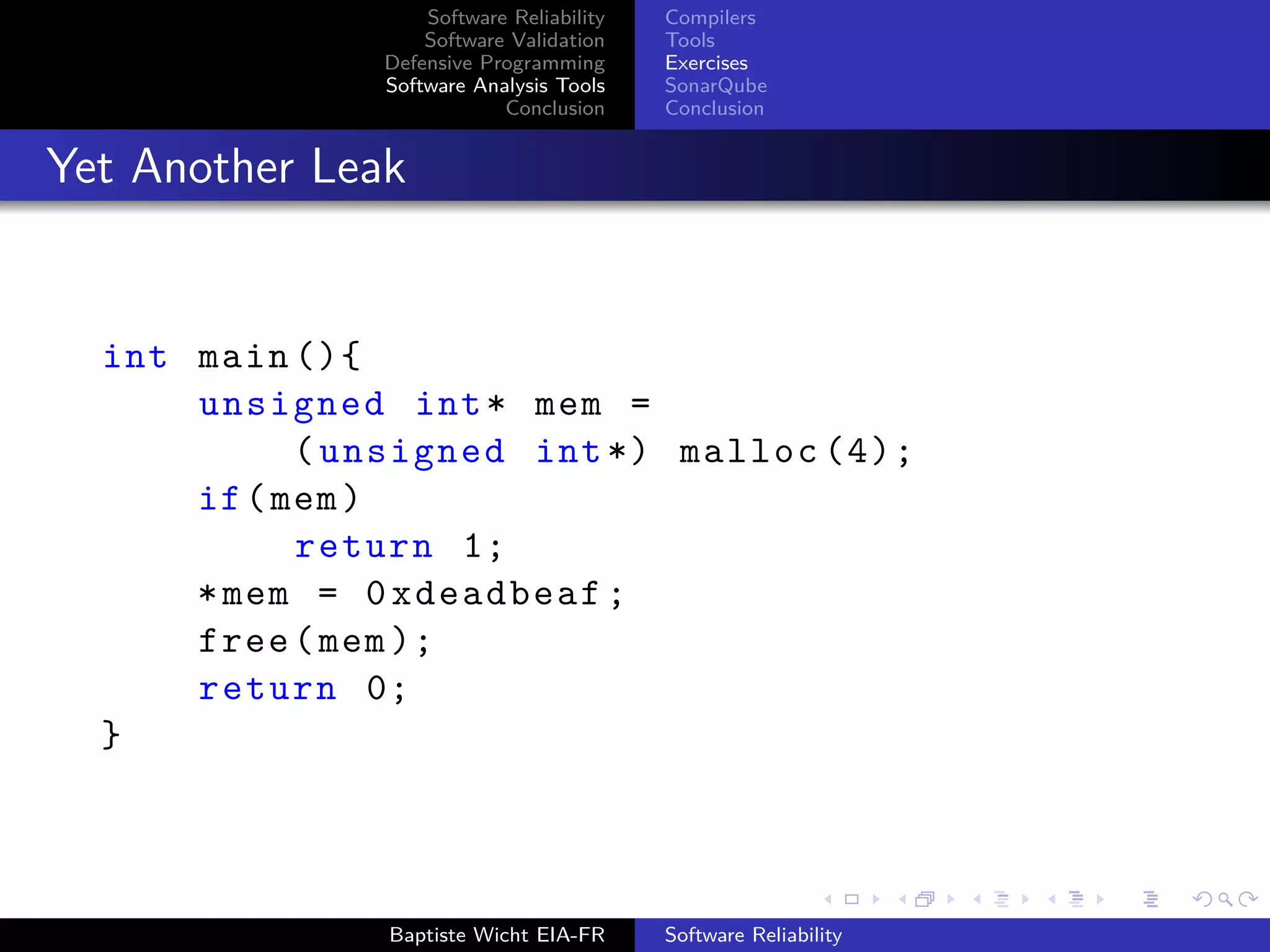
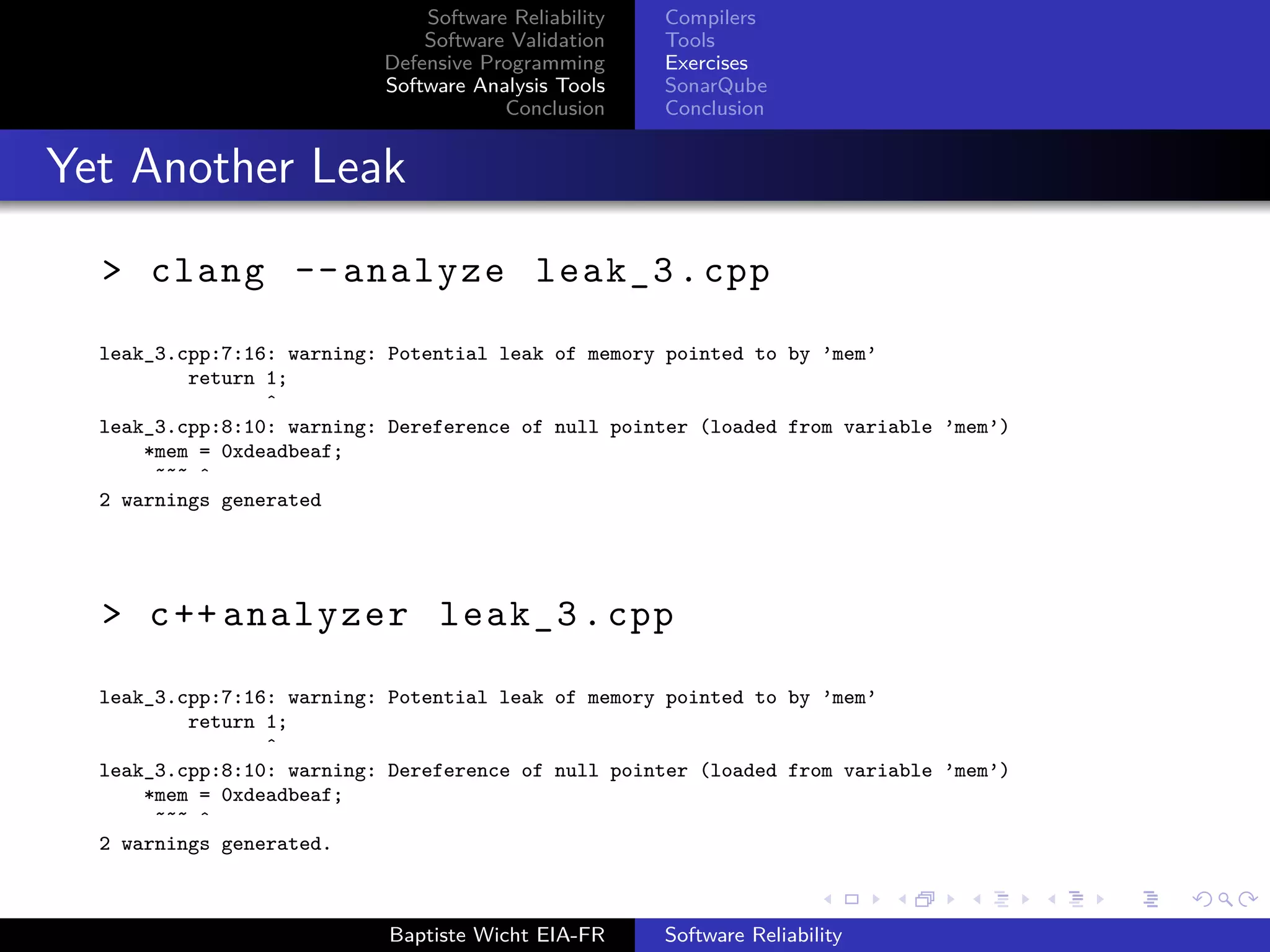
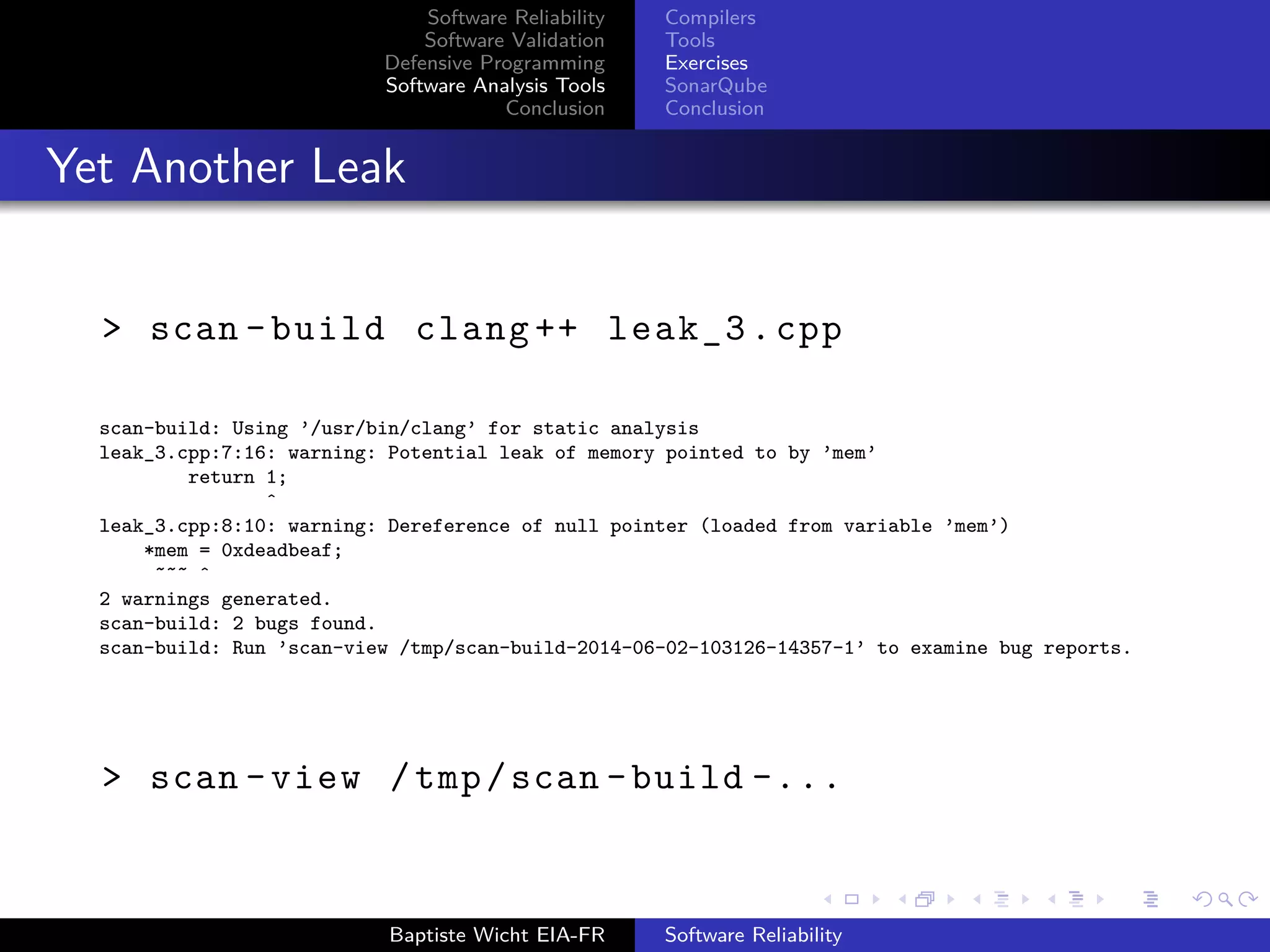
Complex Memory Leak
int main (){
int* array [42];
for(int i = 0; i < 42; ++i){
array[i] = new int;
}
// Something
for(int i = 0; i < 41; ++i){
delete array[i];
}
}
> cppcheck --enable=all leak_2.cpp
Baptiste Wicht EIA-FR Software Reliability](https://image.slidesharecdn.com/softwarereliability-140606124250-phpapp01/75/Software-reliability-49-2048.jpg)