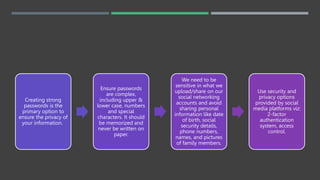
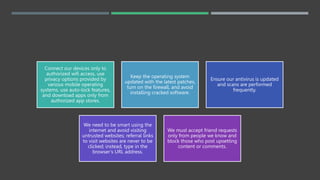
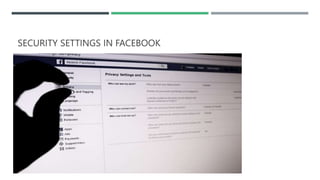
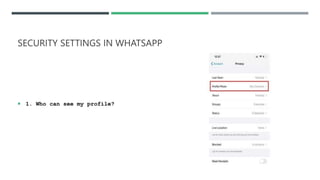
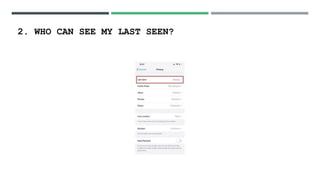
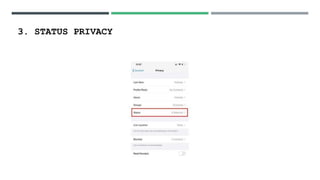
This document discusses social media security, privacy risks, and challenges. It outlines how sharing personal information on social media can lead to privacy breaches if default settings are not adjusted. It also explains how third parties can mine user data shared on social media for targeted advertising without consent. Additional risks include virus and malware attacks through ads, privacy issues with third party apps accessing contacts and location, legal issues from offensive posts, identity theft from shared personal details, cyberbullying, and use of social media for cyber terrorism activities. The document provides solutions such as using strong, unique passwords, being selective about shared information, enabling two-factor authentication and privacy settings, only installing apps from authorized sources, and keeping devices and software updated. It also