Infographic: Penetration Testing - A Look into a Full Pen Test Campaign
•
0 likes•1,071 views
A thorough penetration testing campaign involves social engineering, vulnerability scanning, and the manual hacking of computer systems, networks, and web applications. Follow this infographic to learn more about the various elements of a complete penetration test.
Report
Share
Report
Share
Download to read offline
Recommended
What is Social Engineering? An illustrated presentation.

Social engineering relies profoundly on human interaction and often involves the misleading of employees into violating their organization’s security procedures. Humans are naturally helpful, but when it comes to protecting an organization’s security, being helpful to an outsider can do more harm than good.
These slides discuss social engineering, the most common attack methods, and the best means for defending against a social engineering attack.
For more helpful cyber security blog articles, visit www.integritysrc.com/blog.
Social Engineering Basics

Do you know what social engineering is? Do you know how to protect yourself from attacks? Learn the basics so you can protect your business!
Social engineering

Social engineering is manipulating people into revealing confidential information through deception rather than technical hacking methods. It includes techniques like quid pro quo, phishing, baiting, pretexting, and diversion theft. Famous social engineer Kevin Mitnick emphasized that people inherently want to be helpful and trustworthy, making them vulnerable. Training and policies can help prevent social engineering by raising awareness of common tactics and restricting disclosure of private information. The human element remains the weakest link despite strong technical security defenses.
Social Engineering | #ARMSec2015

Social Engineering as the Art of "Human OS" hacking
Main points of the presentation (1) Overall introduction on social engineering (2) Case studies (3) Defending against Social Engineering.
for: http://armsec.org/
MHTA Social Engineering Presentation - 050917

This was the presentation given by Evan Francen at the 2017 MHTA Conference in Minneapolis on May 9, 2017.
Social Engineering,social engeineering techniques,social engineering protecti...

Social Engineering,social engineering techniques,social engineering protection techniques,stages of social engineering ,effect on organizations
Social engineering hacking attack

Learn what is social engineering attack. It includes the social engineering techniques like shoulder surfing, eavesdropping, baiting, Tailgating, phishing, spear phishing and pretexting.
Social Engineering

Social engineering relies on human interaction and manipulation to gain access or information through psychological attacks. It works by exploiting human weaknesses like insecurity, authority, urgency or familiarity. There are physical techniques like impersonation or tailgating and digital methods like phishing emails, spam, hoaxes or hijacking common website misspellings to trick users into giving away access or sensitive information. Social engineering is an ongoing tactic that requires constant vigilance against evolving methods of deception targeting human vulnerabilities.
Recommended
What is Social Engineering? An illustrated presentation.

Social engineering relies profoundly on human interaction and often involves the misleading of employees into violating their organization’s security procedures. Humans are naturally helpful, but when it comes to protecting an organization’s security, being helpful to an outsider can do more harm than good.
These slides discuss social engineering, the most common attack methods, and the best means for defending against a social engineering attack.
For more helpful cyber security blog articles, visit www.integritysrc.com/blog.
Social Engineering Basics

Do you know what social engineering is? Do you know how to protect yourself from attacks? Learn the basics so you can protect your business!
Social engineering

Social engineering is manipulating people into revealing confidential information through deception rather than technical hacking methods. It includes techniques like quid pro quo, phishing, baiting, pretexting, and diversion theft. Famous social engineer Kevin Mitnick emphasized that people inherently want to be helpful and trustworthy, making them vulnerable. Training and policies can help prevent social engineering by raising awareness of common tactics and restricting disclosure of private information. The human element remains the weakest link despite strong technical security defenses.
Social Engineering | #ARMSec2015

Social Engineering as the Art of "Human OS" hacking
Main points of the presentation (1) Overall introduction on social engineering (2) Case studies (3) Defending against Social Engineering.
for: http://armsec.org/
MHTA Social Engineering Presentation - 050917

This was the presentation given by Evan Francen at the 2017 MHTA Conference in Minneapolis on May 9, 2017.
Social Engineering,social engeineering techniques,social engineering protecti...

Social Engineering,social engineering techniques,social engineering protection techniques,stages of social engineering ,effect on organizations
Social engineering hacking attack

Learn what is social engineering attack. It includes the social engineering techniques like shoulder surfing, eavesdropping, baiting, Tailgating, phishing, spear phishing and pretexting.
Social Engineering

Social engineering relies on human interaction and manipulation to gain access or information through psychological attacks. It works by exploiting human weaknesses like insecurity, authority, urgency or familiarity. There are physical techniques like impersonation or tailgating and digital methods like phishing emails, spam, hoaxes or hijacking common website misspellings to trick users into giving away access or sensitive information. Social engineering is an ongoing tactic that requires constant vigilance against evolving methods of deception targeting human vulnerabilities.
Social engineering 

This document discusses social engineering and its threats. Social engineering refers to manipulating people into performing actions or divulging confidential information. It is a significant threat because existing computer security technologies do not protect against human vulnerabilities. Common social engineering attacks include phishing emails, vishing phone calls, leaving infected USB drives in parking lots, and impersonating maintenance workers. The document demonstrates real examples of vishing attacks and provides tips for preventing social engineering, such as verifying identities of people requesting information. However, it notes that fully preventing social engineering attacks can be difficult due to human factors.
Social engineering

Social engineering is manipulating people into revealing sensitive information or performing actions, rather than using technical hacking methods. It involves gaining people's trust and obtaining information that seems harmless but can be combined to compromise security. Famous social engineer Kevin Mitnick used only social engineering to access private networks. Common social engineering attacks include phishing scams, impersonating help desk staff, stealing documents, and installing malware under false pretenses. The weakest link is often human rather than technical, as people are more vulnerable to manipulation. Training employees, testing defenses with ethical hackers, and verifying unsolicited contacts can help prevent social engineering attacks.
Social engineering tales 

An introductory session about Social Engineering presented at ICT Nuggets Forum - Khartoum, organized by Duko team. We talked about what is social engineering? terms related to it? and how attacks can bee carried. We also told a lot of stories about successful social engineering attacks and how much damage they did. Finally we talked about how to protect yourself and your company social engineering attacks.
Social Engineering: the Bad, Better, and Best Incident Response Plans

One of today's most challenging security issues is social engineering defense. Despite evidence proving the impact of a social engineering attack, we often see inadequate incident response plans in place. In this talk, we will share our experiences about what organizations are doing when (or, more commonly, if) they detect an attack, steps to strengthen the social engineering defensive strategy, and what best practices to enforce for the strongest possible security posture.
Social engineering 

Social engineering is a form of hacking that exploits human trust and helpfulness. It is done through impersonation, phone calls, email, or in-person interactions to obtain sensitive information. Anyone can be a target if the social engineer can build rapport and trust. Common techniques include pretending to need technical help, claiming to be from the same organization, or creating a sense of urgency or fear in the target. Education and strict security policies are needed to combat social engineering threats.
Social Engineering: "The Cyber-Con"

A detailed look at the growing threat of social engineering, examples of such attacks, and recommendations for effective prevention in the workplace.
Social engineering for security attacks

Social Engineering is a kind of advance persistent threat (APT) that gains private and sensitive information through social networks or other types of communication
Social Engineering - Are You Protecting Your Data Enough?

Social engineering involves deceiving people into providing private information through manipulation. Common social engineering attacks include phishing scams by email or phone that try to steal login credentials. Other methods are shoulder surfing to see passwords, dumpster diving to find sensitive trash, and tailgating to access restricted areas. Social engineering works because people are inclined to trust authority, follow social proof, reciprocate kindness, and make decisions based on scarcity and distractions. Protecting against social engineering requires vigilance, secure disposal of documents, awareness of manipulation tactics, and escalating any suspicious requests for information.
Social Engineering - Human aspects of industrial and economic espionage

Social engineering is not just a supporting process to obtain system access; it could be the main attack. Organizations that focus only on a narrow definition of social engineering as an attack vector to obtain system access will fail to create awareness of all other possible social engineering attack methods.
Hacking and Penetration Testing - a beginners guide

Learn all about hacking and penetration testing. The phases in hacking, the process of hacking and then learning what is penetration testing. Also get a sense of cyber crimes and cyber security
Social engineering

Social engineering involves manipulating people into revealing confidential information through psychological tricks. Attackers use tactics like establishing trust, playing on emotions like fear or curiosity, or pretending to have technical expertise to obtain information like passwords, financial details, or other personal data. Common targets are employees who may unintentionally compromise security. The impacts of social engineering can be significant, such as the $80 million bank hacking in Bangladesh. Individuals and organizations can protect themselves through security awareness training, strong password management, two-factor authentication, and limiting the personal information shared online.
Social engineering presentation

Social engineering is a type of attack that manipulates people into revealing sensitive information or performing actions that violate security policies. It works by exploiting human trust and the natural tendency to help others. Attackers first gather information about targets, then develop relationships to gain trust before exploiting that trust to obtain access or steal information. Common social engineering techniques include phishing emails and calls where attackers pretend to be from technical support. While no system can fully prevent social engineering, organizations can minimize risks by educating users and restricting what sensitive information users provide over the phone or to unknown parties.
Presentation of Social Engineering - The Art of Human Hacking

Nowadays if you want to hack a corporation or damage a personal "enemy" fast, Social Engineering techniques work every time and more often than not it works the first time. Within the presentation you will be able to learn what social engineering is, types of social engineering and related threats.
Social engineering-Attack of the Human Behavior

Social engineering exploits human behavior and trust to gain access to sensitive information. It includes technical attacks like phishing emails and pop-up windows, as well as non-technical attacks like dumpster diving. Common human behaviors exploited include curiosity, fear, and thoughtlessness. To help mitigate social engineering risks, organizations should educate employees, implement security policies, conduct audits, and use technical defenses like email filters and firewalls. Regular awareness training can help motivate employees to follow best practices.
Social engineering

This document discusses social engineering and why organizations should use it. Social engineering involves using psychological manipulation to trick people into revealing confidential information. It works because people are inherently lazy, want to help, and are curious. The document outlines common social engineering techniques like phishing, impersonation, and physical security compromises. It recommends that organizations conduct social engineering assessments of their own employees to identify vulnerabilities and provide ongoing training. Regular social engineering tests can help educate employees and strengthen an organization's security over time.
Social Engineering

Social Engineering - Human aspects of grey and black competitive intelligence. What is social engineering? How it is used in the context of competitive intelligence and industrial espionage? How to recognize HUMINT / social engineering attacks? Which governments are known to use it?
Social Engineering 2.0

Dr. Shawn P. Murray was invited to the National Security Institute in April 2012 to present current topics related to social engineering and the threats they pose to organizations and their sensitive information. This presentation analyzes the principles of social engineering tactics as they relate to technology and security practices. Dr. Murray is a well known Cyber Security professional and has presented at various conferences regarding Cyber Security and Information Assurance topics.
Sharon Conheady - Social engineering & social networks (4 novmber Jaarbeurs U...

This document discusses how social engineers exploit social networking sites for malicious purposes such as gathering sensitive information, distributing malware, and executing attacks. It provides examples of common social engineering techniques used over social networks, including impersonating individuals to gain their trust, hijacking accounts to target friends, and setting up fake groups or sending malicious attachments disguised as coming from trusted sources like Facebook. The document also explains how social networks are used for reconnaissance by revealing personal details that can help social engineers craft more convincing phishing attacks.
social engineering

The document defines and discusses various social engineering techniques used to psychologically manipulate people into divulging confidential information or performing actions, including pretexting, diversion theft, phishing, baiting, quid pro quo, and tailgating. Pretexting involves creating fake scenarios to engage victims and trick them into providing information, while phishing uses fraudulent emails appearing to be from legitimate companies to steal personal details. Baiting and quid pro quo manipulate people using curiosity, greed or promises of help in exchange for access or information.
Social engineering The Good and Bad

Understand Social Engineering on a new perspective, beyond the conventional understanding that we have, learn how we use it on social development and securing the weakest link in cybersecurity
Ethical hacking 

The presentation is recently designed by me for my college presentation on ethical hacking . Hope the info will help you in your learning.
Ethical hacking and social engineering

ETHICAL HACKING AND SOCIAL ENGINEERING
Topics Covered: Ethical Hacking Concepts and Scopes, Threats and Attack Vectors, Information Assurance, Threat Modelling, Enterprise Information Security Architecture, Vulnerability, Assessment and Penetration Testing, Types of Social Engineering, Insider Attack, Preventing Insider Threats, Social Engineering Targets and Defence Strategies
More Related Content
What's hot
Social engineering 

This document discusses social engineering and its threats. Social engineering refers to manipulating people into performing actions or divulging confidential information. It is a significant threat because existing computer security technologies do not protect against human vulnerabilities. Common social engineering attacks include phishing emails, vishing phone calls, leaving infected USB drives in parking lots, and impersonating maintenance workers. The document demonstrates real examples of vishing attacks and provides tips for preventing social engineering, such as verifying identities of people requesting information. However, it notes that fully preventing social engineering attacks can be difficult due to human factors.
Social engineering

Social engineering is manipulating people into revealing sensitive information or performing actions, rather than using technical hacking methods. It involves gaining people's trust and obtaining information that seems harmless but can be combined to compromise security. Famous social engineer Kevin Mitnick used only social engineering to access private networks. Common social engineering attacks include phishing scams, impersonating help desk staff, stealing documents, and installing malware under false pretenses. The weakest link is often human rather than technical, as people are more vulnerable to manipulation. Training employees, testing defenses with ethical hackers, and verifying unsolicited contacts can help prevent social engineering attacks.
Social engineering tales 

An introductory session about Social Engineering presented at ICT Nuggets Forum - Khartoum, organized by Duko team. We talked about what is social engineering? terms related to it? and how attacks can bee carried. We also told a lot of stories about successful social engineering attacks and how much damage they did. Finally we talked about how to protect yourself and your company social engineering attacks.
Social Engineering: the Bad, Better, and Best Incident Response Plans

One of today's most challenging security issues is social engineering defense. Despite evidence proving the impact of a social engineering attack, we often see inadequate incident response plans in place. In this talk, we will share our experiences about what organizations are doing when (or, more commonly, if) they detect an attack, steps to strengthen the social engineering defensive strategy, and what best practices to enforce for the strongest possible security posture.
Social engineering 

Social engineering is a form of hacking that exploits human trust and helpfulness. It is done through impersonation, phone calls, email, or in-person interactions to obtain sensitive information. Anyone can be a target if the social engineer can build rapport and trust. Common techniques include pretending to need technical help, claiming to be from the same organization, or creating a sense of urgency or fear in the target. Education and strict security policies are needed to combat social engineering threats.
Social Engineering: "The Cyber-Con"

A detailed look at the growing threat of social engineering, examples of such attacks, and recommendations for effective prevention in the workplace.
Social engineering for security attacks

Social Engineering is a kind of advance persistent threat (APT) that gains private and sensitive information through social networks or other types of communication
Social Engineering - Are You Protecting Your Data Enough?

Social engineering involves deceiving people into providing private information through manipulation. Common social engineering attacks include phishing scams by email or phone that try to steal login credentials. Other methods are shoulder surfing to see passwords, dumpster diving to find sensitive trash, and tailgating to access restricted areas. Social engineering works because people are inclined to trust authority, follow social proof, reciprocate kindness, and make decisions based on scarcity and distractions. Protecting against social engineering requires vigilance, secure disposal of documents, awareness of manipulation tactics, and escalating any suspicious requests for information.
Social Engineering - Human aspects of industrial and economic espionage

Social engineering is not just a supporting process to obtain system access; it could be the main attack. Organizations that focus only on a narrow definition of social engineering as an attack vector to obtain system access will fail to create awareness of all other possible social engineering attack methods.
Hacking and Penetration Testing - a beginners guide

Learn all about hacking and penetration testing. The phases in hacking, the process of hacking and then learning what is penetration testing. Also get a sense of cyber crimes and cyber security
Social engineering

Social engineering involves manipulating people into revealing confidential information through psychological tricks. Attackers use tactics like establishing trust, playing on emotions like fear or curiosity, or pretending to have technical expertise to obtain information like passwords, financial details, or other personal data. Common targets are employees who may unintentionally compromise security. The impacts of social engineering can be significant, such as the $80 million bank hacking in Bangladesh. Individuals and organizations can protect themselves through security awareness training, strong password management, two-factor authentication, and limiting the personal information shared online.
Social engineering presentation

Social engineering is a type of attack that manipulates people into revealing sensitive information or performing actions that violate security policies. It works by exploiting human trust and the natural tendency to help others. Attackers first gather information about targets, then develop relationships to gain trust before exploiting that trust to obtain access or steal information. Common social engineering techniques include phishing emails and calls where attackers pretend to be from technical support. While no system can fully prevent social engineering, organizations can minimize risks by educating users and restricting what sensitive information users provide over the phone or to unknown parties.
Presentation of Social Engineering - The Art of Human Hacking

Nowadays if you want to hack a corporation or damage a personal "enemy" fast, Social Engineering techniques work every time and more often than not it works the first time. Within the presentation you will be able to learn what social engineering is, types of social engineering and related threats.
Social engineering-Attack of the Human Behavior

Social engineering exploits human behavior and trust to gain access to sensitive information. It includes technical attacks like phishing emails and pop-up windows, as well as non-technical attacks like dumpster diving. Common human behaviors exploited include curiosity, fear, and thoughtlessness. To help mitigate social engineering risks, organizations should educate employees, implement security policies, conduct audits, and use technical defenses like email filters and firewalls. Regular awareness training can help motivate employees to follow best practices.
Social engineering

This document discusses social engineering and why organizations should use it. Social engineering involves using psychological manipulation to trick people into revealing confidential information. It works because people are inherently lazy, want to help, and are curious. The document outlines common social engineering techniques like phishing, impersonation, and physical security compromises. It recommends that organizations conduct social engineering assessments of their own employees to identify vulnerabilities and provide ongoing training. Regular social engineering tests can help educate employees and strengthen an organization's security over time.
Social Engineering

Social Engineering - Human aspects of grey and black competitive intelligence. What is social engineering? How it is used in the context of competitive intelligence and industrial espionage? How to recognize HUMINT / social engineering attacks? Which governments are known to use it?
Social Engineering 2.0

Dr. Shawn P. Murray was invited to the National Security Institute in April 2012 to present current topics related to social engineering and the threats they pose to organizations and their sensitive information. This presentation analyzes the principles of social engineering tactics as they relate to technology and security practices. Dr. Murray is a well known Cyber Security professional and has presented at various conferences regarding Cyber Security and Information Assurance topics.
Sharon Conheady - Social engineering & social networks (4 novmber Jaarbeurs U...

This document discusses how social engineers exploit social networking sites for malicious purposes such as gathering sensitive information, distributing malware, and executing attacks. It provides examples of common social engineering techniques used over social networks, including impersonating individuals to gain their trust, hijacking accounts to target friends, and setting up fake groups or sending malicious attachments disguised as coming from trusted sources like Facebook. The document also explains how social networks are used for reconnaissance by revealing personal details that can help social engineers craft more convincing phishing attacks.
social engineering

The document defines and discusses various social engineering techniques used to psychologically manipulate people into divulging confidential information or performing actions, including pretexting, diversion theft, phishing, baiting, quid pro quo, and tailgating. Pretexting involves creating fake scenarios to engage victims and trick them into providing information, while phishing uses fraudulent emails appearing to be from legitimate companies to steal personal details. Baiting and quid pro quo manipulate people using curiosity, greed or promises of help in exchange for access or information.
Social engineering The Good and Bad

Understand Social Engineering on a new perspective, beyond the conventional understanding that we have, learn how we use it on social development and securing the weakest link in cybersecurity
What's hot (20)
Social Engineering: the Bad, Better, and Best Incident Response Plans

Social Engineering: the Bad, Better, and Best Incident Response Plans
Social Engineering - Are You Protecting Your Data Enough?

Social Engineering - Are You Protecting Your Data Enough?
Social Engineering - Human aspects of industrial and economic espionage

Social Engineering - Human aspects of industrial and economic espionage
Hacking and Penetration Testing - a beginners guide

Hacking and Penetration Testing - a beginners guide
Presentation of Social Engineering - The Art of Human Hacking

Presentation of Social Engineering - The Art of Human Hacking
Sharon Conheady - Social engineering & social networks (4 novmber Jaarbeurs U...

Sharon Conheady - Social engineering & social networks (4 novmber Jaarbeurs U...
Similar to Infographic: Penetration Testing - A Look into a Full Pen Test Campaign
Ethical hacking 

The presentation is recently designed by me for my college presentation on ethical hacking . Hope the info will help you in your learning.
Ethical hacking and social engineering

ETHICAL HACKING AND SOCIAL ENGINEERING
Topics Covered: Ethical Hacking Concepts and Scopes, Threats and Attack Vectors, Information Assurance, Threat Modelling, Enterprise Information Security Architecture, Vulnerability, Assessment and Penetration Testing, Types of Social Engineering, Insider Attack, Preventing Insider Threats, Social Engineering Targets and Defence Strategies
Module 3-cyber security

Ethical Hacking Concepts and Scopes, Threats and Attack Vectors, Information Assurance, Threat Modelling
Enterprise Information Security Architecture, Vulnerability
Assessment and Penetration Testing
Types of Social Engineering, Insider Attack, Preventing Insider
Threats, Social Engineering Targets and Defence Strategies
Mis3rd

The document discusses several topics related to information systems and e-commerce:
1) It defines e-business and electronic commerce as conducting business online through buying, selling, and servicing customers.
2) It explains that "communitainment" refers to how the internet has become a medium for community, communication and entertainment.
3) Two key ethical issues related to e-commerce are threats to individual privacy from data collection and potential job losses as e-commerce reduces the need for some roles. Companies must handle layoffs and assist displaced workers sensitively.
Application security testing an integrated approach

This document discusses application security testing and provides recommendations for a comprehensive testing plan. It begins by outlining common application security vulnerabilities like injection flaws, cross-site scripting, and sensitive data exposure. It then recommends using tools like vulnerability scanning, threat modeling, code analysis, and penetration testing to test for vulnerabilities. The document concludes by describing how to test for issues in specific areas like authentication, authorization, data validation, and payment processing.
Best Ethical Hacking Institute in Delhi 

The field of information security or ethical hacking is among the most interesting employment options. It is important to protect our digital assets from hackers in today's world where everything is digital or computerized. Many companies both nationally and internationally are looking for ethical hackers or cyber security specialists.
https://ethicalhackingcourseindelhi3.blogspot.com/2022/12/best-ethical-hacking-course-in-delhi.html
attack vectors by chimwemwe.pptx

The document discusses computer security and common cyber attack vectors. It defines key terms like attack surface, attack vectors, and security breaches. It then describes 8 common attack vectors: compromised credentials, weak/stolen credentials, malicious insiders, missing/poor encryption, misconfiguration, ransomware, phishing, and trust relationships. Typical symptoms of an attack are also listed, such as slow performance, strange files/programs, and automatic messages. The consequences of a successful attack compromise the goals of computer security - confidentiality, integrity and availability.
VAPT - Vulnerability Assessment & Penetration Testing 

VAPT (Vulnerability Assessment and Penetration Testing) involves evaluating systems and networks to identify vulnerabilities, configuration issues, and potential routes of unauthorized access. It is recommended for SMEs due to common security issues like phishing and ransomware attacks targeting them. The document outlines the types of VAPT testing, why SMEs need it, example data breaches, and estimated costs of common cyber attacks and security services.
Types of attack -Part3 (Malware Part -2)

This document discusses various types of malware and cyber attacks. It describes crimeware as software used to perpetrate illegal acts, such as identity theft, and notes it can spread through viruses, Trojans, worms, spyware or adware. Trapdoors and backdoors allow unauthorized access to systems by bypassing authentication. Keyloggers record keystrokes to steal personal or financial information. Spoofing tricks networks by masquerading as a legitimate entity. Phishing uses fraudulent emails to steal information. Sniffing monitors network traffic to extract passwords and other data from packets. Port scanning identifies open ports that could enable unauthorized access. SQL injection allows interference with database queries and access to data.
Cyber security

In present world, where computers/laptops and smart phone made it possible to extract other's secrets, a need has been imminent to handle such problems by Cyber Security Regime, which not only be launched by individuls(IT Expert) of organizations but the governments of the country should also play a vital role.
Information Technology Security Is Vital For The Success...

Here are a few key ways organizations can manage IoT and BYOD threats while preserving productivity:
1. Implement a zero-trust network access (ZTNA) model. Rather than trusting devices based on their location, authenticate each device and user and apply granular access policies. Only grant as much access as necessary.
2. Use network segmentation to isolate BYOD/IoT traffic. Put these devices on their own network segments separate from sensitive corporate resources. Enforce policies at the network edge.
3. Conduct risk assessments of all connecting devices. Understand what data each device needs access to and what vulnerabilities it may pose. Deny access if risks outweigh benefits.
4. Require endpoint security on all BY
Ethical Hacking Services

A short summary of ethical hacking services as well basic information on vulnerability assessments and the types of security tests we offer.
Ethical Hacking justvamshi .pptx

Hacking involves identifying and exploiting weaknesses in computer systems to gain unauthorized access, while ethical hacking (also called penetration testing or white-hat hacking) involves using the same tools and techniques as hackers but legally and without causing damage. There are different types of hackers, including black hat hackers who use their skills maliciously, white hat hackers who use their skills defensively, and grey hat hackers whose behavior cannot be predicted. Ethical hacking is important for evaluating security and reporting vulnerabilities to owners.
Web and Mobile Application Security

OWASP security vulnerabilities, their technical and business impact and mitigating strategies for web and mobile applications with examples.
Information Security

This document discusses information security in management information systems. It defines information security and explains how classified information is typically stored and protected using high-level security networks, technology, and encryption. It also examines factors that influence information security systems, such as service agreements, operational requirements, and staff qualifications. Risk management in information technology is also covered, looking at risks like intellectual property protection, data leakage, and compliance. The document then analyzes a case study on security issues found at the FBI, such as unsecured networks, outdated plans and training. It also discusses wireless security threats and solutions for protecting wireless networks and devices. Finally, it addresses the roles and responsibilities of management in information security systems.
3.8 Ways to Establish Secure Protocols in a Digital Organization.pdf

How to establish secure protocols in a digital organization? In recent years, massive cybercrimes have targeted businesses all around the world. Organizations are constantly subjected to security breaches, including data leaks, broken authentication, database hacking, malware infestations, and denial of service attacks on their networks, web applications, and servers.
https://itphobia.com/8-ways-to-establish-secure-protocols-in-a-digital-organization/
Ethical hacking seminardk fas kjfdhsakjfh askfhksahf.pptx

This document provides an overview of ethical hacking. It defines hacking and describes different types of hackers such as white-hat, black-hat, and grey-hat hackers. Ethical hacking, or white-hat hacking, involves legally testing a system's security to help strengthen it. The document outlines the typical hacking process and some common attack types such as denial of service attacks and SQL injection. It discusses the advantages and disadvantages of ethical hacking, required skills, and how ethical hackers have helped identify vulnerabilities. Lastly, it provides tips for protecting systems and future areas for enhancing security techniques.
Chapter 4

Mobile devices are vulnerable due to weaknesses in their applications, operating systems, network protocols, hardware configurations, and security policies. Threats can take advantage of these vulnerabilities and come in many forms, including unstructured threats from inexperienced hackers, structured threats from skilled hackers, external threats from outside attackers, and internal threats from inside a company. Common attacks include application-based malware and spyware, web-based phishing scams and drive-by downloads, network-based exploits, and physical threats from lost, stolen, or compromised devices.
Securing Your Remote Access Desktop Connection

Many businesses use remote access software for more convenience, but it poses some data security risks. Learn how to properly secure your remote access.
Security (IM).ppt

This document discusses various topics related to IT security including security, testing, error detection, control, vulnerability, disaster management, computer crime, and securing networks. It provides information on different types of security like physical security, network security, and information security. It also covers principles of security, causes of accidents, types of computer crimes like hacking and cyber theft. Other topics include computer viruses and worms, different types of testing, error detection methods, and an overview of securing web applications and networks.
Similar to Infographic: Penetration Testing - A Look into a Full Pen Test Campaign (20)
Application security testing an integrated approach

Application security testing an integrated approach
VAPT - Vulnerability Assessment & Penetration Testing 

VAPT - Vulnerability Assessment & Penetration Testing
Information Technology Security Is Vital For The Success...

Information Technology Security Is Vital For The Success...
3.8 Ways to Establish Secure Protocols in a Digital Organization.pdf

3.8 Ways to Establish Secure Protocols in a Digital Organization.pdf
Ethical hacking seminardk fas kjfdhsakjfh askfhksahf.pptx

Ethical hacking seminardk fas kjfdhsakjfh askfhksahf.pptx
Recently uploaded
What is an RPA CoE? Session 1 – CoE Vision

In the first session, we will review the organization's vision and how this has an impact on the COE Structure.
Topics covered:
• The role of a steering committee
• How do the organization’s priorities determine CoE Structure?
Speaker:
Chris Bolin, Senior Intelligent Automation Architect Anika Systems
TrustArc Webinar - 2024 Global Privacy Survey

How does your privacy program stack up against your peers? What challenges are privacy teams tackling and prioritizing in 2024?
In the fifth annual Global Privacy Benchmarks Survey, we asked over 1,800 global privacy professionals and business executives to share their perspectives on the current state of privacy inside and outside of their organizations. This year’s report focused on emerging areas of importance for privacy and compliance professionals, including considerations and implications of Artificial Intelligence (AI) technologies, building brand trust, and different approaches for achieving higher privacy competence scores.
See how organizational priorities and strategic approaches to data security and privacy are evolving around the globe.
This webinar will review:
- The top 10 privacy insights from the fifth annual Global Privacy Benchmarks Survey
- The top challenges for privacy leaders, practitioners, and organizations in 2024
- Key themes to consider in developing and maintaining your privacy program
Building Production Ready Search Pipelines with Spark and Milvus

Spark is the widely used ETL tool for processing, indexing and ingesting data to serving stack for search. Milvus is the production-ready open-source vector database. In this talk we will show how to use Spark to process unstructured data to extract vector representations, and push the vectors to Milvus vector database for search serving.
Driving Business Innovation: Latest Generative AI Advancements & Success Story

Are you ready to revolutionize how you handle data? Join us for a webinar where we’ll bring you up to speed with the latest advancements in Generative AI technology and discover how leveraging FME with tools from giants like Google Gemini, Amazon, and Microsoft OpenAI can supercharge your workflow efficiency.
During the hour, we’ll take you through:
Guest Speaker Segment with Hannah Barrington: Dive into the world of dynamic real estate marketing with Hannah, the Marketing Manager at Workspace Group. Hear firsthand how their team generates engaging descriptions for thousands of office units by integrating diverse data sources—from PDF floorplans to web pages—using FME transformers, like OpenAIVisionConnector and AnthropicVisionConnector. This use case will show you how GenAI can streamline content creation for marketing across the board.
Ollama Use Case: Learn how Scenario Specialist Dmitri Bagh has utilized Ollama within FME to input data, create custom models, and enhance security protocols. This segment will include demos to illustrate the full capabilities of FME in AI-driven processes.
Custom AI Models: Discover how to leverage FME to build personalized AI models using your data. Whether it’s populating a model with local data for added security or integrating public AI tools, find out how FME facilitates a versatile and secure approach to AI.
We’ll wrap up with a live Q&A session where you can engage with our experts on your specific use cases, and learn more about optimizing your data workflows with AI.
This webinar is ideal for professionals seeking to harness the power of AI within their data management systems while ensuring high levels of customization and security. Whether you're a novice or an expert, gain actionable insights and strategies to elevate your data processes. Join us to see how FME and AI can revolutionize how you work with data!
June Patch Tuesday

Ivanti’s Patch Tuesday breakdown goes beyond patching your applications and brings you the intelligence and guidance needed to prioritize where to focus your attention first. Catch early analysis on our Ivanti blog, then join industry expert Chris Goettl for the Patch Tuesday Webinar Event. There we’ll do a deep dive into each of the bulletins and give guidance on the risks associated with the newly-identified vulnerabilities.
Skybuffer SAM4U tool for SAP license adoption

Manage and optimize your license adoption and consumption with SAM4U, an SAP free customer software asset management tool.
SAM4U, an SAP complimentary software asset management tool for customers, delivers a detailed and well-structured overview of license inventory and usage with a user-friendly interface. We offer a hosted, cost-effective, and performance-optimized SAM4U setup in the Skybuffer Cloud environment. You retain ownership of the system and data, while we manage the ABAP 7.58 infrastructure, ensuring fixed Total Cost of Ownership (TCO) and exceptional services through the SAP Fiori interface.
Digital Banking in the Cloud: How Citizens Bank Unlocked Their Mainframe

Inconsistent user experience and siloed data, high costs, and changing customer expectations – Citizens Bank was experiencing these challenges while it was attempting to deliver a superior digital banking experience for its clients. Its core banking applications run on the mainframe and Citizens was using legacy utilities to get the critical mainframe data to feed customer-facing channels, like call centers, web, and mobile. Ultimately, this led to higher operating costs (MIPS), delayed response times, and longer time to market.
Ever-changing customer expectations demand more modern digital experiences, and the bank needed to find a solution that could provide real-time data to its customer channels with low latency and operating costs. Join this session to learn how Citizens is leveraging Precisely to replicate mainframe data to its customer channels and deliver on their “modern digital bank” experiences.
Programming Foundation Models with DSPy - Meetup Slides

Prompting language models is hard, while programming language models is easy. In this talk, I will discuss the state-of-the-art framework DSPy for programming foundation models with its powerful optimizers and runtime constraint system.
Biomedical Knowledge Graphs for Data Scientists and Bioinformaticians

Dmitrii Kamaev, PhD
Senior Product Owner - QIAGEN
Energy Efficient Video Encoding for Cloud and Edge Computing Instances

Energy Efficient Video Encoding for Cloud and Edge Computing Instances
[OReilly Superstream] Occupy the Space: A grassroots guide to engineering (an...![[OReilly Superstream] Occupy the Space: A grassroots guide to engineering (an...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[OReilly Superstream] Occupy the Space: A grassroots guide to engineering (an...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
The typical problem in product engineering is not bad strategy, so much as “no strategy”. This leads to confusion, lack of motivation, and incoherent action. The next time you look for a strategy and find an empty space, instead of waiting for it to be filled, I will show you how to fill it in yourself. If you’re wrong, it forces a correction. If you’re right, it helps create focus. I’ll share how I’ve approached this in the past, both what works and lessons for what didn’t work so well.
JavaLand 2024: Application Development Green Masterplan

My presentation slides I used at JavaLand 2024
Digital Marketing Trends in 2024 | Guide for Staying Ahead

https://www.wask.co/ebooks/digital-marketing-trends-in-2024
Feeling lost in the digital marketing whirlwind of 2024? Technology is changing, consumer habits are evolving, and staying ahead of the curve feels like a never-ending pursuit. This e-book is your compass. Dive into actionable insights to handle the complexities of modern marketing. From hyper-personalization to the power of user-generated content, learn how to build long-term relationships with your audience and unlock the secrets to success in the ever-shifting digital landscape.
GraphRAG for LifeSciences Hands-On with the Clinical Knowledge Graph

Tomaz Bratanic
Graph ML and GenAI Expert - Neo4j
Dandelion Hashtable: beyond billion requests per second on a commodity server

This slide deck presents DLHT, a concurrent in-memory hashtable. Despite efforts to optimize hashtables, that go as far as sacrificing core functionality, state-of-the-art designs still incur multiple memory accesses per request and block request processing in three cases. First, most hashtables block while waiting for data to be retrieved from memory. Second, open-addressing designs, which represent the current state-of-the-art, either cannot free index slots on deletes or must block all requests to do so. Third, index resizes block every request until all objects are copied to the new index. Defying folklore wisdom, DLHT forgoes open-addressing and adopts a fully-featured and memory-aware closed-addressing design based on bounded cache-line-chaining. This design offers lock-free index operations and deletes that free slots instantly, (2) completes most requests with a single memory access, (3) utilizes software prefetching to hide memory latencies, and (4) employs a novel non-blocking and parallel resizing. In a commodity server and a memory-resident workload, DLHT surpasses 1.6B requests per second and provides 3.5x (12x) the throughput of the state-of-the-art closed-addressing (open-addressing) resizable hashtable on Gets (Deletes).
Your One-Stop Shop for Python Success: Top 10 US Python Development Providers

Simplify your search for a reliable Python development partner! This list presents the top 10 trusted US providers offering comprehensive Python development services, ensuring your project's success from conception to completion.
Leveraging the Graph for Clinical Trials and Standards

Katja Glaß
OpenStudyBuilder Community Manager - Katja Glaß Consulting
Marius Conjeaud
Principal Consultant - Neo4j
Generating privacy-protected synthetic data using Secludy and Milvus

During this demo, the founders of Secludy will demonstrate how their system utilizes Milvus to store and manipulate embeddings for generating privacy-protected synthetic data. Their approach not only maintains the confidentiality of the original data but also enhances the utility and scalability of LLMs under privacy constraints. Attendees, including machine learning engineers, data scientists, and data managers, will witness first-hand how Secludy's integration with Milvus empowers organizations to harness the power of LLMs securely and efficiently.
Recently uploaded (20)
Building Production Ready Search Pipelines with Spark and Milvus

Building Production Ready Search Pipelines with Spark and Milvus
Driving Business Innovation: Latest Generative AI Advancements & Success Story

Driving Business Innovation: Latest Generative AI Advancements & Success Story
Deep Dive: AI-Powered Marketing to Get More Leads and Customers with HyperGro...

Deep Dive: AI-Powered Marketing to Get More Leads and Customers with HyperGro...
Digital Banking in the Cloud: How Citizens Bank Unlocked Their Mainframe

Digital Banking in the Cloud: How Citizens Bank Unlocked Their Mainframe
Programming Foundation Models with DSPy - Meetup Slides

Programming Foundation Models with DSPy - Meetup Slides
Biomedical Knowledge Graphs for Data Scientists and Bioinformaticians

Biomedical Knowledge Graphs for Data Scientists and Bioinformaticians
Energy Efficient Video Encoding for Cloud and Edge Computing Instances

Energy Efficient Video Encoding for Cloud and Edge Computing Instances
[OReilly Superstream] Occupy the Space: A grassroots guide to engineering (an...![[OReilly Superstream] Occupy the Space: A grassroots guide to engineering (an...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[OReilly Superstream] Occupy the Space: A grassroots guide to engineering (an...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[OReilly Superstream] Occupy the Space: A grassroots guide to engineering (an...
JavaLand 2024: Application Development Green Masterplan

JavaLand 2024: Application Development Green Masterplan
Digital Marketing Trends in 2024 | Guide for Staying Ahead

Digital Marketing Trends in 2024 | Guide for Staying Ahead
GraphRAG for LifeSciences Hands-On with the Clinical Knowledge Graph

GraphRAG for LifeSciences Hands-On with the Clinical Knowledge Graph
Dandelion Hashtable: beyond billion requests per second on a commodity server

Dandelion Hashtable: beyond billion requests per second on a commodity server
Your One-Stop Shop for Python Success: Top 10 US Python Development Providers

Your One-Stop Shop for Python Success: Top 10 US Python Development Providers
Leveraging the Graph for Clinical Trials and Standards

Leveraging the Graph for Clinical Trials and Standards
Generating privacy-protected synthetic data using Secludy and Milvus

Generating privacy-protected synthetic data using Secludy and Milvus
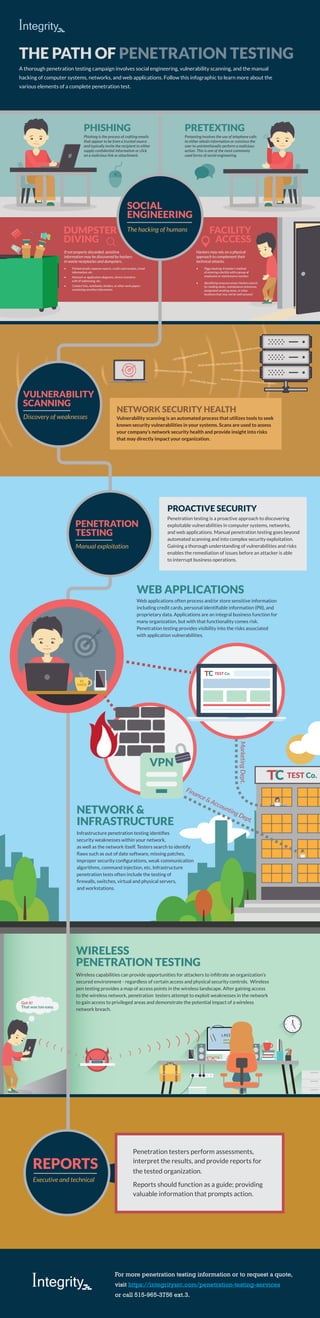
Infographic: Penetration Testing - A Look into a Full Pen Test Campaign
- 1. ***** username LOGIN WIRELESS PENETRATION TESTING That was too easy. Got it! TEST Co. PHISHING DUMPSTER DIVING FACILITY ACCESS PRETEXTING THE PATH OF PENETRATION TESTING VULNERABILITY SCANNING Discovery of weaknesses Pretexting involves the use of telephone calls to either obtain information or convince the user to unintentionally perform a malicious action. This is one of the most commonly used forms of social engineering. If not properly discarded, sensitive information may be discovered by hackers in waste receptacles and dumpsters. • Printed emails, expense reports, credit card receipts, travel information, etc. • Network or application diagrams, device inventory with IP addressing, etc. • Contact lists, notebooks, binders, or other work papers containing sensitive information Hackers may rely on a physical approach to complement their technical attacks. • Piggy backing: A hacker’s method of entering a facility with a group of employees or maintenance workers • Identifying unsecure areas: Hackers search for loading docks, maintenance entrances, designated smoking areas, or other locations that may not be well secured. Phishing is the process of crafting emails that appear to be from a trusted source and typically invite the recipient to either supply confidential information or click on a malicious link or attachment. PEAR.XMLRPC.XML.File.Code.Injection MS.IIS.ISAPI.Extension.Buffer.Overflow Ajax.File.Browser.approot.Parameter.File.Inclusion HTTP.Negative.Data.Length PHP.PHPInfo.Cross.Site.Scripting MS.Windows.CMD.Reverse.Shell HTTP.URI.SQL.Injection Vulnerability scanning is an automated process that utilizes tools to seek known security vulnerabilities in your systems. Scans are used to assess your company’s network security health and provide insight into risks that may directly impact your organization. NETWORK SECURITY HEALTH Penetration testing is a proactive approach to discovering exploitable vulnerabilities in computer systems, networks, and web applications. Manual penetration testing goes beyond automated scanning and into complex security exploitation. Gaining a thorough understanding of vulnerabilities and risks enables the remediation of issues before an attacker is able to interrupt business operations. Web applications often process and/or store sensitive information including credit cards, personal identifiable information (PII), and proprietary data. Applications are an integral business function for many organization, but with that functionality comes risk. Penetration testing provides visibility into the risks associated with application vulnerabilities. Infrastructure penetration testing identifies security weaknesses within your network, as well as the network itself. Testers search to identify flaws such as out of date software, missing patches, improper security configurations, weak communication algorithms, command injection, etc. Infrastructure penetration tests often include the testing of firewalls, switches, virtual and physical servers, and workstations. PROACTIVE SECURITY PENETRATION TESTING Manual exploitation MarketingDept. Finance & Accounting Dept. WEB APPLICATIONS NETWORK & INFRASTRUCTURE TEST Co. VPN HACK #1 Wireless capabilities can provide opportunities for attackers to infiltrate an organization’s secured environment - regardless of certain access and physical security controls. Wireless pen testing provides a map of access points in the wireless landscape. After gaining access to the wireless network, penetration testers attempt to exploit weaknesses in the network to gain access to privileged areas and demonstrate the potential impact of a wireless network breach. A thorough penetration testing campaign involves social engineering, vulnerability scanning, and the manual hacking of computer systems, networks, and web applications. Follow this infographic to learn more about the various elements of a complete penetration test. For more penetration testing information or to request a quote, visit https://integritysrc.com/penetration-testing-services or call 515-965-3756 ext.3. SOCIAL ENGINEERING The hacking of humans REPORTS Executive and technical Penetration testers perform assessments, interpret the results, and provide reports for the tested organization. Reports should function as a guide; providing valuable information that prompts action.
